Classic distributed denial-of-service (DDoS) attacks are somewhat different from application-layer DDoS attacks. Traditional DDoS attacks send a huge number of simultaneous permission requests to targets, resulting in server outages and device crashes. Such threats are easy to spot, and ready-to-use fixes are easily available. Application layer DDoS attacks, on the other hand, may be disguised as routine traffic or even regular business requests, allowing them to quickly get through security measures to disrupt services or trigger business damage.
The percentages of attacks initiated from various attack sources are as follows:
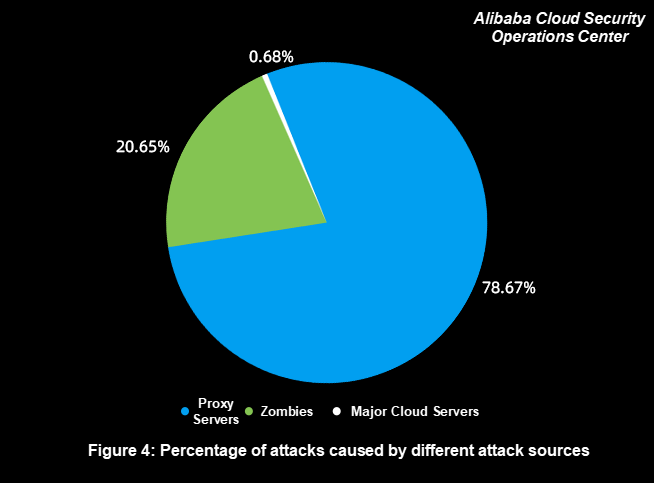
The percentages of different attack source types are as follows:
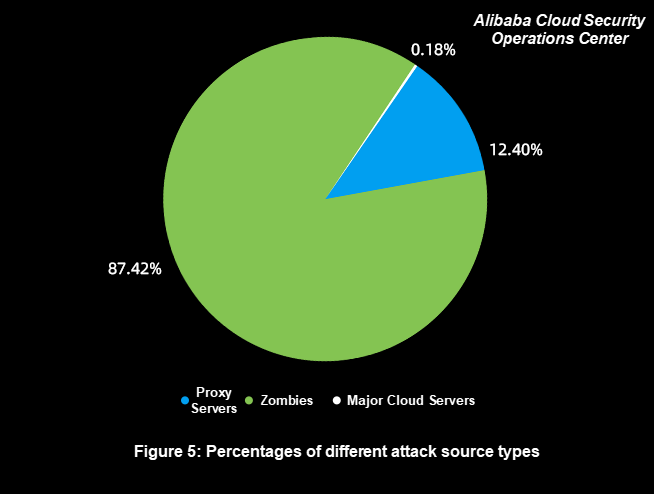
According to Figure 4 and Figure 5, the following observations are made:
1) Proxy Server Attacks Have Become a Norm, and Enterprises Need to Pay More Attention to Them
Proxy server attacks account for the highest proportion of all attacks, but their attack sources account for only 12.40%. These attack sources are extensively used because of their cost-effectiveness. Attackers easily obtain IP addresses at a low cost to initiate effective attacks.
We recommend enterprises to block proxy servers for websites that do not need to be accessed by proxy when business-related proxy servers are allowed to achieve the defense with the same effectiveness and less effort.
2) Enterprises Should Adjust Their Defense Strategies for Scattered Zombie Attack Sources
Zombie attacks account for 20.65% of all attacks, but their attack sources account for 87.42%, which is the largest of all sources. These attack sources are extremely scattered, and their IP addresses are usually broadband or base station egress IP addresses. For attackers, these attack sources are not stable online and have moderate attack performance.
For attacks initiated by these attack sources, we recommend enterprises not to use IP address-based defense. Most IP addresses of zombie servers are the broadband and base station egress IP addresses, which have a large number of regular users. Blocking an IP address previously used for attacks may block the regular access of hundreds of potential users.
Furthermore, the IP addresses of zombie servers change rapidly due to device location changes or the dynamic IP address allocation mechanism of internet service providers (ISPs). Therefore, it is not easy to block these IP addresses.
To defend against such attacks, it is necessary to block requests identified as impossible in advance based on regular business request features. For example, block requests from PCs for app-specific services. Enterprises can also adjust policies dynamically based on the differences between regular business requests and attack requests.
3) Attacks Initiated by Major Cloud Servers Have Been Significantly Reduced
Attacks initiated by major cloud servers account for only 0.68%, which is the least, and the attack sources account for only 0.18%. This is attributed to the strict control over DDoS attacks on major cloud platforms, which makes it costly to use these attack sources.
