Bolster the growth and digital transformation of your business amid the outbreak through the Anti COVID-19 SME Enablement Program. Get a $300 coupon package for all new SME customers or a $500 coupon for paying customers.
Application layer distributed denial-of-service (DDoS) attacks differ greatly from traditional DDoS attacks. Traditional DDoS attacks initiate a large number of concurrent access requests to targets, which causes service unavailability and system crashes. Such attacks are easy to identify, and mature solutions are widely available in the market. Application layer DDoS attacks, however, can be disguised as normal traffic and even as normal business requests, which allow these attacks to easily bypass security protection and cause service interruption or loss of business.
Alibaba Cloud Security Operations Center has conducted an in-depth analysis of the application layer DDoS attacks during the coronavirus disease (COVID-19) epidemic. We hope our findings help enterprises enhance their defenses against these attacks.
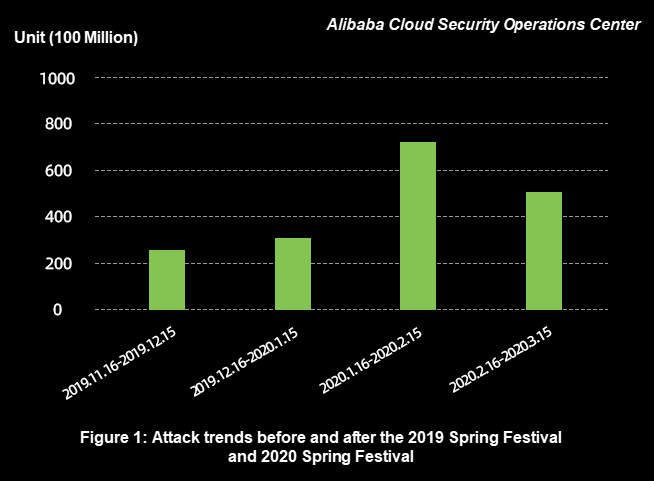
The COVID-19 epidemic onset at the beginning of the new year. The quantity of application layer DDoS attacks remained very high during the period from January to March 2020. In particular, attacks surged from mid-January to mid-February, when the impact of the COVID-19 epidemic was most severe. As shown in Figure 1, attackers initiated more attacks during the epidemic prevention period.
According to findings based on statistical analysis by Alibaba Cloud Security Operations Center, from 16th January to 15th March, the top three industries subject to application layer DDoS attacks were healthcare, online education and online collaboration, and gaming, as shown in Figure 2.
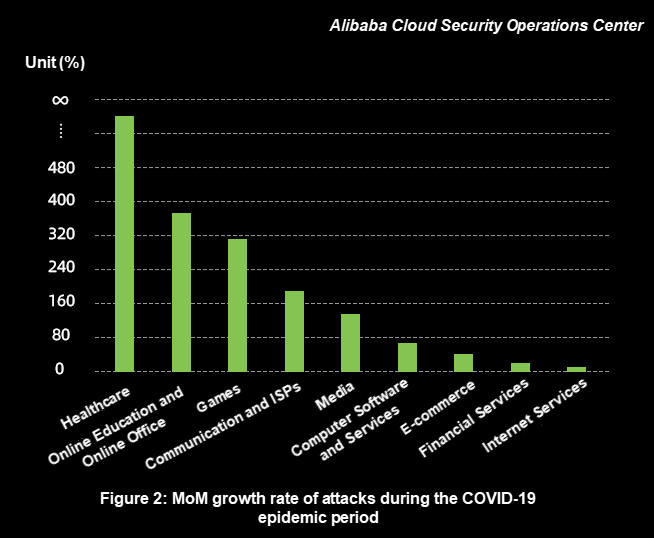
During this period, healthcare, online education, and online collaboration gained unprecedented attention and a lot of resources were invested in these industries. Hackers looking to benefit from this increased value began to target these industries. During the COVID-19 epidemic, most of the population stayed at home, leading to a surge in the popularity of the gaming industry. As a result, the number of attacks in the gaming industry increased by more than 300% month-on-month (MoM).
According to the clustering analysis performed on hundreds of application layer DDoS attacks and the hundreds of millions of attack requests during the COVID-19 epidemic period, attacks mainly originated from proxy servers, zombies, major cloud servers, or a single attack originated from a single type of source, as shown in Figure 3.

