DataWorks supports mappings between the built-in or custom workspace-level roles of a workspace and the roles of a MaxCompute compute engine instance associated with the workspace. After you assign a workspace-level role to a RAM user, the RAM user is automatically granted the permissions of the mapped role of the MaxCompute compute engine instance in the development environment. By default, the RAM user does not have permissions on the MaxCompute compute engine instance in the production environment. This topic describes the permissions of built-in workspace-level roles on a MaxCompute compute engine instance and background information about permission management for a MaxCompute compute engine instance. This topic also describes how to use workspace-level roles to grant permissions on a MaxCompute compute engine instance to a RAM user.
Background information
DataWorks provides built-in workspace-level roles and allows you to create custom workspace-level roles. You can assign a workspace-level role to a user to control the permissions of the user on a specific workspace-level service and a MaxCompute compute engine instance in the development environment. A user with a built-in workspace-level role has the permissions of the automatically mapped role of an associated MaxCompute compute engine instance in the development environment. A user with a custom workspace-level role has the permissions of the manually mapped role of an associated MaxCompute compute engine instance in the development environment.
- An Alibaba Cloud account has the highest permissions on its resources. In this topic, permission management operations are performed for a RAM user.
- Only RAM users to which the Development or Workspace Manager role is assigned can create nodes and execute statements to create tables on the DataStudio page.
Overview
| No. | Aim | References |
|---|---|---|
| 1 | Understand the basic information of built-in workspace-level roles of DataWorks. | |
| 2 | Understand how workspace members can obtain permissions on MaxCompute compute engine instances. | Grant permissions on a MaxCompute compute engine instance to a RAM user |
| 3 | Understand the operations that a workspace administrator can perform to manage permissions on a MaxCompute compute engine instance in the production environment. | Procedure for requesting permissions on a MaxCompute compute engine instance in Security Center |
| 4 | Understand how to execute statements to query permissions on a MaxCompute compute engine instance. | Query permissions of users on a MaxCompute compute engine instance |
Precautions
- For a workspace in standard mode, RAM users who are added to the workspace as members do not have permissions on the MaxCompute compute engine instance in the production environment by default. If you want to query MaxCompute tables in the production environment as a RAM user, you must request the required permissions for the RAM user in Security Center. For more information, see MaxCompute data access control.
- For a workspace in basic mode, RAM users who are added to the workspace have permissions on the MaxCompute compute engine instance in the production environment by default. In this case, permissions on data in the MaxCompute compute engine instance cannot be managed.
Permissions of built-in workspace-level roles on a MaxCompute compute engine instance
| Permission | Description |
|---|---|
| Permissions on a MaxCompute compute engine instance in the development environment | DataWorks and MaxCompute use the role-based access control (RBAC) mode to manage permissions. By default, mappings exist between the built-in workspace-level roles of DataWorks and the roles of a MaxCompute compute engine instance. After you assign a built-in workspace-level role to a member in a workspace, the member is automatically granted the permissions of the mapped role of the MaxCompute compute engine instance. |
| Permissions on a MaxCompute compute engine instance in the production environment | By default, RAM users who are added to a workspace as members do not have permissions
on the MaxCompute compute engine instance in the production environment.
All built-in and custom workspace-level roles do not have permissions on the MaxCompute compute engine instance in the production environment. To access MaxCompute tables in the production environment, you must request the required permissions in Security Center. For more information, see MaxCompute data access control. Note Only RAM users to whom the Development or Workspace Manager role is assigned can create
nodes on the DataStudio page and use the nodes to execute statements to create tables.
|
Grant permissions on a MaxCompute compute engine instance to a RAM user
- Obtain permissions on a MaxCompute compute engine instance in the development environment
(automatic authorization):
- After a workspace member is assigned a built-in workspace-level role, the member is automatically granted permissions on a MaxCompute compute engine instance. For more information, see Scenario 1: Grant permissions on a MaxCompute compute engine instance to a user by assigning built-in workspace-level roles.
- After a workspace member is assigned a custom workspace-level role, the member is automatically granted permissions on a MaxCompute compute engine instance. For more information, see Scenario 2: Grant permissions on a MaxCompute compute engine instance to a user by assigning custom workspace-level roles.
