Alibaba Cloud ACK One is a product service provided by Alibaba Cloud that enables hybrid and multi-cloud environments based on Kubernetes. ACK One manages Kubernetes clusters from AWS, Azure, Google Cloud, on-premises, and others as a unified managed Kubernetes service in Alibaba Cloud ACK clusters, allowing for flexible multi-cluster configurations across different environments. With ACK One, as long as there is Kubernetes on the other cloud or on-premises environments, you can register the Kubernetes cluster with ACK One and operate it based on Alibaba Cloud's fully managed Kubernetes service, Alibaba Cloud Container Service for Kubernetes (ACK), even on other cloud or on-premises environments.
In a previous article, we explained how to build a multi-cluster service between ASK clusters on Alibaba Cloud using ACK One. With ACK One, clusters deployed in data centers and third-party cloud clusters can be registered, making it possible to build multi-cluster services involving GKE clusters.
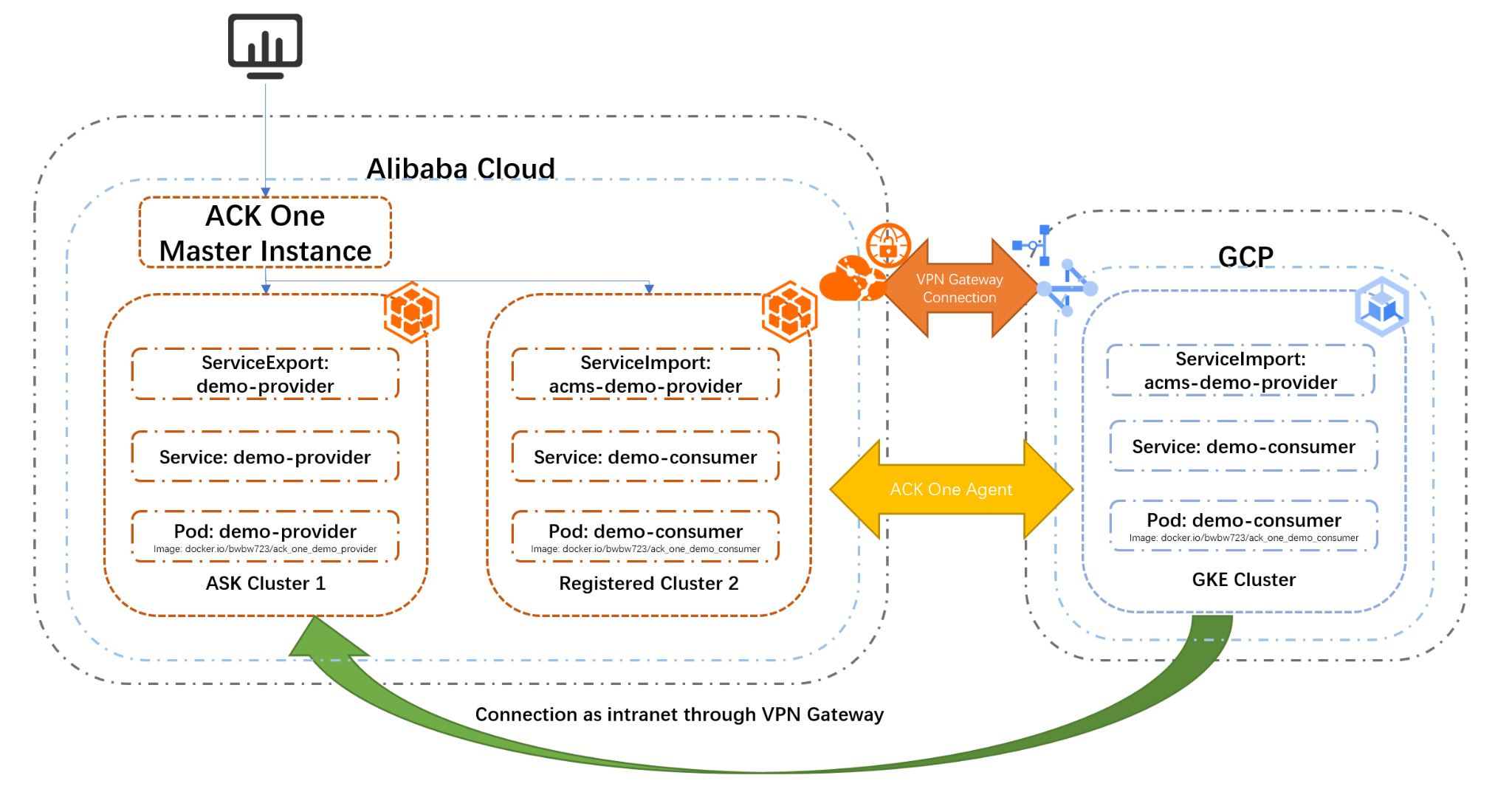
This article explains how to build network connections between Alibaba Cloud and Google Cloud (via VPN Gateway) and how to use this as a base to build multi-cluster services with ACK One.
The overall configuration diagram is below:
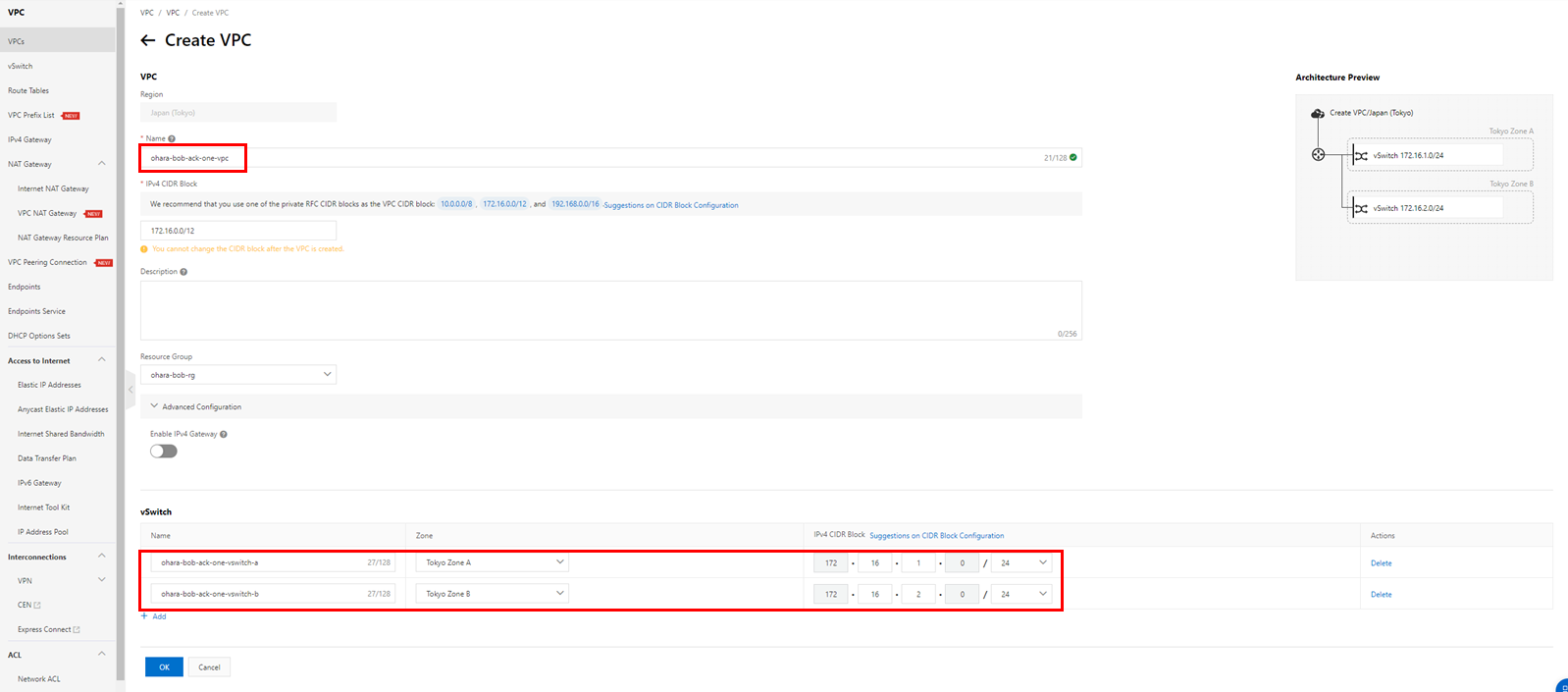
In order to build a network connection with VPN Gateway, create VPC and vSwitch on Alibaba Cloud:
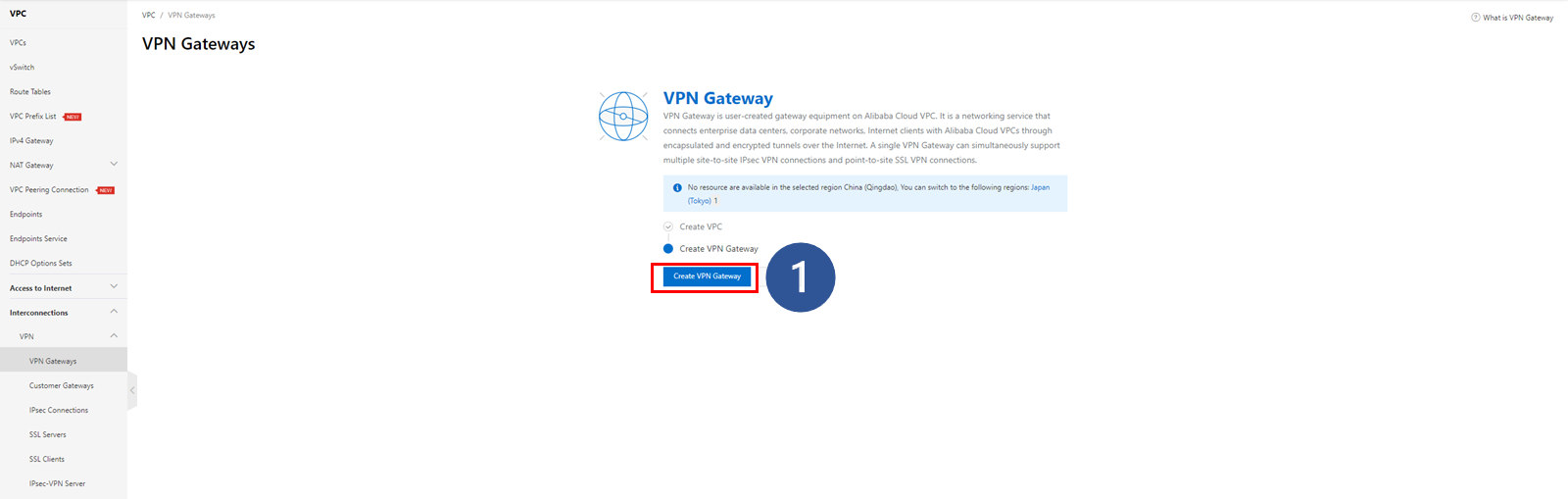
In order to generate an external IP address, create a VPN Gateway on Alibaba Cloud:
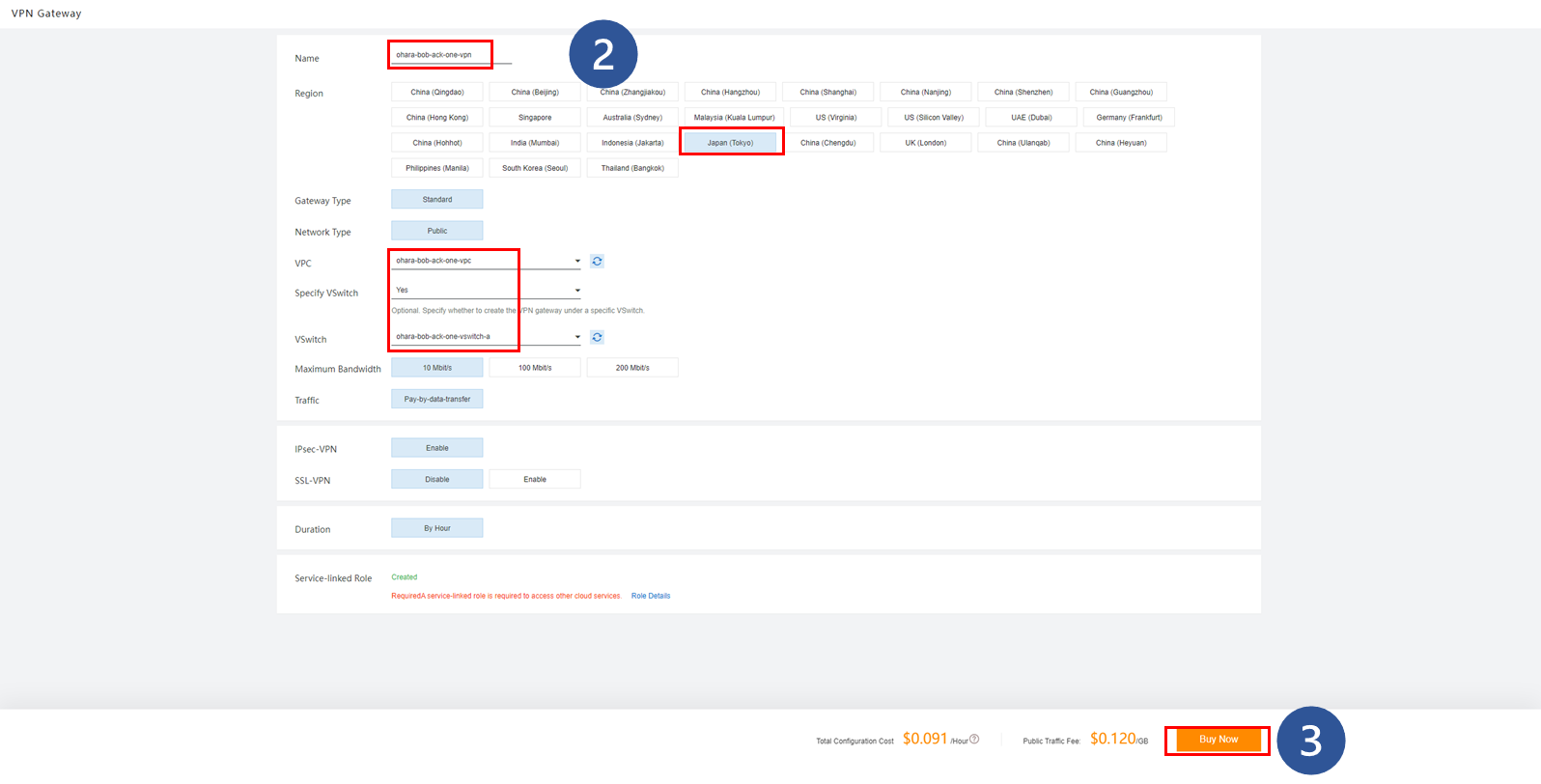
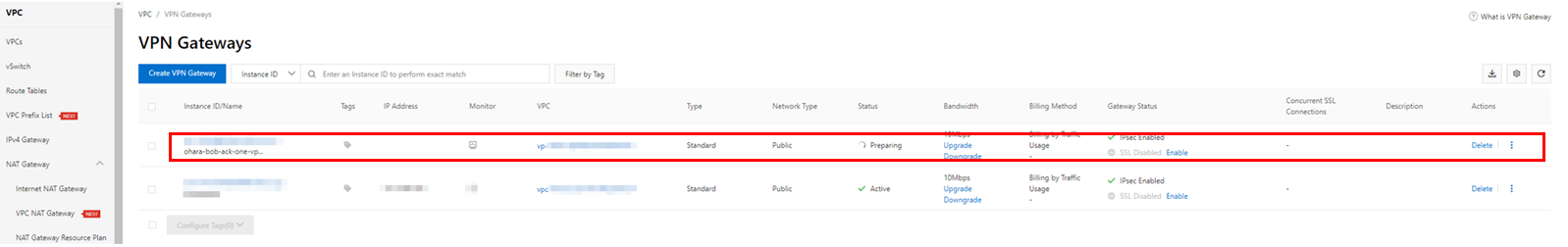
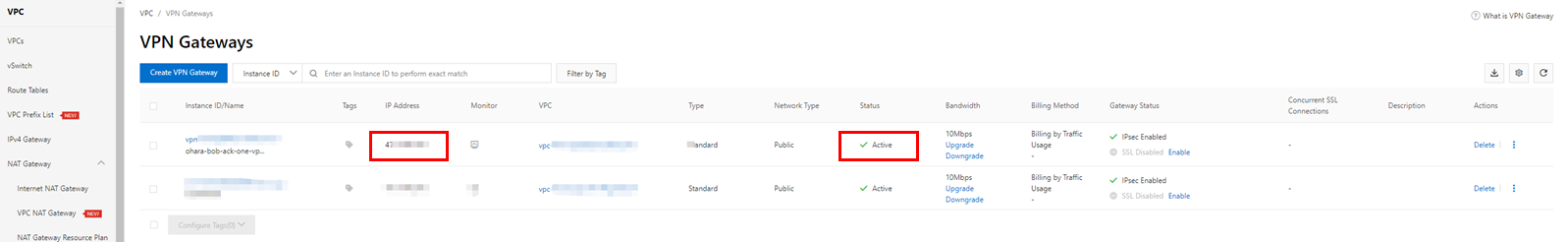
Check the created resources and wait for the IP address to be generated. At this time, the VPN Gateway instance will be in the Active state, so make a note of the IP address displayed at that time. This IP address will be used in the future.
