Object Storage Service (OSS) can use the server-side encryption feature to encrypt stored static data. To prevent data leaks due to the accidental deletion of encryption rules, you can use Data Security Center (DSC) to monitor OSS data-related operations. DSC monitors and records changes to encryption rules in OSS buckets in real time and generates alerts when encryption rules are deleted. This way, you can identify and handle OSS data leaks at the earliest opportunity.
Overview
In this example, the server-side encryption feature is enabled for an OSS bucket. When a server-side encryption rule of the OSS bucket is deleted, an alert notification email is immediately sent to the specified security administrator. The security administrator can view the operation logs to check whether the account and source IP address that are used to delete the server-side encryption rule are normal and handle the alert accordingly.
To complete data risk auditing and alerting, perform the following steps:
Create an OSS bucket: Create an OSS bucket and enable the server-side encryption feature for the OSS bucket.
Connect the OSS bucket to DSC. Authorize DSC to access the OSS bucket. This ensures that DSC can audit the logs of the OSS bucket.
Configure audit alert rules and alert notifications for the OSS bucket: Enable cloud-native audit log collection to collect the logs of the OSS bucket and objects in the OSS bucket. If an audit alert rule is triggered, DSC generates alerts and sends alert notifications to the specified security administrator.
View and handle alerts: Analyze alerts and check whether the operation poses a threat to OSS data security and handle the alerts at the earliest opportunity.
The free edition of DSC is activated for the current account. DSC is authorized to access other Alibaba Cloud resources.
The free edition of DSC provides the data auditing, audit alerting, and alert notification features. The free edition provides 500 TB of OSS protection capacity each month free of charge. In this example, the free edition of DSC is activated.
OSS is activated. To activate OSS, go to the OSS buy page.
Step 1: Create an OSS bucket
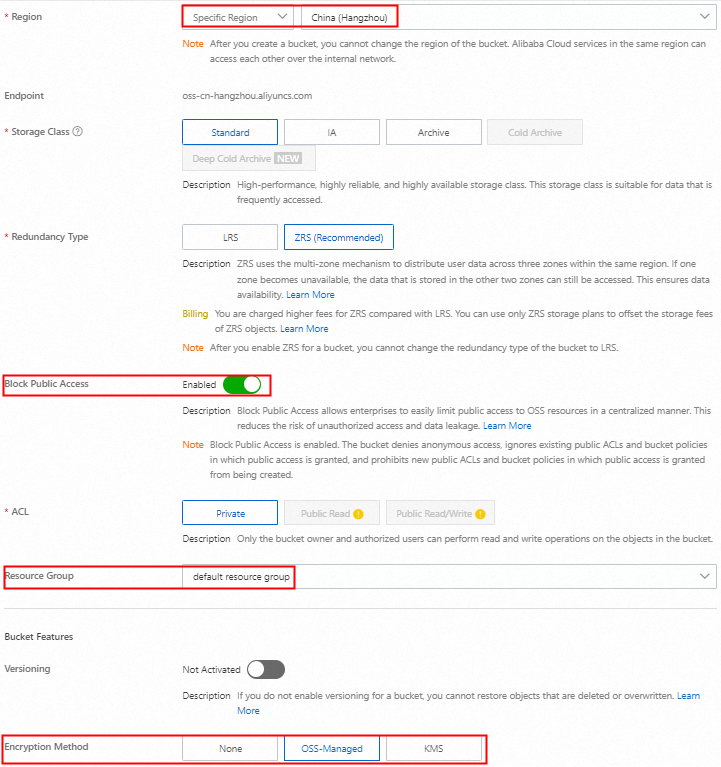
On the Buckets page in the OSS console, click Create Bucket.
In the Create Bucket panel, configure the parameters as shown in the following figure and use the default settings for other parameters. Then, click Create.
Step 2: Connect the OSS bucket to DSC
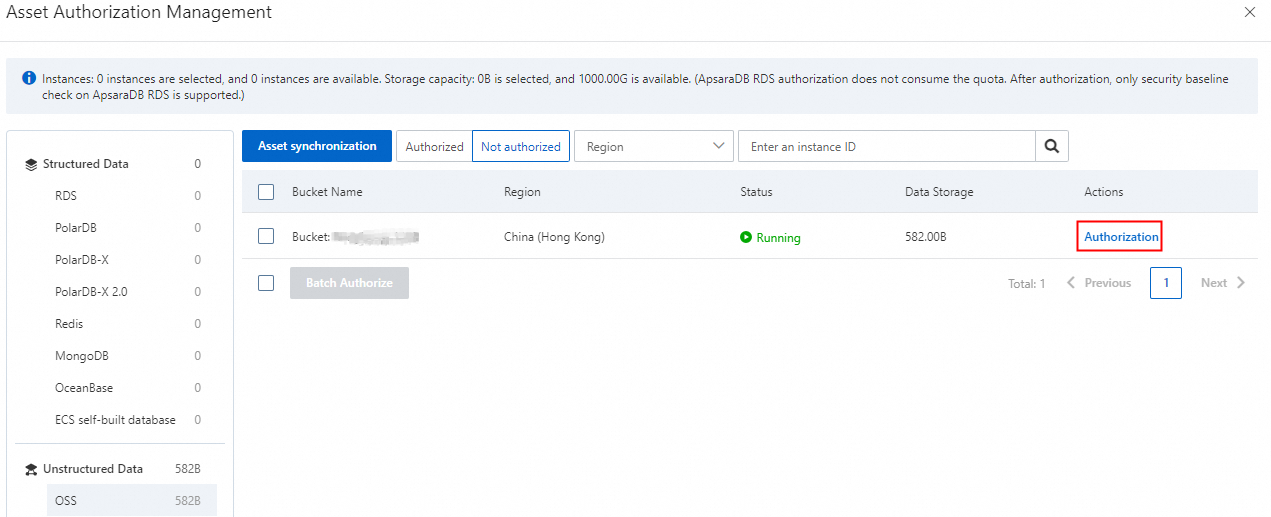
On the Authorization Management page in the DSC console, click Asset Authorization Management.