- Obtain permissions on a MaxCompute compute engine instance in the production environment
(manual authorization): You must go to Security Center and request the required permissions for the member. The following table describes
the scenarios in which this type of authorization method is required. For information
about how to request permissions in Security Center, see MaxCompute data access control.
Scenario Description You want to access tables in the production environment of a workspace as a RAM user in the development environment. 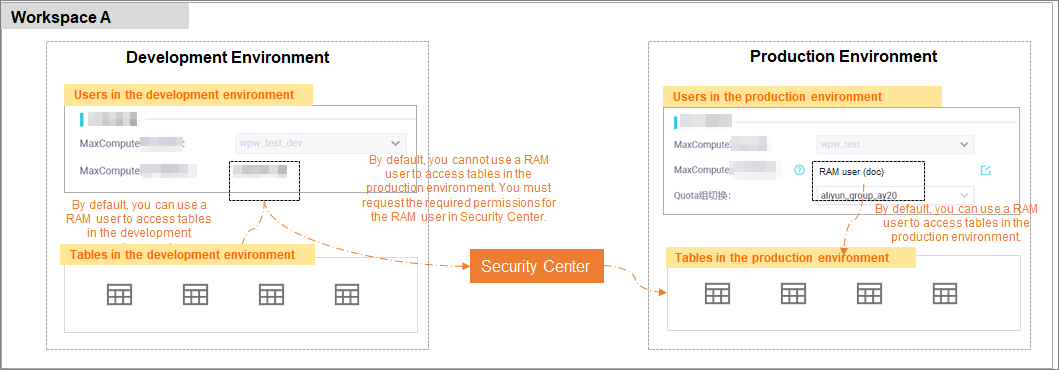
By default, if the RAM user that you want to use is not specified as an identity used to access a MaxCompute compute engine instance in the production environment, you cannot perform operations on tables in the production environment of the workspace on the DataStudio page as the RAM user. To perform operations on the tables on the DataStudio page as the RAM user, you must request the required permissions for the RAM user in Security Center.
You want to access tables in the development or production environment of Workspace B on the DataStudio page of Workspace A as a RAM user in the development or production environment of Workspace A. 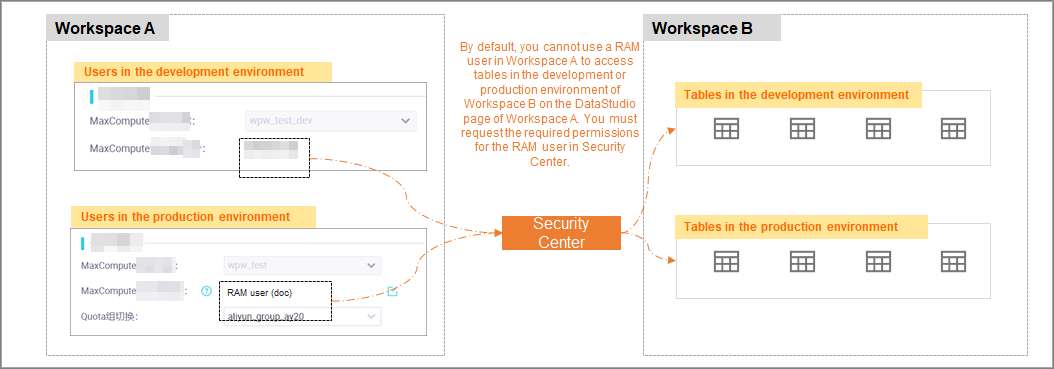
By default, you cannot use a RAM user in Workspace A to access tables in the development or production environment of Workspace B on the DataStudio page of Workspace A. If you want to use a RAM user in Workspace A to access tables in the development or production environment of Workspace B, you must request the required permissions for the RAM user in Security Center.