As shown in Figure 3, a single attack was initiated by a single attack source, and only a few attacks were initiated from different attack sources. For example, if a proxy server is used to initiate an attack, zombies or cloud servers are not used to initiate attacks at the same time.
The percentages of attacks initiated from various attack sources are as follows:
The percentages of different attack source types are as follows:
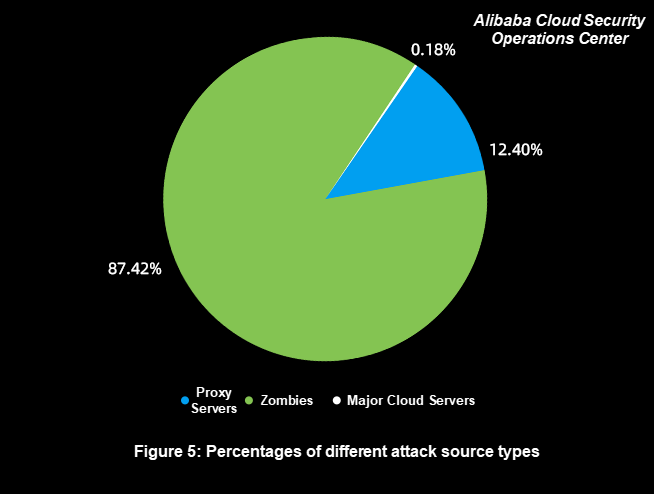
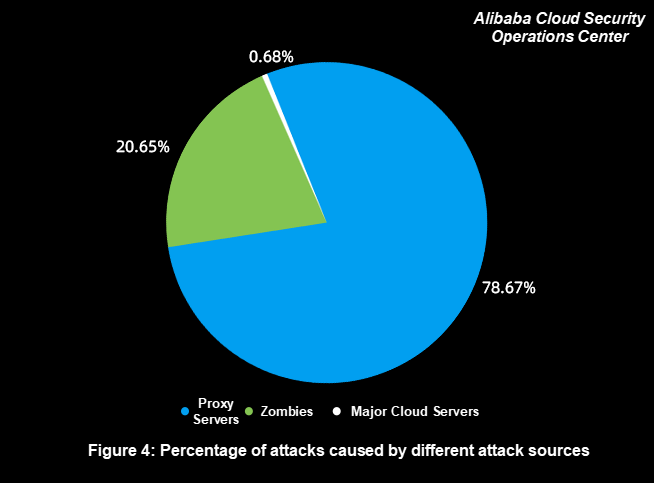
According to Figure 4 and Figure 5, the following observations are made:
Proxy server attacks account for the highest proportion of all attacks, but their attack sources account for only 12.40%. These attack sources are extensively used because of their cost-effectiveness. Attackers easily obtain IP addresses at a low cost to initiate effective attacks.
We recommend enterprises to block proxy servers for websites that do not need to be accessed by proxy when business-related proxy servers are allowed to achieve the defense with the same effectiveness and less effort.
Zombie attacks account for 20.65% of all attacks, but their attack sources account for 87.42%, which is the largest of all sources. These attack sources are extremely scattered, and their IP addresses are usually broadband or base station egress IP addresses. For attackers, these attack sources are not stable online and have moderate attack performance.
For attacks initiated by these attack sources, we recommend enterprises not to use IP address-based defense. Most IP addresses of zombie servers are the broadband and base station egress IP addresses, which have a large number of regular users. Blocking an IP address previously used for attacks may block the regular access of hundreds of potential users.
Furthermore, the IP addresses of zombie servers change rapidly due to device location changes or the dynamic IP address allocation mechanism of internet service providers (ISPs). Therefore, it is not easy to block these IP addresses.
To defend against such attacks, it is necessary to block requests identified as impossible in advance based on regular business request features. For example, block requests from PCs for app-specific services. Enterprises can also adjust policies dynamically based on the differences between regular business requests and attack requests.
Attacks initiated by major cloud servers account for only 0.68%, which is the least, and the attack sources account for only 0.18%. This is attributed to the strict control over DDoS attacks on major cloud platforms, which makes it costly to use these attack sources.
Therefore, if the attack source IP addresses come from only a small number of class C addresses and few requests come from the CIDR block in normal cases, we recommend enterprises to block IP addresses to prevent malicious requests.
Based on the preceding analysis, we provide the following suggestions on how to defend against application layer DDoS attacks:
A common ex post defense reinforcement method is to blacklist attack sources that have been used to initiate attacks. This method can prevent subsequent attacks from proxy servers or major cloud servers to a certain extent. However, if the attacks are zombie attacks, the downside outweighs the gains. Therefore, identify the attack source types before blacklisting IP addresses of attacks.
Blacklisting IP addresses with a high access frequency is the most traditional in-process defense method. This method is very effective when there is only a small number of attack sources. However, the number of cloud server attack sources can reach tens of thousands. This means that, even if the defense policy allows only one request from each IP address each second, tens of thousands of requests are directed to the website every second, which most servers for small and medium-sized websites cannot handle. Therefore, to completely suppress attacks, we need to block request sources that are identified as impossible and request characteristics in advance. We also need to dynamically adjust defense policies based on the differences between attacks and normal businesses in the process. Frequency-based policies only help to some extent.
While continuing to wage war against the worldwide outbreak, Alibaba Cloud will play its part and will do all it can to help others in their battles with the coronavirus. Learn how we can support your business continuity at https://www.alibabacloud.com/campaign/fight-coronavirus-covid-19
The Secret Behind Taobao's AI-Powered Personalized Recommendations

2,593 posts | 793 followers
FollowAlibaba Clouder - April 8, 2021
Kidd Ip - November 24, 2025
Alibaba Clouder - July 12, 2019
Alibaba Clouder - June 28, 2020
Alibaba Clouder - July 15, 2021
Alibaba Clouder - November 28, 2018

2,593 posts | 793 followers
Follow Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More Fight Coronavirus [COVID-19]
Fight Coronavirus [COVID-19]
Empowering businesses to fight against coronavirus through technology
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn MoreMore Posts by Alibaba Clouder