In the Asset Authorization Management panel, click OSS in the Unstructured Data section and click Asset synchronization.
After you synchronize assets, find the OSS bucket that you want to manage and click Authorization in the Actions column.
After the authorization is complete, find the OSS bucket on the Authorization Management page and click Connect in the Actions column.
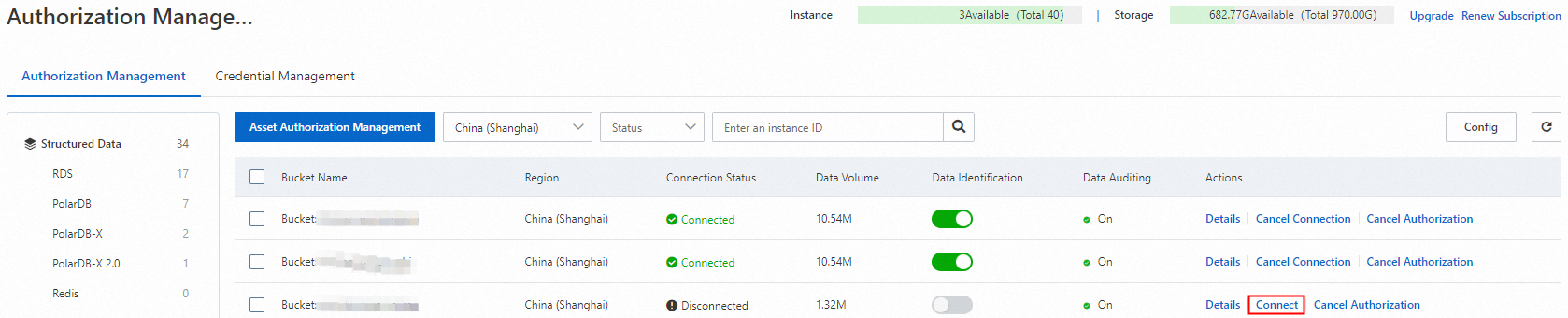
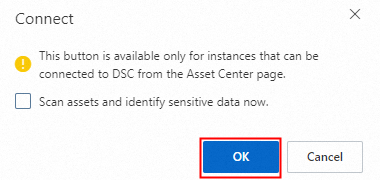
In the Batch Connect dialog box, click OK. You do not need to select Immediately scan database assets and identify data.
Wait until the Connection Status of the OSS bucket changes to Connected.
Step 3: Configure audit alert rules and alert notifications for the OSS bucket
3.1 Enable cloud-native audit log collection
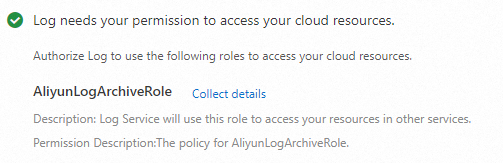
On the Asset Configurations tab of the Config page, click Authorize Now to authorize Simple Log Service to access cloud resources.