Procedure for requesting permissions on a MaxCompute compute engine instance in Security Center
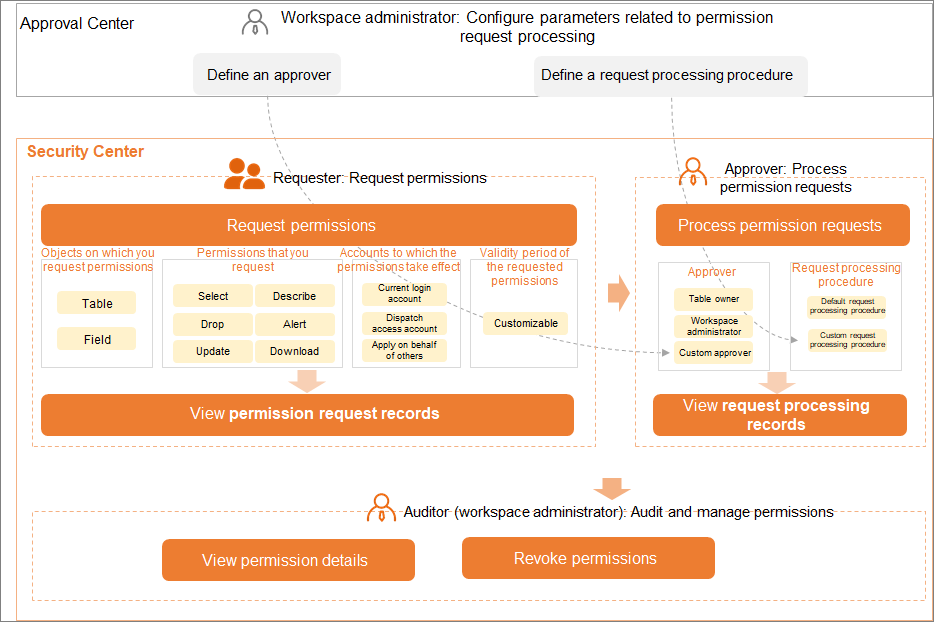
- You can request permissions on tables in the production environment for the RAM user in Security Center.
- Security Center allows you to customize a request processing procedure.
Query permissions of users on a MaxCompute compute engine instance
show grants: queries your access permissions on the MaxCompute compute engine instance.show grants for <username>: queries the access permissions of a specified user on the MaxCompute compute engine instance. You can execute this statement only if you are assigned the Workspace Manager role.
Appendix: Grant permissions on a MaxCompute compute engine instance to a user by assigning workspace-level roles
Scenario 1: Grant permissions on a MaxCompute compute engine instance to a user by assigning built-in workspace-level roles
- Underlying logic: If a RAM user is added to a workspace as a member and assigned a built-in workspace-level role, the member is automatically assigned the mapped role of the MaxCompute compute engine instance associated with the workspace. This way, the member is also granted the permissions of the mapped MaxCompute role. For information about mappings between the built-in workspace-level roles of DataWorks and the roles of a MaxCompute compute engine instance, see Mappings between the built-in workspace-level roles of DataWorks and the roles of MaxCompute.
- Sample scenario: A RAM user is added to a DataWorks workspace as a member by a user
who is assigned the Workspace Manager role, and the RAM user is assigned the built-in
workspace-level role Development.
