Join us at the Alibaba Cloud ACtivate Online Conference on March 5-6 to challenge assumptions, exchange ideas, and explore what is possible through digital transformation.
Previously, I have written an article about "Troubleshooting MaxCompute and DataWorks Permission Problems", which talks about setting permissions on MaxCompute. However, some people still want to know how to implement the permission control in DataWorks so that a specific resource, table or UDF can only be used by a specified user. The UDF may involve the encryption and decryption algorithm of data, which is within the scope of data security control.
The "package" solution, to perform fine-grained control of permissions through package authorization.
Package basics: It is often used to solve the problem of user authorization for sharing data and resources across projects. After packaging, we can see that the user has received all permissions after being given the role of DataWorks developer. This is uncontrollable.
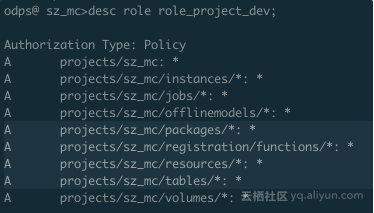
From the perspective of permission configuration, it obviously does not meet our requirements. It is obvious that the user has all permissions on packages, functions, resources and tables in the project by default.
A projects/sz_mc/packages/*: *
A projects/sz_mc/registration/functions/*: *
A projects/sz_mc/resources/*: *
A projects/sz_mc/tables/*: *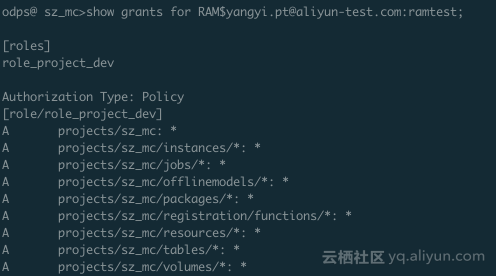
Create a new role on DataWorks (Management > MaxCompute Advanced Configuration > Custom User Role) for advanced control. However, in the advanced configuration of DataWorks-MaxCompute, only a table or a project can be authorized, and the resource and UDF cannot be authorized.
The "role policy" solution. Through a policy, we can finely manage the specific permission granularity of specific users for specific resources, which can meet our scenario requirements. However, the official documentation of the policy mechanism has not been disclosed, the main consideration of which is whether the user is familiar with the policy or not. If not, it will likely cause problems and reduce development efficiency.
For security, it is recommended that beginners use a test project to verify the policy. The following operations are completed through MaxCompute console. For details, see the console configuration.
Create a denyudfrole role, as follows:
odps@ sz_mc>create role denyudfrole;Create a policy authorization file, as follows:
{
"Version": "1", "Statement":
[{
"Effect":"Deny",
"Action":["odps:Read","odps:List"],
"Resource":"acs:odps:*:projects/sz_mc/resources/getaddr.jar"
},
{
"Effect":"Deny",
"Action":["odps:Read","odps:List"],
"Resource":"acs:odps:*:projects/sz_mc/registration/functions/getregion"
}
] }Set up and view the role policy. As follows:
odps@ sz_mc>put policy /Users/yangyi/Desktop/role_policy.json on role denyudfrole;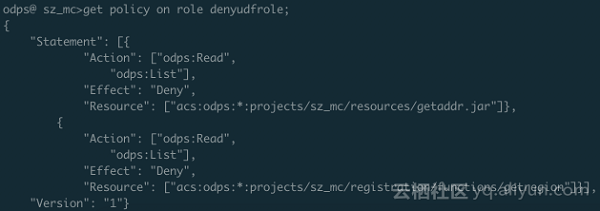
Add users to the denyudfrole role.
odps@ sz_mc>grant denyudfrole to RAM$yangyi.pt@aliyun-test.com:ramtest;Now, we verified whether the MaxCompute console can be logged in with the RAM user RAM$yangyi.pt@aliyun-test.com:ramtest.
Log in to the console to confirm the role.
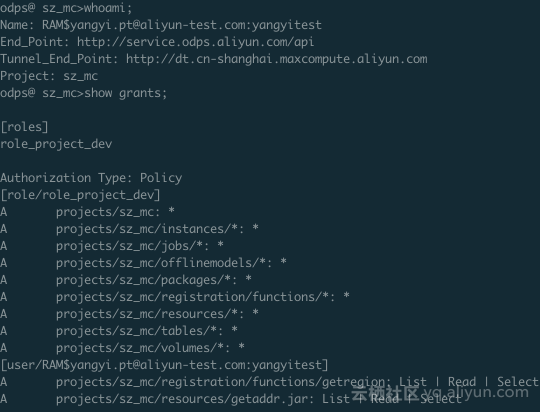
Check the permission of the current logged in user through "show grants".
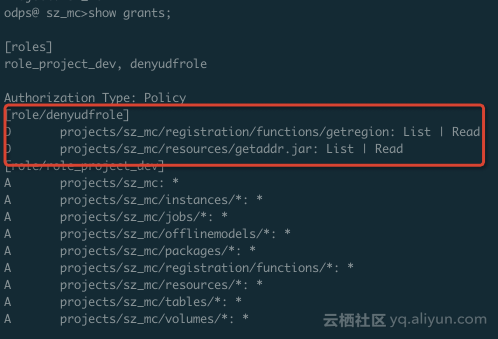
As you can see, this RAM user has two roles, one is role_project_dev, which is actually the default DataWorks developer role, and the other is denyudfrole that we just created by ourselves.
