A Referer blacklist or whitelist is a way of access control based on the Referer header. With this feature, you can protect your resources from unauthorized access. After you configure a Referer blacklist or whitelist, Alibaba Cloud CDN allows or rejects requests based on the Referer header.
Important By default, the feature is not enabled in Alibaba Cloud CDN. This means that all websites can access your resources.
Referer blacklist or whitelist is a method to prevent data transmission abuse.
After you add a domain name to the Referer blacklist or whitelist, the wildcard domain name that matches the domain name is automatically added to the blacklist or whitelist. For example, if you add aliyundoc.com to the Referer blacklist or whitelist, it takes effect for all domain names that match *.aliyundoc.com.
Referer structure
The Referer header is a component of the header section in HTTP requests and contains information about the source address and is used to identify the source of a request. The Referer header consists of the scheme, domain, path, and parameters. The following figure describes the structure of the Referer header.

Note The protocol and domain name are required, and the path and query parameters are optional.
Alibaba Cloud allows you to specify only domain names as Referers by selecting Ignore Scheme.
Scenarios
A Referer blacklist or whitelist is suitable for the following scenarios:
Copyright protection: To safeguard copyrighted content on your website, you can use a Referer blacklist or whitelist to allow only authorized websites to access the content.
Hotlink protection: Referer whitelists or blacklists can prevent your resources from being used by other websites.
Enhanced website security: Only domain names that are included in the Referer whitelist are allowed to access your website resources. This prevents malicious hotlinking or theft of sensitive information.
Traffic source management: You can manage the domains that are authorized to use your resources. This ensures the security and stability of your website.
You can use the feature in different scenarios to protect your website assets, manage traffic, and improve website security.
How it works
The server checks the Referer field of each request and rejects a request if the Referer field in the request does not match the pre-configured whitelist. This helps save bandwidth and server resources. Referer rules in Alibaba Cloud CDN:
If the Referer header in the request is included in the Referer blacklist or is not included in the Referer whitelist, Alibaba Cloud CDN rejects the request.
If the Referer header in the request is included in the Referer whitelist, Alibaba Cloud CDN allows the request.

Usage notes
After you configure Referer blacklists or whitelists, requests from clients in the Referer blacklist can still reach points of presence (POPs). However, POPs reject the requests and return HTTP 403 status code. The requests are recorded in Alibaba Cloud CDN logs.
You are charged for data transfer that is generated when POPs block requests from clients in the blacklist and HTTPS requests if clients request resources over HTTPS.
Data transmission abuse is from Internet access. Therefore, Referer blacklists or whitelists rules apply only to public domain names.
Procedure
Log on to the Alibaba Cloud CDN console.
In the left-side navigation pane, click Domain Names.
On the Domain Names page, find the domain name that you want to manage and click Manage in the Actions column.
In the left-side navigation tree of the domain name, click Access Control.
On the Referer Black/Whitelist tab, click Modify.
Configure the parameters listed in the following table based on your business requirements.
Click OK.
Referer blacklists or whitelists parameters
Parameter | Description |
Type |
Note The whitelist and blacklist are mutually exclusive. You can configure only one of the lists. |
Rules | You can add multiple domain names to the Referer blacklist or whitelist. Separate domain names with carriage return characters. You can use asterisks (*) as wildcards to match all domain names. For example, *.example.com matches all subdomains of example.com. You can also omit the asterisk (*) to match the domain and its all subdomains. For example, example.com matches example.com and *.example.com.
|
Redirect URL | If a request is blocked, HTTP status code 302 and the Location header are returned. This parameter is the value of the Location header. The value must start with http:// or https://, such as http://www.example.com. |
Advanced Settings | Allow resource URL access from browsers | By default, the check box is not selected. If you select the check box, requests that contain an empty Referer header are allowed to access CDN resources, regardless of whether you configure a Referer blacklist or whitelist. An empty Referer header may suggest one of the following scenarios: The Referer header is not included in the requests. The Referer header is included, but the value is empty.
|
Exact Match | By default, the check box is not selected. After you select this check box, you cannot omit the asterisk (*) for matching. If the asterisk (*) is not used, example.com matches only example.com. |
Ignore Scheme | If you do not select Ignore Scheme, the value of the Referer header must start with http:// or https://. If you select Ignore Scheme, the value of the Referer header does not need to start with http:// or https://.
|
Rule Condition | Rule conditions can identify parameters in a request to determine whether a configuration applies to the request. |
Verify the Referer header
The curl command is used to verify the Referer header. -e is followed by the value of the Referer header, and -I is followed by the accelerated domain name. The header information is returned. In this example, the whitelist is used.
Scenario 1: Configure only a Referer blacklist or whitelist rule
Note In this scenario, only a rule aliyun.com is configured. The Redirect URL, Advanced Settings, and Rule Condition parameters are not configured.
