To manage permissions on Alibaba Cloud services including Enterprise Distributed Application Service (EDAS) in one access control system, you can replace EDAS-defined permissions with the policies of Resource Access Management (RAM). This topic describes how to replace EDAS-defined permissions with RAM policies.
Background information
For information about the structure and syntax of RAM policies, see Policy structure and syntax.
Parameter | Description |
Effect | Specifies whether a statement result is an explicit allow or an explicit deny. Valid values: Allow and Deny. |
Action | Describes one or more API operations that are allowed or denied. You can specify one or more operations. Set the value to the name of the operation for the resource. Format:
|
Resource | Specifies one or more objects that the statement covers. Syntax: |
Condition (optional) | Specifies the conditions that are required for a policy to take effect. A condition block consists of one or more condition clauses. A condition clause consists of a key, an operator, and a value. |
Step 1: Create a policy for EDAS-defined permissions
You can use one of the following methods to create or query a policy for EDAS-defined permissions:
Method 1: Query the library of sample policies and permissions
You can query RAM policies and EDAS-defined permissions in the library. For more information, see RAM policies.
Method 2: Use the permission assistant to create a policy
The scenario in the following example involves only basic operations. For more information, see Use the EDAS permission assistant to create RAM policies.
Log on to the EDAS console.
In the left-side navigation pane, choose .
On the Permission Assistant page, click New permission Strategy.
In the New permission Strategy panel, configure the parameters.
In the Create a new custom permission policy step, configure the parameters and click next step. The following table describes the parameters.
Parameter
Description
Name of strategy
Enter a custom name for the policy.
note
Enter remarks for the policy.
New permission statement
Click New permission statement. You can add one or more statements.
In the Add authorization statement panel, configure the Permissions for and Operations and resource authorization parameters. Then, click yes.
ImportantWhen you create a policy, you can select only one of the following effects: Allow and Deny.
In the Create a new custom permission policy step, find a statement in the statement list and click duplicate, edit, or delete in the operation column to copy, modify, or delete the statement as required.
In the Strategy to preview step, preview the policy. Click copy in the upper-right corner of the code editor and click Finish in the lower-left corner.
The following message appears: New policy authorization succeeded. You can click Return to list view to view and manage the created policy.
Find the created policy and click view detail. In the view detail message, click copy to copy the created policy.
Method 3: Create a RAM policy based on EDAS-defined permissions
If you have specified RAM users that are granted EDAS-defined permissions, you can create a RAM policy based on the EDAS-defined permissions in the EDAS console.
Log on to the EDAS console.
In the left-side navigation pane, choose .
On the RAM User page, find a RAM user to which EDAS-defined permissions are granted and click Create RAM Permission Policy in the RAM Authorization column.
In the RAM Permission Policy message, copy the policy and click OK.
Step 2: Create a policy in RAM
Log on to the RAM console with an Alibaba Cloud account.
In the left-side navigation pane, choose .
On the Policies page, click Create Policy.
- On the Create Policy page, click the JSON tab.
In the code editor, enter a custom policy and click Next to edit policy information.
NotePaste the policy that you copied in Step 1.
- Specify the Name and Description fields.
- Check and optimize the document of the custom policy.
- Basic optimization
The system automatically optimizes the policy statement. The system performs the following operations during basic optimization:
- Deletes unnecessary conditions.
- Deletes unnecessary arrays.
- Optional:Advanced optimization
You can move the pointer over Optional advanced optimize and click Perform. The system performs the following operations during the advanced optimization:
- Splits resources or conditions that are incompatible with actions.
- Narrows down resources.
- Deduplicates or merges policy statements.
- Basic optimization
- Click OK.
Step 3: Create a RAM user and attach the policy to the RAM user
Log on to the RAM console with your Alibaba Cloud account.
In the left-side navigation pane, choose .
On the Users page, click Create User.
In the User Account Information section of the Create User page, configure the following parameters:
Logon Name: The logon name can be up to 64 characters in length, and can contain letters, digits, periods (.), hyphens (-), and underscores (_).
Display Name: The display name can be up to 128 characters in length.
(Optional) Tag: You can click the
 icon. In the dialog box that appears, specify the Tag Key and Tag Value parameters. You can add one or more tags to the RAM user. This way, you can manage the RAM user based on the tags.
icon. In the dialog box that appears, specify the Tag Key and Tag Value parameters. You can add one or more tags to the RAM user. This way, you can manage the RAM user based on the tags.
NoteYou can click Add User to create multiple RAM users at a time.
In the Access Mode section, select an access mode and configure the required parameters.
To ensure the security of your Alibaba Cloud account, we recommend that you select only one access mode for the RAM user. This way, the RAM user for an individual is separated from the RAM user for a program.
Console Access
If the RAM user represents an individual, we recommend that you select Console Access for the RAM user. This way, the RAM user can use a username and password to access Alibaba Cloud. If you select Console Access, you must configure the following parameters:
Console Password: You can select Automatically Regenerate Default Password or Reset Custom Password. If you select Reset Custom Password, you must specify a password. The password must meet the complexity requirements. For more information, see Configure a password policy for RAM users.
Password Reset: specifies whether the RAM user is required to reset the password upon the next logon.
Multi-factor Authentication: specifies whether to enable multi-factor authentication (MFA) for the RAM user. If you select Required to Enable MFA for the RAM user, the RAM user must bind an MFA device when the RAM user logs on to the Alibaba Cloud Management Console. For more information, see Bind an MFA device to a RAM user.
