By Alain Francois
Having your infrastructure on the cloud means you can reach a lot of people worldwide. However, it also means people with bad intentions can reach your services. It is important to secure your cloud network. Alibaba Cloud offers a Virtual Private Network (VPC), which is a secure and isolated private cloud that contains your Elastic Compute Services (ECS) instances within a public cloud. You can access a VPC publicly from the Internet and secure traffic by configuring a security group.
A Virtual Private Cloud (VPC) is a private network that you fully control. You can specify a CIDR block and configure route tables and gateways. You can deploy your Alibaba Cloud resources, such as Elastic Compute Service (ECS) instances or Server Load Balancer (SLB) instances. You can have multiple VPCs to establish some strategies regarding your cloud instances. It means you can create a VPC for web servers and another one for databases servers.
A Security Group can be considered as a virtual firewall that provides stateful packet inspection and packet filtering of network protocol, port, and sources IP traffic to allow or deny access to Elastic Compute Service (ECS) instances to improve security. When creating an ECS instance, you must select a security group because it is an important means of security isolation.
You should think of a security group as a whitelist. When you create security groups, some default rules are added to the security groups by default. You can maintain them or manually add and modify the rules of security groups to implement finer-grained traffic control. Security groups have some characteristics. Each ECS instance must belong to at least one security group but can be added to multiple Security Groups at the same time. There are two classifications for security groups:
Some rules must be also followed when you add instances to security groups:
If you want to create an Alibaba Cloud VPC, you need an Alibaba Cloud account. If you don't have one yet, you can get a coupon during the Alibaba Cloud March Mega Sale.
After logging into your cloud account, go to Virtual Private Cloud on the left panel, click _Networking & CDN_, and click _Virtual Private Network_:
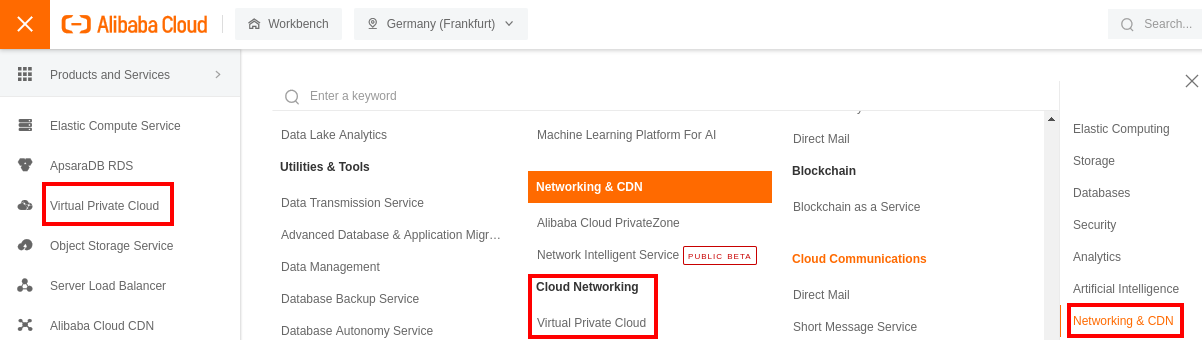
You can see the VPC overview with some created information, such as IPv4 CIDR Block or the num of vSwitch and Cloud Instance on each VPC. Select the appropriate region before creating your VPC:
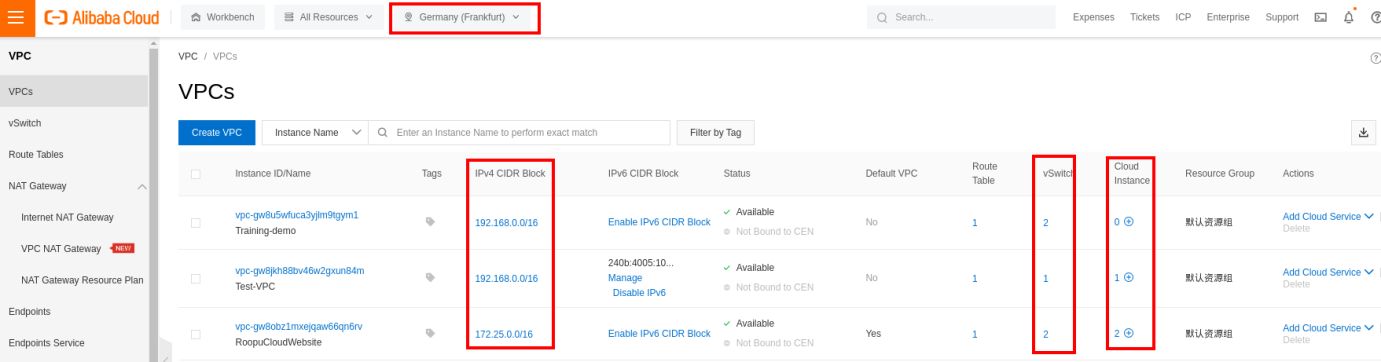
You can create a new VPC. You will need to indicate a name for the VPC and the IPv4 CIDR Block. You can assign an IPv6 or not. As we mentioned previously, when creating a VPC, you will also need to create a vSwitch. During the creation of the vSwitch, you will have to select a zone of your region. If you already have some ECS instances created, make sure to select the zone where they are located if you want them to use the new vSwitch:
You can see the new VPC with the detail on the VPC overview page:
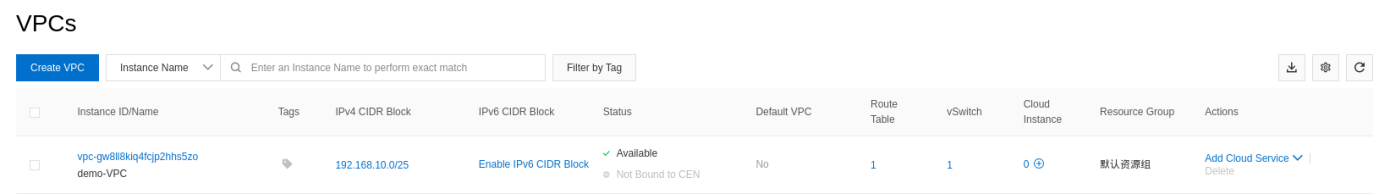
Now your VPC has been created. You can create a security group that you will use to secure your VPC during the creation of your instance.
