Hybrid cloud access is an Alibaba Cloud solution for Web Application Protection and service traffic management for businesses with services deployed outside of Alibaba Cloud. If your services are deployed on third-party public clouds, private clouds, or on-premises data centers, you can use the hybrid cloud access mode to centrally manage and maintain your web services on the cloud and on-premises using Web Application Firewall (WAF). This topic describes what hybrid cloud access is and how to deploy it.
What is hybrid cloud access?
Hybrid cloud access is a product model that extends cloud-based protection components to other cloud platforms or on-premises data centers. Its primary purpose is to provide an integrated web application security management solution that combines on-premises and cloud-based capabilities.
Scenarios
Protecting on-premises web services whose traffic cannot be directed to the public cloud due to specific business requirements.
Providing a unified web service protection solution for services deployed across Alibaba Cloud, other public clouds, private clouds, on-premises data centers, and VPC intranets.
Providing unified protection for latency-sensitive and high-reliability services that require active-active disaster recovery across multiple network environments.
Benefits
Allows for unified management and control of cloud-based and on-premises assets and mitigation policies.
The localization deployment solution protects customer services from a nearby location.
Synchronizes cloud-based mitigation rules and threat intelligence in real time.
Protects both internet and intranet services simultaneously.
Allows for traffic diversion and bypass detection at a unified access layer. It supports manual and automatic bypass to ensure timely failover if the WAF cluster fails.
Connection types
Connection type | Principle | Scenarios |
Reverse proxy connection | In reverse proxy mode, you need to add the website domain name or IP address to WAF and point the DNS record to the WAF protection cluster endpoint. The Hybrid Cloud WAF cluster performs security checks on all proxied access requests. | This mode is suitable for scenarios where the network architecture can be modified and the service traffic volume is not excessively large. Examples include the Internet, retail, government, finance, and media industries. |
SDK integration | In SDK integration mode, you need to deploy an SDK plug-in on the unified access gateway. The SDK plug-in copies the service traffic from the gateway to the WAF protection cluster. In this mode, the Hybrid Cloud WAF protection cluster does not participate in traffic forwarding, which separates service forwarding from detection. | This mode is suitable for users who have a unified access layer gateway (such as Nginx or APISIX), possess O&M capabilities, and have large traffic volumes with high requirements for latency and stability. Examples include leading Internet customers and customers with special requirements for forwarding features. |
When selecting a hybrid cloud connection type, you must choose one based on your network architecture and requirements. The following section describes common scenarios and explains how to select the appropriate connection type.
Public service portal of an enterprise
Background: The portal provides various online services and information query features. The website requires strict security protection because it involves sensitive data. In addition, the website traffic is relatively stable, and some adjustments to the network architecture are acceptable.
Recommended connection type: Reverse proxy mode
Reasons:
Ease of deployment: The deployment steps for the reverse proxy mode are relatively simple. The main task is to direct traffic to WAF through DNS configuration. This method does not require complex adjustments to the existing internal network structure or the deployment of plug-ins or software at each endpoint. It is suitable for teams with basic O&M capabilities to implement quickly.
Simple architecture adjustment: Because the website traffic is relatively stable, you can adjust DNS settings to point traffic to WAF without affecting the user experience.
Easy management and monitoring: Using a reverse proxy, you can centrally configure and manage security policies and rules on the WAF platform, which simplifies security policy implementation.
Large social e-commerce platform
Background: A company with large-scale, high-concurrency services has strict requirements for system performance, stability, and security. The company wants to enhance its application security detection capabilities without changing the existing architecture or user experience. Because the application's users are widely distributed and the traffic characteristics are complex, the company needs a solution that can effectively detect and protect against potential threats.
Recommended connection type: SDK integration
Reasons:
A platform that prioritizes user experience has extremely high requirements for access latency and system stability. The SDK integration mode reduces extra redirects and prevents traffic from passing through additional proxy nodes, which lowers the overall access latency.
The SDK integration mode separates service traffic forwarding from security detection, which offers multiple advantages for a social platform:
Improved system stability: Even if the WAF protection cluster encounters issues, it does not directly affect service traffic forwarding or overall system availability.
Independent scaling: The WAF protection cluster can be independently scaled out based on business growth to ensure that security protection capabilities keep pace with business requirements.