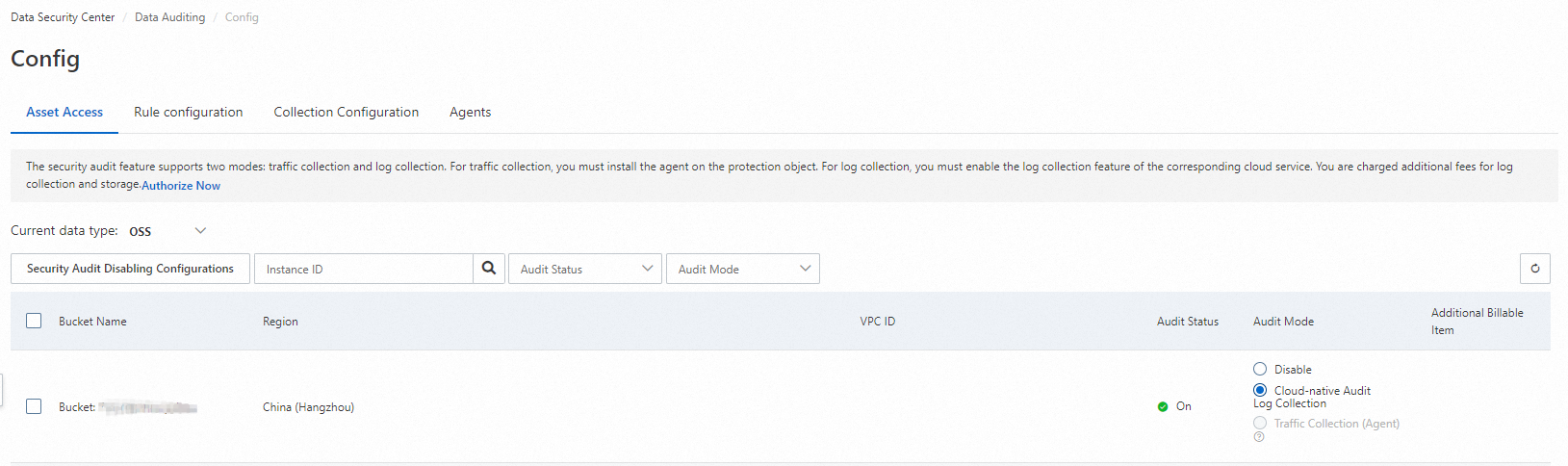
On the Asset Configurations tab, select OSS from the Current Data Type drop-down list.
Find the OSS bucket and select Cloud-native Audit Log Collection in the Audit Mode column. In the message that appears, click OK.
3.2 Enable audit alert rules
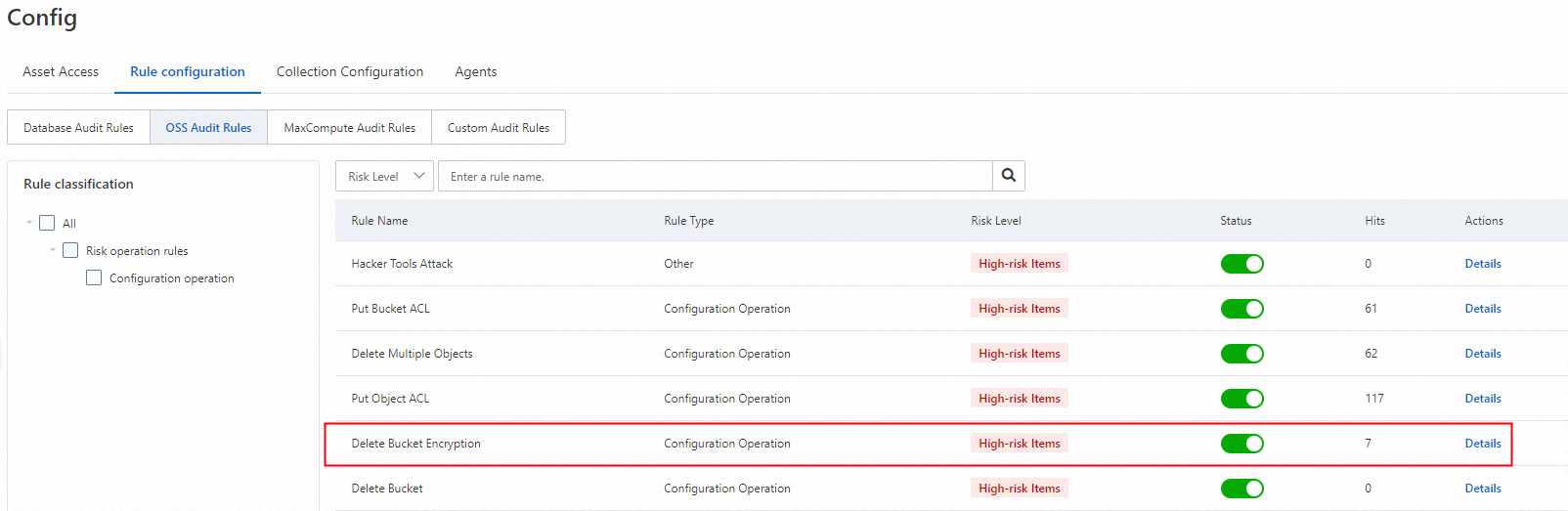
On the Rule Configurations tab of the Config page, click the OSS Audit Rules tab.
In the rule list, turn on Delete Bucket Encryption.