Note For information about how to add a user to a workspace as a member and grant permissions to the member, see Manage permissions on workspace-level services.
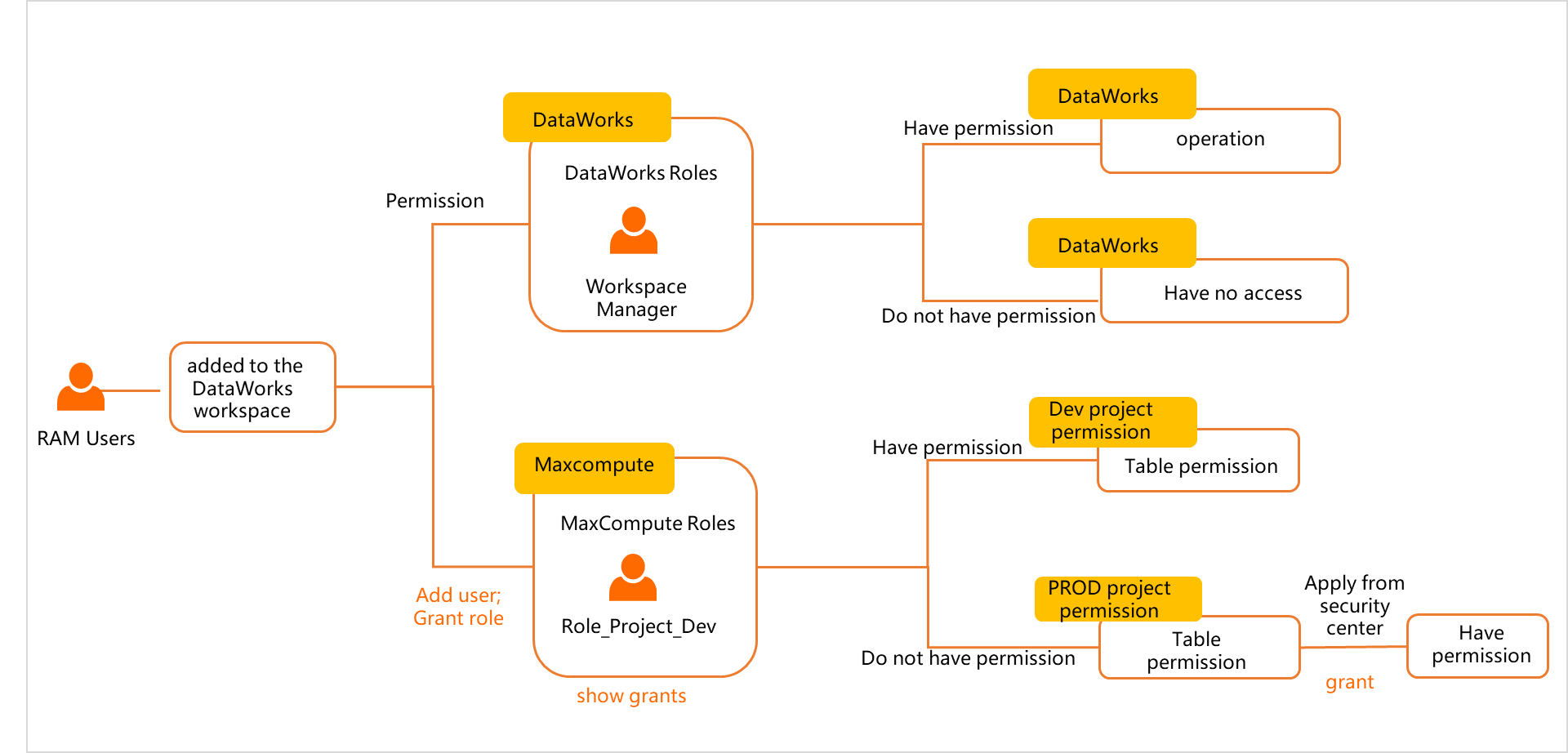
- DataWorks: After the Development role is assigned to the RAM user, the RAM user can develop and commit the code of a node in the workspace but cannot deploy the code of the node to the production environment. Only the Project Owner, Workspace Manager, and O&M roles have permissions to deploy the code of a node to the production environment.
- MaxCompute: After the Development role is assigned to the RAM user, the Role_Project_Dev role of the MaxCompute compute engine instance is assigned to the RAM user. The Role_Project_Dev
role has specified permissions on the MaxCompute project in the development environment
and tables in the project.
Note
- You can assign the Workspace Manager role to a RAM user to grant the RAM user various permissions on DataWorks. However, the RAM user still cannot access tables in the production environment.
- The RAM user refers to a RAM user who is not specified as an identity used to access a MaxCompute project in the production environment.
Scenario 2: Grant permissions on a MaxCompute compute engine instance to a user by assigning custom workspace-level roles
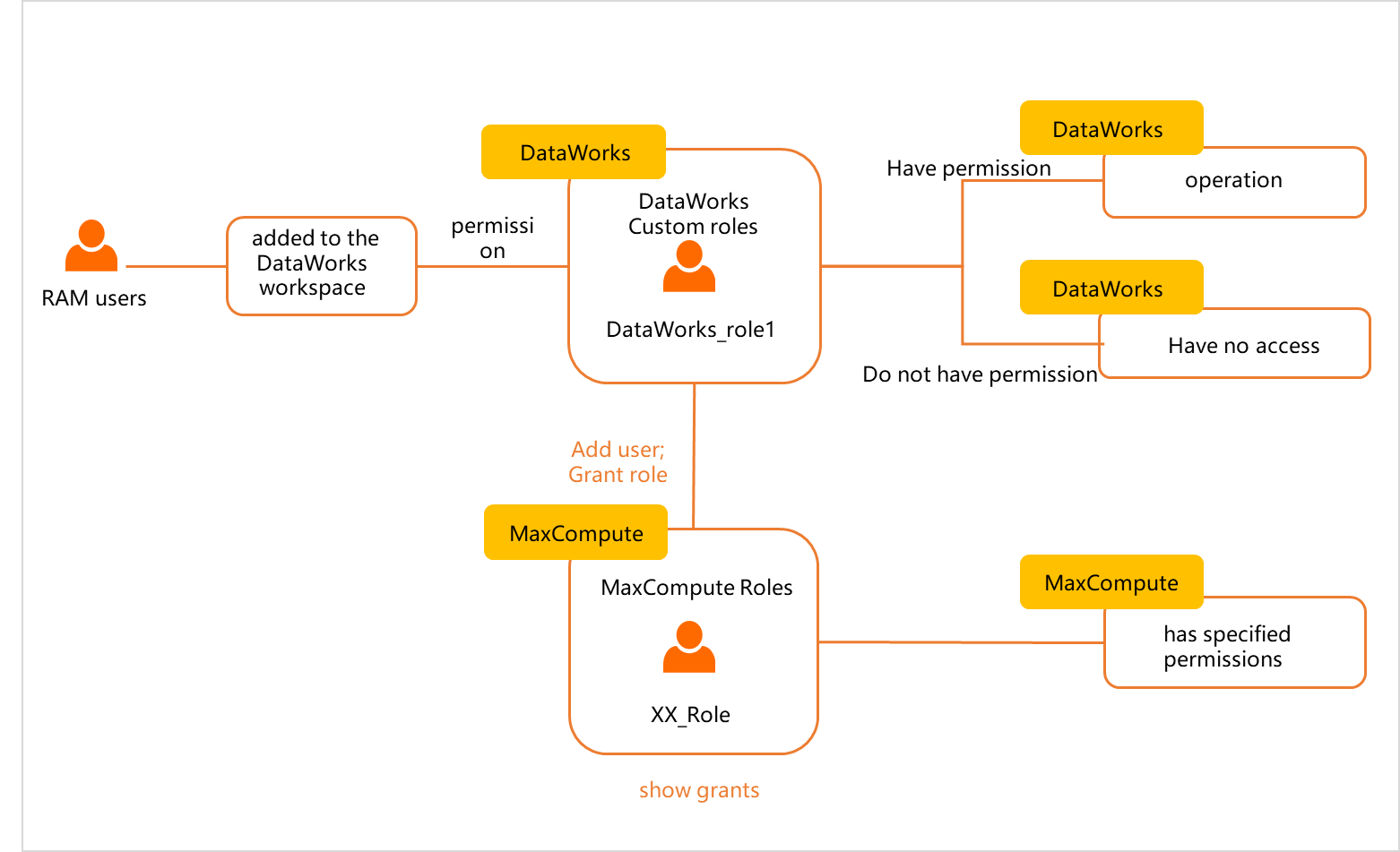 When you create the custom workspace-level role, you can specify whether to map this
role to a role of the MaxCompute compute engine instance associated with the workspace.
After the custom workspace-level role is created, you can assign the role to a RAM
user when you add the RAM user to the workspace as a member. After the custom workspace-level