The platform already uses a unified access layer gateway, such as Nginx or APISIX, to manage and distribute traffic. The SDK integration mode is particularly suitable for this architecture:
Seamless integration: By deploying the WAF SDK plug-in on the existing gateway, you can more conveniently integrate and manage security protection without making large-scale adjustments to the existing network architecture.
Flexible configuration: You can flexibly configure WAF policies and rules as needed to meet evolving security requirements.
Limits
Hybrid cloud access does not support the web tamper-proofing feature.
Prerequisites
You have activated a subscription Enterprise or Ultimate instance. For more information, see Purchase a subscription WAF 3.0 instance.
NoteSubscription Basic, Pro, or pay-as-you-go instances do not support hybrid cloud access.
You have prepared the required resources. For more information about the recommended number of resources, see Prepare cluster resources.
NoteA hybrid cloud cluster consists of management, storage, and protection components. To ensure high cluster stability, we recommend that you deploy different components separately. If a component contains multiple nodes, we recommend that you deploy a load balancing device in front of the nodes.
Step 1: Install the WAF client
Introduction to the WAF client
A hybrid cloud cluster uses your local servers to deploy WAF protection nodes. Before you deploy a hybrid cloud cluster, you must install the WAF client, vagent, on the local servers that are planned as cluster nodes.
The vagent is used for the following purposes:
Communicates with the Alibaba Cloud WAF server to pull Hybrid Cloud WAF installation and upgrade images from the cloud.
Monitors and reports the running status of hybrid cloud components to ensure WAF service availability.
Synchronizes cloud-based configuration information in real time, including forwarding configurations, mitigation rules, and threat intelligence, to ensure the real-time effectiveness of Hybrid Cloud WAF protection.
The vagent can be installed only on Linux servers using an RPM package. The following 64-bit Linux operating systems are supported: AliOS 3.2104, Tencent OS 3.1, CentOS 7, Red Hat 7, and Kylin V10 (x86). The kernel version must be 4.10 or later.
CentOS 7 is no longer maintained, and Alibaba Cloud will stop supporting this operating system. Users who are using CentOS 7 are not affected, but images are no longer updated.
Procedure
Log on to your local server.
Obtain the latest version of vagent and download it to your local server.
Method: To obtain vagent, submit a ticket to contact a product technical expert.
Install vagent.
Run the following command to install vagent on the local server.
sudo rpm -ivh t-yundun-vagent-xxxxxxx.xxxxx.rpmNoteReplace
xxxxxxx.xxxxxwith the version number of the vagent that you downloaded.After the installation is complete, run the following command to view the version number of the installed vagent and confirm that you have installed the latest version.
rpm -qa|grep vagent
Modify the vagent connection configuration.
After you install vagent, you must modify the configurations for communication between vagent and the Alibaba Cloud server based on the Hybrid Cloud WAF connection type. The following steps describe the procedure:
Run the following command to open the vagent configuration file in edit mode.
sudo vi /home/admin/vagent/conf/vagent.tomlPress the i key to enter edit mode, and then modify or add the following content:
domain="wafopenapi.cn-hangzhou.aliyuncs.com" //The endpoint of the Hybrid Cloud WAF service. For more information about the value, see Hybrid cloud access. access_key_id=***************** //The AccessKey ID of your Alibaba Cloud account. access_key_secret=***************** //The AccessKey secret of your Alibaba Cloud account.Table 1. domain values
WAF service region
Hybrid Cloud WAF connection type
domain value
the Chinese mainland
Internet access (The hybrid cloud cluster connects to the On-cloud WAF console over the Internet)
wafopenapi.cn-hangzhou.aliyuncs.comPrivate connection over Express Connect (The hybrid cloud cluster connects to the On-cloud WAF private console over an Express Connect circuit. You can use this mode only after you have set up an Express Connect circuit)
NoteCurrently, VPC-connected instances in the China (Hangzhou), China (Shanghai), and China (Beijing) regions are supported. If your VPC-connected instance is in another region in the Chinese mainland, submit a ticket to contact a product technical expert.
wafopenapi.vpc-proxy.aliyuncs.comoutside the Chinese mainland
Internet access (The hybrid cloud cluster connects to the On-cloud WAF console over the Internet)
wafopenapi.ap-southeast-1.aliyuncs.comPrivate connection over Express Connect (The hybrid cloud cluster connects to the On-cloud WAF private console over an Express Connect circuit. You can use this mode only after you have set up an Express Connect circuit)
NoteIf your VPC-connected instance is in a region outside the Chinese mainland, submit a ticket to contact a product technical expert.
wafopenapi-intl.vpc-proxy.aliyuncs.comPress the Esc key to exit edit mode.