3.3 Configure alert notifications
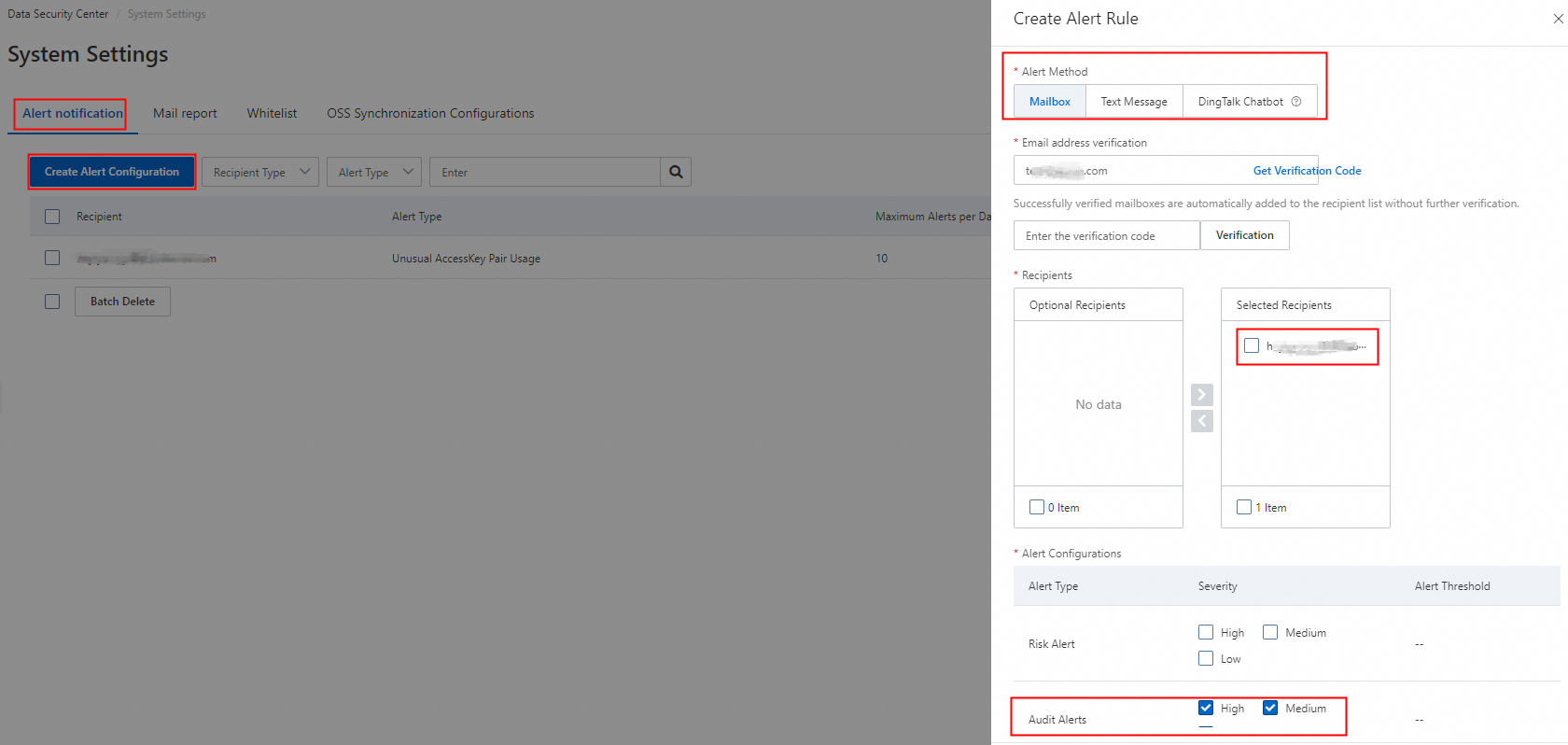
On the Alert notification tab, click Create Alert Configuration.
In the Create Alert Rule panel, set the Alert Method parameter to Mailbox, select all severity levels of audit alert rules, and then click OK.
Step 4: View alerts
If a server-side encryption rule of the OSS bucket is deleted, DSC generates an alert and sends an alert notification to the specified alert recipients.
4.1 View alert notification emails
The specified alert recipients receive the alert information in emails.
4.2 View alerts
On the Audit Alerts page, view OSS alerts.
