Database assets are crucial to enterprises. Operations and maintenance (O&M) operations on database assets must be controlled to ensure security. Bastionhost Enterprise Edition and Bastionhost SM Edition support O&M and audit operations on ApsaraDB RDS for MySQL, ApsaraDB RDS for SQL Server, and ApsaraDB RDS for PostgreSQL instances, PolarDB for MySQL, PolarDB for PostgreSQL, and PolarDB for PostgreSQL (Compatible with Oracle) clusters, and self-managed MySQL, SQL Server, PostgreSQL, and Oracle databases. This topic uses specific examples to describe how to perform O&M operations on databases using Bastionhost.
Background information
Enterprise assets include many database assets in addition to Windows servers and Linux servers. Database assets contain a large amount of sensitive data. The key requirements of enterprises are to ensure O&M security and prevent unauthorized access and operations.
The database assets of enterprises are divided into several types, such as ApsaraDB RDS instances and self-managed databases that run MySQL, SQL Server, PostgreSQL, and Oracle. The database assets of large enterprises are also distributed across multiple accounts, virtual private clouds (VPCs), data centers, or heterogeneous clouds. Bastionhost controls O&M operations on assets in the preceding hybrid scenarios and allows O&M security teams to manage the O&M operations in a centralized manner.
Bastionhost Enterprise or SM Edition supports O&M operations on Windows servers, Linux servers, and database assets. The Bastionhost administrator can control O&M permissions on different types of databases. The O&M operations can be traced and audited. This way, database O&M security is ensured. Additionally, the platform provides operational capabilities for hybrid environments. By leveraging its network domain management feature, it allows assets from multi-account, on-premises data centers, and heterogeneous cloud environments to be integrated into a unified platform. This facilitates one-stop management and control for security teams.
Bastionhost Enterprise and SM Edition are built on top of a reliable dual-engine architecture. Both engines are active, which ensures business continuity and meets the high requirements of database O&M. For more information, see Comparison of features between Bastionhost editions.
Process
When using a bastion host for database O&M, an administrator first manages assets and assigns permissions to the O&M personnel through the bastion host. The O&M personnel then establish an SSH tunnel to the bastion host using a client or an O&M portal, and log on to the database assets under the bastion host's control to perform maintenance.
O&M methods and steps
Client-based O&M
Prerequisites
A database and a user are created in Bastionhost, and the user is authorized to access the asset and asset account. For more information, see Create a database, Manage users, and Authorize assets and asset accounts.
This topic uses MySQL and local users as examples.
A database O&M tool that supports SSH tunnels is installed on the local system. For more information about recommended client tools and versions, see Recommended client connection tools and versions.
This topic describes the O&M process using Windows system + Navicat Premium tool and Linux system + command line.
Step 1: Obtain the O&M address of Bastionhost and a database O&M token
Log on to the O&M portal. For more information, see Log on to the O&M portal.
In the navigation pane on the left, click Databases.
On the Databases page, find the target database. In the Remote Connection column, select View O&M Token from the Login Method drop-down list and click Log On.
In the O&M Token dialog box, click Apply For O&M Token (You need to apply for an O&M token for the first login).
When you obtain an O&M token from the O&M portal, if the current database account is not hosted on Bastionhost, you must first configure the basic information of the database account in the O&M Token dialog box. For more information about how to create a database account, see Database management.
O&M tokens must be used within their validity periods. An administrator can set the validity period in the Bastionhost console. If O&M approval is enabled, the validity period that is set by the administrator during the approval process is used.
If an administrator allows O&M users to renew their own tokens, the users can renew the tokens before they expire. After a token expires, the user must request a new one. If O&M approval is enabled, users cannot renew tokens. After token settings are changed, you must request a new token or update the existing one for the new settings to take effect.
If a token is valid but the O&M connection fails, the number of concurrent O&M connections may have reached the upper limit. In this case, contact an administrator to upgrade the instance type of your Bastionhost instance or release idle connections. Another possible reason is that an administrator has blocked O&M requests from your source IP address or during the current time period. In this case, contact the administrator to remove the restrictions.
