Your workload may need to store sensitive information, such as usernames, passwords, and certificates, to connect to a backend database or authenticate client requests. You can use secrets in an Alibaba Cloud Container Compute Service (ACS) cluster to manage this information and prevent it from being exposed. This topic describes how to create a secret in the ACS console and use it as a volume or an environment variable.
Prerequisites
The pod and the secret must be in the same cluster and namespace.
A kubectl client is connected to the cluster. See Obtain a cluster kubeconfig file and use kubectl to connect to the cluster.
Create a secret
This example shows how to create a secret named secret-test.
Log on to the ACS console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its ID. In the left-side navigation pane of the cluster details page, choose .
On the Deployments page, click Create from YAML.
Select a sample template or select Custom. Then, copy the YAML content and click Create.
The following sample YAML template shows how to create a secret.
apiVersion: v1 kind: Secret metadata: name: secret-test type: Opaque data: username: YWRtaW4= # The Base64-encoded value of admin. password: MTIzNDU= # The Base64-encoded value of 12345.
You can also create a secret in the ACS console. For more information, see Create a Secret.
Use a secret as a volume
Use kubectl
You can use a secret as a file in a pod. In this example, the username and password keys from the secret-test secret are saved as files in the /srt directory.
Create a file named example0.yaml and copy the following content into it.
apiVersion: v1 kind: Pod metadata: name: pod0 spec: containers: - name: redis image: redis volumeMounts: - name: srt mountPath: "/srt" readOnly: true volumes: - name: srt secret: secretName: secret-testCreate the pod.
kubectl apply -f example0.yamlVerify that the secret is mounted.
kubectl describe pod pod0 | grep -A 4 VolumesExpected output:
Volumes: srt: Type: Secret (a volume populated by a Secret) SecretName: secret-test Optional: false
Use the console
Log on to the ACS console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its ID. In the left-side navigation pane of the cluster details page, choose .
On the Deployments tab, click Create from Image.
NoteFor more information about the parameters, see Create a stateless application (Deployment).
On the Basic Information step, configure the parameters and click Next.
On the Container step, in the Volume section, click Add Local Storage. Set PV Type to Secret. For Mount Source, select the secret that you created in the Create a secret section. For Container Path, specify the access path in the container. After configuring the parameters, click Next.
The following figure shows a configuration example.
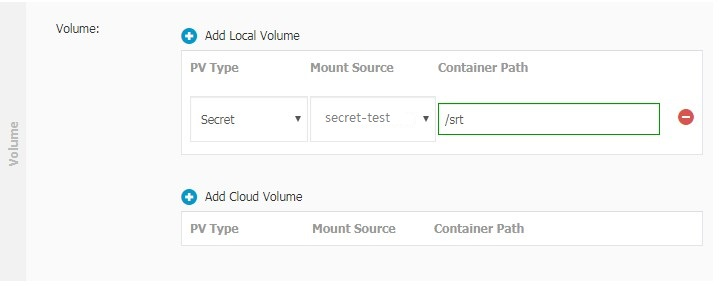
On the Advanced tab, configure the parameters and click Create.
Use a secret as environment variables
You can use either of the following methods.
Use kubectl
This example sets the username and password keys from the secret-test secret as environment variables for the pod.
Create a file named example1.yaml and copy the following content into it.
apiVersion: v1 kind: Pod metadata: name: pod1 spec: containers: - name: redis image: redis env: - name: USERNAME valueFrom: secretKeyRef: name: secret-test key: username - name: PASSWORD valueFrom: secretKeyRef: name: secret-test key: passwordCreate the pod.
kubectl apply -f example1.yamlVerify that the environment variables are configured.
kubectl describe pod pod1 | grep -A 2 EnvironmentExpected output:
Environment: USERNAME: <set to the key 'username' in secret 'secret-test'> Optional: false PASSWORD: <set to the key 'password' in secret 'secret-test'> Optional: false
Use the console
Log on to the ACS console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its ID. In the left-side navigation pane of the cluster details page, choose .
On the Deployments page, click Create from Image.
NoteFor more information, see Create a stateless application (Deployment).
On the Basic Information tab, configure the parameters and click Next.
On the Container tab, in the Environments section, click Add. Set Type to Secrets. For Value/ValueFrom, select the secret that you created in the Create a secret section. Then, select the key to reference and enter a name for the variable.