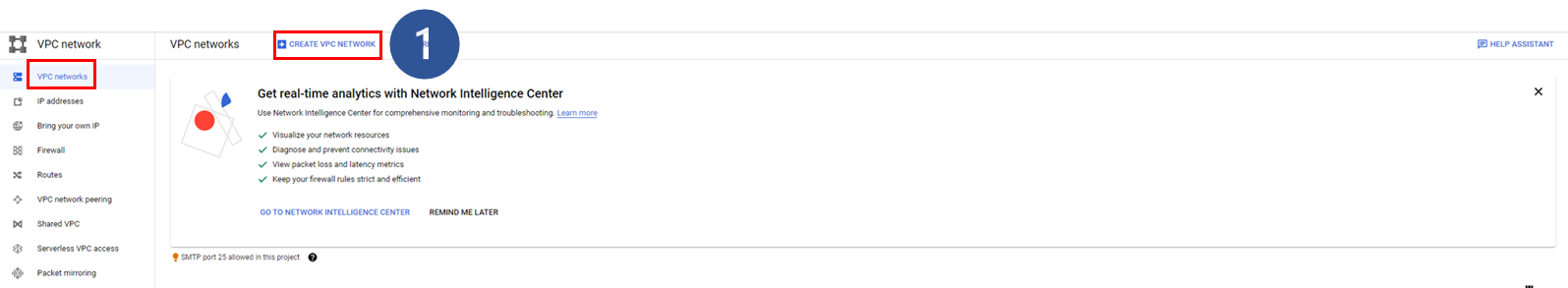
Go to the VPC Network console on the Google Cloud platform and create a new VPC with a subnet:
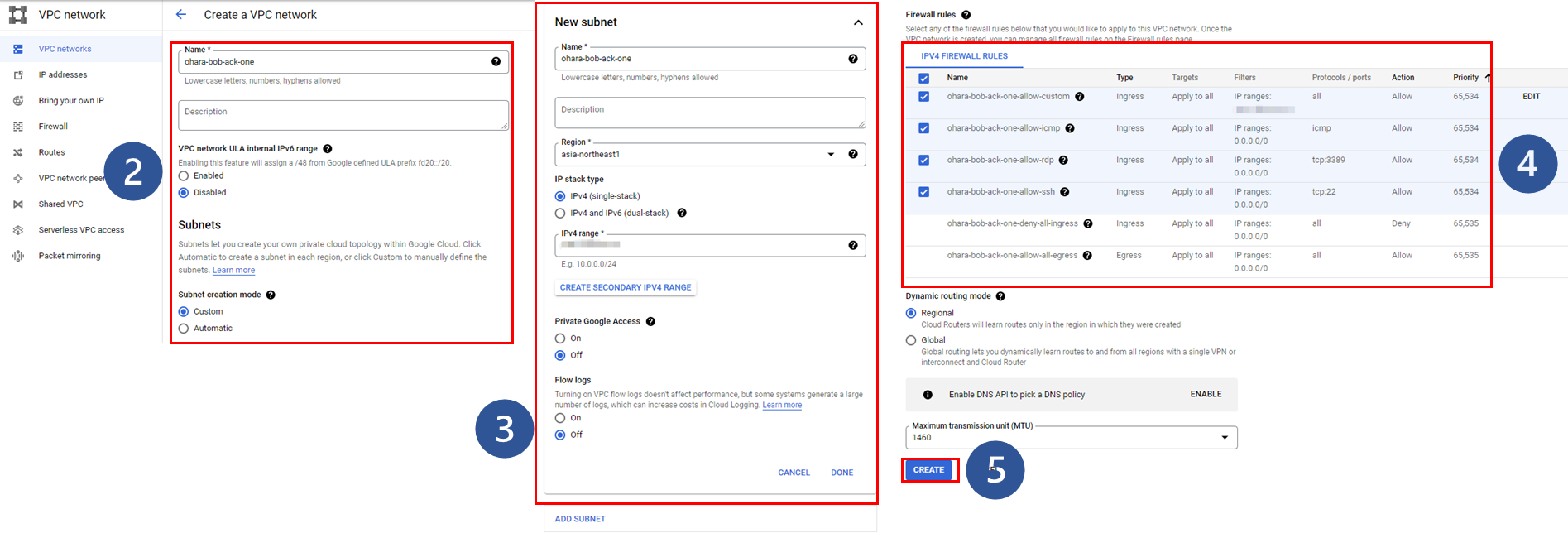
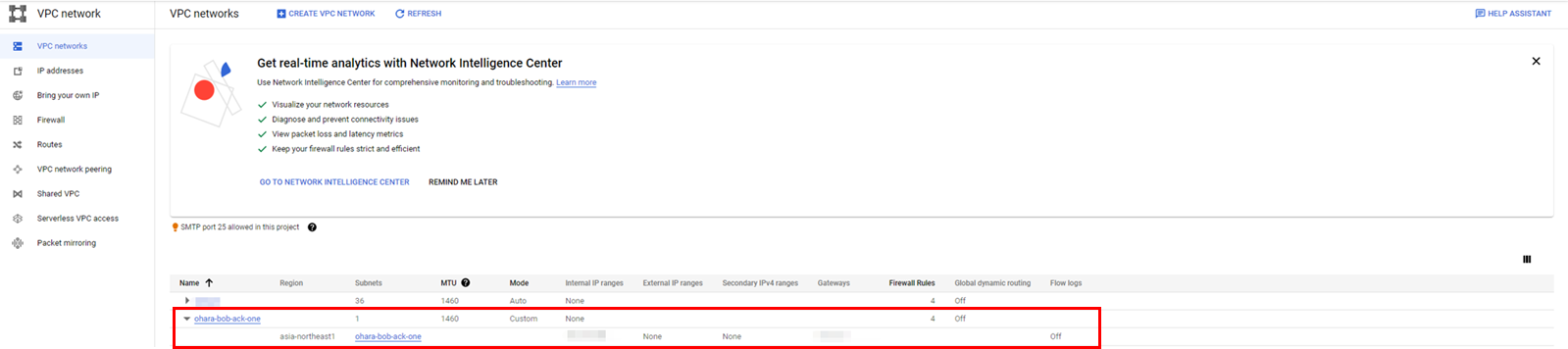
Once complete, the target VPC network will be displayed on the Google Cloud console:
Navigate to the VPN console on Google Cloud and create a VPN connection for further use:
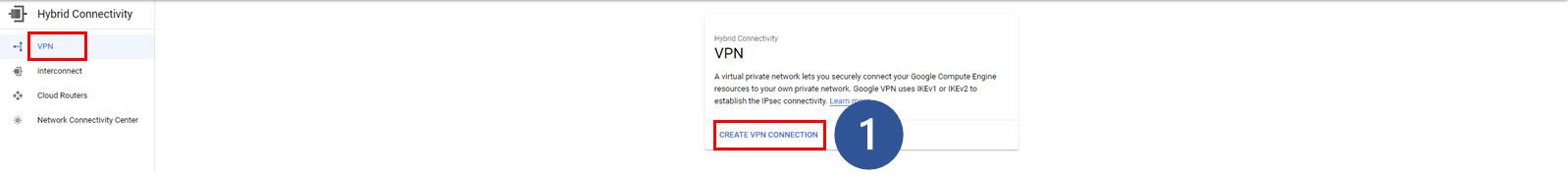
1. Click Create VPN connection on the VPN console
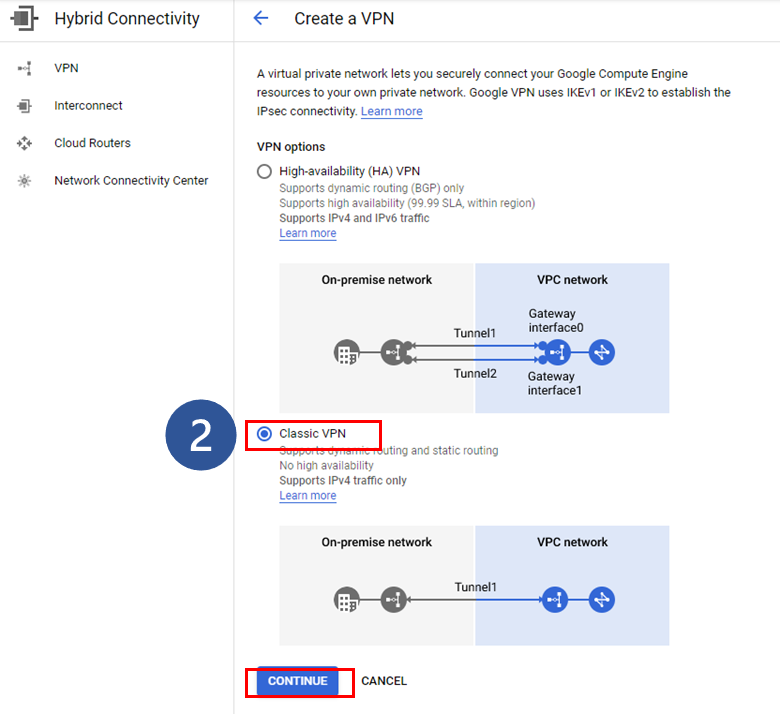
2. Select the classic VPN mode and click Continue to proceed to the next step
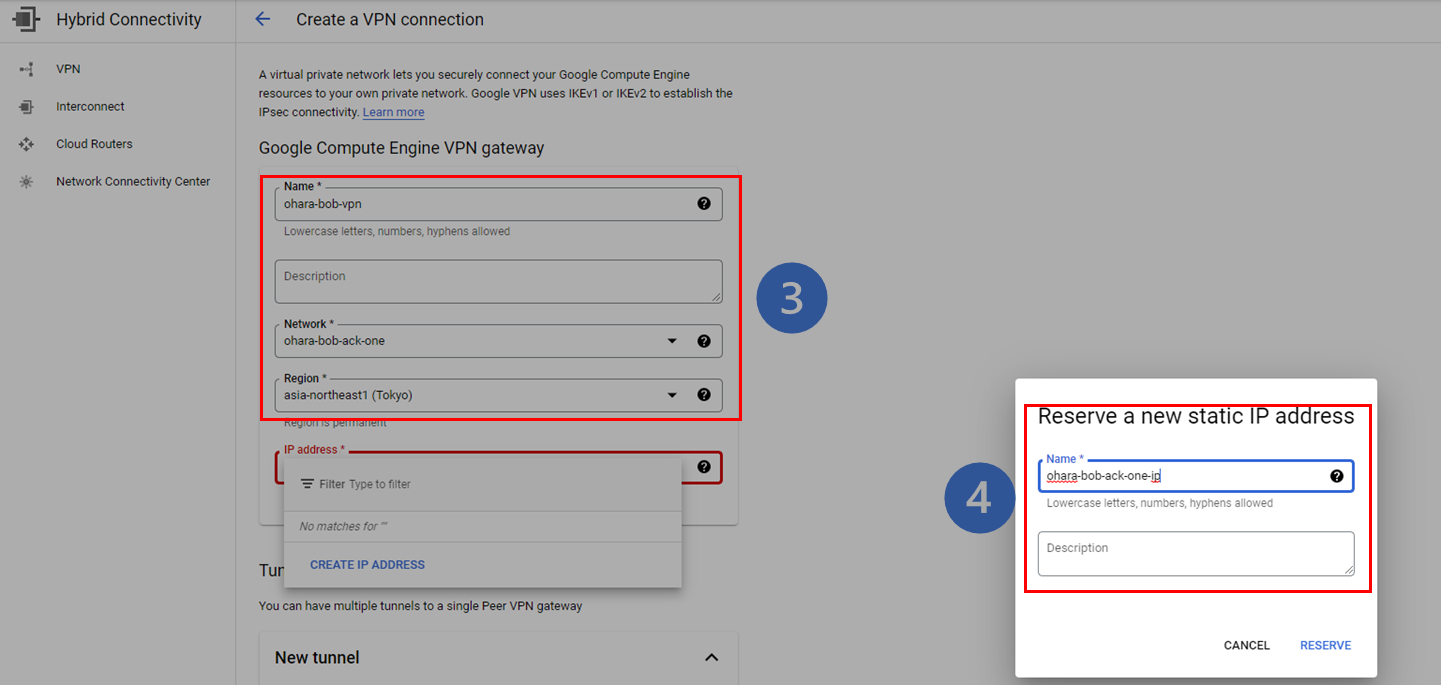
3. Enter the basic information of the VPN Gateway (network, region, etc.)
4. Reserve a new static IP address to bind with the target VPN Gateway. This can also be created separately on the IP addresses page of the VPC Network console. Remember this IP address for future use.
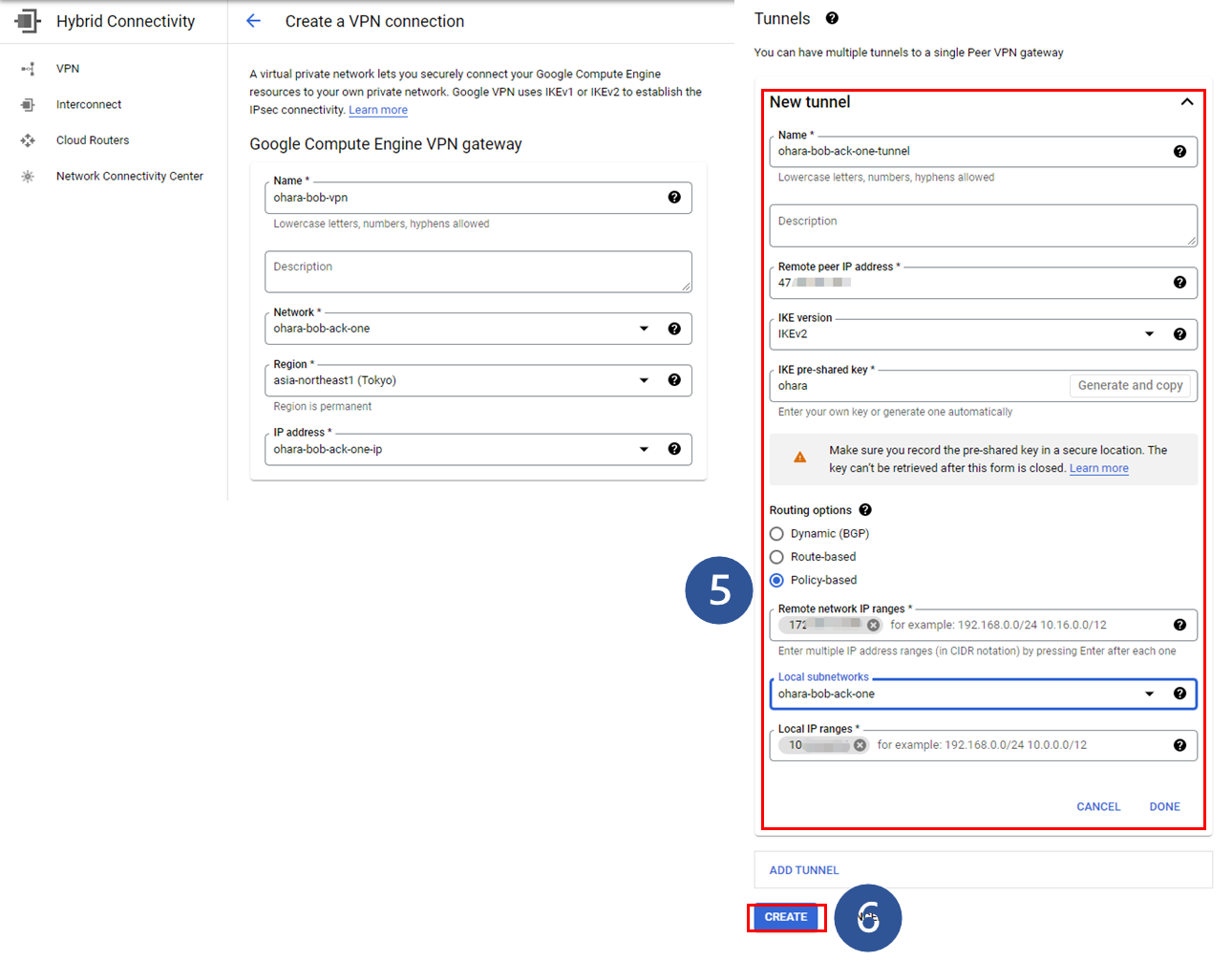
5. Configure the VPN tunnel settings
6. Click Create and execute the operation.
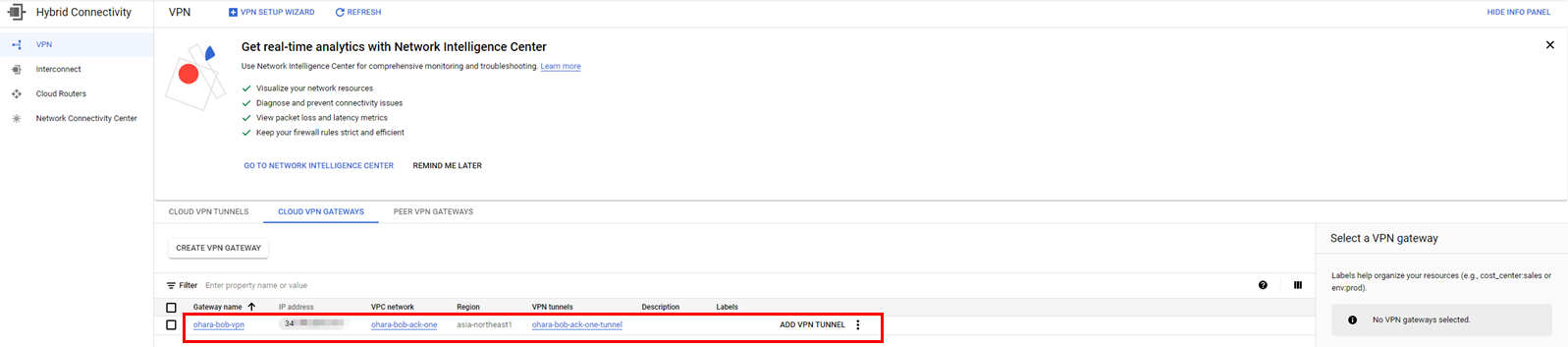
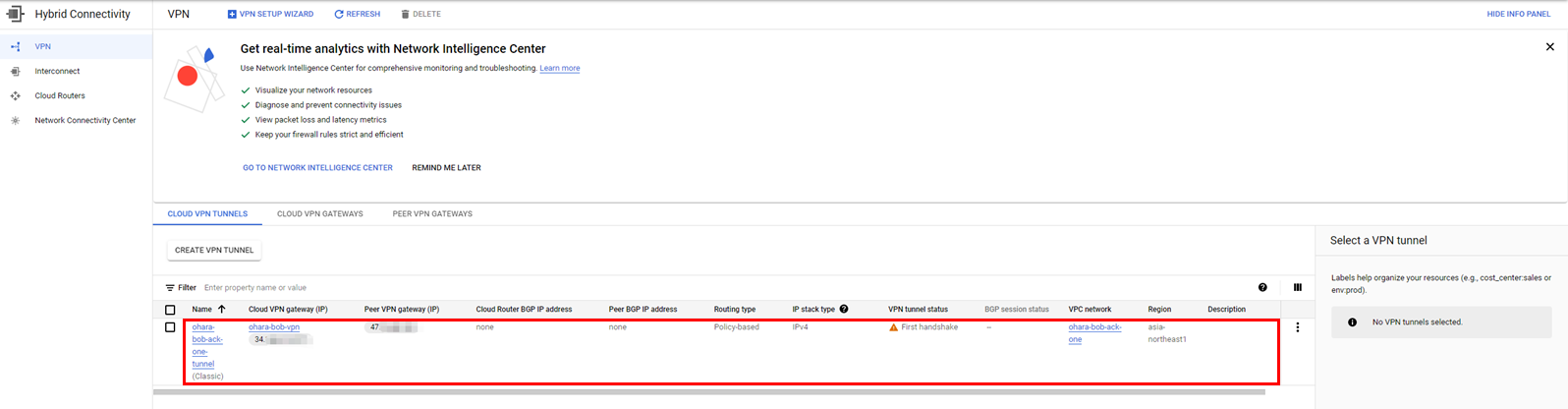
Check the created resources (such as the VPN Gateway and tunnel)
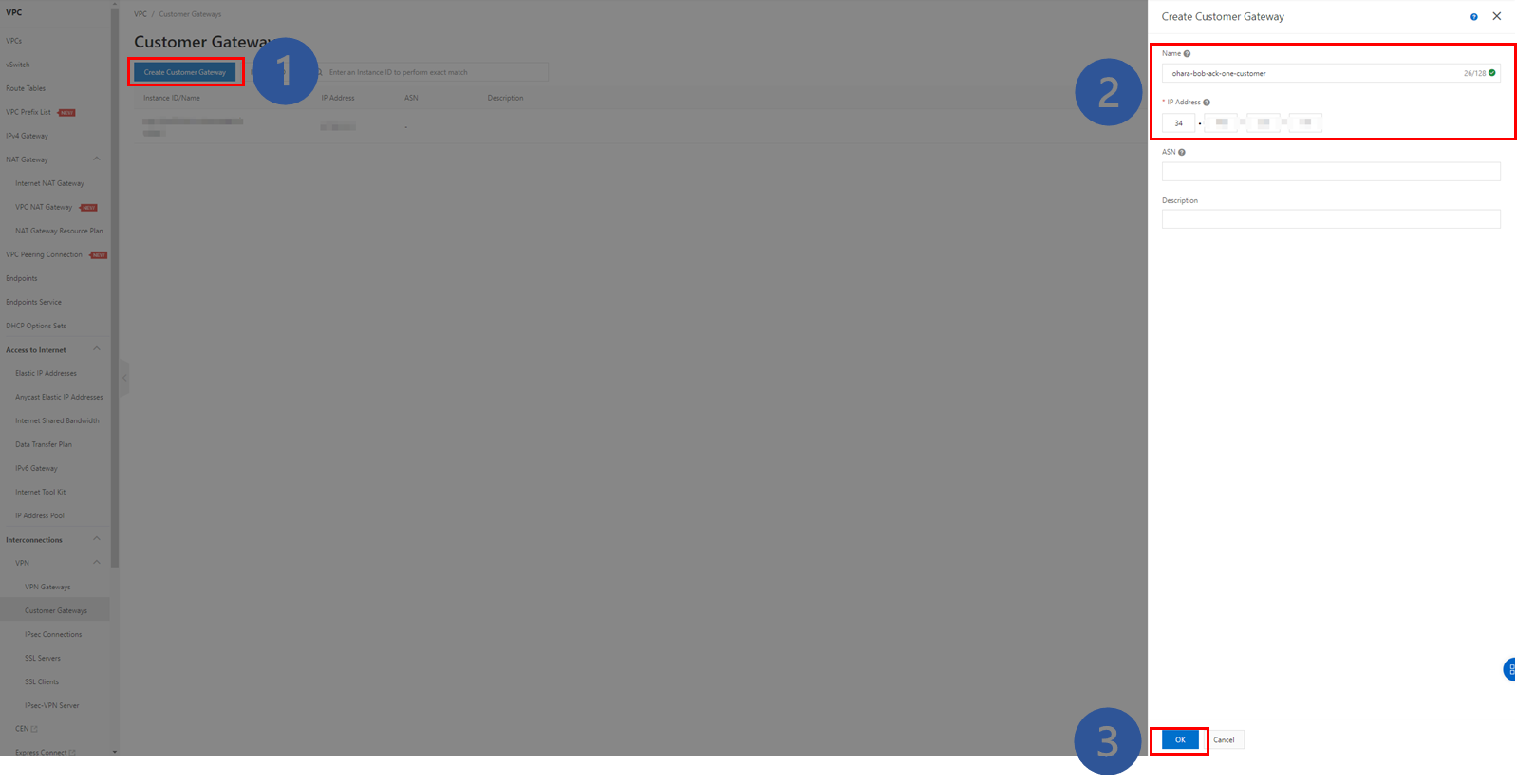
Create a customer gateway on Alibaba Cloud:
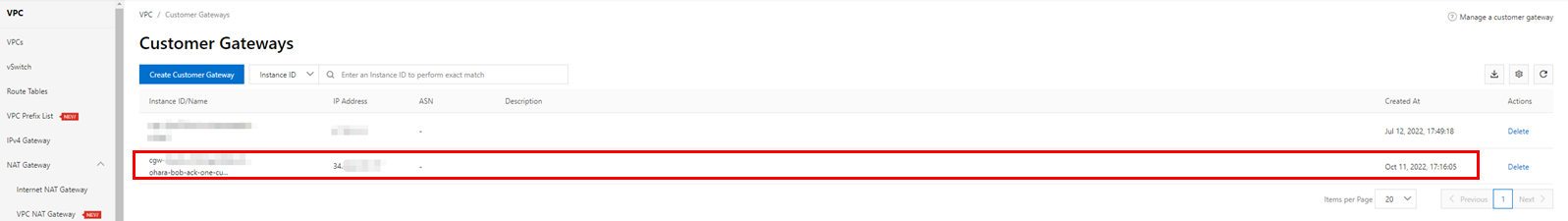
Verify the created instance as the following image:
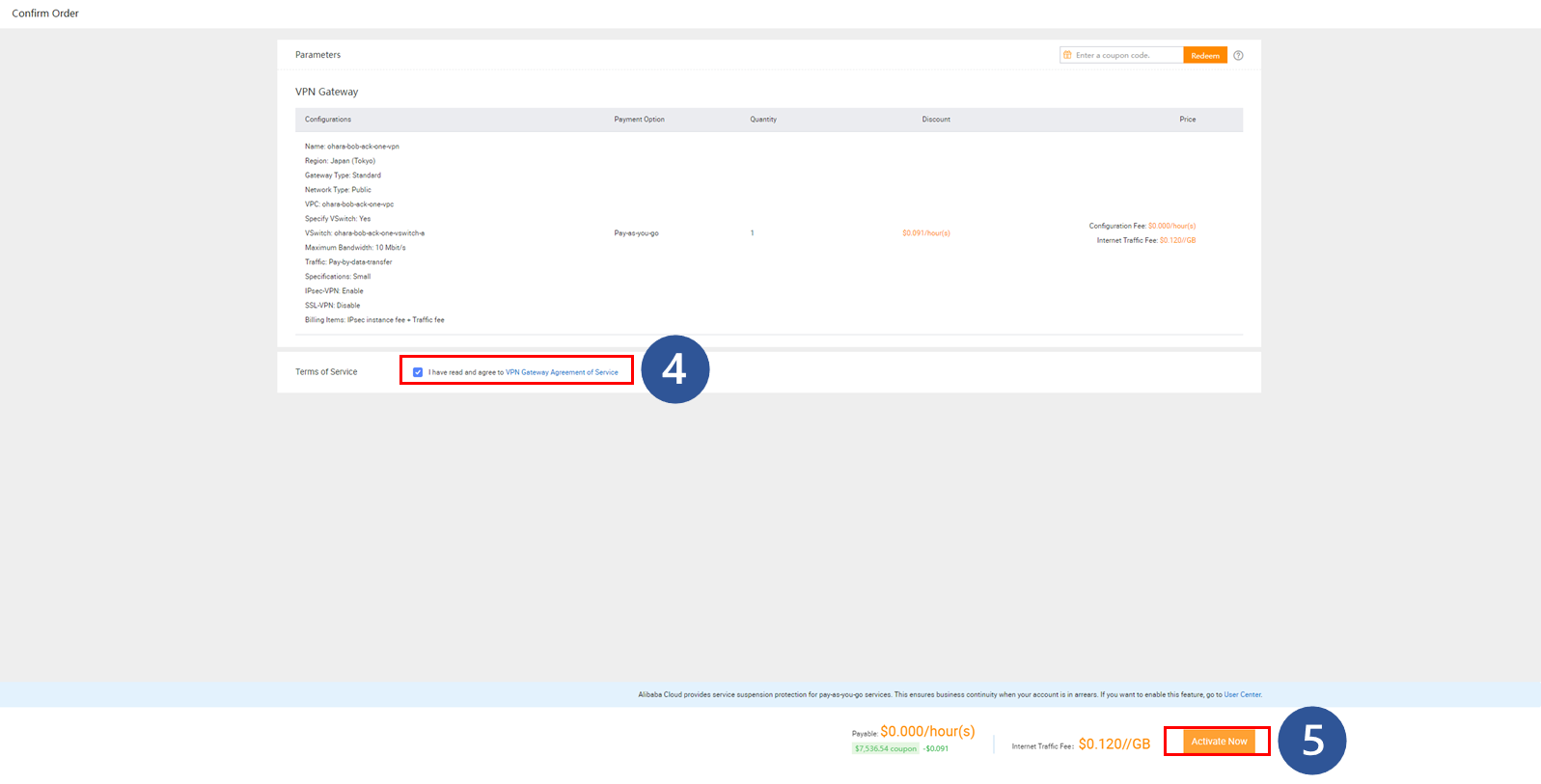
Next, we will build an IPsec connection on Alibaba Cloud. This will be done from the VPC console on Alibaba Cloud.