If you want to create a security group, you should go to the Elastic Compute Service (ECS) panel:
Now, navigate the left panel to Network & Security and click Security Groups
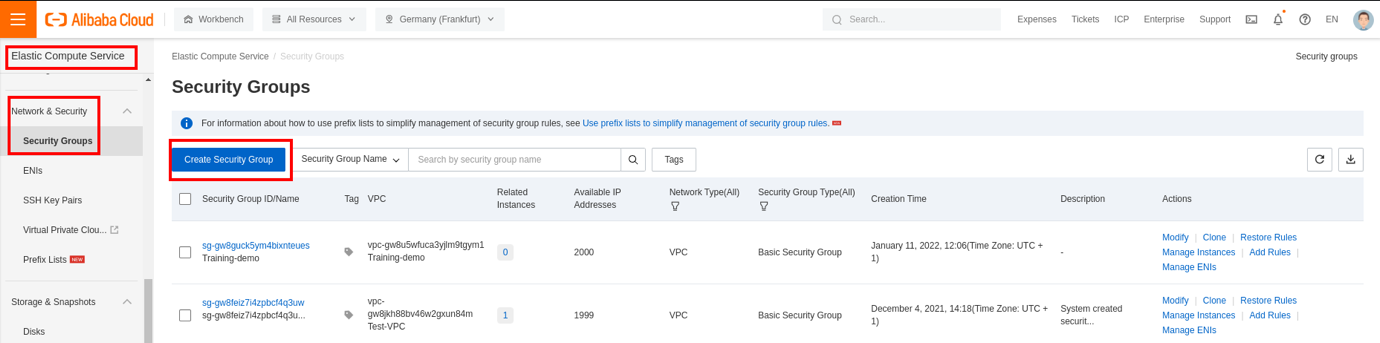
In our case, we already have some security groups created. Let's create a new one by selecting the option. As we have explained in the security group section, there are default rules you can maintain or edit during the creation. Also, a basic security group is created by default:
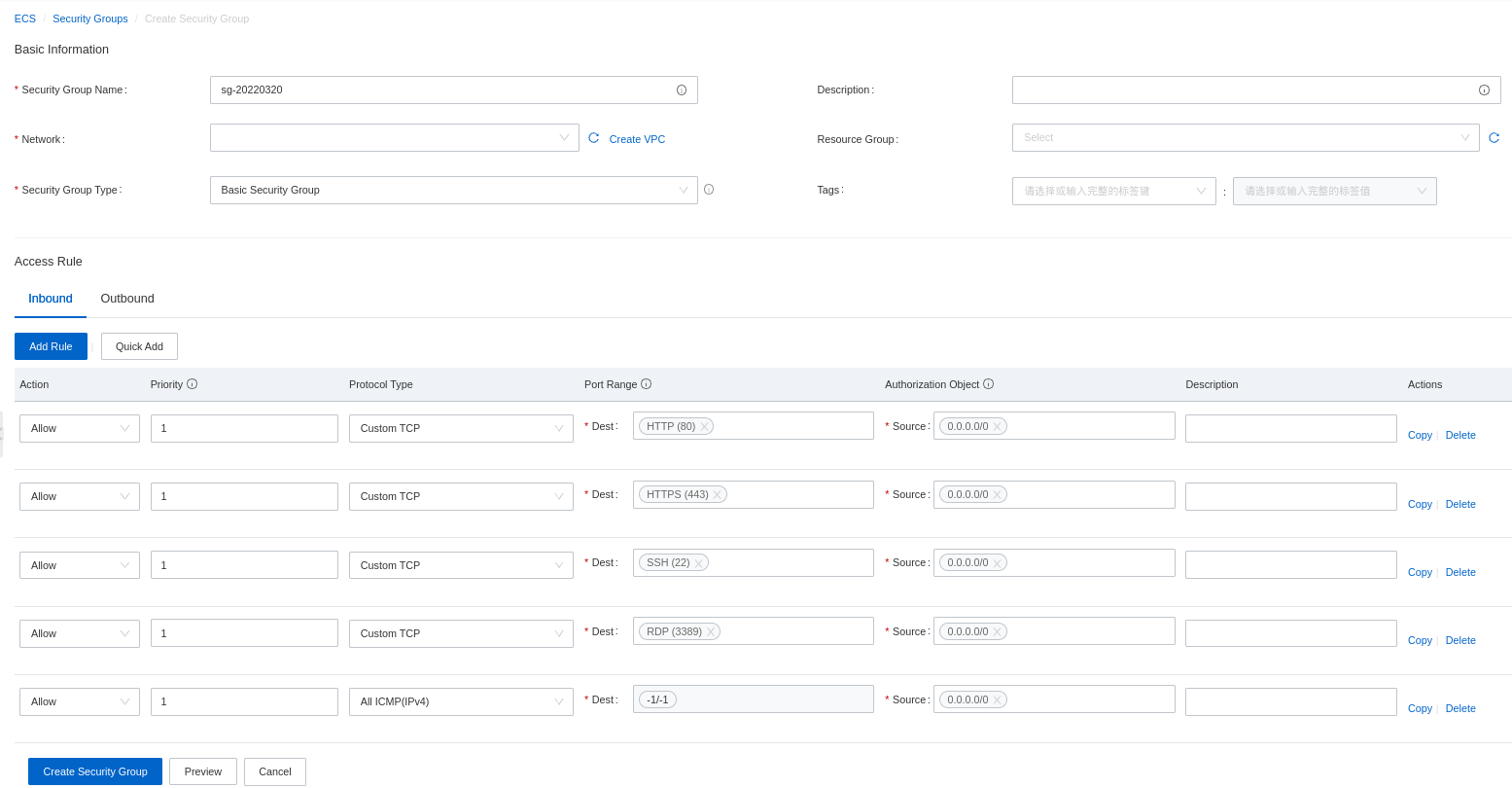
You can change some values like the type of security groups for advanced and the outgoing rules. You should give an indicative name for the security groups and a proper description.
