This topic describes basic concepts related to Anti-DDoS services.
DDoS attack
A distributed denial-of-service (DDoS) attack includes volumetric attacks and application-layer attacks.
A volumetric attack targets the network bandwidth of a service. Attackers typically use multiple controlled computers or attack simulators to send a high volume of requests or data packets to the target server. This exhausts the network bandwidth and makes the service unavailable.
An application-layer attack targets servers. During these attacks, malicious requests exhaust the server's memory or CPU resources. As a result, the server cannot respond to normal requests.
Traffic scrubbing
Traffic scrubbing uses professional anti-DDoS devices or services to analyze and filter traffic. It distinguishes normal traffic from attack traffic and forwards only the normal traffic back to the origin server. This reduces the load and risk on the server.
Blackhole filtering
Blackhole filtering is triggered when DDoS attack traffic exceeds the maximum mitigation capability of the scrubbing service. To protect the availability of other services on the same network, all traffic to the target IP address is dropped. For more information, see Blackhole filtering policy of Alibaba Cloud.
Web resource exhaustion attack
A web resource exhaustion attack is a malicious request attack that targets application-layer protocols, such as HTTP and HTTPS. The attack mimics the access behavior of real users, such as logon, registration, and search, to consume the application resources of the target site. As a result, the target site cannot respond to normal requests.
Connection flood attack
A connection flood attack is a malicious session attack at the transport layer. Attackers use multiple zombie terminals to send many TCP requests to the target website. These requests consume resources of the target server, such as connections, CPU, and memory. As a result, the target server cannot respond to normal requests.
Volumetric attack
A volumetric attack targets network bandwidth. Attackers typically use multiple controlled computers or packet generators to send a high volume of requests or data packets to the target server. This exhausts the network bandwidth and makes normal services inaccessible.
Best-effort protection (Anti-DDoS Pro and Anti-DDoS Premium)
The Anti-DDoS Pro and Anti-DDoS Premium cluster uses all available resources to provide best-effort protection. However, if an attack exceeds the maximum mitigation capability of the cluster, blackhole filtering may be triggered. For more information, see Billing of Anti-DDoS Pro (the Chinese mainland).
Burstable protection
Burstable protection is a DDoS mitigation feature available in the Professional Edition of Anti-DDoS Pro (the Chinese mainland). If a DDoS attack exceeds the basic protection bandwidth, you can set a maximum attack traffic threshold for Anti-DDoS Pro (the Chinese mainland). This threshold is known as the burstable protection bandwidth. If the peak DDoS attack traffic exceeds the basic protection bandwidth but is less than your configured burstable protection bandwidth, burstable protection is triggered. When this occurs, burstable protection fees are charged for the day of the attack. For more information, see Billing method of burstable protection bandwidth.
Advanced mitigation
Advanced mitigation, also known as best-effort protection, aims to successfully defend against every DDoS attack. It integrates the capabilities of all Anti-DDoS scrubbing centers in the current Alibaba Cloud region to fully protect your services.
If an Anti-DDoS Proxy instance receives more than 5 Gbit/s of DDoS attack traffic, an advanced mitigation session that is provided for the instance is consumed. The advanced mitigation session protects the instance for 24 hours. All DDoS attacks that occur on the Anti-DDoS Proxy instance within 24 hours consume the same advanced mitigation session.
The following instance editions provide advanced mitigation:
Anti-DDoS Pro (the Chinese mainland): Premium Edition
Anti-DDoS Premium (outside the Chinese mainland): Insurance, Unlimited, and Sec-MCA (including Sec-MCA 1.0, Sec-CMA (Basic), Sec-MCA 2.0 (Insurance), and Sec-MCA 2.0 (Unlimited)) mitigation plans
For more information, see Billing of Anti-DDoS Pro (the Chinese mainland), Billing of the Insurance and Unlimited mitigation plans for Anti-DDoS Premium (outside the Chinese mainland), and Billing of the Sec-MCA mitigation plan for Anti-DDoS Premium (outside the Chinese mainland).
Anycast
Anti-DDoS Premium (outside the Chinese mainland) uses the anycast communication pattern. It leverages the capabilities of Alibaba Cloud scrubbing centers around the world as resources for the Anti-DDoS Premium (outside the Chinese mainland) service. Anycast is a network addressing and routing method where messages sent to an anycast address are routed to a specific group of servers identified by that address.
Anti-DDoS Premium (outside the Chinese mainland) uses the anycast method to route incoming traffic to the nearest scrubbing center with mitigation capabilities. This routing method enables scheduling to prioritize service availability, even during high concurrent traffic and network congestion. However, this scenario may involve cross-border data transmission. For more information, see Cross-border data transmission.