The audit logs record the user who requested the token, not the username or asset account that is entered in the client.
Step 2: Establish an SSH tunnel by using a client tool or a command line
The following sections describe how to perform O&M operations on database assets through Bastionhost using Navicat Premium and a terminal command line tool.
Navicat Premium
Open Navicat Premium and create a MySQL connection.
On the SSH tab, select SSH Tunnel and configure the information required to log on to Bastionhost (the client SSH tunnel configuration items obtained in Step 1).
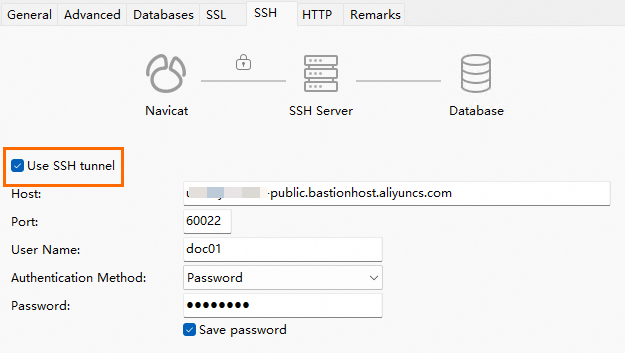
Key parameter
Description
Host
The O&M address of the bastion host, which is the public or private O&M address in the Client SSH Tunnel Configuration section in Step 1.
Port
Enter the O&M port of the bastion host for SSH tunnels. Default value: 60022.
User Name
The username that you use to log on to your bastion host.
Password
Database O&M token, which is used to fill in the O&M token in Step 1 Client SSH Tunnel Configuration.
On the General tab, configure the database information.
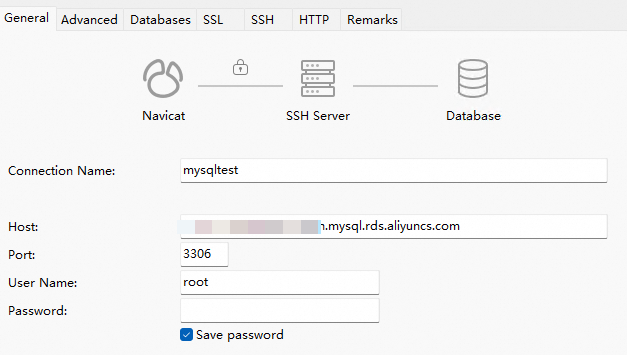
Key parameter
Description
Host
The database endpoint.
User Name
The username of the database account.
Password
If the administrator hosts the username and password of the database account on the bastion host, you can leave this parameter empty.
If the administrator does not host the username and password of the database account on the bastion host, you must enter the password of the database account.
Note We recommend that you save the password. If you do not save the password, the database O&M tool may require you to enter a password. In this case, you can enter the O&M token.
In Navicat Premium, double-click the created database connection. After the connection is established, you can perform O&M operations.
Terminal command line
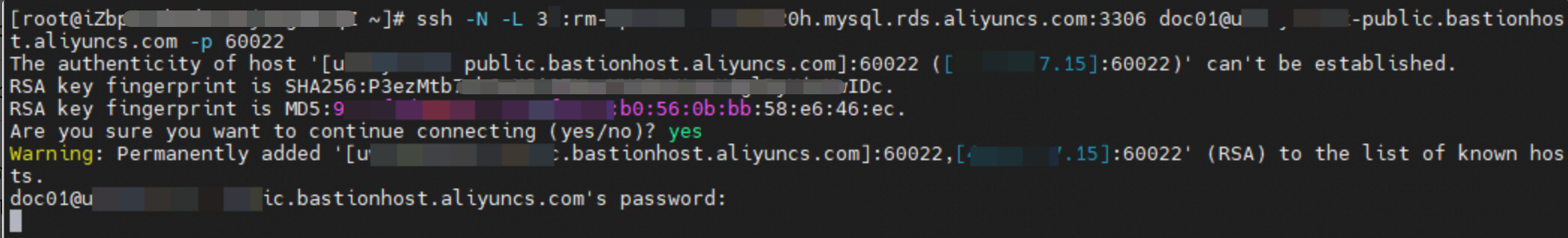
Open the CLI and run the following command:
Syntaxes of commands:
ssh -N -L <localport>:<databaseAddress>:<databasePort> <bastionusername>@<bastionAddress> -p <bastionPort>Parameter description:
Parameter
Description
localport
The custom local listening port that is used after the SSH tunnel is created. Make sure that the local listening port is not occupied.