You can create many security groups for some specifics scenario or ECS instances roles. For example, you can create a security group only for web servers that will only allow ports 22, 80, and 443. You can delete rules for ICMP so your instances will not receive any ICMP requests (for ping). Configuring a security group is the moment for you to define the default actions or rules that should be applied to filter the egress and ingress traffic to your ECS instances inside the VPC on which the security groups will be applied. It's the moment to strategically define the default rules, but you can add a specific rule later.
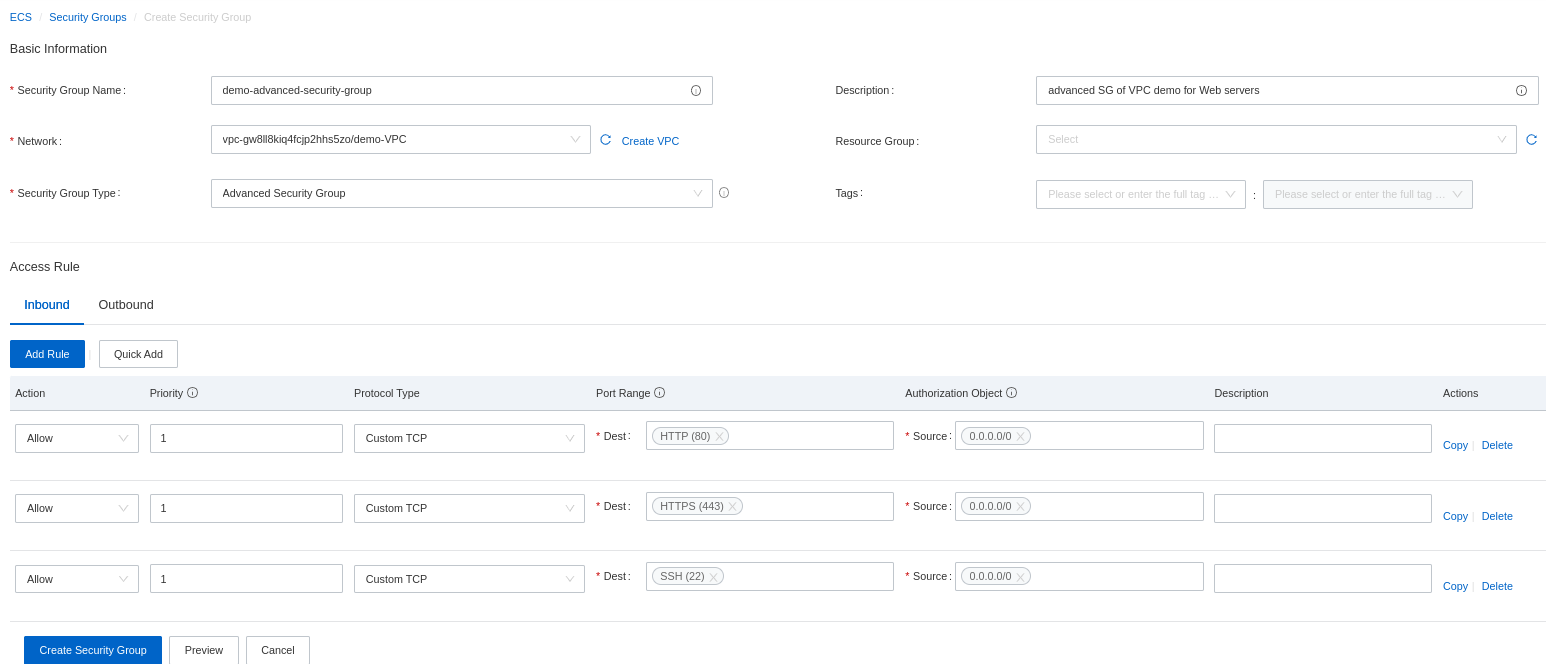
