The authorization system of Container Compute Service (ACS) includes Resource Access Management (RAM) authorization for underlying computing resources and Role-Based Access Control (RBAC) authorization for ACS clusters. Users with different roles require different permissions at these two layers. This topic describes authorization best practices for five types of roles: enterprise resource managers, Kubernetes cluster administrators, cluster and application O&M engineers, application developers, and permission administrators.
ACS authorization system
The authorization system of ACS consists of RAM authorization for computing resources and RBAC authorization for ACS clusters. The following figure shows the ACS authorization system.

RAM authorization involves cluster O&M operations. ACS clusters are a type of Container Service for Kubernetes (ACK) Serverless cluster, and you must call the ACK API to perform O&M operations on ACS clusters. Therefore, you must acquire permissions to call the API operations of ACK and other Alibaba Cloud services. You can call these API operations to perform the following O&M operations:
Create, view, and delete clusters.
Manage RBAC authorization.
Monitor clusters and manage logs and events.
RBAC authorization is used to grant namespace-level or cluster-wide permissions on Kubernetes resources in ACS clusters. This allows you to grant the permissions to create, delete, modify, and view the following types of Kubernetes resources:
Workload resources: such as Deployment, StatefulSet, Job, CronJob, pod, ReplicaSet, and HorizontalPodAutoscaler (HPA).
Network resources: such as Service, Ingress, and NetworkPolicy.
Storage resources: such as persistent volume (PV), persistent volume claim (PVC), and StorageClass.
Namespace, ConfigMap, and Secret.
System default authorization policies
Container Compute Service (ACS) provides the following system authorization policies. You can grant these policies to RAM users or RAM roles to quickly grant permissions.
The authorization scopes of system default policies are large. These policies may grant read or write permissions for all OpenAPI operations of ACK and ACS. Grant these permissions with caution.
System default authorization policy | Authorization policy overview |
AliyunAccFullAccess | Permissions to manage Container Compute Service (ACS). |
AliyunAccReadOnlyAccess | Read-only permissions on Container Compute Service (ACS). |
AliyunCSFullAccess | Permissions to manage Container Service for Kubernetes (ACK). Important Grants read and write permissions on all ACK clusters, including ACS clusters. Grant these permissions with caution. |
AliyunCSReadOnlyAccess | Read-only permissions on Container Service for Kubernetes (ACK). Important Grants read permissions on all ACK clusters, including ACS clusters. Grant these permissions with caution. |
AliyunAccFullAccess authorization policy
{
"Statement": [
{
"Effect": "Allow",
"Action": "acc:*",
"Resource": "*"
}
],
"Version": "1"
}AliyunAccReadOnlyAccess authorization policy
{
"Version": "1",
"Statement": [
{
"Action": [
"acc:Describe*",
"acc:CheckServiceRole"
],
"Resource": "*",
"Effect": "Allow"
}
]
}AliyunCSFullAccess authorization policy
{
"Version": "1",
"Statement": [
{
"Action": "cs:*",
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ram:PassRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"acs:Service": "cs.aliyuncs.com"
}
}
}
]
}AliyunCSReadOnlyAccess authorization policy
{
"Version": "1",
"Statement": [
{
"Action": [
"cs:CheckServiceRole",
"cs:Get*",
"cs:List*",
"cs:Describe*"
],
"Resource": "*",
"Effect": "Allow"
}
]
}Authorization best practices
When a RAM user or RAM role needs to perform cluster and application O&M, you must grant RAM permissions and RBAC permissions to the RAM user or RAM role sequentially. You must grant RAM permissions before you grant RBAC permissions. The authorization operations for three typical scenarios are as follows:
If the authorization object is an O&M engineer for clusters and in-cluster applications, see Scenario 1: Granting permissions to an O&M engineer for clusters and in-cluster applications.
If the authorization object is a developer for in-cluster applications, see Scenario 2: Granting permissions to a developer for in-cluster applications.
If the authorization object is a permission administrator for in-cluster applications, see Scenario 3: Granting permissions to a permission administrator for in-cluster applications.