Enter :wq and press the Enter key to save the changes and exit.
Start vagent.
Run the following command to start vagent.
sudo systemctl start vagentRun the following command to enable vagent to automatically start at system startup.
sudo systemctl enable vagentAfter you set vagent to automatically start at boot, you receive the following message, which indicates that the setting is successful:
Created symlink from /etc/systemd/system/multi-user.target.wants/vagent.service to /usr/lib/systemd/system/vagent.service.
If the startup fails, you can use the following methods to query the vagent log information for analysis:
Query using the systemd tool. The query command is as follows:
sudo journalctl -u vagentQuery using the vagent log file. The query command is as follows:
tail /home/admin/vagent/logs/vagent.log
You can also run the following commands to stop or view vagent:
Verify the installation.
In Linux, you can run the following command to verify whether vagent is installed.
ps aux | grep AliYunDunWafIf the output contains the
AliYunDunWafprocess, vagent is installed and running on the local server, and can communicate with the Alibaba Cloud WAF server. In this case, you can add the server as a local WAF protection node by deploying a cluster configuration.If the output does not contain the
AliYunDunWafprocess, we recommend that you check whether you have correctly performed the installation steps and try to install and start vagent again. If the installation still fails after you retry, submit a ticket to contact a product technical expert.
Step 2: Deploy a hybrid cloud cluster
Visit the Web Application Firewall purchase page, configure Additional Hybrid Cloud Protection Nodes.
NoteOnly subscription Enterprise and Ultimate instances support hybrid cloud access. Subscription Basic, Pro, or pay-as-you-go instances do not support this connection type.
A single cluster must have at least two protection nodes deployed. A single protection node can protect HTTP services with a maximum of 5,000 QPS or HTTPS services with a maximum of 3,000 QPS. You can select the number of cluster nodes based on the QPS of the website services that you want to protect and scale out performance by adding more protection nodes.
Log on to the WAF 3.0 console. In the top navigation bar, select the resource group and region of the WAF instance. You can select Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, click Hybrid Clouds.
On the Hybrid Clouds page, click Add Cluster.
In the Basic Information Configuration step of the wizard, configure the following parameters and click Next.
Configuration item
Description
Cluster Name
Specify a name for the hybrid cloud cluster.
Cluster Type
Select the type of hybrid cloud cluster that you want to create. Valid values:
Reverse Proxy Mode: If you select this mode, WAF serves as a reverse proxy cluster for service forwarding and protection.
SDK Integration Mode: If you select this mode, you must deploy an SDK plug-in on the unified access layer gateway. The SDK plug-in copies traffic to the WAF protection cluster. In this mode, the WAF protection cluster does not participate in traffic forwarding.
If the WAF cluster is abnormal, you can Enable Manual Bypass. After you enable manual bypass, the WAF protection cluster immediately enters the bypass state. The SDK corresponding to the cluster no longer forwards traffic to the WAF cluster, and your services bypass WAF protection.
ImportantAfter you select a Cluster Type, you cannot change it. We recommend that you plan the hybrid cloud cluster that you want to create before you configure it.
Protection Nodes
Select the number of protection nodes that the hybrid cloud cluster contains.
NoteThe total number of nodes that you add to all custom hybrid cloud clusters cannot exceed the purchased Additional Hybrid Cloud Protection Nodes specification.
Server Port
Set the protection ports that are used by the hybrid cloud cluster. The cluster protection ports must include all protocol ports that are used by the website services to be protected. When you add website services to the hybrid cloud cluster for protection, you can select only the protocol ports of the website services from the cluster protection ports.
The hybrid cloud cluster enables ports 80, 8080, 443, and 8443 by default. If you have no special requirements, you do not need to modify the settings.
To add other ports, you can manually enter them. Press the Enter key after you enter each port.