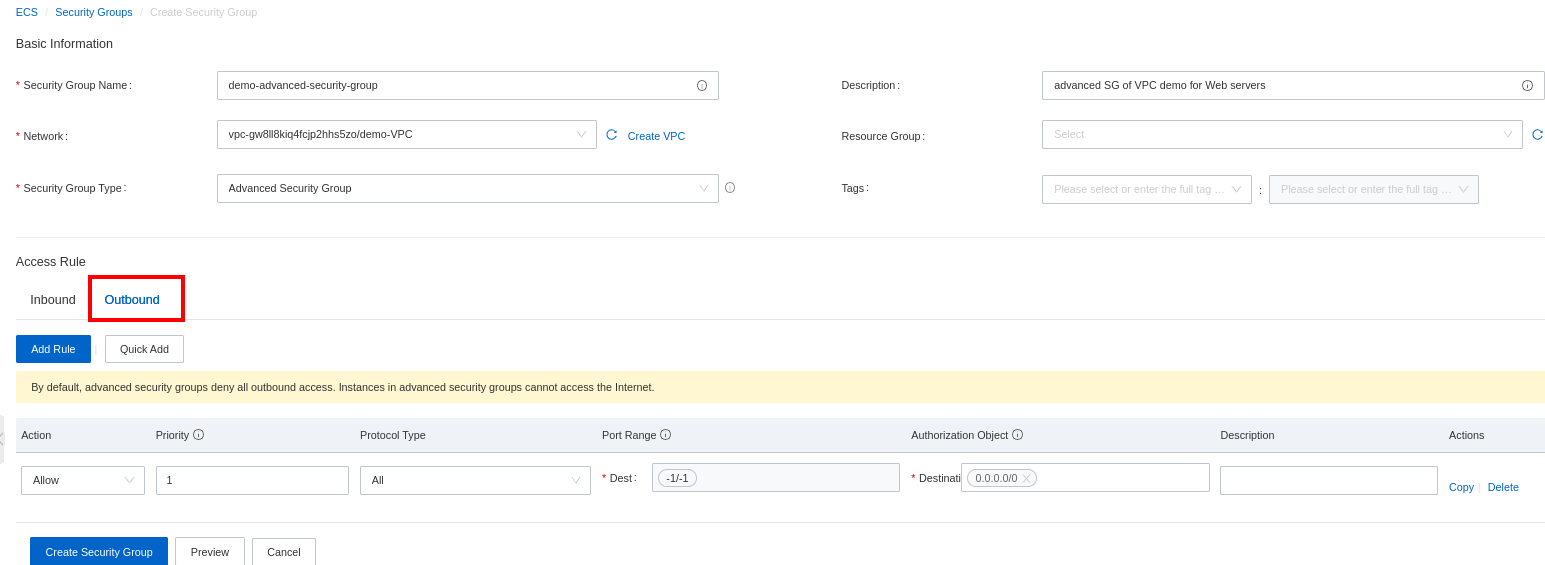
The outbound rules on the security group allow all traffic from your server to the external network by default:
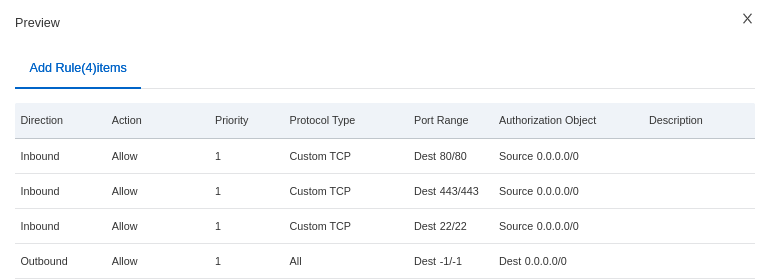
If you have a preview regarding all the rules you have defined:
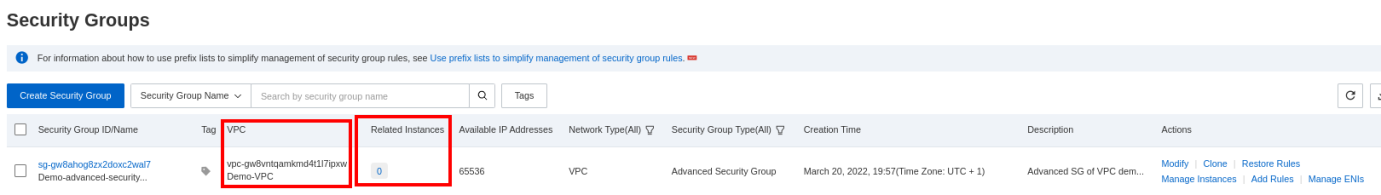
Just validates the creation of your security groups after finishing the configuration. You will see the default security group on the list. There are no ECS instances related to the VPC or the security by default:
We will create a new instance to integrate an ECS instance to the new VPC and security groups created. On the left panel, scroll to Instances & Images and select _Instances_. Then, create a new ECS instance:
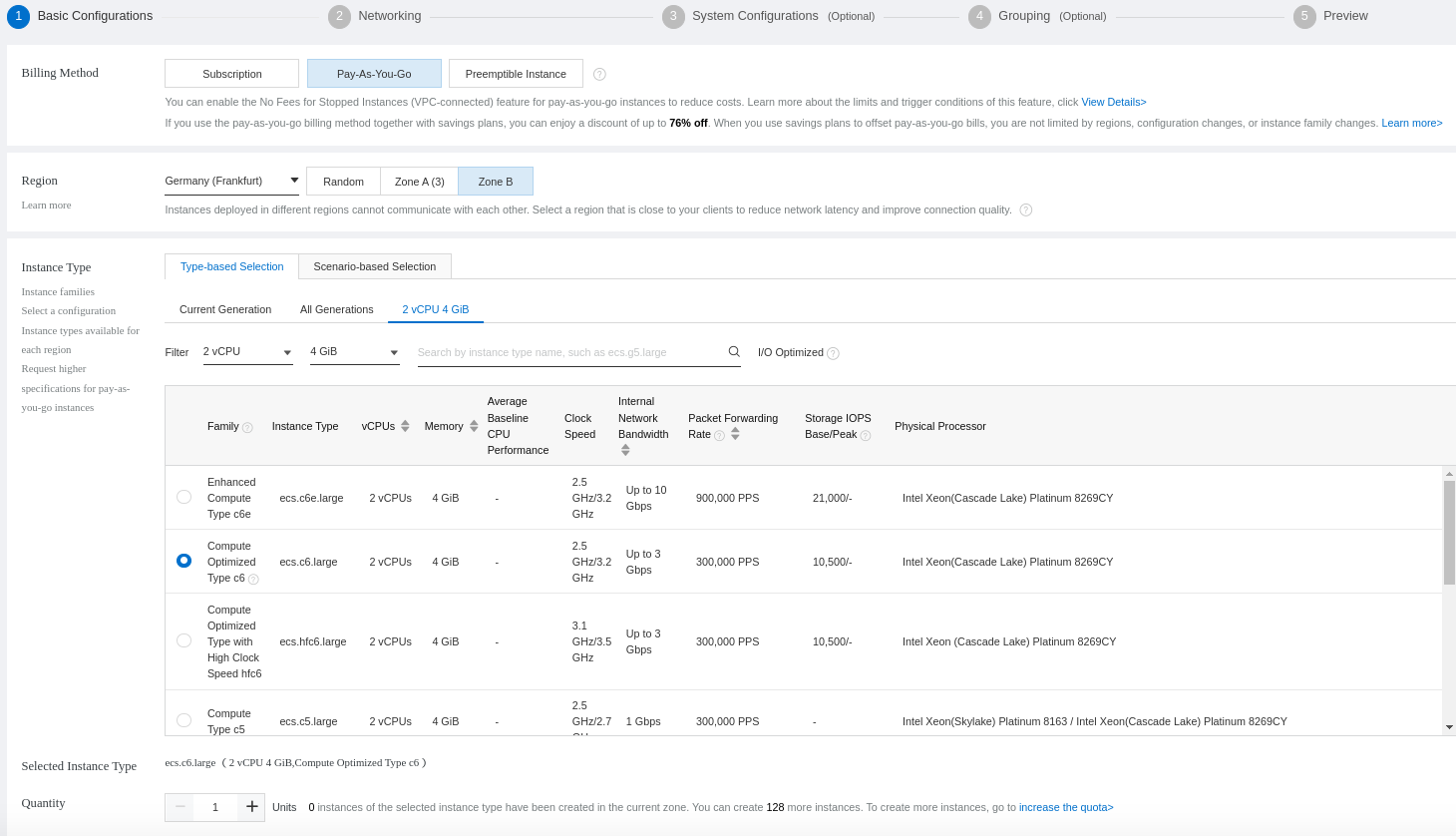
Choose your instance specifications with CPU and memory:
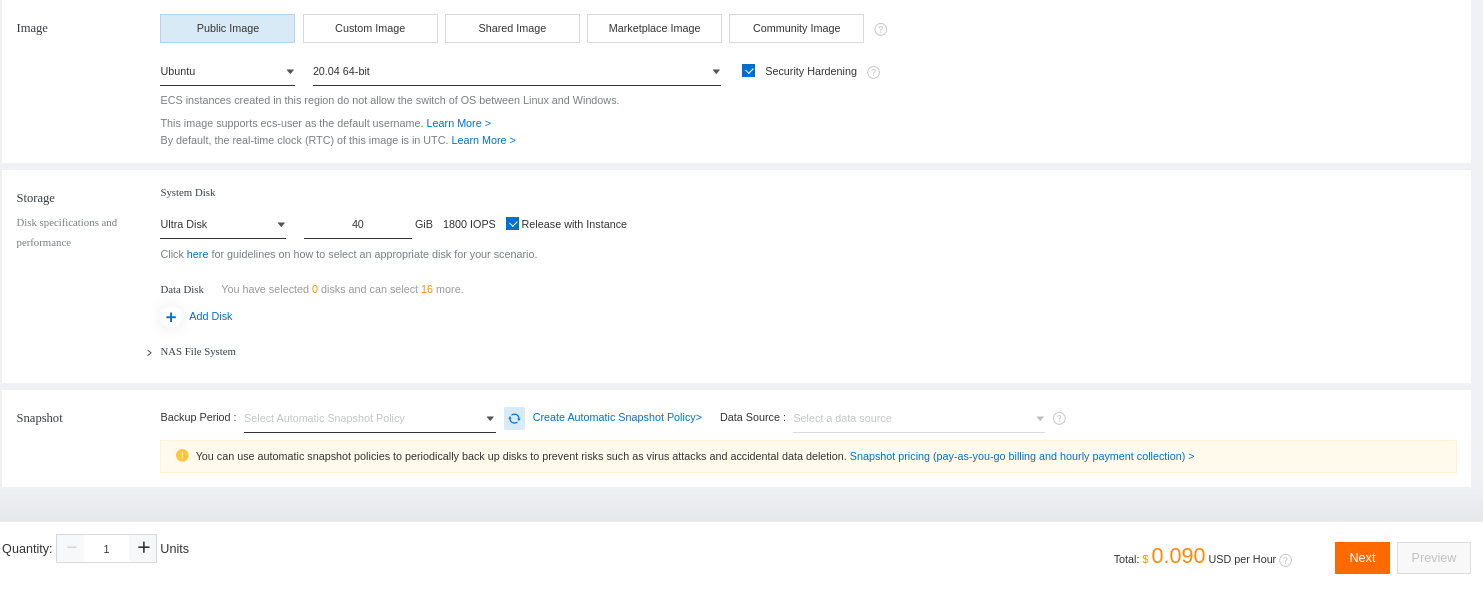
Select the operating system and the disk size:
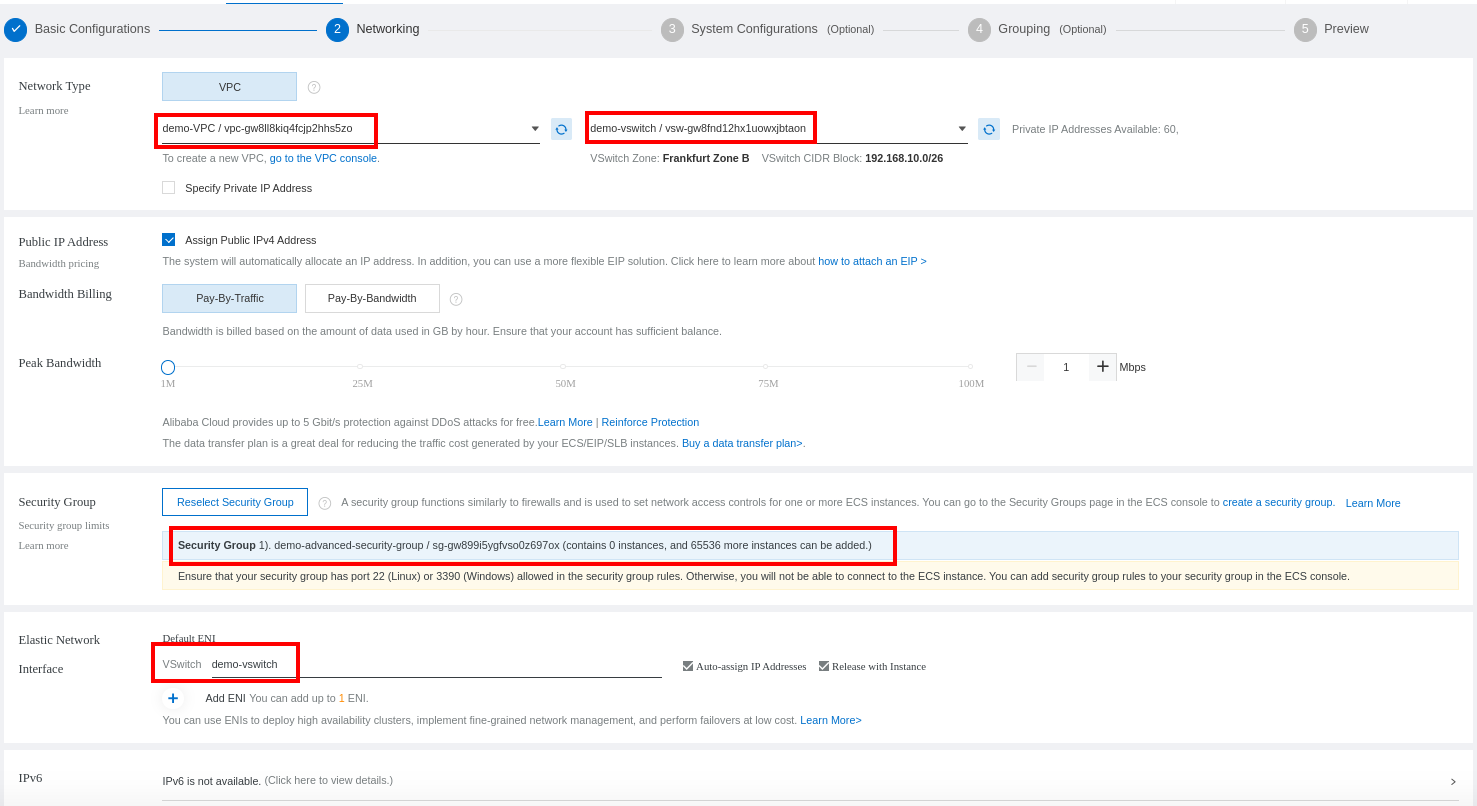
Configure your instance networking. Select the VPC we have created. It will select the vSwitch and the security groups created and linked to the VPC by default:
You need to configure how you will access your ECS (password and public key):
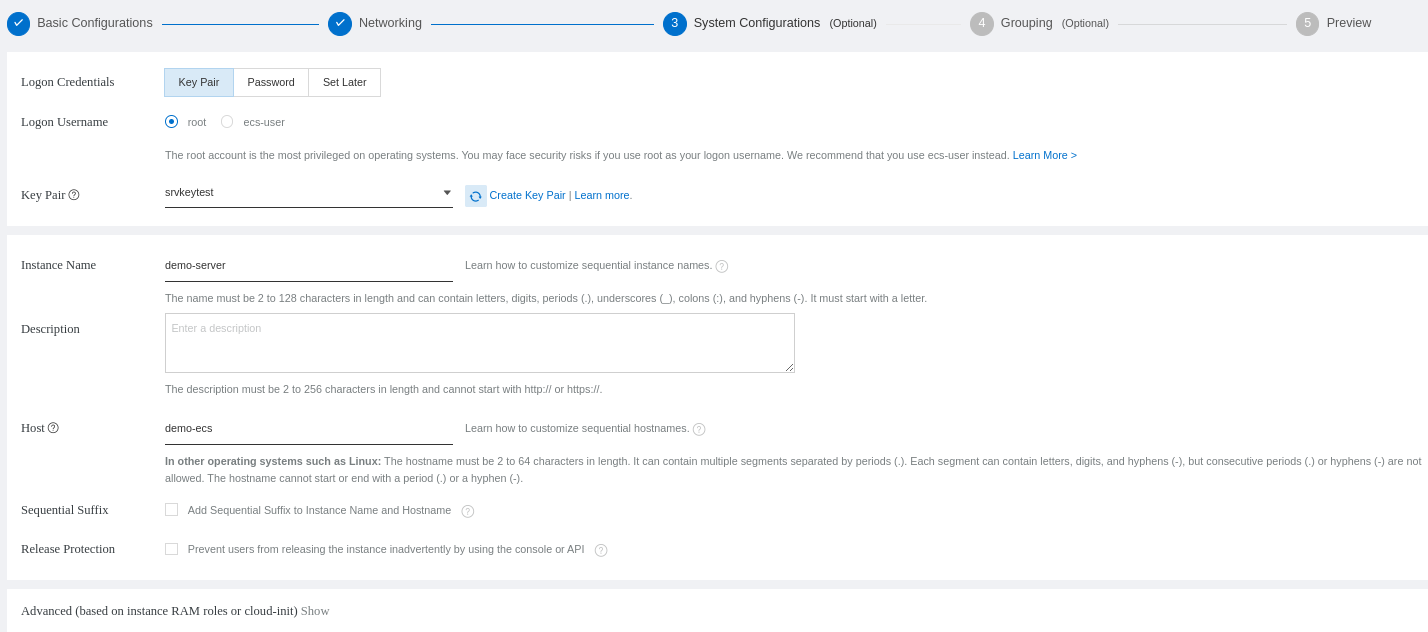
You can go to the next step:
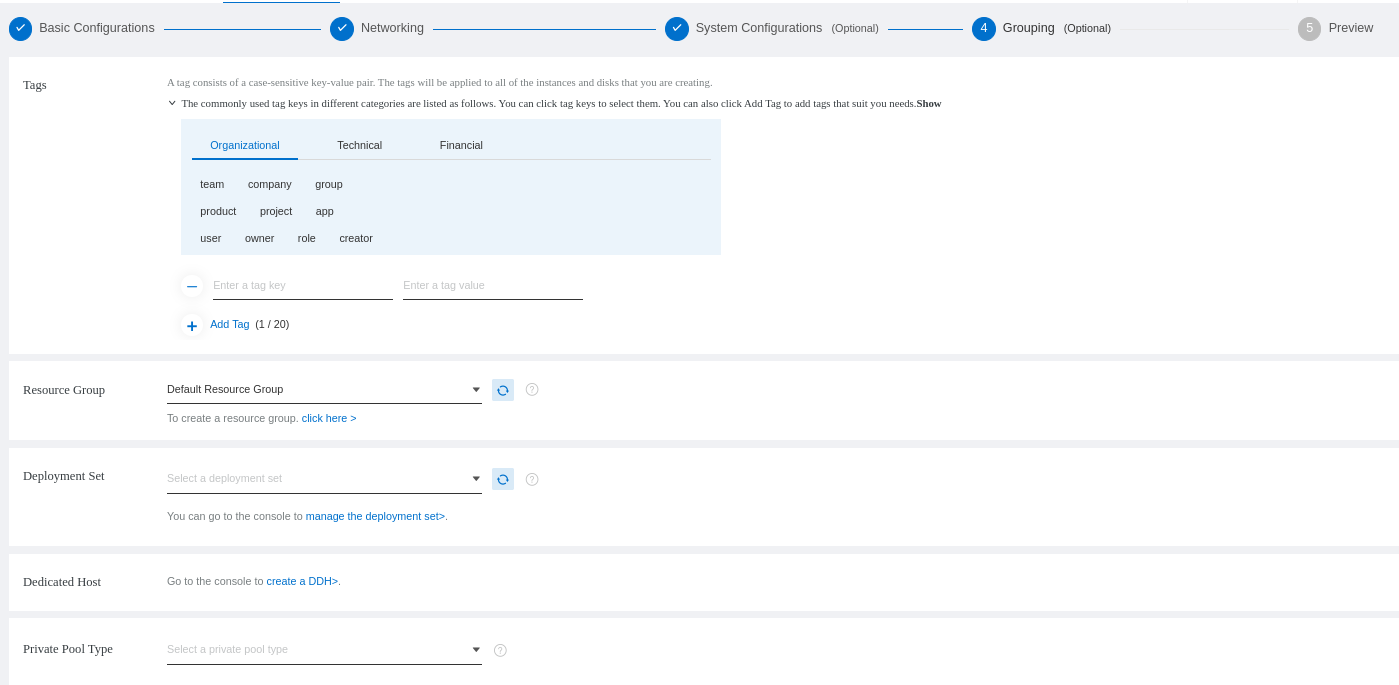