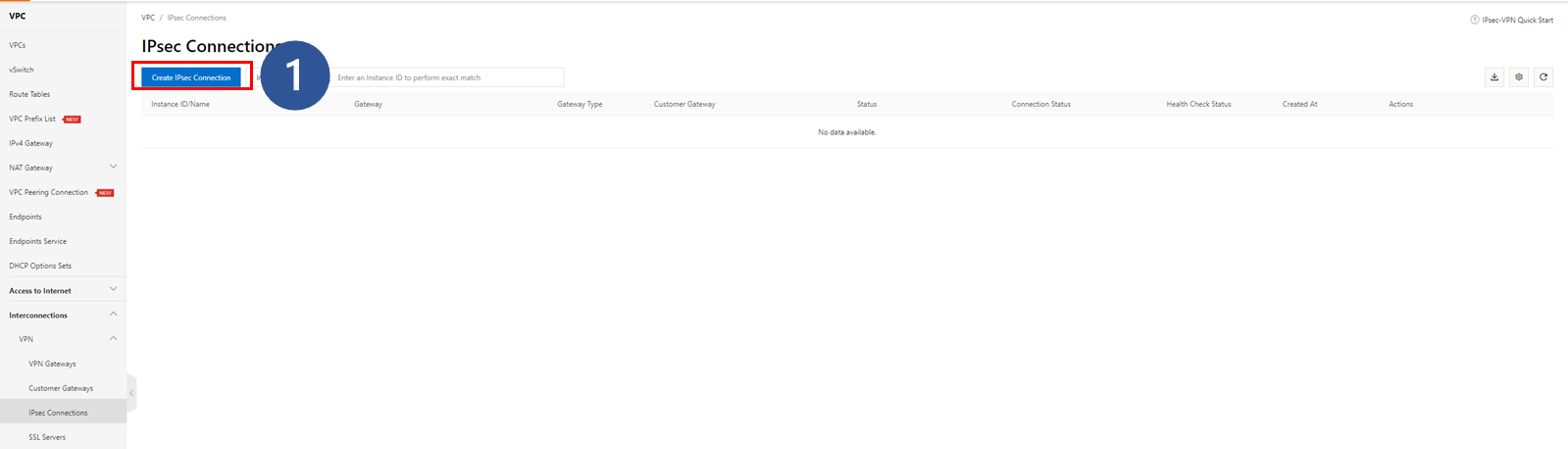
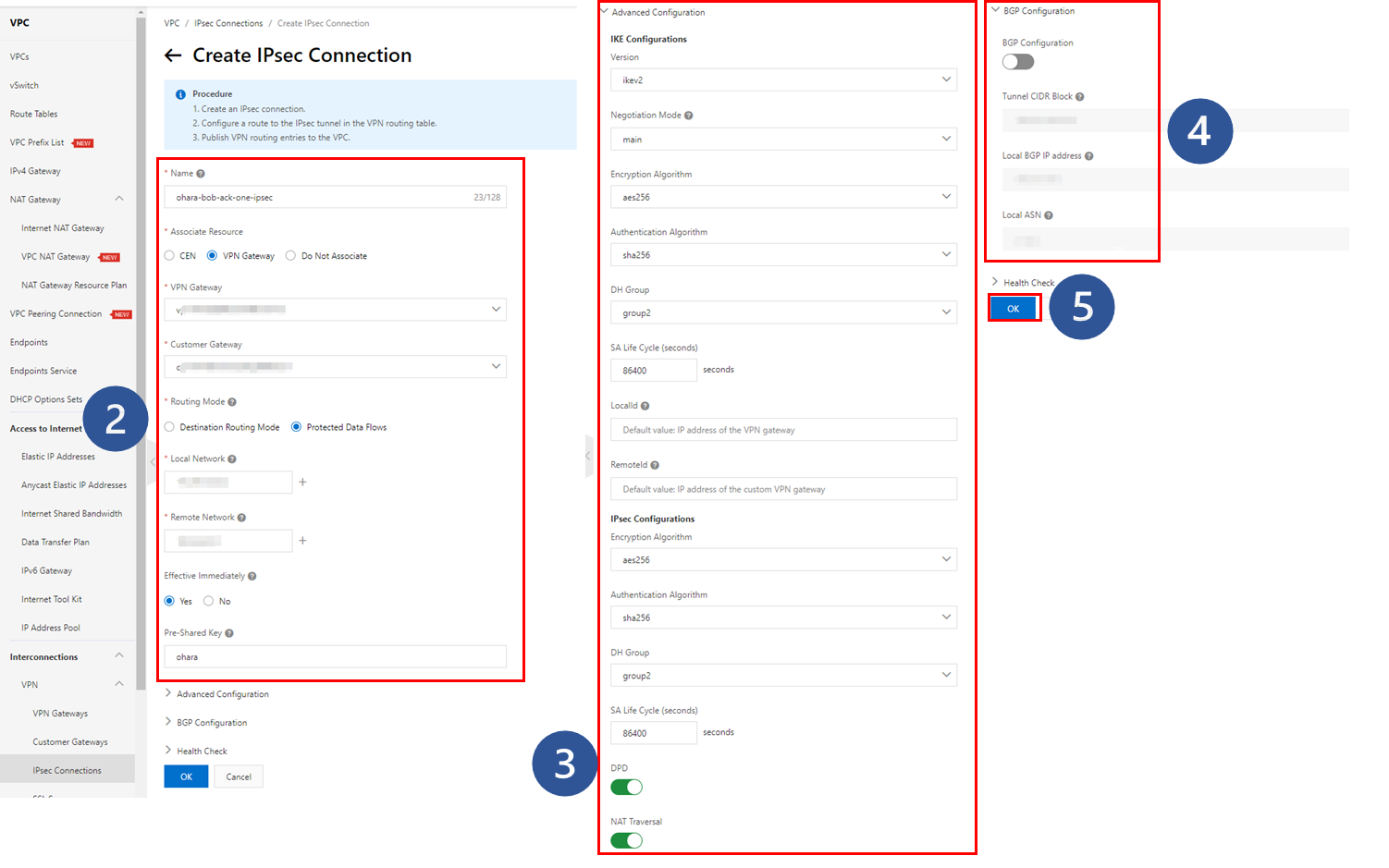
1. Click Create IPsec Connection
2. Enter the required information for basic settings
3. Enter the required information for detailed settings
4. Leave the BGP settings disabled by default
5. Click OK to perform the operation
The IPsec connection that was created shows an error in the connection status. However, since all necessary resources have been prepared, the connection status will quickly change to successful. Please confirm that the final connection status is Phase 2 of IKE Tunnel Negotiation Succeeded. If the connection status is not as described, there may have been some error in the configuration steps above.
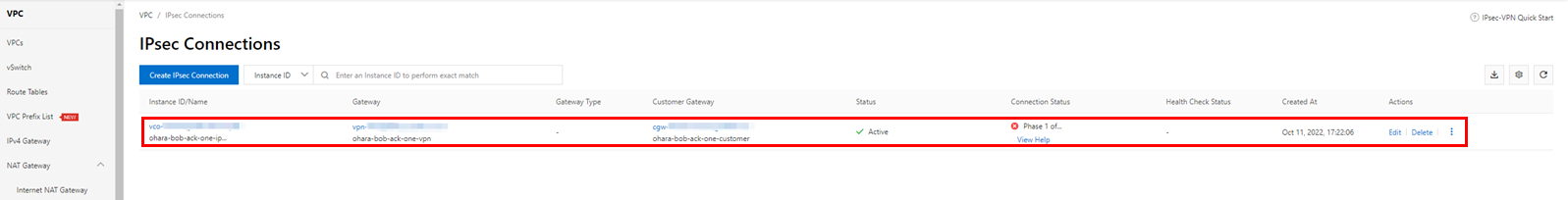
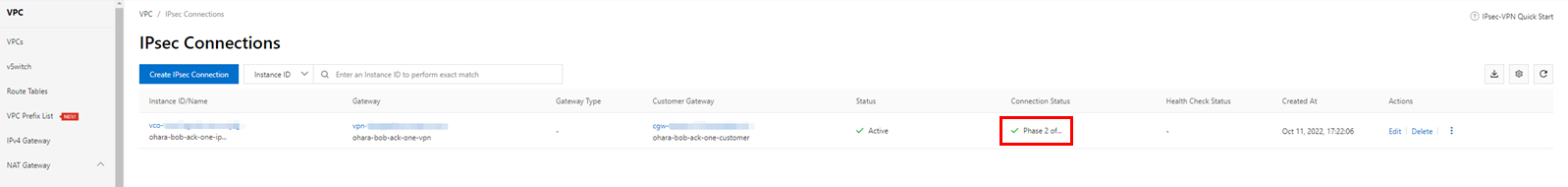
We recommend checking several items in addition to the IPsec connection status to confirm that the configuration has been completed successfully. First, check the status of the VPN tunnel in Google Cloud. Once the IPsec connection has been successfully configured in Alibaba Cloud, the VPN tunnel in Google Cloud also needs to be updated to Established simultaneously.