Therefore, if the attack source IP addresses come from only a small number of class C addresses and few requests come from the CIDR block in normal cases, we recommend enterprises to block IP addresses to prevent malicious requests.
Alibaba Cloud provides DDoS protection capabilities to help customers to mitigate the risks of such attacks. In the past, customers usually had to choose between protection or acceleration, as some security services are incompatible with acceleration services. However, now, Alibaba Cloud DDoS protection can be used in combination with Content Delivery Networks (CDN), ensuring that there won't be any attacks to your traffic that's going through CDN.
This tutorial is a step-by-step guide on how you can accelerate and protect your website hosted outside of Mainland China using Anti-DDoS premium with CDN interaction.
After all the hard work of developing a web application or Mobile App, it may be rather daunting thinking about how you can protect your work against external threats like DDoS attacks. DDoS attacks could easily destroy your hard work, making your application completely unresponsive, or even causing your website to be blackholed by your internet service provider. And, adding to worry, not all Anti-DDoS services are built the same, some of them offer much less protection than others, and other ones can start to bog down your services, so choosing the right anti-DDoS service is crucial nowadays.
In this tutorial, I'm going to show you how you can get started using Alibaba Cloud's Anti-DDoS Premium service, the ultimate anti-DDoS service, to protect your critical assets against DDoS attacks and CC attacks. I'll also show you how you can use the all-new Mainland China Acceleration (MCA) feature to accelerate access to your web application in Mainland China if your application is hosted outside of Mainland China, such as in Singapore or Hong Kong.
In this tutorial, I will be using this service in combination with other Alibaba Cloud products, including Alibaba Cloud Domain Name Service (DNS) and Object Storage Service (OSS).
This tutorial is a step-by-step explanation about how you can configure the whole setup in just 30 minutes.
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Anti-DDoS service is based on Alibaba Cloud's global scrubbing centers, combined with intelligent DDoS detection and protection systems developed at Alibaba, automatically mitigates attacks and reinforce the security of your applications, reduce the threat of malicious attacks.
A scalable and high-performance content delivery service for accelerated distribution of content to users across the globe.
You can use content delivery network (CDN) to deliver content to users from the nodes that are nearest to them, accelerating the response to user requests and increasing the response rate. CDN also resolves the delivery latency problem that is usually caused by distribution, bandwidth, and server performance issues. CDN has been applied in multiple scenarios, including site acceleration, on-demand streaming, and live streaming.
Alibaba Cloud provides you with various DDoS mitigation solutions. You can select an appropriate solution based on your business needs. This topic describes the DDoS mitigation solutions and application scenarios.
Anti-DDoS Origin is a protection service that improves protection capacity against DDoS attacks for resources. These resources include Elastic Compute Service (ECS) instances, Server Load Balancer (SLB) instances, elastic IP addresses (EIPs), and Web Application Firewall (WAF) instances. Anti-DDoS Origin directly protects cloud services and imposes no limits, which is different from Anti-DDoS Pro and Anti-DDoS Premium. You do not need to change the IP addresses of the resources that you want to protect. You do not need to consider the limits on the number of Layer-4 ports and the number of Layer-7 domain names. Anti-DDoS Origin is easy to deploy. You only need to bind the IP address of a resource that you want to protect with Anti-DDoS Origin. The protection for the resource only requires a few minutes to take effect.
Anti-DDoS Pro and Anti-DDoS Premium are proxy-based mitigation services provided by Alibaba Cloud to mitigate DDoS attacks. These services can be used to protect network servers against volumetric DDoS attacks. To protect servers against volumetric and resource exhaustion DDoS attacks, Anti-DDoS Pro and Anti-DDoS Premium forward traffic to the Alibaba Cloud anti-DDoS network by using DNS resolution.

2,593 posts | 793 followers
FollowNeel_Shah - November 14, 2025
Alibaba Clouder - May 9, 2020
Ced - November 6, 2024
Alibaba Clouder - June 12, 2019
Kidd Ip - November 24, 2025
Alibaba Clouder - November 9, 2018

2,593 posts | 793 followers
Follow Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Sensitive Data Discovery and Protection
Sensitive Data Discovery and Protection
SDDP automatically discovers sensitive data in a large amount of user-authorized data, and detects, records, and analyzes sensitive data consumption activities.
Learn MoreMore Posts by Alibaba Clouder