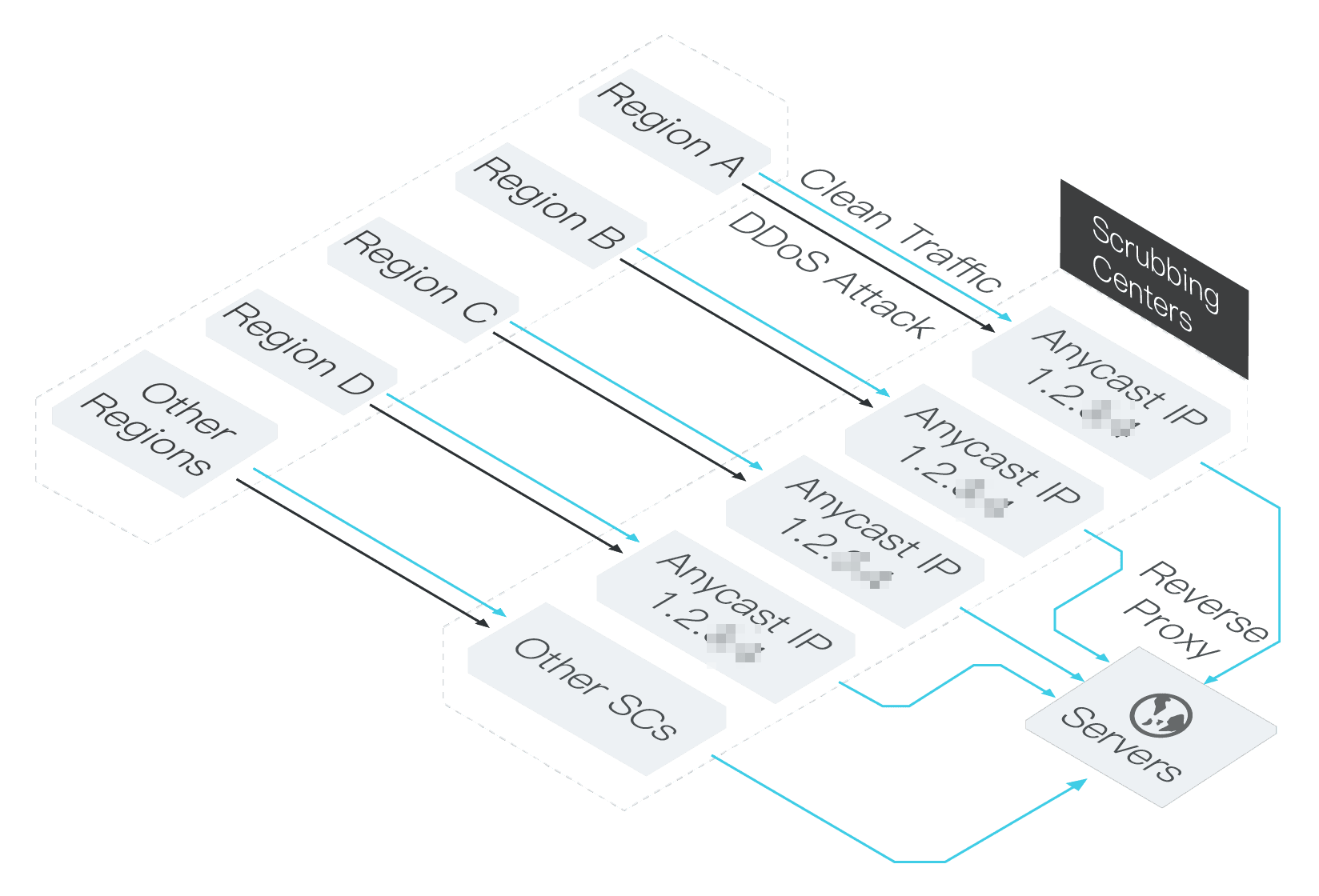
An anycast address can route incoming traffic to multiple data centers. When access traffic arrives at an IP address attached to an anycast address, the traffic is distributed to different data centers based on the configured distribution method. Typically, traffic is distributed to the data center closest to the traffic source. Anti-DDoS Premium (outside the Chinese mainland) has access points in the following regions to help you connect to Alibaba Cloud.
Area | Region |
Asia Pacific | China (Hong Kong), Singapore, Japan, Malaysia, Indonesia |
North America | US (Silicon Valley), US (Virginia) |
Europe | UK (London), Germany (Frankfurt) |
For example, assume that the anycast IP address of an Anti-DDoS Premium (outside the Chinese mainland) instance is 170.x.x.x. All Alibaba Cloud scrubbing centers outside the Chinese mainland advertise the route to this IP address. When a data packet is sent to this IP address, it passes through a series of routes and is sent to the node with the shortest path (fewest route hops). The shortest path is determined by checking the available paths to each node in the Alibaba Cloud scrubbing centers outside the Chinese mainland. If a server at a node fails and becomes unavailable, the advertisement for the unavailable IP segment is immediately stopped. Packets are then routed to the nearest available service node based on the shortest path principle.
By default, traffic from users in Hong Kong (China) is routed to the Alibaba Cloud Anti-DDoS scrubbing center in China (Hong Kong).