databaseAddress
The address of the database on which you want to perform O&M operations.
databasePort
The port of the database on which you want to perform O&M operations.
bastionusername
The username of your bastion host.
bastionAddress
The public O&M address of your bastion host.
bastionPort
The O&M port of your bastion host for SSH. Default value: 60022.
Example:
ssh -N -L 33061:rm-******m020h.mysql.rds.aliyuncs.com:3306 bastuser@******-public.bastionhost.aliyuncs.com -p 60022
In the password authentication step, enter the database O&M token and press Enter to wait.
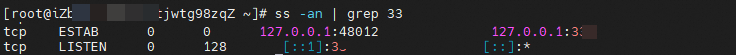
Open another command line and check whether the custom local port is in the listening state. LISTEN indicates that the port is in the listening state.
Run the following command. After you are connected to the database, you can perform O&M operations.
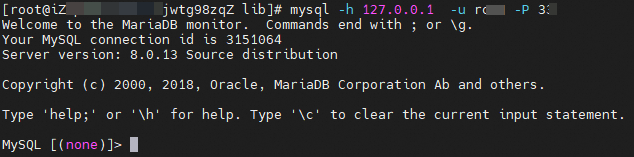
Syntax
mysql -h 127.0.0.1 -u <accountname> -P <localport>Parameter description
accountnameis the username of the database account that you want to use for O&M operations.localportis the custom local listening port that you specified when you connected to Bastionhost.
Web-based O&M
Bastionhost allows you to perform O&M operations on databases through the O&M portal or web console. The following section uses the O&M portal as an example to describe the data O&M process.
Prerequisites
A database and a user are created in Bastionhost, and the user is authorized to access the asset and asset account. For more information, see Create a database, Manage users, and Authorize assets and asset accounts.
This topic uses MySQL and local users as examples.
Procedure
Log on to the O&M portal of Bastionhost. For more information, see Log on to the O&M portal.
In the left-side navigation pane, click Databases.
Find the target database. In the Remote Connection column, select Web Remote Connection as the login method and click Log On.
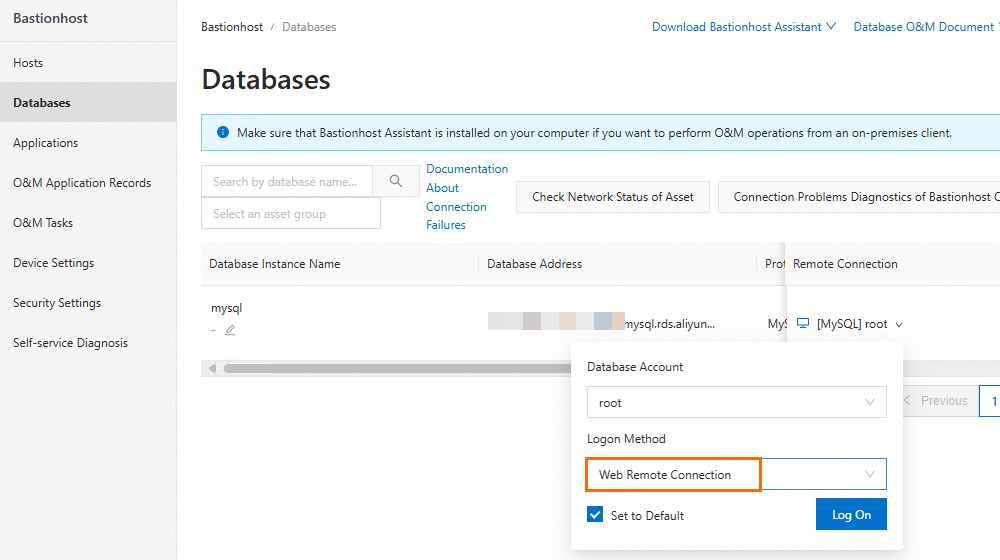
O&M via Single sign-on (SSO)
O&M engineers can use the single sign-on launcher on a web page to automatically call a local client to establish a session. This eliminates the need to separately configure the client. The following section uses the O&M portal of Bastionhost as an example to describe how to use SSO to perform O&M operations on a MySQL database.