role is assigned to the RAM user, the RAM user is granted specified permissions on
DataWorks services and the MaxCompute compute engine instance.
When you create the custom workspace-level role, you can specify whether to map this
role to a role of the MaxCompute compute engine instance associated with the workspace.
After the custom workspace-level role is created, you can assign the role to a RAM
user when you add the RAM user to the workspace as a member. After the custom workspace-level
role is assigned to the RAM user, the RAM user is granted specified permissions on
DataWorks services and the MaxCompute compute engine instance.
- DataWorks: After the custom workspace-level role is assigned to the RAM user, the RAM user is granted permissions on the DataWorks services on which the custom workspace-level role can perform operations.
- MaxCompute:
- If the custom workspace-level role is not mapped to a role of the MaxCompute compute engine instance, the RAM user does not have permissions on the MaxCompute compute engine instance. The RAM user cannot query objects in the MaxCompute compute engine instance by running commands.
- If the custom workspace-level role is mapped to a role of the MaxCompute compute engine instance, the RAM user has the permissions of the mapped MaxCompute role.
FAQ
For information about the issues related to permission management for MaxCompute, see FAQ about permission management.
Appendix: Query permissions by using MaxCompute SQL
MaxCompute allows you to query the permissions of a user or role, or the permissions on an object by using MaxCompute SQL. For more information, see Query permissions by using MaxCompute SQL.