Some features of Alibaba Cloud Elasticsearch (ES) clusters are unavailable because of limitations in the new network architecture. You can use PrivateLink and Server Load Balancer (SLB) to establish a private connection between an Alibaba Cloud ES cluster and other cloud resources. These resources can include Elastic Compute Service (ECS) instances, elastic network interfaces (ENIs), elastic container instances (ECIs), or network resources at a specific IP address. This topic describes how to use Classic Load Balancer (CLB) and PrivateLink to establish a private connection between an Alibaba Cloud ES cluster and other Alibaba Cloud server resources. This topic also describes how to use Network Load Balancer (NLB) and PrivateLink to establish a private connection between Alibaba Cloud ES clusters. You can apply these solutions to other scenarios that are supported by PrivateLink and SLB.
Configuring a private connection is the only way to overcome the limitations that the new network architecture imposes on features such as X-Pack Watcher, reindex, Lightweight Directory Access Protocol (LDAP) authentication, and Active Directory (AD) user authentication.
Clusters created in or after October 2020 are deployed in the new network architecture and support private connections. Clusters created before October 2020 use the original network architecture and do not support private connections. This includes clusters in Alibaba Finance Cloud and Alibaba Gov Cloud.
Application scenarios for Alibaba Cloud ES PrivateLink
An ES cluster needs to access service resources in an external network for features such as Watcher alerts, LDAP, or Active Directory.
You can configure a private connection between an Alibaba Cloud ES cluster and an Alibaba Cloud ECS instance. The ECS instance can act as a business server or a proxy server to forward network traffic. The following figure shows how this works.
The following table describes the scenarios and features.
Feature
Scenario description
References
Watcher
The X-Pack feature of Alibaba Cloud ES monitors system information based on query conditions and provides an external alert service.
Alibaba Cloud ES security features
The X-Pack feature of Alibaba Cloud ES supports various cluster-level security settings, such as LDAP and AD user authentication.
Custom plug-ins accessing external dictionaries
Custom plug-ins dynamically access dictionaries on an external network.
Cross-cluster reindex
You can use cross-cluster reindex to write data from a self-managed ES cluster to an Alibaba Cloud ES cluster.
Migrate data from a self-managed Elasticsearch cluster to Alibaba Cloud using a private connection
You can migrate data between two Alibaba Cloud ES clusters using cross-cluster reindex. In this scenario, two ES clusters are deployed in VPC_1 and VPC_2. You can configure a private connection for the ES_1 cluster in VPC_1. This connects the endpoint in VPC_1 to the endpoint service in VPC_2 and establishes a private connection between the two ES clusters. The following figure shows how this works.
The following table describes the scenarios and features.
Feature
Scenario description
References
reindex
Use cross-cluster reindex to write data from one Alibaba Cloud ES cluster to another.
Use NLB and PrivateLink to establish a private connection between Alibaba Cloud ES clusters
Terms
To use PrivateLink for private access, you must create an endpoint and an endpoint service.
Term | Description |
Endpoint service | An endpoint service is a service that can be connected to from other VPCs by creating an endpoint. You must manually create the related service resources. |
Endpoint | An endpoint is associated with an endpoint service and can establish a network connection to access external services through a VPC private network. When you configure a private connection for an Alibaba Cloud ES cluster, an endpoint is automatically created in the network environment of the ES cluster. |
Use CLB and PrivateLink to establish a private connection between an Alibaba Cloud ES cluster and an ECS instance
Prerequisites
An Alibaba Cloud ES cluster was created in VPC_1 in or after October 2020. For more information, see Create an Alibaba Cloud ES cluster.
An ECS instance was created in VPC_2 and the related applications are deployed. For more information, see Create an instance using the wizard.
NoteThe ECS instance serves as a backend server that receives requests forwarded by the SLB instance. When you create the ECS instance, you must select a region and a zone that support PrivateLink. For information about the regions that support PrivateLink, see Regions and zones that support PrivateLink.