Prerequisites
A database and a user are created in Bastionhost, and the user is authorized to access the asset and asset account. For more information, see Create a database, Manage users, and Authorize assets and asset accounts.
This topic uses MySQL and local users as examples.
A client that is supported by the single sign-on launcher is installed on the local system. For more information about supported clients, see Clients supported by the single sign-on launcher.
This topic uses Windows system and Dbeaver 23 as examples.
Step 1: Obtain the O&M portal address
Log on to the Bastionhost console. In the top navigation bar, select the region where your Bastionhost instance is located.
In the list of Bastionhost instances, find the target instance and click Manage.
In the left-side navigation pane, click Overview to obtain the O&M portal address.
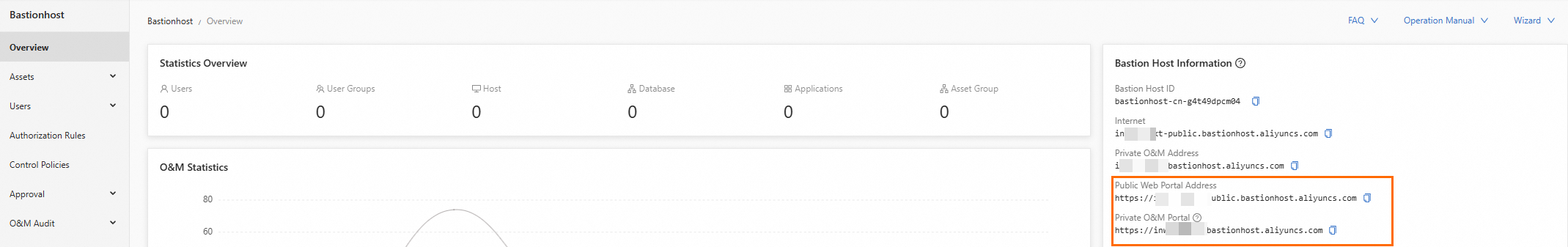
Step 2: Install the single sign-on launcher on the local system
In the address bar of your browser, enter the address of the O&M portal.
On the Alibaba Cloud Bastionhost logon page, enter the username and password of your bastion host and click Log On.
On the O&M portal page, click Download Single Sign-on Launcher.
In this example, the single sign-on launcher for Windows is downloaded.
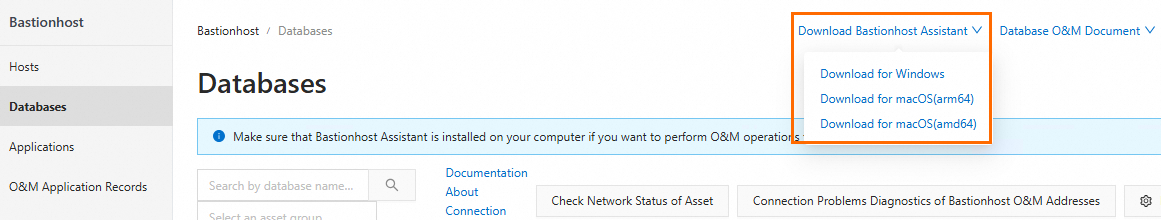
After the download is complete, install the single sign-on launcher (You do not need to open it after installation).
Step 3: Configure the O&M terminal
In the left-side navigation pane of the O&M portal, click Device Settings.
On the MySQL tab, select the Dbeaver client and click Save.