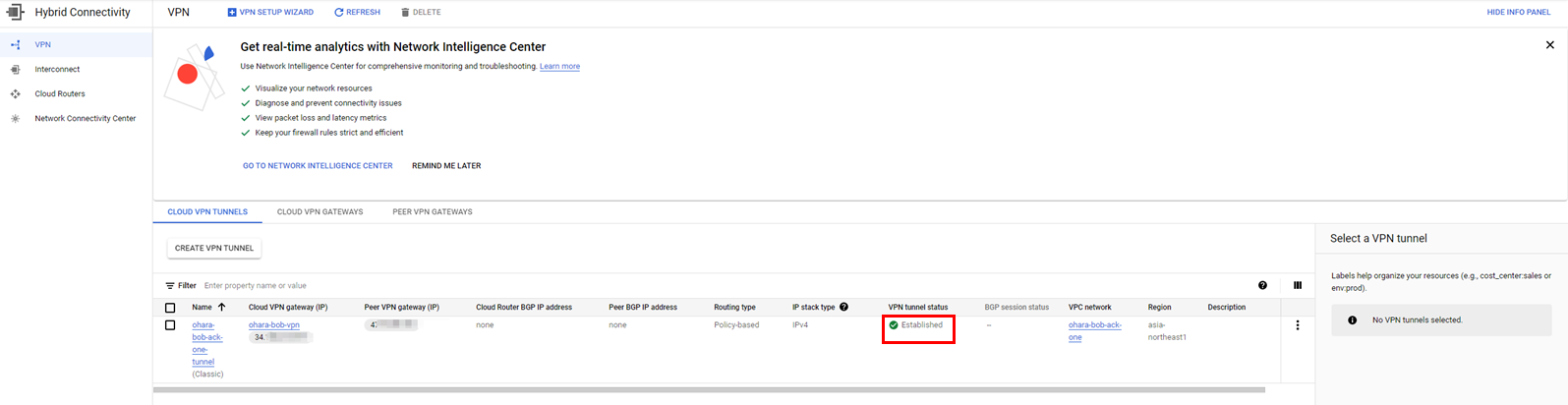
Next, return to the VPN console in Alibaba Cloud and check the Policy-based Routing under the target VPN Gateway. There should be published route entries. If the route entry is in an Unpublished state, please manually publish it.
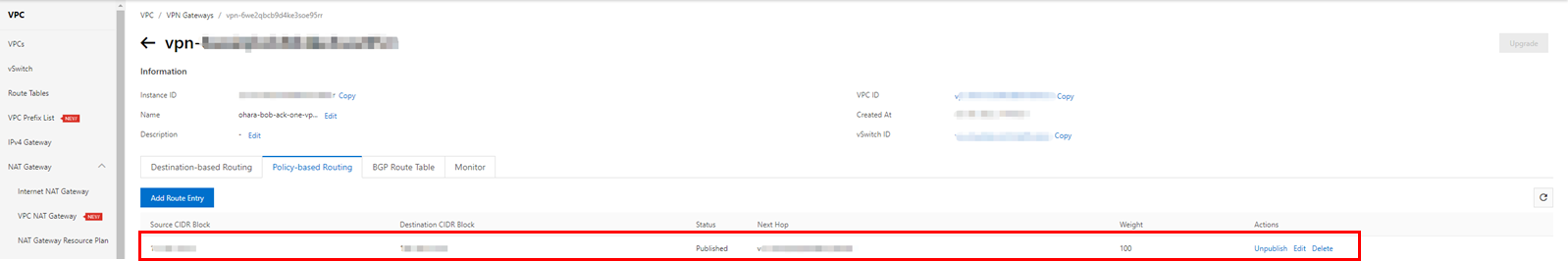
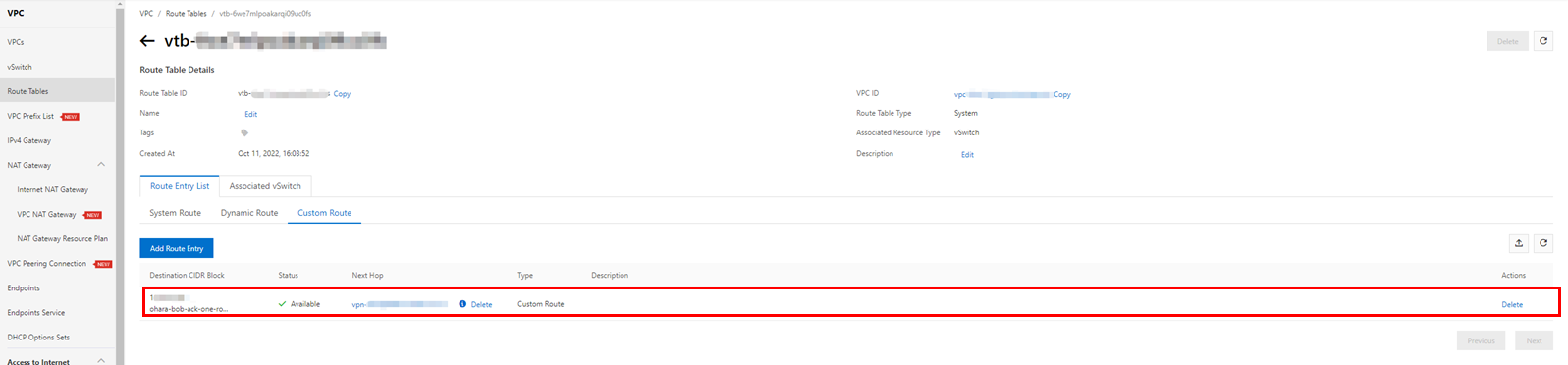
Display the route table for the selected VPC and check the custom routes in the route entry list. There should be one item corresponding to the published route entry under the VPN Gateway.
Create two virtual machines on both Alibaba Cloud and Google Cloud and confirm network connectivity using the ping command. If there is no problem with the connection configuration, the response will be something like this:
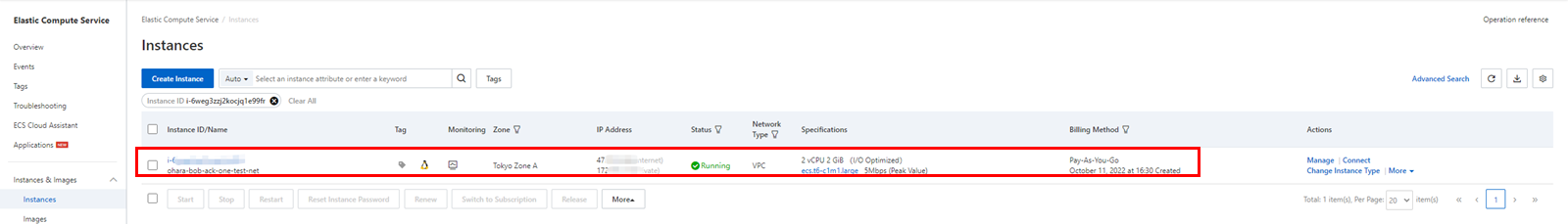
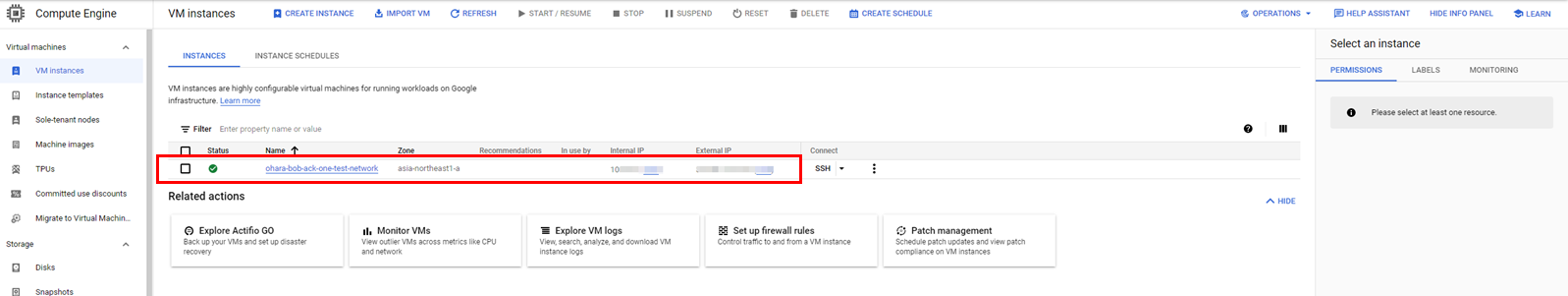
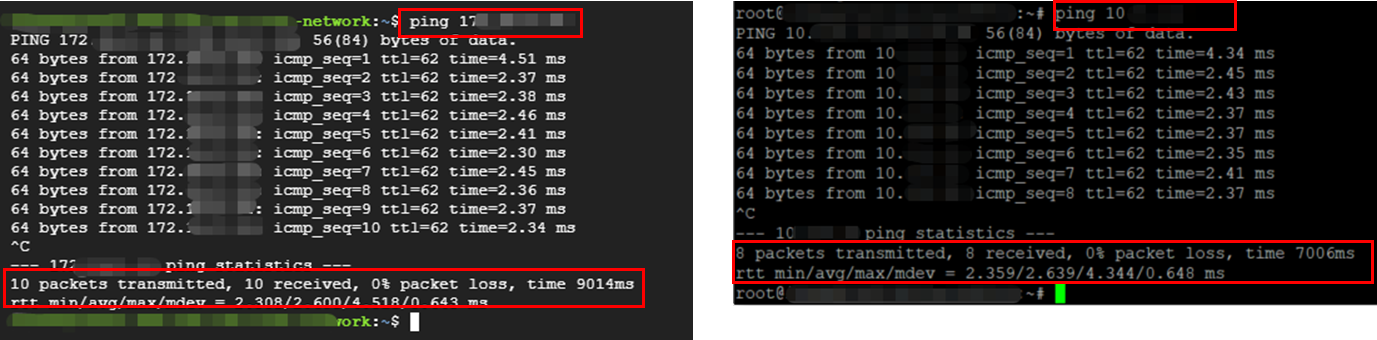
Use ACK One to build a multi-cluster service. Deploy an Alibaba Cloud ASK cluster as a service provider and a GKE cluster on Google Cloud as a provider for demo consumers to check service responses.
Prerequisites:
You can also read this article as a reference.
Reuse the YAML file for configuring the multi-cluster service in this article (in Japanese) to deploy the application, create a service exporter on the ASK cluster on Alibaba Cloud, and create a service importer on the GKE cluster on Google Cloud. Here is an example of the relevant YAML file configuration: ack-vpc-app-meta.yaml, which includes deployments and services for a distributed application.
apiVersion: v1 # The Service provider.
kind: Service
metadata:
name: service1
namespace: provider-ns
spec:
ports:
- port: 80
protocol: TCP
targetPort: 8080
selector:
app: web-demo
department: demo
sessionAffinity: None
type: ClusterIP
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: web-demo
department: demo
name: web-demo
namespace: provider-ns
spec:
replicas: 1
selector:
matchLabels:
app: web-demo
department: demo
template:
metadata:
labels:
app: web-demo
department: demo
spec:
containers:
- image: bwbw723/ack_one_demo_provider:1.0
name: web-demo
env:
- name: ENV_NAME
value: cluster1-jp-for-gke
---
apiVersion: core.oam.dev/v1beta1
kind: Application
metadata:
name: web-demo # Defining resources and propagation policies for the application
namespace: provider-ns
annotations:
app.oam.dev/publishVersion: version1
spec:
components:
- name: web-demo
type: ref-objects
properties:
objects:
- resource: deployment
name: web-demo
- resource: service
name: service1
policies:
- type: topology
name: cluster2
properties:
clusters: ["ID of the ASK cluster"] # This is the destination cluster for resource distribution. Replace it with the target cluster ID.A YAML file for configuring the service importer and exporter (ack-vpc-mcs-service-policy.yaml) will be provided separately.
apiVersion: multicluster.x-k8s.io/v1alpha1
kind: ServiceExport
metadata:
name: service1 # The value need to be the same as the name of the Kubernetes Service being exported
namespace: provider-ns # The value need to be the same as the namespace of the Kubernetes Service being exported
---
apiVersion: multicluster.x-k8s.io/v1alpha1
kind: ServiceImport
metadata:
name: service1 # The value need to be the same as the name of the Kubernetes Service being exported
namespace: provider-ns # The value need to be the same as the namespace of the Kubernetes Service being exported
spec:
ports: # the value of this field need to be the same as the port used by the Kubernetes Service being exported
- port: 80
protocol: TCP
type: ClusterSetIP
---
apiVersion: core.oam.dev/v1beta1
kind: Application
metadata:
name: amcs-export-service1
namespace: provider-ns
labels:
amcs: export
amcs-service: service1
app: web-demo
department: demo
annotations:
app.oam.dev/publishVersion: version1
spec:
components:
- name: export-service
type: ref-objects
properties:
objects:
- resource: serviceexport # Refer to ServiceExport
name: service1
policies:
- type: topology
name: export-clusters
properties:
clusters: ["ID of the ASK cluster"] # Distribute ServiceExport to ACK Cluster 2
---
apiVersion: core.oam.dev/v1beta1
kind: Application
metadata:
name: amcs-import-service1
namespace: provider-ns
labels:
amcs: import
amcs-service: service1
app: web-demo
department: demo
annotations:
app.oam.dev/publishVersion: version1
spec:
components:
- name: import-service
type: ref-objects
properties:
objects:
- resource: serviceimport # Refer to ServiceImport
name: service1
policies:
- type: topology
name: import-clusters
properties:
clusters: ["ID of the register cluster for GKE cluster"] # Distribute ServiceImport to ACK Cluster 1Update the cluster ID in the YAML configuration file before using it. The following is gke-consumer.yaml in the verification process of the multi-cluster service.
apiVersion: apps/v1
kind: Deployment
metadata:
name: demo-consumer
namespace: provider-ns
labels:
app: web-demo
department: demo
spec:
selector:
matchLabels:
app: web-demo
department: demo
strategy:
type: Recreate
template:
metadata:
labels:
app: web-demo
department: demo
spec:
containers:
- image: bwbw723/ack_one_demo_consumer:1.0
name: demo-consumer
ports:
- containerPort: 8080
name: demo-consumerIf necessary, you can upload it to an OSS bucket, download it to the Alibaba Cloud shell environment, and use it further. Alternatively, you can use it directly in your local working environment with the following steps.