Scenario 1: Granting permissions to an O&M engineer for clusters and in-cluster applications
The authorization object requires the necessary permissions to manage and maintain ACS clusters and to perform O&M on application resource objects within ACS clusters. Therefore, the authorization process includes both RAM authorization and RBAC authorization.
RAM Authorization
Container Service for Kubernetes (ACK) provides two system policies for RAM: AliyunCSFullAccess and AliyunCSReadOnlyAccess.
AliyunCSFullAccess grants read and write access permissions for all OpenAPI operations of ACK.
AliyunCSReadOnlyAccess grants read-only access permissions for all OpenAPI operations of ACK.
ImportantThese two system policies grant permissions on all ACK clusters, including ACS clusters. Grant these permissions with caution.
Log on to the RAM console and attach one of the system policies as needed. For more information, see Grant permissions to a RAM user and Grant permissions to a RAM role.
If you require fine-grained access control, you can create a custom policy. For more information, see Grant RAM permissions to a RAM user or RAM role.
In this scenario, an example of a RAM authorization policy is as follows.
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": "ecs:DescribePrice", "Effect": "Allow", "Resource": "*" }, { "Action": "ram:GetRole", "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:CreateCluster", "cs:DescribeAddons", "cs:DescribeUserQuota", "cs:DescribeTasks", "cs:ListClusterAddonInstances" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:GetClusters", "cs:DescribeClustersV1", "cs:DescribeClusterUserKubeconfig", "cs:DescribeClusterResources", "cs:DescribeUserQuota", "cs:DescribeClusterLogs", "cs:ModifyCluster", "cs:UpgradeCluster", "cs:GetUpgradeStatus", "cs:ResumeUpgradeCluster", "cs:PauseClusterUpgrade", "cs:CancelClusterUpgrade", "cs:InstallClusterAddons", "cs:UpgradeClusterAddons", "cs:DescribeClusterAddonsUpgradeStatus", "cs:UnInstallClusterAddons", "cs:DeleteCluster", "cs:DescribeClusterDetail", "cs:GetClusterAuditProject", "cs:DescribeClusterAddonsVersion", "cs:DescribeClusterTasks", "cs:DescribeClusterEvents", "cs:DescribeEvents", "cs:ListClusterReportSummary", "cs:GetClusterBasicInfo", "cs:ListReportTaskRule", "cs:CreateReportTaskRule", "cs:CheckControlPlaneLogEnable", "cs:CreateClusterCheck" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/<yourclusterID>" }, { "Action": [ "cs:CheckServiceRole", "cs:DescribeKubernetesVersionMetadata" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/*" }, { "Action": [ "log:ListProject" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses", "vpc:DescribeVSwitches" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }In the preceding example, replace
<yourclusterID>with the ID of your ACS cluster.For more information about the OpenAPI of ACK, see [Product Change] Announcement on the optimization of OpenAPI authentication for Container Service and API overview.
RBAC Authorization
After you grant the RAM permissions, you must also grant the RBAC permissions for the corresponding cluster to the RAM user or RAM role. ACK provides four predefined roles at the cluster level.
Role
In-cluster RBAC permissions
Administrator
Read and write permissions on all resources in all namespaces.
O&M engineer
Read and write permissions on Kubernetes resources that are visible in the console in all namespaces, and read-only permissions on cluster nodes, PVs, namespaces, and quotas.
Developer
Read and write permissions on Kubernetes resources that are visible in the console in all or selected namespaces.
Restricted user
Read-only permissions on Kubernetes resources that are visible in the console in all or selected namespaces.
In the Container Compute Service console, click Authorizations in the navigation pane on the left. On the RAM Users or RAM Roles tab, find the authorization object and click Modify Permissions.
In the dialog box that appears, click Add Permissions, set the permission management for the target cluster and corresponding namespace to O&M Engineer, and then click Submit to complete the configuration.