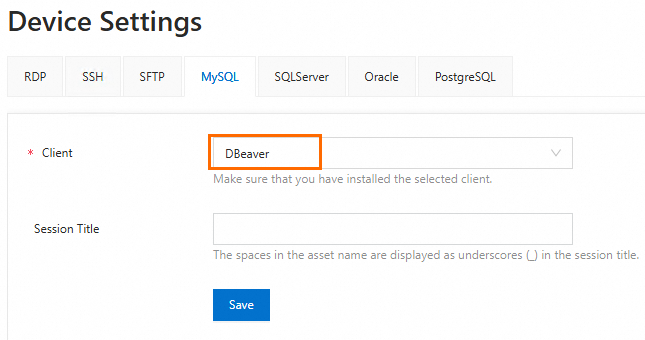
In the usmsso.exe dialog box that appears, click Open and follow the page instructions to configure the client for database O&M.
Step 4: Perform O&M operations on the database
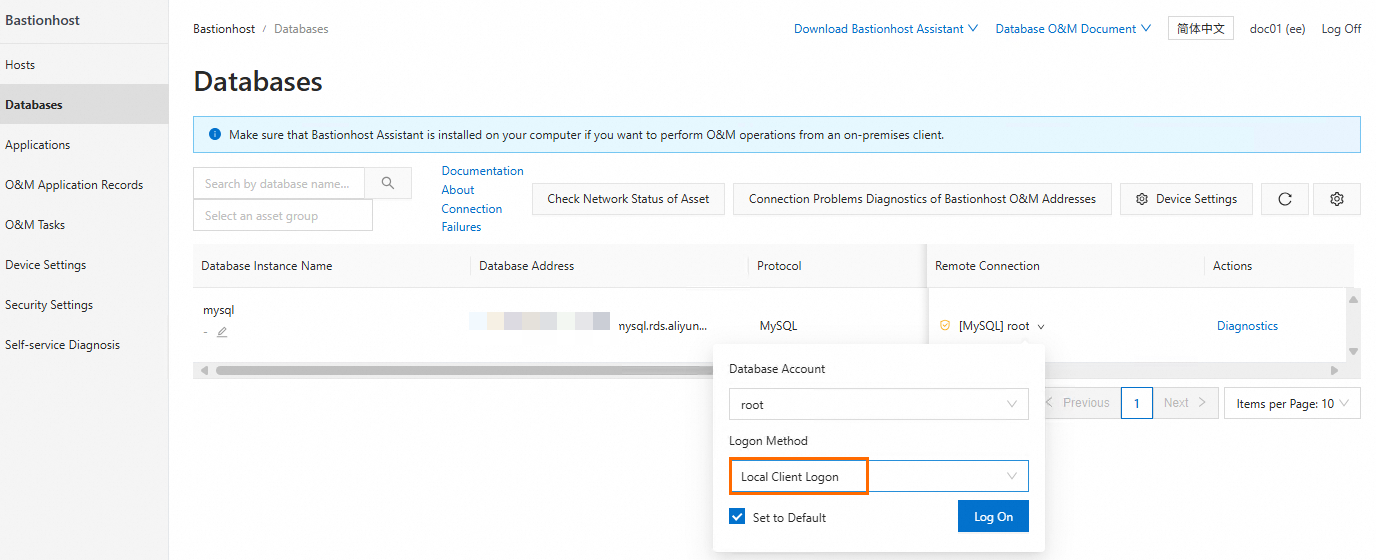
In the left-side navigation pane of the O&M portal, click Databases.
Find the target database. In the Remote Connection column, click the drop-down list, set the login method to Local Client Logon, and click Log On.
Database O&M audit
After O&M engineers use Bastionhost to perform O&M operations on database assets, session records and operation logs are generated. Auditors can view the session records and operation logs to trace O&M operations. Auditors can also monitor sessions in real time to check whether unauthorized operations are performed.
Log on to the Bastionhost console. In the top navigation bar, select the region where your Bastionhost instance is located.
In the list of Bastionhost instances, find the target instance and click Manage.
In the navigation pane on the left, choose .
On the Session Audit page, view the session records.