Once the multi-cluster service is completed through the VPN connection, you need to access the service from Pods on the GKE cluster. Therefore, you need to make the IP range of Pods on the GKE cluster visible through the VPN connection.
In other words, in addition to the IP range of the subnet network in the steps above, you need to set a new route entry for the IP range of Pods.
Confirm the IP range of Pods and services configured in the GKE cluster:
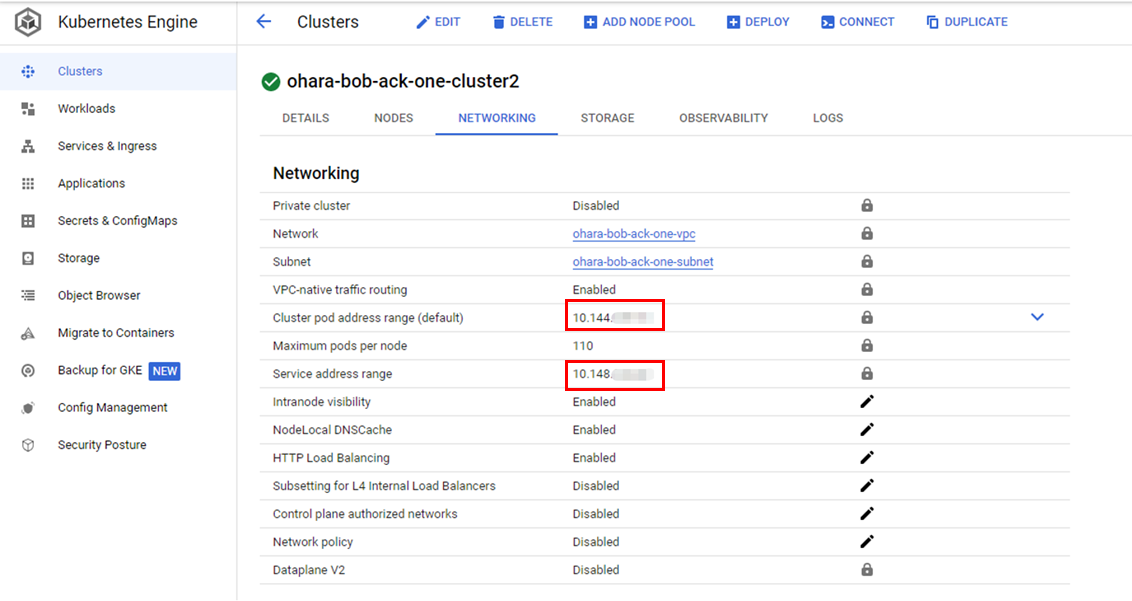
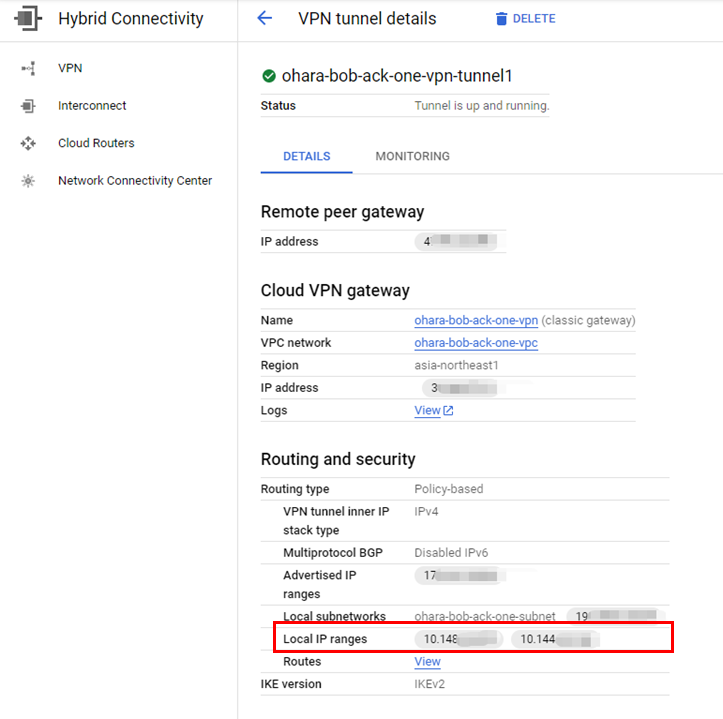
Recreate the VPN tunnel to include both the IP ranges of Pods and services:
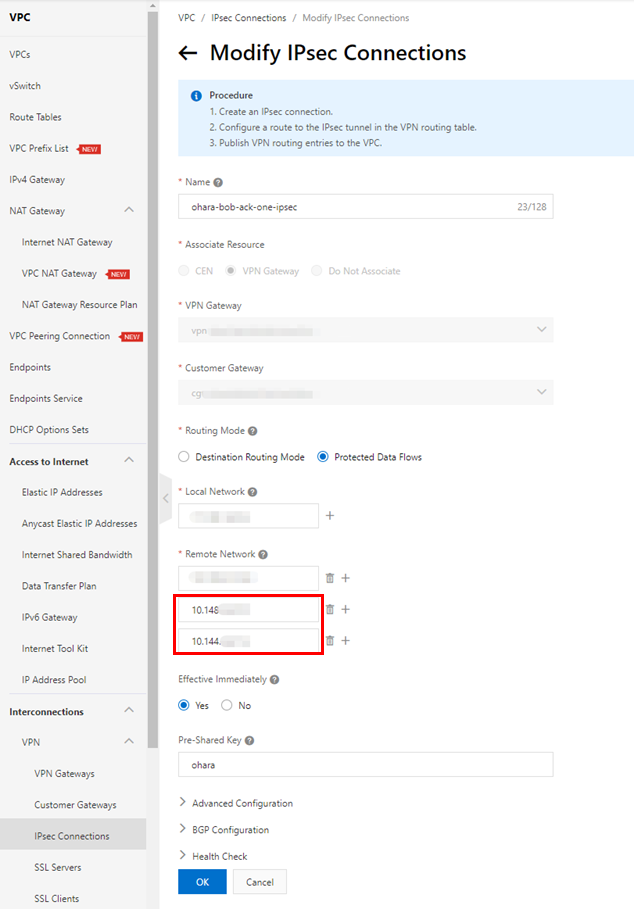
Update the Alibaba Cloud IPsec connection to add two IP ranges as remote network options:
Check the public route entry on both the VPN Gateway and vSwitch:
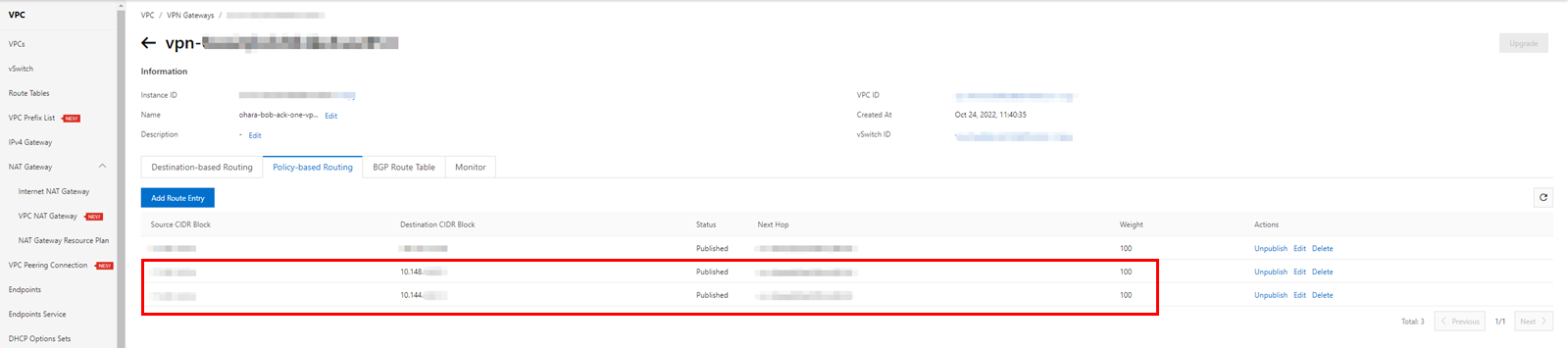
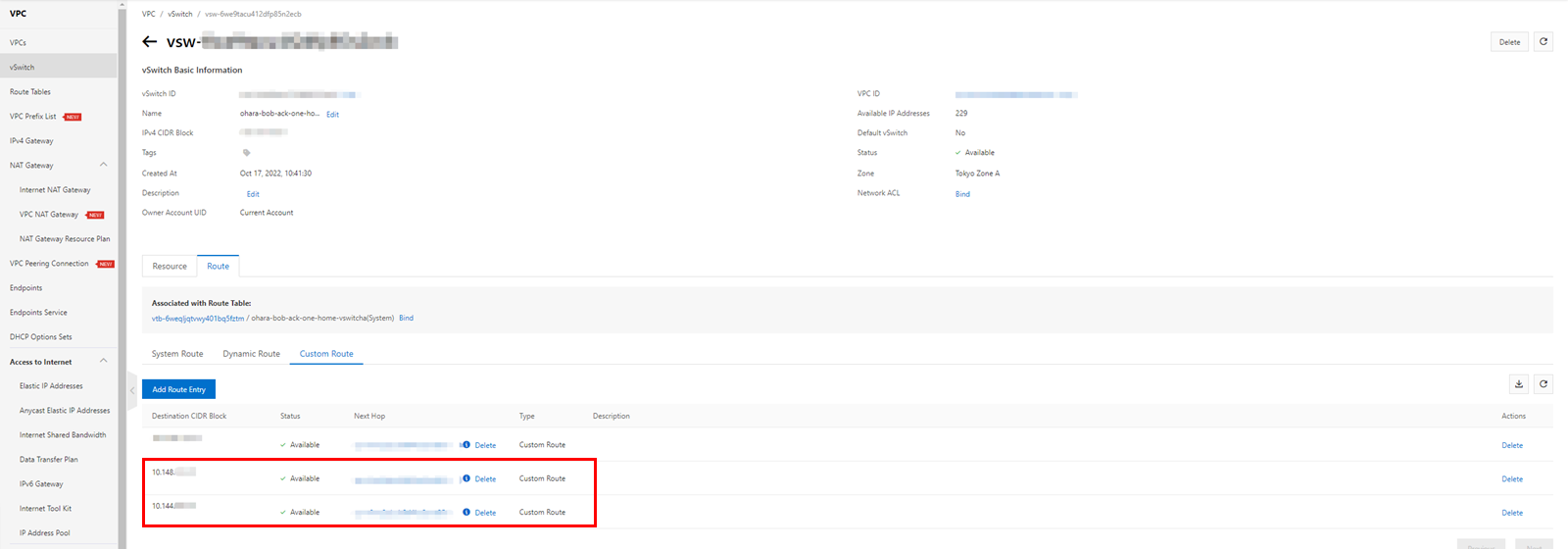
Network connections can be matched to clusters.