You will see a review of your ECS configuration and order:
You will be asked to return to the console or another page:
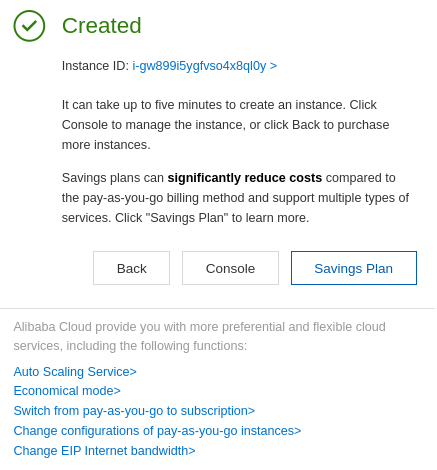
You can return to the list of your ECS instance to see if it has been created. You can see it on the list of your ECS instances:
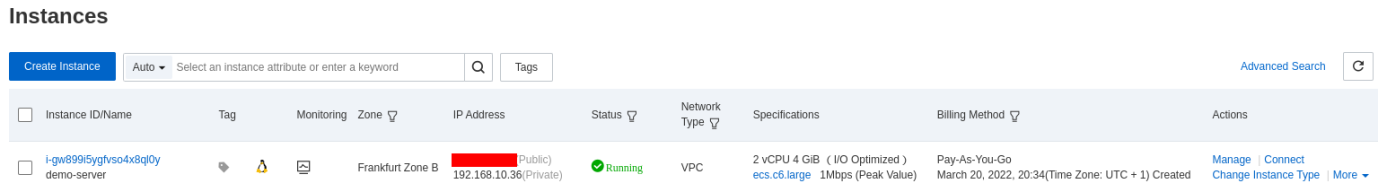
You can check if the instance is linked to the security groups by checking the security group information:
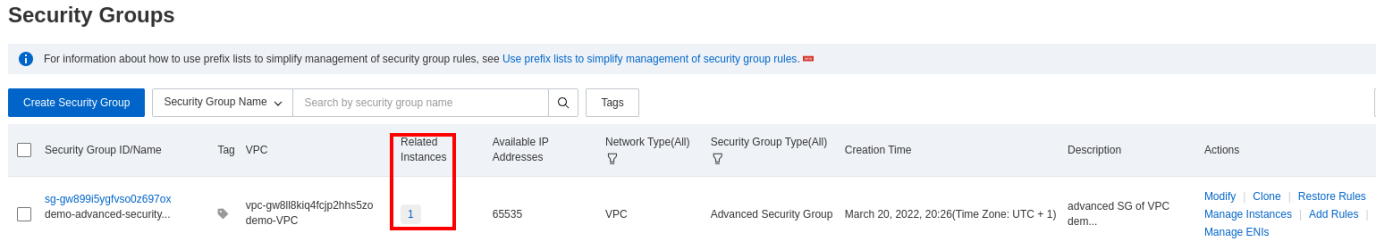
Your VPC will show that an instance is present:
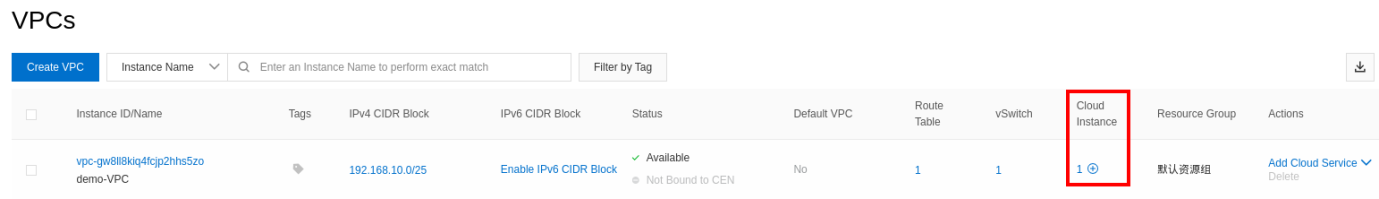
You can see that your new instance is inside the VPC and the security groups that have been created.