The Alibaba Cloud ES, ECS, and SLB instances must be deployed in the same zone of the same region.
Step 1: Create and configure an SLB instance
Log on to the CLB console.
Create an SLB instance that supports PrivateLink.
On the Instances page, click Create CLB.
On the CLB (Pay-As-You-Go) purchase page, select the same region as the Alibaba Cloud ES cluster, set Instance Type to Intranet, and click Buy Now to purchase the CLB instance.
For more information, see Create and manage a CLB instance.
Configure the SLB instance.
On the Instances page, find the destination instance. In the Actions column, click Configure Listener.
On the Configure Server Load Balancer page, configure the listener and backend servers, perform a health check, and review the configuration.
For more information, see Configure an SLB instance and CLB listeners.
Step 2: Create an endpoint service
The private connection feature automatically creates an endpoint in the network environment of the ES cluster. You only need to manually create an endpoint service in the environment of the ECS instance.
In the top navigation bar, select the region where you want to create the endpoint service.
The endpoint service must be in the same region as the SLB instance.
Click Create Endpoint Service.
On the Create Endpoint Service page, select the SLB instance as the service resource, configure other parameters as needed, and click OK.
For more information, see Create an endpoint service.
Step 3: Configure a private connection for the Alibaba Cloud ES cluster
Log on to the Alibaba Cloud Elasticsearch console.
In the left-side navigation pane, click Elasticsearch Clusters.
Navigate to the desired cluster.
In the top navigation bar, select the resource group to which the cluster belongs and the region where the cluster resides.
On the Elasticsearch Clusters page, find the cluster and click its ID.
In the navigation pane on the left, choose .
In the Network Settings section, click Modify to the right of Configure Private Connection.
In the Configure Private Connection panel, click Add Private Connection.
In the Associated Endpoint Service dialog box that appears, select a Zone, select the acknowledgment checkbox, and then click OK.
In the Actions column of the endpoint, click Allow Connection.
After the endpoint and the endpoint service are connected, the Endpoint Connection Status changes to Connected. This indicates that communication is enabled between the ES cluster in VPC_1 and VPC_2.
(Optional) View the domain name of the endpoint.
You can use the domain name of the endpoint for other service configurations, such as Watcher, single sign-on (SSO), and LDAP.
In the Configure Private Connection panel, click the ID of the destination Endpoint ID.
On the Endpoint Connections tab, click the
 icon next to the destination endpoint ID to view the domain name that corresponds to the endpoint.
icon next to the destination endpoint ID to view the domain name that corresponds to the endpoint.
Use NLB and PrivateLink to establish a private connection between Alibaba Cloud ES clusters
This section describes how to use a Network Load Balancer (NLB) instance to connect an Alibaba Cloud ES_1 cluster to an Alibaba Cloud ES_2 cluster. You can mount the IP address of the ES_2 cluster to the NLB instance. This method is often used when two Alibaba Cloud ES clusters cannot communicate with each other because of network architecture limitations.
After a private connection is established between the ES_1 and ES_2 clusters, you can migrate data from the ES_2 cluster to the ES_1 cluster.
Alibaba Cloud NLB supports IP address mounting. For more information, see Features.
Prerequisites
Two Alibaba Cloud ES clusters were created in the same region and zone.
When you create the ES clusters, you must select a region and a zone that support PrivateLink. For information about the regions that support PrivateLink, see Regions and zones that support PrivateLink.
Step 1: Create an NLB instance
An NLB instance receives requests from clients and forwards the requests to backend servers based on listening rules. To use the NLB service, you must create an NLB instance and add a listener and backend servers to the instance.
Create an NLB instance.
Log on to the NLB console.
On the Instances page, click Create NLB.
On the purchase page, configure the instance parameters.
Select the region for the ES_2 cluster, set the network type to Internal-facing, and select the zone.
For more information, see Create and manage an NLB instance.