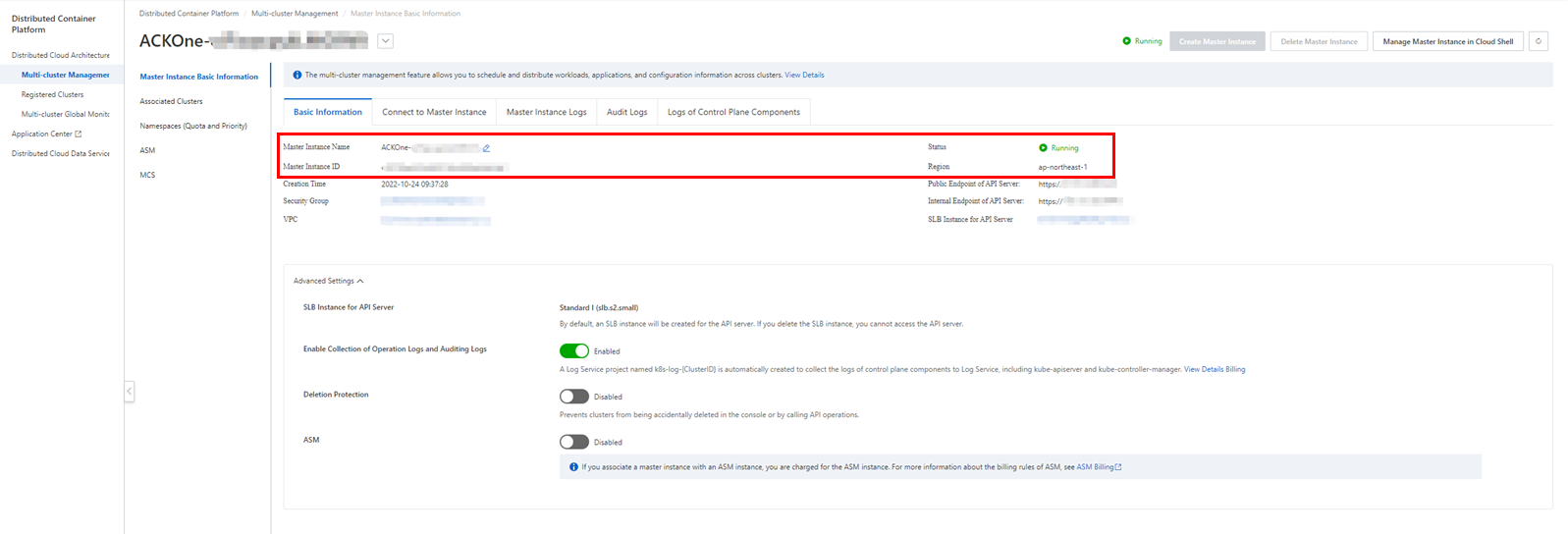
You can connect to the ACK One master instance from your working environment using Alibaba Cloud shell, just like with ASK/ACK clusters. Open the Master Instance Basic Information page on the ACK One console and click Manage Master Instance in Cloud Shell to enable Cloud Shell.
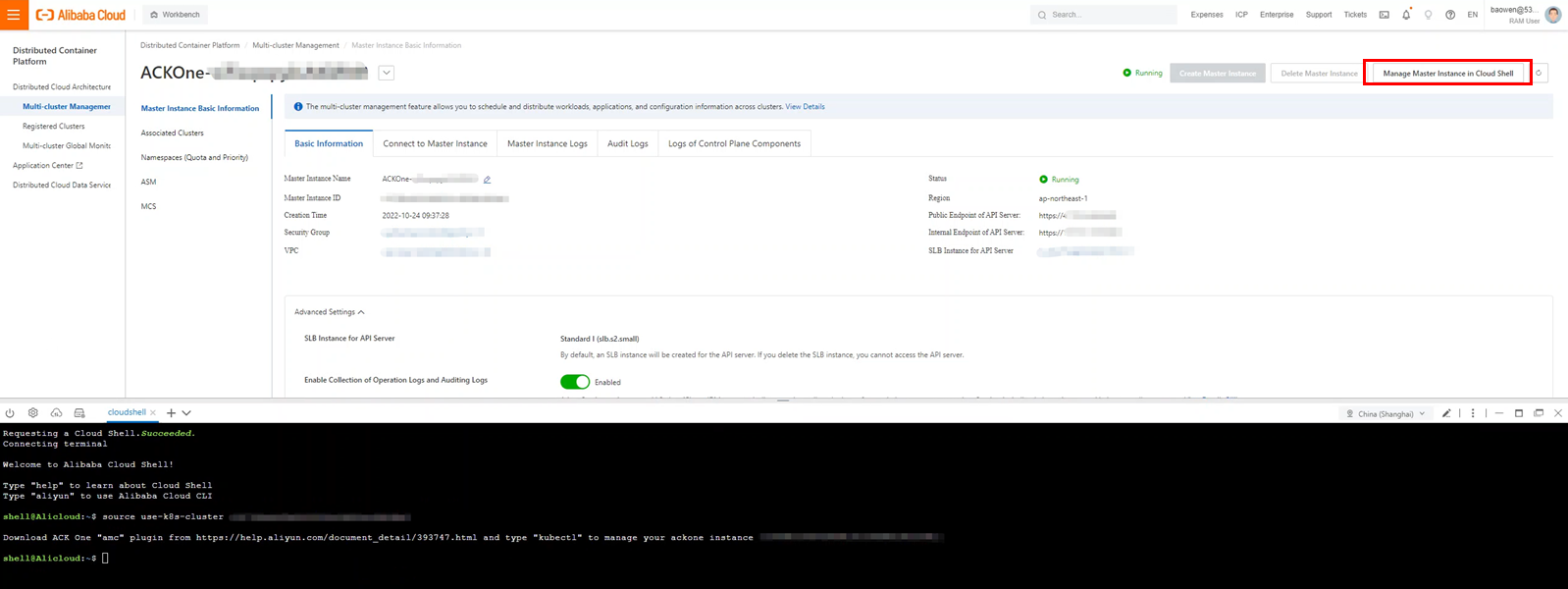
You need to install the AMC component to use the kubectl amc command.
wget http://ack-one.oss-cn-hangzhou.aliyuncs.com/kubectl-amc-linux && chmod +x kubectl-amc-linux && mv kubectl-amc-linux /usr/local/bin/kubectl-amc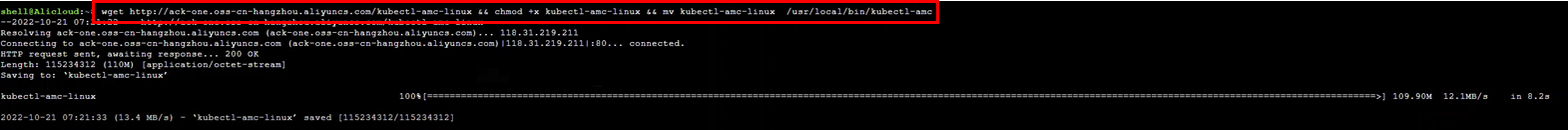
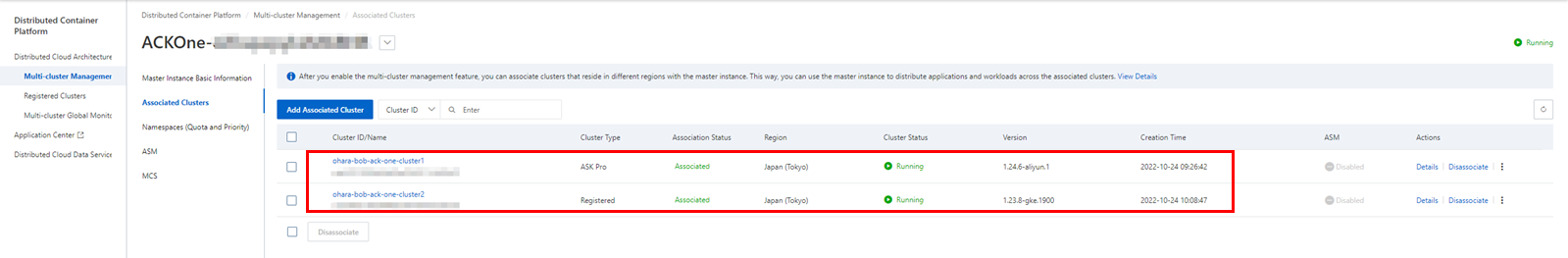
Check the clusters managed by the command. If you have successfully associated a cluster in ACK One, it should be displayed here:
kubectl amc get managedclusters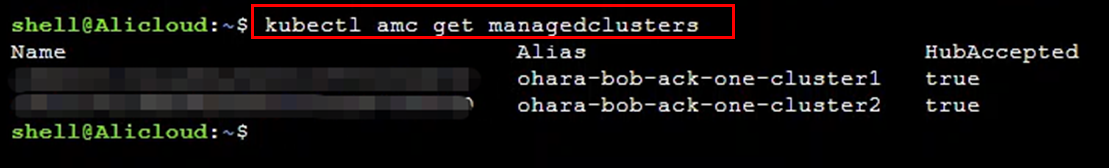
Create a new namespace called provider-ns and then create deployments and services as the following steps:
kubectl create ns provider-ns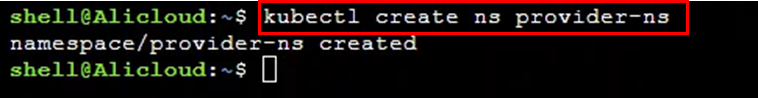
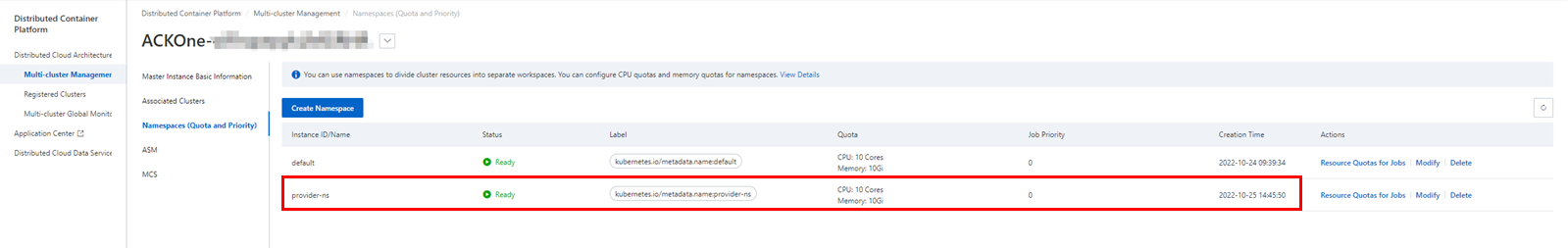
Create a distributed application that includes deployment and service using the prepared configuration YAML file. If using the image bwbw723/ack_one_demo_provider:1.0, the created service will respond with generated order information.
kubectl apply -f ack-vpc-app-meta.yaml
kubectl get app web-demo -n provider-ns
kubectl amc get deployment,service -n provider-ns -m <cluster ID>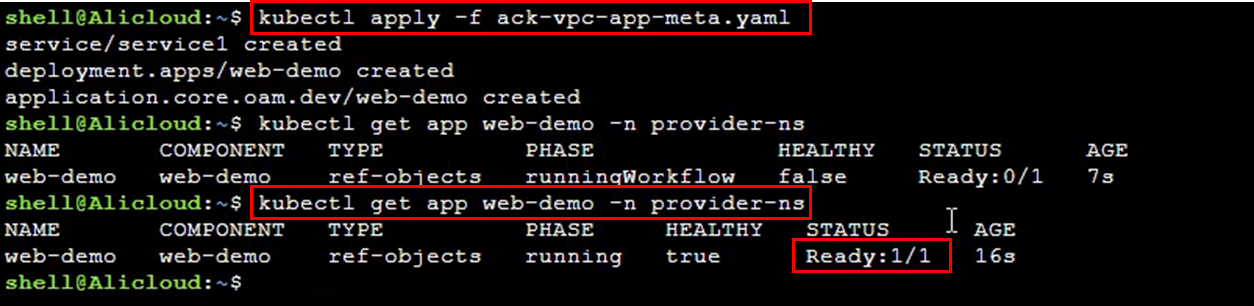
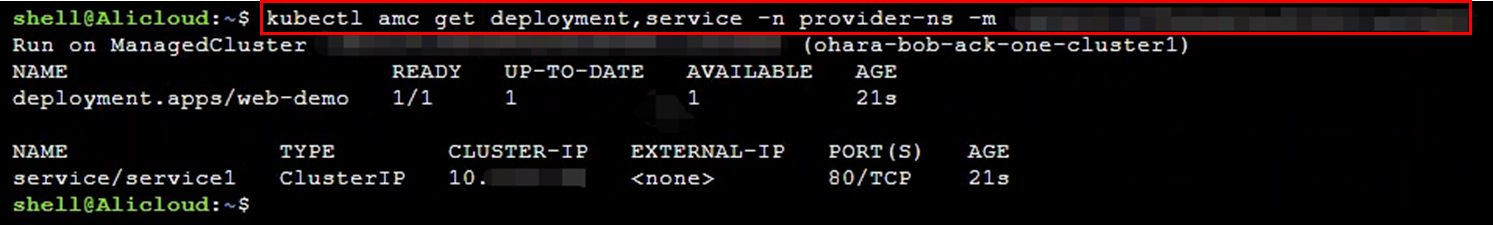
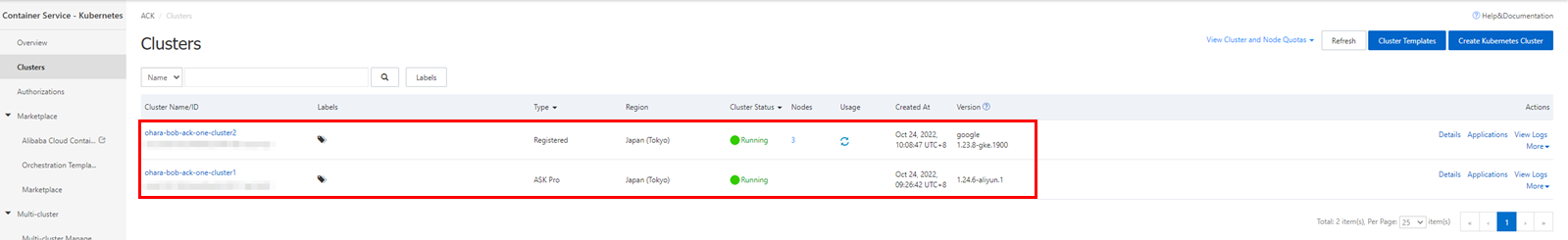
You can also check resources directly from the console. Since the application is distributed to an ASK cluster on Alibaba Cloud, the details page of the target cluster should display the relevant deployment, pods, and services.