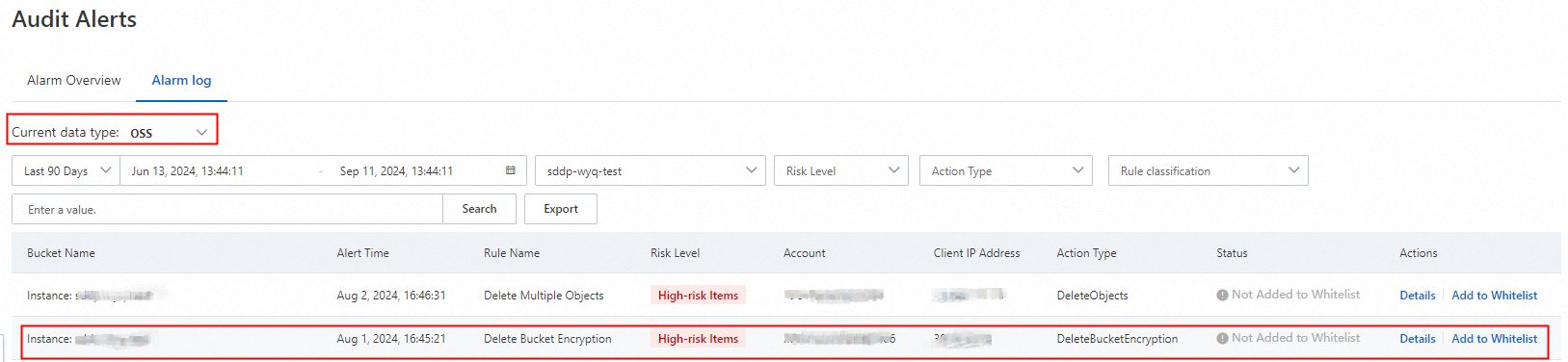
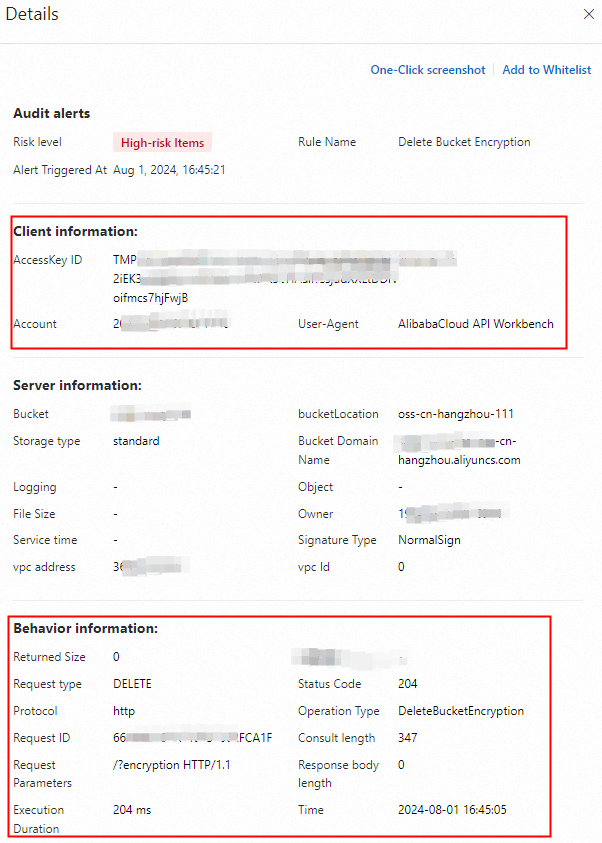
Find an alert and click Details in the Actions column. In the Details panel, you can view the client information, server information, and operation information.
4.3 Confirm and handle alerts
If the sensitive data in the bucket may be leaked due to the deletion of encryption rules, you must handle alerts at the earliest opportunity.
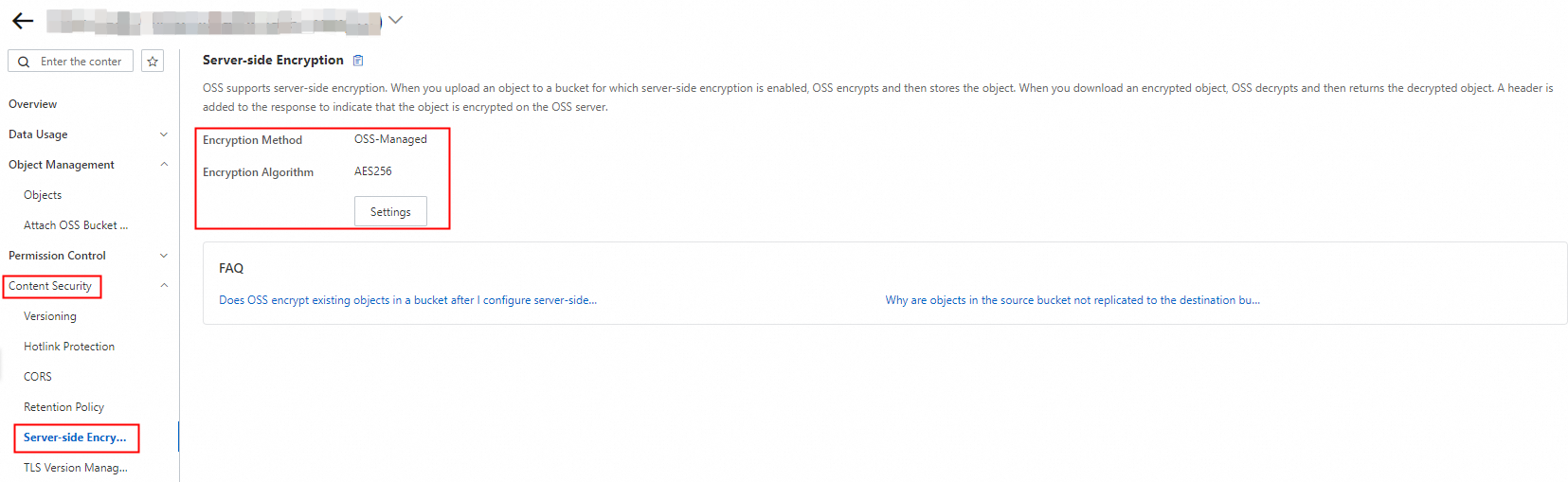
On the Server-side Encryption page of the OSS bucket, configure the Encryption Method and Encryption Algorithm parameters.