Create an NLB server group.
A server group is used to route requests from clients to one or more backend servers. NLB determines the service availability of backend servers by performing health checks. When you add a listener to an NLB instance, you must specify a server group. The listener uses the configured protocol and port to check client connection requests and forward traffic to the corresponding server group.
On the Server Groups page, click Create Server Group.
In the dialog box that appears, configure the server group.
Set the server group type to IP, enter a custom name, and select the VPC associated with the ES_2 cluster.
Add the ES_2 cluster to the NLB instance as a backend server.
Add the private IP address and port of the ES_2 cluster to the server group that you created.
Run the ping command to retrieve the private IP address of the ES_2 cluster.
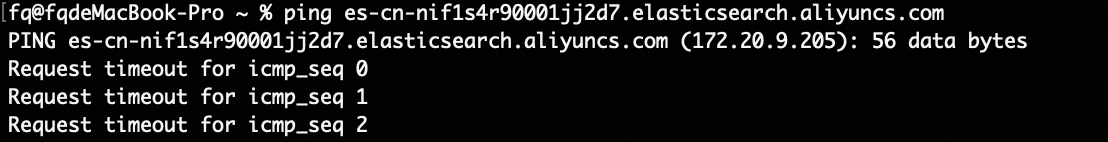
In the Actions column for the destination server group, click Modify Backend Server.
On the Backend Servers tab, click Add IP Address.
Add the private IP address of the ES_2 cluster to the backend servers and click Next.
Add the ES port that is used for the operation. For example, reindex requires port 9200 for communication.
Click OK.
Add a listener.
Log on to the NLB console.
On the Instances page, click Create Listener in the Actions column for the target NLB instance.
Set the listener protocol to TCP and the listener port to 9200, and then click Next.
Set the server group type to IP, select the backend server group, and click Next.
Click Submit.
Step 2: Create an endpoint service
The private connection feature automatically creates an endpoint in the network environment of the ES cluster. You only need to manually create an endpoint service in the environment of the other ES cluster.
Click Create Endpoint Service.
On the Create Endpoint Service page, you can configure the service.
The following table describes some of the parameters. For more information, see Create an NLB instance.
Configuration
Description
Region
Select the same region as the ES cluster.
Service Resource Type
Select Network Load Balancer (NLB).
Select Service Resource
The NLB instance that you created.
Service Payer
You can select either option.
Click OK.
After the endpoint service is created, it is attached to the NLB instance and appears in the Endpoint Service section.
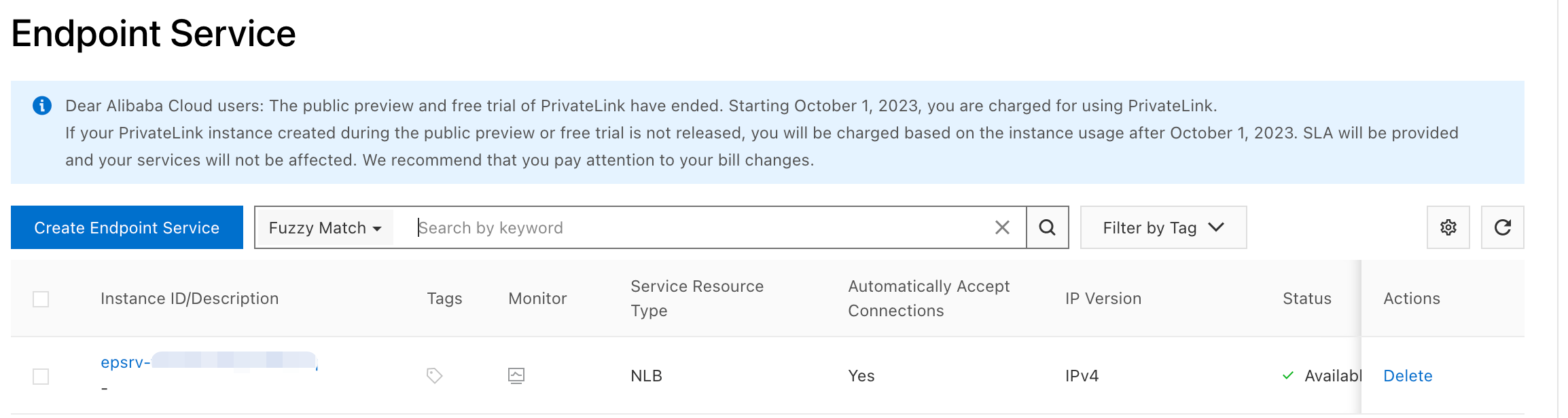
Step 3: Configure a private connection on the Alibaba Cloud ES cluster
Configure a private connection on the Alibaba Cloud ES_1 cluster. The system automatically creates an endpoint in the network environment of the ES_1 cluster to connect to the endpoint service.