Requests whose Referer header contains http(s)://aliyun.com or its subdomains are matched. Requests whose Referer header is not in the whitelist are rejected.
Run the following command to verify a request whose Referer header contains the root domain: curl -e http://aliyun.com -I DomainName
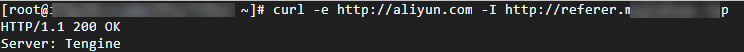
Run the following command to verify a request whose Referer header contains the subdomain: curl -e http://sub.aliyun.com -I DomainName
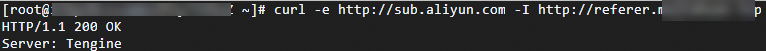
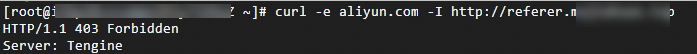
Run the following command to verify a request whose Referer header contains another domain: curl -e http://aIiyun.com -I DomainName
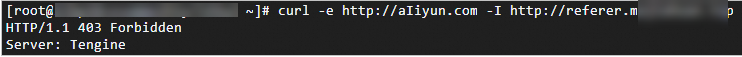
Run the following command to verify a request whose Referer header is empty: curl -e " " -I DomainName
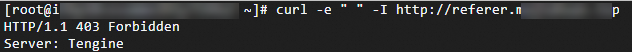
Run the following command to verify the Referer header that contains only the configured domain: curl -e aliyun.com -I DomainName
Scenario 2: Configure a Referer blacklists or whitelists rule and select Allow resource URL access from browsers
Note In this scenario, a rule aliyun.com is configured and Allow resource URL access from browsers is selected. Other options in Advanced Settings are not selected. The Redirect URL and Rule Condition parameters are not configured.
Compared with the scenario 1, requests whose Referer header is empty are matched. This way, requests whose Referer header is empty and direct access requests are allowed.
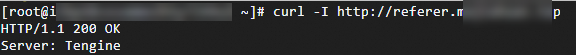
Run the following command to verify a request whose Referer header is empty: curl -I DomainName
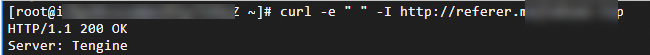
Run the following command to verify a request whose Referer header contains " ": curl -e " " -I DomainName
Scenario 3: Configure a Referer blacklists or whitelists rule and select Ignore Scheme
Note In this scenario, a rule aliyun.com is configured and Ignore Scheme is selected. Other options in Advanced Settings are not selected. The Redirect URL and Rule Condition parameters are not configured.
Compared with the scenario 1, requests whose Referer header does not contain the protocol, such as aliyun.com, are allowed.
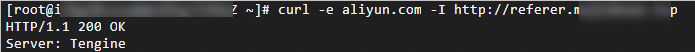
Run the following command to verify a request whose Referer header does not contain the protocol: curl -e aliyun.com -I DomainName
FAQ
Why is the HTTP or HTTPS string occasionally missing in the Referer header in a request?
In most cases, the HTTP or HTTPS string is included in the Referer header in a request.
However, in some cases, when a browser navigates a request from a website that does not use HTTPS to a website that uses HTTPS, the browser may present only the domain name in the Referer header. This is to protect sensitive user data based on security policies such as Referrer-Policy.
In addition, some browsers or proxy servers may automatically exclude the Referer string in specific scenarios, such as access in private browsing mode or by using an anonymous proxy.
Therefore, in actual practice, take note of the scenarios in which HTTP or HTTPS is not included in the Referer header when you configure the feature. If you want to allow requests whose Referer header does not include HTTP or HTTPS, select Ignore Scheme.
Why is the Referer header empty in a request? What do I do to resolve the issue?
In most cases, the Referer header in a request contains the full URI, which includes the protocol, such as http or https, the hostname, and possibly the path and query string. The Referer header in a request may be empty due to the following reasons:
Direct access: If a user enters a URL in the address bar of a browser, uses a bookmark, or opens a new blank browser tab, the Referer header is empty because a referring page does not exist.
User privacy settings: Users configure private browsing mode or use privacy-focused extensions to remove the Referer header out of privacy concerns.
Security protocol: If a request is redirected from an HTTPS page to an HTTP page, the browser does not present the Referer header to prevent leakage of sensitive information.
Client policy: For security purposes, some websites or applications may restrict the browser from sending the Referer header by specifying the <meta> tag or HTTP headers, such as Referrer-Policy.
Cross-origin requests: Specific cross-origin requests may not include the Referer header based on the security policy of the browser.
The handling measures vary with different scenarios and security requirements:
Default policy: If your service does not rely on the Referer header, you can allow requests that have an empty Referer header.
Allow access: For specific URLs or sources, you can select Allow resource URL access from browsers to allow only requests from these URLs or sources. This way, POPs allow users to access your resources regardless of whether the Referer header is empty.