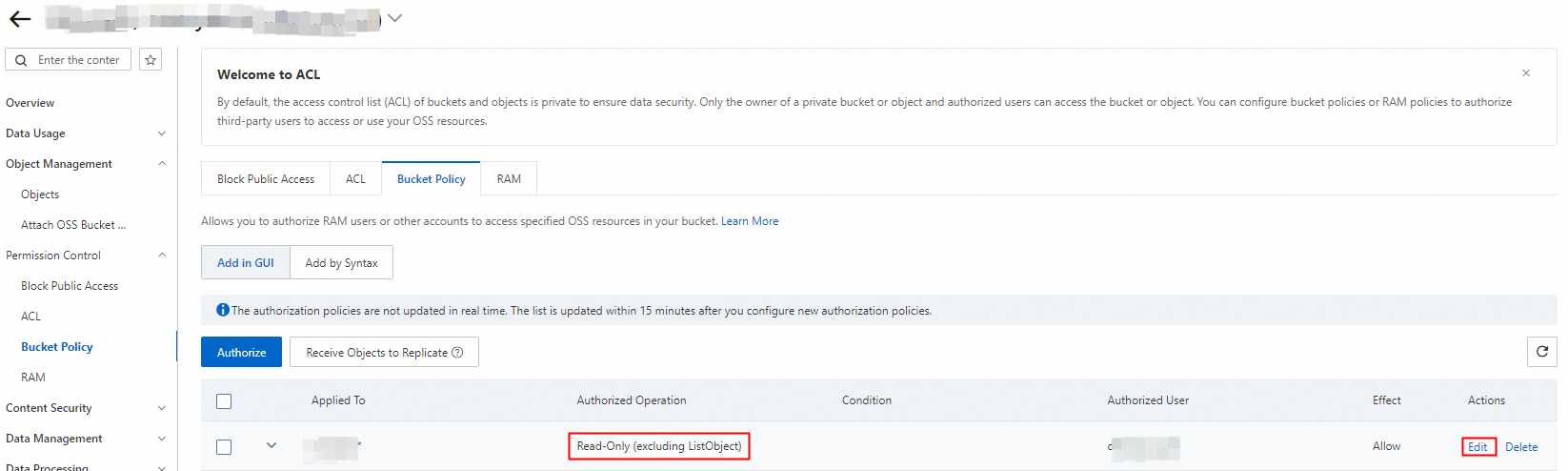
If the permissions are not required by the account, go to the Bucket Policy tab in the OSS console and revoke the permissions from the account. For example, you can grant the read-only permissions to the account.
Summary
DSC can audit the operations of OSS buckets and objects and generate alerts based on enabled alert rules. This helps you identify potential risks at the earliest opportunity and ensure data security.
Audit alert rules
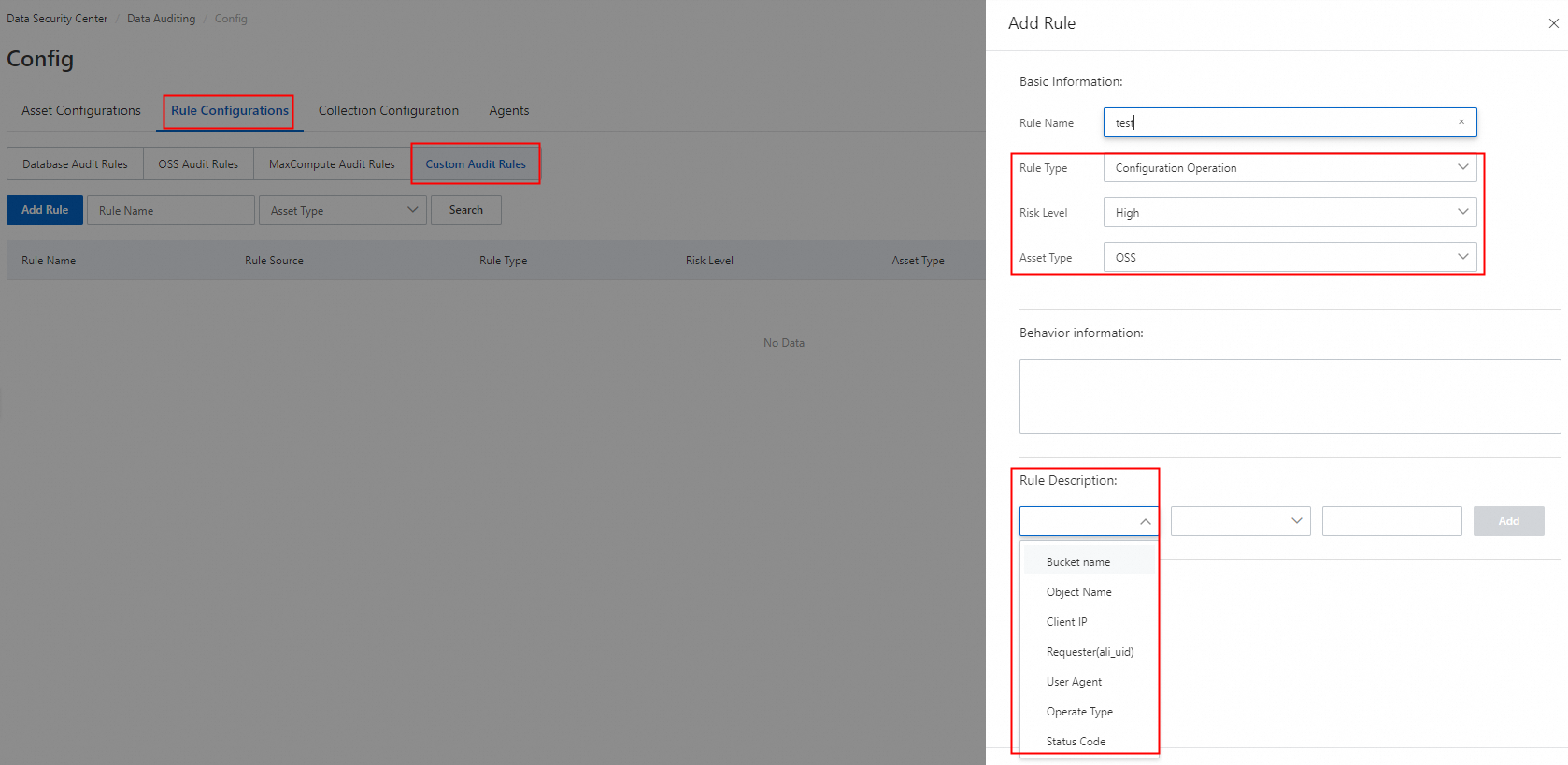
DSC supports the following built-in audit alert rules: Hacker Tools Attack, Put Bucket ACL, Delete Multiple Objects, Put Bucket Encryption, Put Object ACL, Delete Bucket Encryption, and Delete Bucket. DSC also allows you to configure custom audit alert rules by bucket name, object name, client IP address, visitor UID, operation type, and status code.