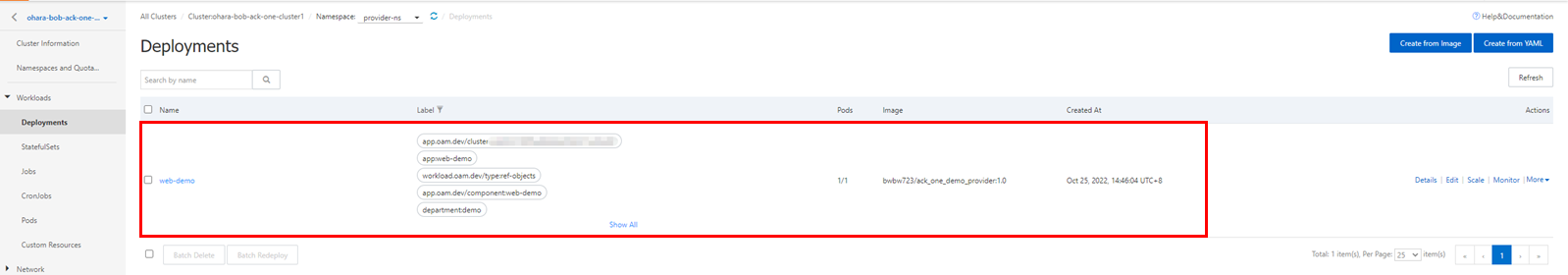
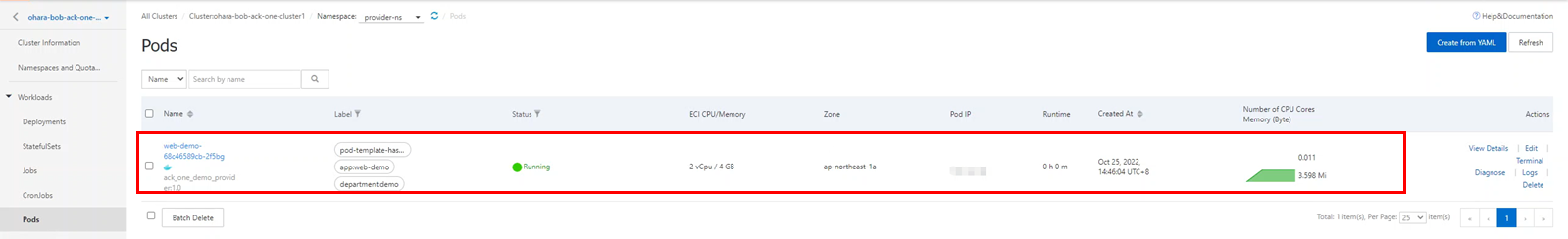
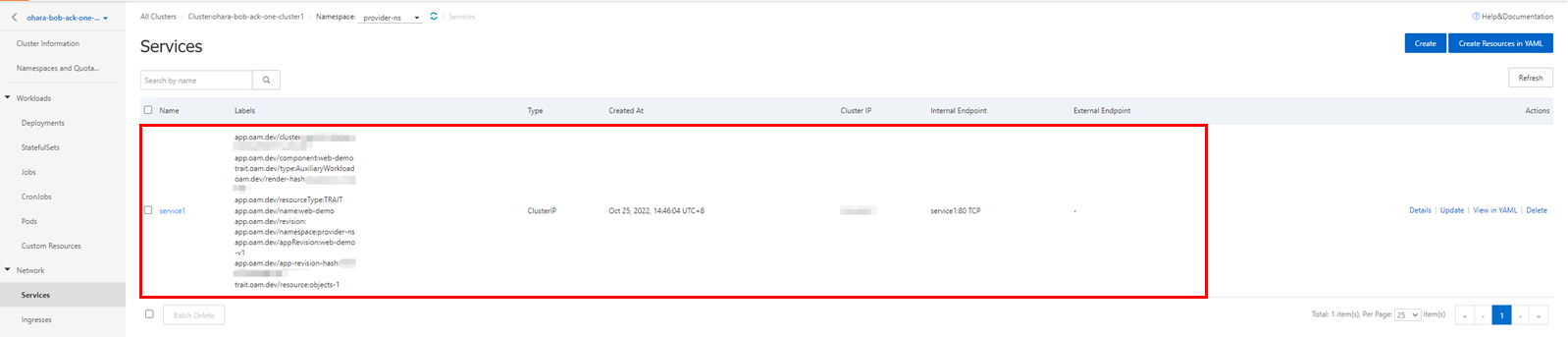
Create service importers and exporters using the kubectl command and build a multi-cluster service between the ASK and GKE clusters. You can also process it with a wizard from the console. Make sure the multi-cluster service only supports services in ClusterIP mode.
kubectl apply -f ack-vpc-mcs-service-policy.yaml
kubectl amc get serviceexport,serviceimport -n provider-ns -m all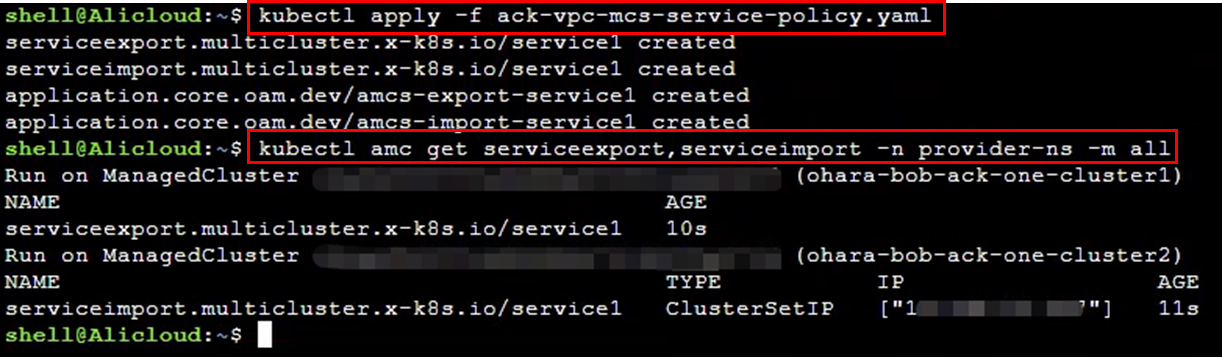
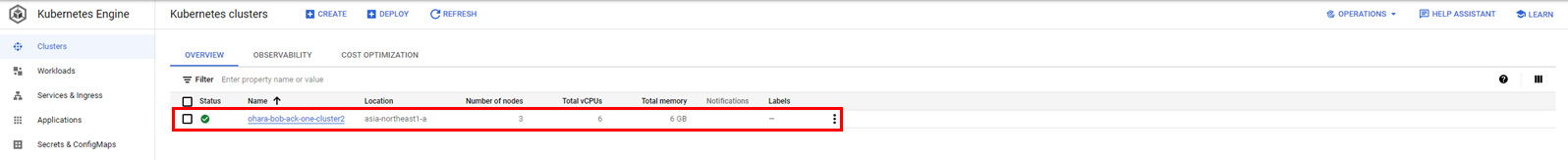
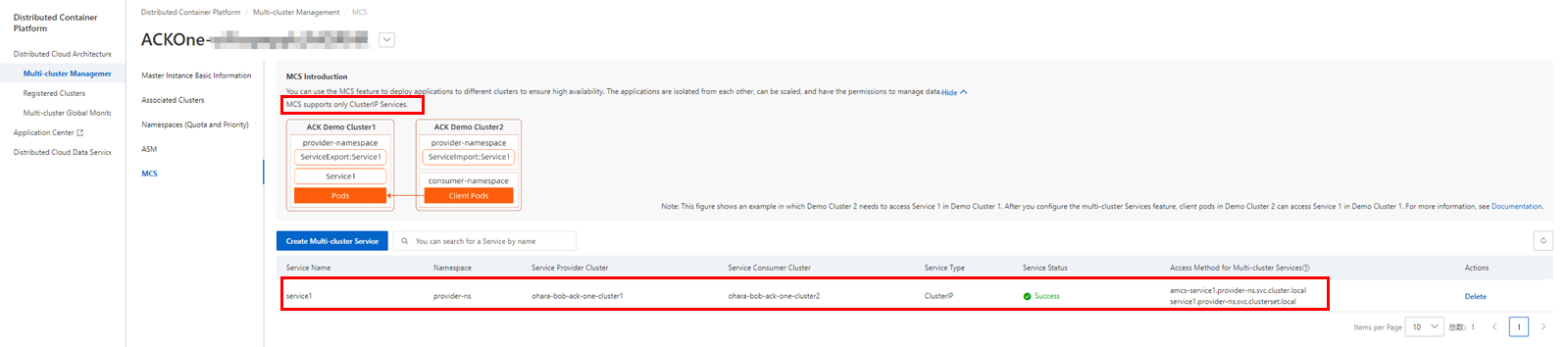
The created multi-cluster service could be confirmed from the console. The figure on the page is an example of where Demo Cluster 2 needs to access Service 1 of Demo Cluster 1.
Please check Access Method for Multi-cluster Services on the page:
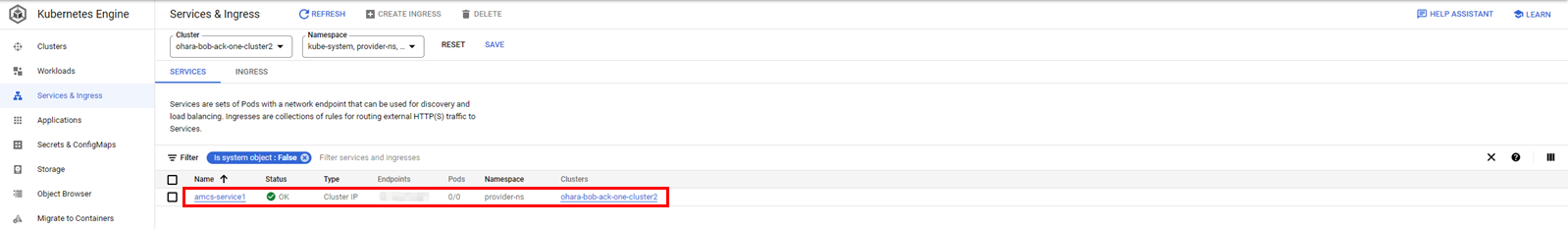
Also, a service will be created on the GKE cluster with the name acms-<name of the service in the ASK cluster>. In this case, the name of the service is acms-service1.
Since the actual response is provided by the service deployed in the ASK cluster, the target service should have a ServingPod of 0/0.
Deploy demo-consumer on the GKE cluster to access the multi-cluster service:
kubectl apply -f gke-consumer.yaml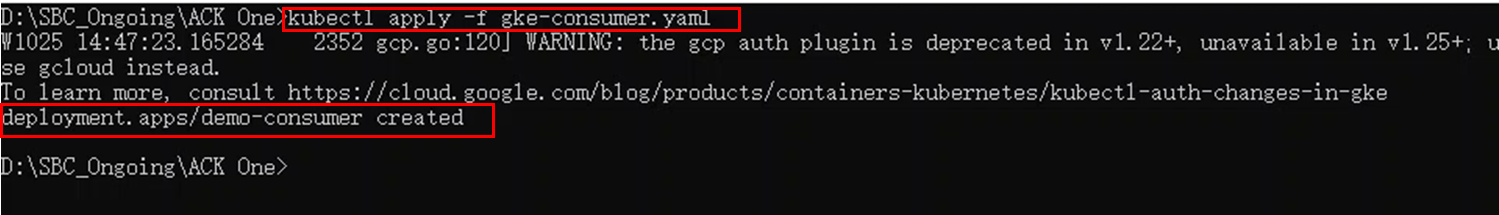
Check the Pod generated using the kubectl command:
kubectl get pod -n provider-ns
Enter the Pod and check the multi-cluster service. You can confirm the access method of the multi-cluster service found in the steps above or check the local web application on port 8080 provided by the demo-consumer image:
kubectl exec -n provider-ns -ti demo-consumer-6bf66448f7-z54nz -- sh
curl amcs-service1.provider-ns.svc.cluster.local
curl 127.0.0.1:8080
Check the security group settings and apply inbound traffic on ports 80/8080 if a connection error occurs there.
This article introduced how to connect Google Cloud Kubernetes (GKE) and Alibaba Cloud Kubernetes using ACK One to build a multi-cloud and manage Kubernetes in a unified way. Currently, various hybrid cloud and multi-cloud solutions (such as Google Cloud Anthos and Redhat Openshift) are available. However, with ACK One's simple and easy-to-manage interface, services can be managed flexibly and easily, even on a large scale. I hope this can be a reference for creating a hybrid cloud and multi-cloud using Kubernetes.
Manage Serverless Kubernetes Clusters in Alibaba Cloud ACK One:
https://www.alibabacloud.com/blog/manage-serverless-kubernetes-clusters-in-alibaba-cloud-ack-one_599848
Start Hybrid Cloud and Multi-Cloud with Alibaba Cloud ACK One [Part One]:
https://www.alibabacloud.com/blog/start-hybrid-cloud-and-multi-cloud-with-alibaba-cloud-ack-one-part-one_599689
Start Hybrid Cloud and Multi-Cloud with Alibaba Cloud ACK One [Part Two]:
https://www.alibabacloud.com/blog/start-hybrid-cloud-and-multi-cloud-with-alibaba-cloud-ack-one-part-two_599690
Manage Serverless Kubernetes Clusters in Alibaba Cloud ACK One
A Beginner's Guide to Building RESTful APIs in Python or Node.js Using Tablestore

9 posts | 0 followers
FollowHironobu Ohara - April 5, 2023
Hironobu Ohara - February 3, 2023
Alibaba Cloud Community - May 19, 2023
5544031433091282 - April 7, 2025
Hironobu Ohara - February 3, 2023
Alibaba Cloud Community - February 11, 2022

9 posts | 0 followers
Follow Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More Function Compute
Function Compute
Alibaba Cloud Function Compute is a fully-managed event-driven compute service. It allows you to focus on writing and uploading code without the need to manage infrastructure such as servers.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn MoreMore Posts by Hironobu Ohara