OpenAPI Access
If the RAM user represents a program, we recommend that you select OpenAPI Access for the RAM user. This way, the RAM user can use an AccessKey pair to access Alibaba Cloud. If you select OpenAPI Access, the system automatically generates an AccessKey ID and AccessKey secret for the RAM user. For more information, see Create an AccessKey pair.
Click OK.
On the Users page, find the created RAM user and click Add Permissions in the Actions column.
In the Add Permissions panel, attach the policy that you created in Step 2 to the RAM user and click OK.
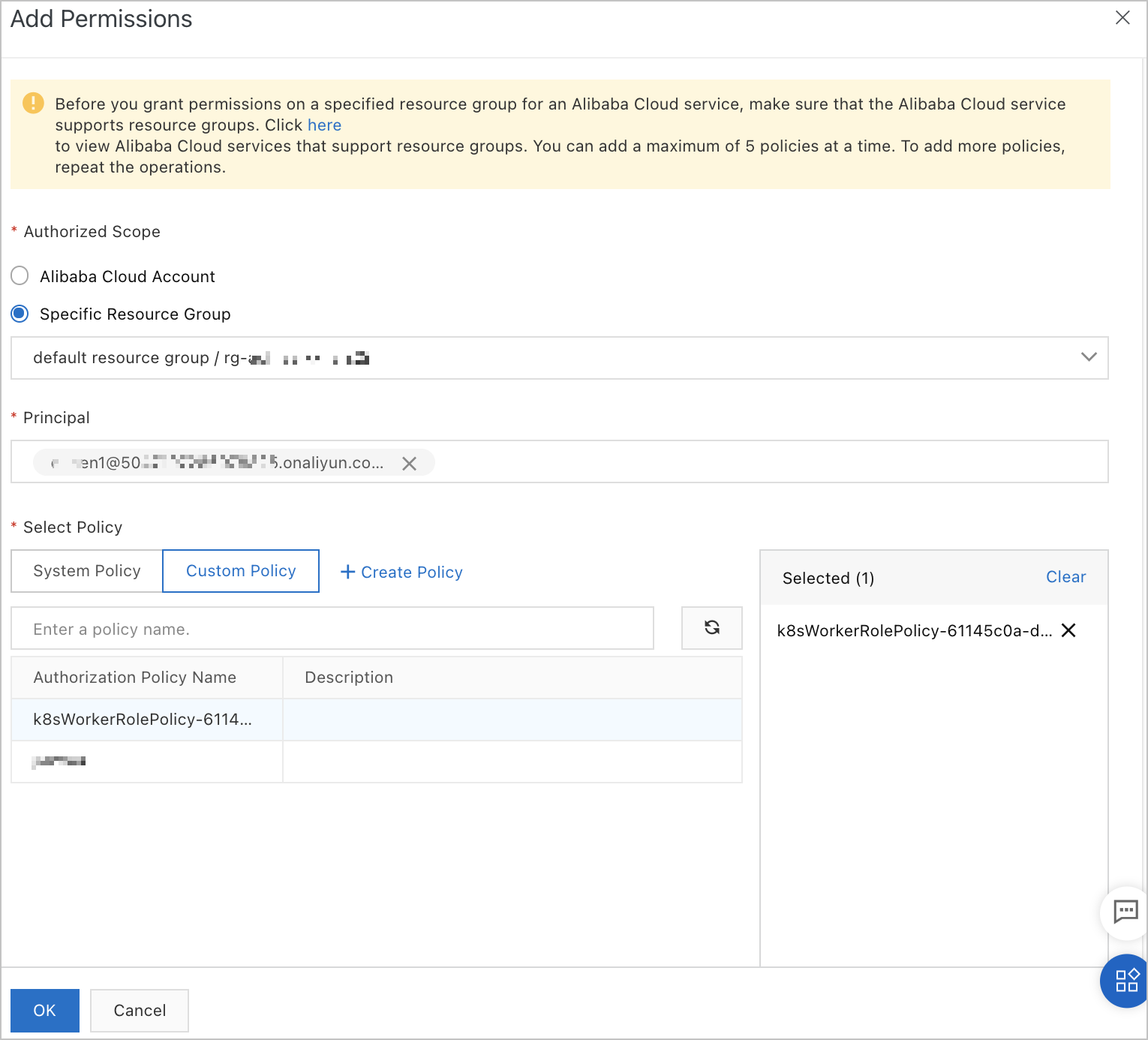
Parameter
Description
Authorized Scope
Valid values: Alibaba Cloud Account and Specific Resource Group. Select an authorized scope based on your business requirements.
Principal
By default, the current RAM user is selected.
Select Policy
Click the Custom Policy tab. Enter the policy name in the search box to search for the policy. Then, click the policy name in the Authorization Policy Name column.
Step 4: Replace the EDAS-defined permissions with the RAM policy for the RAM user in the EDAS console
Log on to the EDAS console.
In the left-side navigation pane, choose .
On the RAM User page, find the RAM user that you want to manage and click Switch to RAM User in the RAM Authorization column.
NoteAfter the EDAS-defined permissions are replaced by the RAM policy for the RAM user, the Switch to RAM User button in the RAM Authorization column is dimmed.
You cannot replace the RAM policy back with the EDAS-defined permissions. After the EDAS-defined permissions are replaced by the RAM policy, the RAM user can no longer use EDAS-defined permissions.
After you click Switch to RAM User, EDAS checks whether the RAM user is granted the permissions on EDAS in the RAM console.
If the RAM user is granted the permissions on EDAS, click OK in the message that appears.
If the RAM user is not granted the permissions on EDAS, you must first grant the permissions in the RAM console.