You can enable audit alert rules based on your scenario and application type. This helps you control OSS bucket access and modification in a fine-grained manner. For more information, see Configure and enable an audit alert rule.
Flexible alert notification methods
DSC supports alert notifications by email and DingTalk chatbot. You can select an alert notification method that allows relevant personnel to receive audit alert notifications in a timely manner. For more information, see Configure email, text message, and phone alert notifications and Configure custom DingTalk chatbot alert notifications.

Audit log analysis
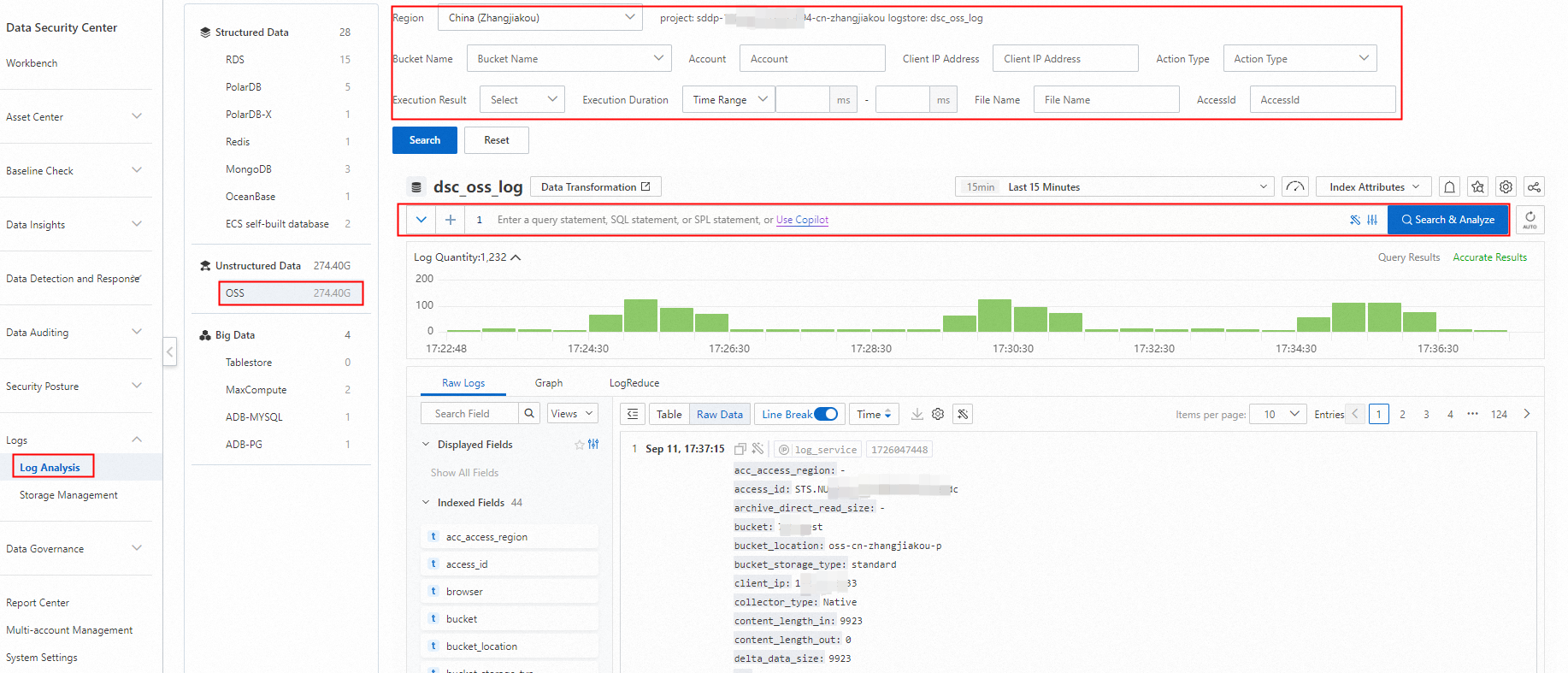
Audit logs record the details of OSS bucket operations. You can view audit logs to track potential malicious behavior or unauthorized access to OSS buckets and objects and analyze the causes of security events. For more information, see View audit logs.