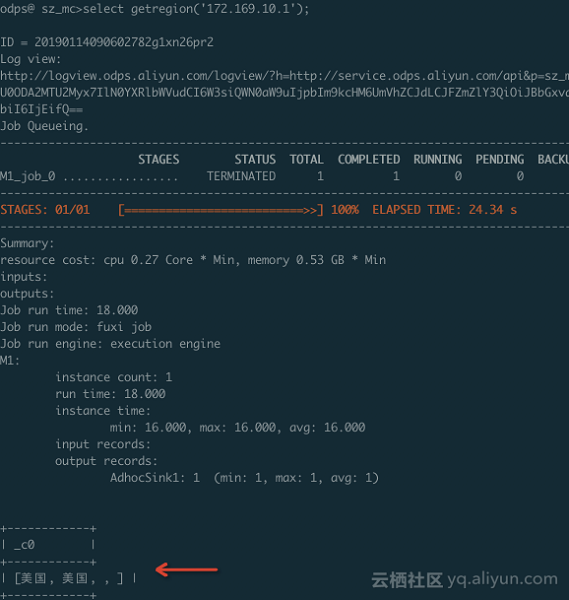
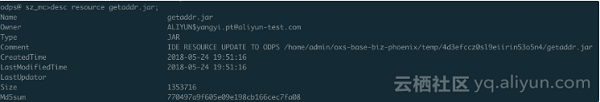
Verify the permissions of the self-built UDF and the dependent package.
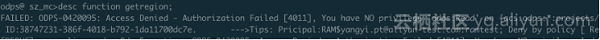
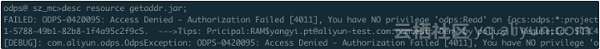
The verification is successful. The RAM user does not have the read permission of self-built UDF "getregion" under the premise of having the DataWorks developer role. However, we are still one step away from our expectation that only specified users can access the UDF. This expectation can be achieved in conjunction with a project policy.
Write a policy.
{
"Version": "1", "Statement":
[{
"Effect":"Allow",
"Principal":"RAM$yangyi.pt@aliyun-test.com:yangyitest",
"Action":["odps:Read","odps:List","odps:Select"],
"Resource":"acs:odps:*:projects/sz_mc/resources/getaddr.jar"
},
{
"Effect":"Allow",
"Principal":"RAM$yangyi.pt@aliyun-test.com:yangyitest",
"Action":["odps:Read","odps:List","odps:Select"],
"Resource":"acs:odps:*:projects/sz_mc/registration/functions/getregion"
}] }Set and view the policy.
odps@ sz_mc>put policy /Users/yangyi/Desktop/project_policy.json;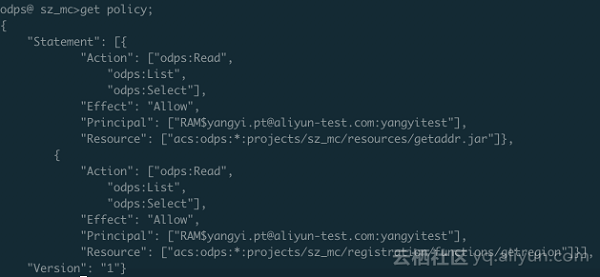
To verify:
To run a SQL:
To view the dependent packages:
Now, we have fulfilled our requirements. Only the specified RAM user can access the specified UDF and dependent packages under the specified project.
At this point, some people may have a clear understanding of the security systems of DataWorks and MaxCompute, while others may still be confused. The summary is as follows:
MaxCompute and DataWorks Security Management Guide: Examples
Converting JSON-formatted Log Data with MaxCompute Built-in Functions and UDTF

137 posts | 21 followers
FollowAlibaba Cloud MaxCompute - October 31, 2022
JDP - June 25, 2021
JDP - May 20, 2021
Farruh - January 12, 2024
Alibaba Cloud MaxCompute - April 25, 2019
Alibaba Cloud MaxCompute - February 15, 2019

137 posts | 21 followers
Follow Big Data Consulting for Data Technology Solution
Big Data Consulting for Data Technology Solution
Alibaba Cloud provides big data consulting services to help enterprises leverage advanced data technology.
Learn More MaxCompute
MaxCompute
Conduct large-scale data warehousing with MaxCompute
Learn More Big Data Consulting Services for Retail Solution
Big Data Consulting Services for Retail Solution
Alibaba Cloud experts provide retailers with a lightweight and customized big data consulting service to help you assess your big data maturity and plan your big data journey.
Learn More RAM(Resource Access Management)
RAM(Resource Access Management)
Secure your cloud resources with Resource Access Management to define fine-grained access permissions for users and groups
Learn MoreMore Posts by Alibaba Cloud MaxCompute