Log on to the Alibaba Cloud Elasticsearch console.
In the left-side navigation pane, click Elasticsearch Clusters.
Navigate to the desired cluster.
In the top navigation bar, select the resource group to which the cluster belongs and the region where the cluster resides.
On the Elasticsearch Clusters page, find the cluster and click its ID.
In the navigation pane on the left, choose .
In the Network Settings section, click Edit to the right of Configure Private Connection.
In the Configure Private Connection panel, click Add Private Connection.
In the dialog box that appears, select the endpoint service that you created, complete the other configurations, and then click OK.
In the Actions column of the endpoint, click Allow Connection.
After the endpoint and the endpoint service are connected, the Endpoint Connection Status changes to Connected. This indicates that the ES_1 and ES_2 clusters are connected.
(Optional) View the domain name of the endpoint.
You can use the domain name of the endpoint and add it to a whitelist for other service configurations, such as Watcher, SSO, and LDAP.
In the Configure Private Connection panel, click the ID of the destination Endpoint ID.
On the Endpoint Connections tab, click the
 icon next to the destination endpoint ID to view the domain name that corresponds to the endpoint.
icon next to the destination endpoint ID to view the domain name that corresponds to the endpoint.
(Optional) Step 4: Test the connectivity between the ES clusters using reindex
You can use reindex to migrate an index from the Alibaba Cloud ES_2 cluster to the Alibaba Cloud ES_1 cluster to verify the network connectivity between the ES_1 and ES_2 clusters.
Configure a reindex whitelist in the YML file of the ES_1 cluster.
In the navigation pane on the left of the details page for the ES_1 cluster, choose .
In the upper-right corner of the YML File Configuration section, click Modify Configuration.
reindex.remote.whitelist: ["Domain name of the endpoint:9200"]
Prepare the data to migrate in the ES_2 cluster. Then, create an index in the ES_1 cluster and perform the reindex migration.
POST _reindex { "source": { "remote": { "host": "http://ep-bp1i4db71e6adaa29718-cn-hangzhou-i.epsrv-bp1fm3v8kc2qr2td6lrm.cn-hangzhou.privatelink.aliyuncs.com:9200", "username": "Username", "password": "Password" }, "index": "myindex" }, "dest": { "index": "myindex2" } }Category
Parameter
Description
source
host
The access address of the PrivateLink endpoint service. The address must contain the protocol, endpoint domain name, and port number. Example:
https://<Endpoint domain name>:9200.username
Optional. The default username for an Alibaba Cloud Elasticsearch cluster is elastic.
password
The password that corresponds to the username. The password for the elastic user of an Alibaba Cloud Elasticsearch cluster is set when you create the cluster. If you forget the password, you can reset it. For information about how to reset the password, see Reset the access password for an instance.
index
The source index in the remote cluster.
query
Use a query to specify the data to migrate. For more information, see Reindex API.
dest
index
The destination index in the local cluster.
In the ES_1 cluster, check whether the data from the ES_2 cluster was successfully migrated.