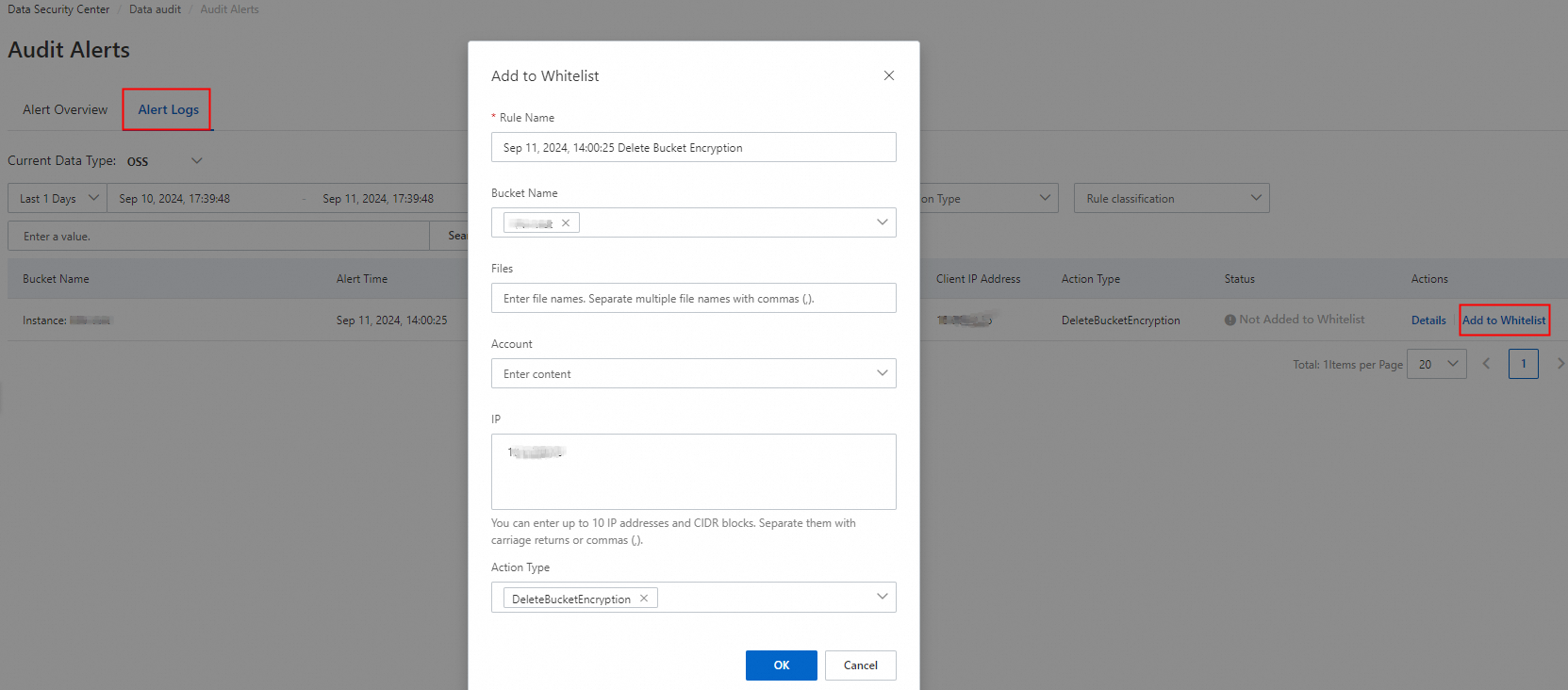
Whitelist management
If an audit alert is not associated with data leaks, you can add the information about the audit alert to the whitelist. In this case, DSC no longer reports alerts or sends notifications of OSS operations or events that fall under the whitelist.
On the Audit Alerts page in the DSC console, find the alert that you want to manage for an OSS bucket and click Add to Whitelist in the Actions column. You can specify the bucket, object, account, IP address, and operation type.
The free edition of DSC does not support the whitelist management feature. To use this feature, you must purchase DSC Enterprise Edition.