Container Service for Kubernetes (ACK) clusters use security groups to manage traffic between control plane nodes and worker nodes. You can also use security groups to manage traffic between nodes, resources in virtual private clouds (VPCs), and external IP addresses. When you create a cluster or node pool, the system associates the cluster or node pool with a default security group. You can also associate the cluster or node pool with an existing security group. If you associate a cluster or node pool with an existing security group, the system does not configure additional access rules for the security group by default. You need to manually manage security group rules.
You can add security group rules to allow or deny access to or from the Elastic Compute Service (ECS) instances in the security group over the Internet or the internal network. For more information, see Overview and Add a security group rule.
Recommended inbound and outbound rules for the cluster security group
Basic security groups
Inbound
Access control scope | Protocol | Port | Authorization object |
Recommended settings | ICMP | -1/-1 (all ports) | 0.0.0.0/0 |
All protocols | -1/-1 (all ports) |
| |
Least privilege settings | All protocols | 53/53 (DNS) |
|
ICMP | -1/-1 (all ports) | ||
TCP |
| ||
TCP | 9082 | The port used by the Poseidon component. If you do not have this component installed, no configuration is required. | |
All protocols | Ports of applications and components that you want to expose. | The IP addresses or security groups to which you want to expose applications or components. |
Outbound
Access control scope | Protocol | Port | Authorization object |
Recommended settings | All protocols | -1/-1 (all ports) | 0.0.0.0/0 |
Least privilege settings | All protocols | -1/-1 (all ports) | 100.64.0.0/10 (the CIDR block of Alibaba Cloud resources) |
All protocols | 53/53 (DNS) |
| |
TCP |
| ||
All protocols | Ports of applications and components that you want to expose. | The IP addresses or security groups to which you want to expose applications or components. |
Advanced security groups
Inbound
Access control scope | Protocol | Port | Authorization object |
Recommended settings | ICMP | -1/-1 (all ports) | 0.0.0.0/0 |
All protocols | -1/-1 (all ports) |
| |
Least privilege settings | All protocols | 53/53 (DNS) |
|
ICMP | -1/-1 (all ports) | ||
TCP |
| ||
TCP | 9082 | The port used by the Poseidon component. If you do not have this component installed, no configuration is required. | |
All protocols | Ports of applications and components that you want to expose. | The IP addresses or security groups to which you want to expose applications or components. |
Outbound
Access control scope | Protocol | Port | Authorization object |
Recommended settings | All protocols | -1/-1 (all ports) | 0.0.0.0/0 |
Least privilege settings | All protocols | -1/-1 (all ports) | 100.64.0.0/10 (the CIDR block of Alibaba Cloud resources) |
All protocols | 53/53 (DNS) |
| |
TCP |
| ||
All protocols | Ports of applications and components that you want to expose. | The IP addresses or security groups to which you want to expose applications or components. |
Disable deletion protection for a security group
To avoid accidentally deleting security groups associated with ACK clusters, deletion protection is enabled for the security groups that are associated with ACK clusters by default. If the following error message is displayed when you delete a security group in the ECS console, deletion protection is enabled for the security group.
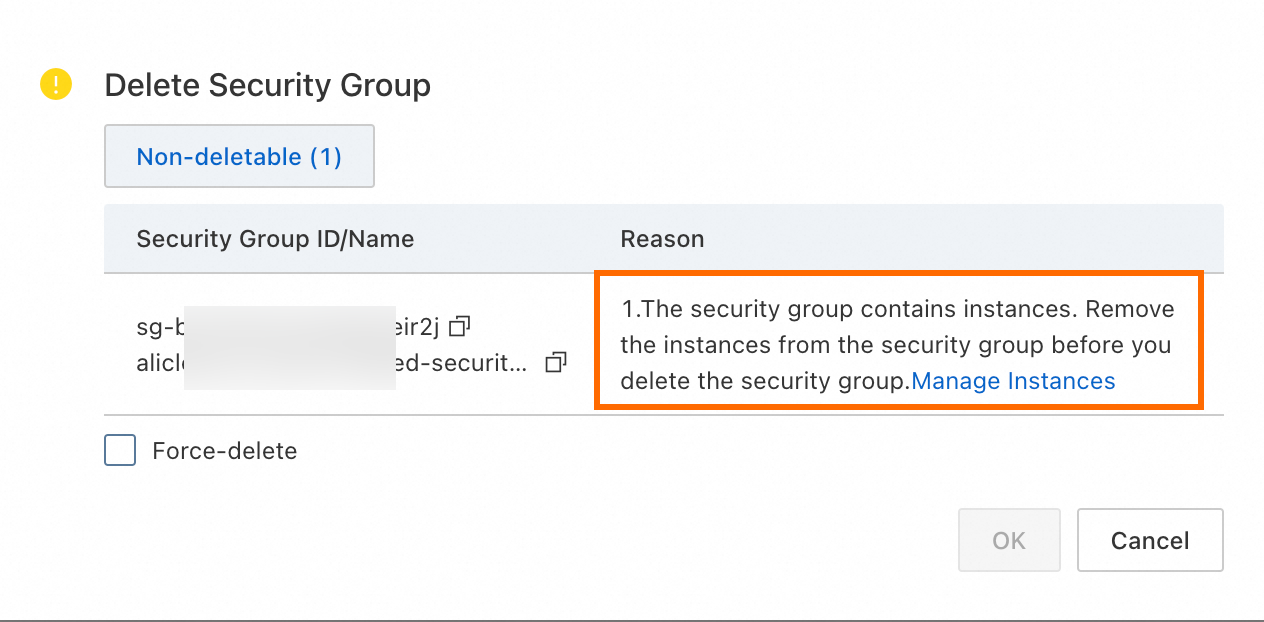
You cannot manually disable deletion protection for security groups in the ECS console or by calling an API operation. After all clusters associated with the security group are deleted, deletion protection is automatically disabled for the security group. To disable deletion protection for a security group, you need to query and delete the clusters associated with the security group in sequence. To query the associated clusters, perform the following steps:
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you created. Click the Basic Information tab to view the security group of the cluster.
After all clusters associated with the security group are deleted, you can delete the security group in the ECS console. If you still cannot delete the security group, submit a ticket to the ACK team.
For more information about how to delete a security group, see Delete a security group.
Related topics
For information about the best practices for network security, such as default allow or deny rules and namespace isolation, see Network security.
For information about how to plan the network of a Kubernetes cluster, such as CIDR blocks of ECS instances, Kubernetes pods, and Services, see Plan CIDR blocks for an ACK cluster.