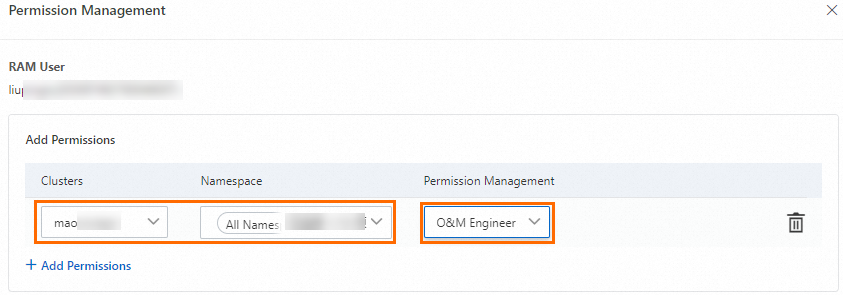
After you attach the predefined role, ACS automatically creates a ClusterRoleBinding instance in the cluster that corresponds to the identity of the authorized object. The RBAC permissions for the predefined O&M engineer role are as follows.
If you require fine-grained RBAC access control, you can create a custom ClusterRole instance. For more information, see RBAC. Then, on the Authorizations page of the Container Compute Service console, select Custom and select the name of the custom ClusterRole from the drop-down list. For more information, see Create a custom RBAC authorization policy.
Scenario 2: Granting permissions to a developer for in-cluster applications
The authorization object requires only permissions to operate on Kubernetes resource objects in an ACS cluster (RBAC authorization) and does not require access permissions to cloud resources.
Before you grant RBAC permissions, the authorization object must have at least read-only permissions for the container service on the target cluster (RAM authorization). If you set the Resource to "*", you grant the RAM user or RAM role the specified Action permissions on all ACK clusters, including ACS clusters. Do not set Resource to "*" unless you fully understand the scope and impact of the authorization and intend to grant full access.
RAM Authorization
In the RAM console, create a custom policy and grant the policy to the target RAM user or RAM role. For more information, see Grant RAM permissions to a RAM user or RAM role. The content of the custom policy is as follows:
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "cs:Get*", "cs:List*", "cs:Check*", "cs:Describe*" ], "Effect": "Allow", "Resource": [ "acs:cs:*:*:cluster/<yourclusterID>" ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }In the preceding example, replace
<yourclusterID>with the ID of your ACS cluster.NoteTo grant the authorization object only read-only permissions on an ACS cluster, you must use this example to specify the ARN of the ACS cluster. Do not grant the
AliyunCSReadOnlyAccessRAM system policy provided by ACK. That policy grants read-only permissions on all ACK clusters and is too broad for this scenario.RBAC Authorization
In the Container Compute Service console, click Authorizations in the navigation pane on the left. On the RAM Users or RAM Roles tab, find the authorization object and click Modify Permissions.
In the dialog box that appears, click Add Permissions, set the permission management for the target cluster and corresponding namespace to Developer, and then click Submit to complete the configuration.
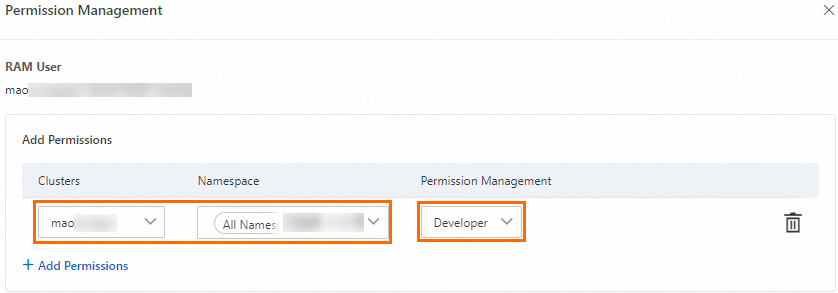
After you attach the predefined role, ACS automatically creates a ClusterRoleBinding instance in the cluster that corresponds to the identity of the authorized object. The RBAC permissions for the predefined developer role are as follows.