When you create an ECS instance in a VPC through the ECS console, a default security group is created if no other security group has been created under the current account in this region. The default security group is a basic security group and has the same network type as the ECS instance.
How to Install SonarQube and PostgreSQL with Docker on Alibaba Cloud ECS Instance

1,317 posts | 463 followers
FollowAlibaba Clouder - January 12, 2021
Alibaba Cloud Community - March 28, 2022
Alibaba Clouder - July 19, 2019
Alibaba Clouder - July 3, 2020
Alibaba Clouder - July 14, 2020
Rupal_Click2Cloud - October 13, 2020

1,317 posts | 463 followers
Follow VPC
VPC
A virtual private cloud service that provides an isolated cloud network to operate resources in a secure environment.
Learn More Alibaba Cloud PrivateZone
Alibaba Cloud PrivateZone
Alibaba Cloud DNS PrivateZone is a Virtual Private Cloud-based (VPC) domain name system (DNS) service for Alibaba Cloud users.
Learn More Apsara Stack
Apsara Stack
Apsara Stack is a full-stack cloud solution created by Alibaba Cloud for medium- and large-size enterprise-class customers.
Learn More Networking Overview
Networking Overview
Connect your business globally with our stable network anytime anywhere.
Learn MoreMore Posts by Alibaba Cloud Community