Scenario 3: Granting permissions to a permission administrator for in-cluster applications
The authorization object needs to manage the RBAC permissions of other RAM users or RAM roles. By default, a RAM user or RAM role does not have permissions to grant RBAC permissions to other RAM users or RAM roles. When the authorization object navigates to the permission management page in the Container Compute Service console, if the interface displays the message The current RAM user account has no permission to manage authorizations. Contact the Alibaba Cloud account owner or authorized RAM user to request permission, this indicates that the authorization object lacks the necessary RAM permissions or the RBAC administrator permissions for the cluster.
RAM authorization
Ensure that the authorization object is granted the necessary RAM permissions. The policy must include permissions to:
List other RAM users or RAM roles.
Grant RAM authorization policies to specified RAM users or RAM roles.
View the Kubernetes RBAC permission configurations of specified RAM users or RAM roles.
Perform Kubernetes RBAC authorization.
Log on to the RAM console to grant the corresponding RAM permissions to the specified RAM user or RAM role. For more information, see Grant RAM permissions to a RAM user or RAM role. An example of a custom RAM policy is as follows.
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "ram:Get*", "ram:List*", "cs:GetUserPermissions", "cs:GetSubUsers", "cs:GrantPermission", "cs:CheckServiceRole" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "ram:AttachPolicyToUser", "ram:AttachPolicyToRole" ], "Effect": "Allow", "Resource": [ "acs:ram:*:*:policy/xxxx", # Replace xxxx with the name of the RAM policy that you need to attach. If you replace it with *, it indicates that the authorization object has the ability to attach all RAM policies. "acs:*:*:*:user/*" ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }RBAC Authorization
In the Container Compute Service console, click Authorizations in the navigation pane on the left. On the RAM Users or RAM Roles tab, find the authorization object and click Modify Permissions.
In the dialog box that appears, click Add Permissions, set the permission management for the target cluster and corresponding namespace to Administrator or the cluster-admin custom role, and then click Submit to complete the configuration.
NoteAn Alibaba Cloud account (root account) and the cluster creator are bound to the cluster-admin role by default and have access to all Kubernetes resource objects in the cluster.
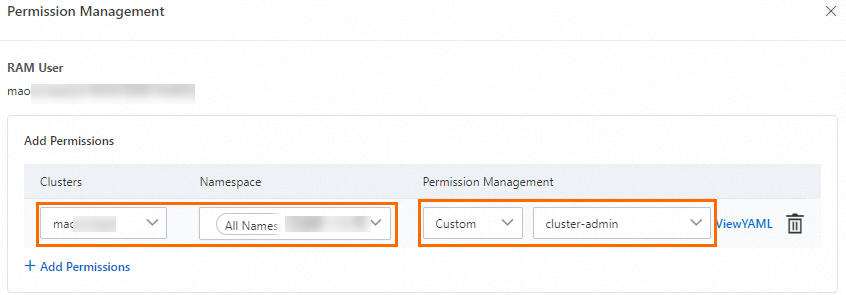
After you grant the preceding RAM and RBAC permissions to the authorization object, the object can manage the RBAC authorization for other RAM users or RAM roles within the specified permission scope. For more information, see Grant RAM permissions to a RAM user or RAM role.
Description of authorization Actions
Permission name (Action) | Description |
acc:CheckServiceRole | Checks whether the account has authorized the product to assume a ServiceRole to access the cloud resources of other accounts. |
acc:DescribeCommodityStatus | Checks whether the ACS product is activated for the account. |
Permission name (Action) | Description |
bssapi:GetPayAsYouGoPrice | Queries the pricing service for pay-as-you-go products. |
ram:ListUserBasicInfos | Queries the basic information of all RAM users. |
ram:ListRoles | Queries the basic information of all RAM roles. |
For a description of the authorization Actions for ACK, see Authorization information.
This topic is for authorization reference only. Before you write authorization rules, make sure that you understand the authorization Actions for ACK and follow the Principle of Least Privilege (PoLP). For more information, see Authorization information.
If you do not specify a target cluster ID and set the authorization scope to "*", you grant permissions to operate on all ACK clusters, excluding ACS clusters. Grant these permissions with caution.