ImportantThe hybrid cloud cluster does not support ports 22, 53, 9100, 4431, 4646, 8301, 6060, 8600, 56688, 15001, 4985, 4986, or 4987. You can click View the range of ports that are not supported to view the unselectable port range of the hybrid cloud cluster.
We recommend that you add only necessary protection ports and do not add ports that are irrelevant to your services to avoid security risks.
Cluster Access Mode
Set the network connection mode for the hybrid cloud cluster. Valid values:
Internet: The hybrid cloud cluster connects to the On-cloud WAF console over the Internet.
Internal Network: The hybrid cloud cluster connects to the On-cloud WAF private console over an Express Connect circuit.
ImportantYou can use the Internal Network mode only after you set up an Express Connect circuit. For more information, see Express Connect.
Remarks
Add remarks for the hybrid cloud cluster.
In the Node Group Configuration step of the wizard, click Add Node Group to add node groups in the desired order, and then click Next.
NoteYou must first add multiple node groups to the hybrid cloud cluster and then add nodes to the node groups. Each node group requires a Server Load Balancer (SLB) server to ensure service load balancing and disaster recovery. If you do not have an SLB device, submit a ticket to contact a product technical expert.
Configuration item
Description
Node Group Name
Specify a name for the node group.
Server IP Address for Load Balancing
Set the public IP address of the SLB server that is bound to the node group.
Node Group Type
Select the type of the node group. Valid values:
Protection: corresponds to the protection component. You can add multiple protection components to a cluster for disaster recovery.
Management: corresponds to the management component. You can add multiple management components to a cluster for disaster recovery.
Storage: corresponds to the storage component. You can add only one storage component to a cluster.
Management And Storage: corresponds to the management and storage components. You can add only one management and storage component to a cluster.
You must add the corresponding node groups in the following order:
Method 1: Add at least three node groups
First, add one Storage node group. Then, add at least one Management node group. Finally, add at least one Protection node group.
Method 2: Add at least two node groups
First, add one Management And Storage node group. Then, add at least one Protection node group.
Region
If you set Node Group Type to Protection, you must select a Region for the node group. You do not need to set this parameter for other types of node groups.
Remarks
Add remarks for the node group.
On the Node Group Configuration page, click Add Node, configure the following parameters, and then click Save.
Configuration item
Description
Server IP Address
Set the public IP address of the local server.
Node Name
Specify a name for the node.
Region
Select the region where the node is located.
Server Configuration
The configuration information of the server is displayed by default.
Protection Node Group
Select the protection node group to which you want to add the node.
The number of nodes that you add to the current cluster cannot exceed the protection node specification of the cluster.
We recommend that you add at least two nodes to the Protection node group to ensure online active-active disaster recovery.
After the cluster is created, you can click Switch Cluster, select the cluster that you want to query, and then perform the following operations:
In the Basic Information section, you can view the basic information of the cluster. You can also click Edit to modify the cluster name, number of protection nodes, service ports, or remarks.
Click Node Group Configuration to add or modify a node group. For more information, see Step 6.
Click Add Node to add a node. For more information, see Step 7.
Check the running status of the node.
Node Status indicates whether the server is running as expected. Normal indicates that the server is running. Abnormal indicates that the server is shut down.
If the server is shut down, the node cannot provide WAF protection services. Check the cause of the server shutdown and fix the issue as soon as possible.
Application Status indicates whether the WAF client application, vagent, on the node is running as expected. Normal indicates that the application is running as expected. Abnormal indicates that vagent has stopped running.
If vagent stops running, the node may not be able to provide WAF protection services as expected. We recommend that you log on to the local server, check the installation and running status of vagent, and fix the issue as soon as possible. For more information, see Step 1: Install the WAF client.
ImportantTo prevent node health checks from failing, do not delete the RAM user or permissions that are used for deployment. If you accidentally delete the RAM user, submit a ticket to contact a product technical expert.
Prepare cluster resources
You can select a cluster deployment solution based on the protection scenario. Different solutions require different numbers of cluster resources.
Protection scenario | Deployment solution | Required resources | Deployment description |
Protection for online services that require high security and stability, and the pursuit of high stability for both services and protection capabilities. | Disaster recovery deployment for both protection and management capabilities. |
|
|
Protection for online services that require high stability, and the pursuit of high service stability. | Disaster recovery deployment for protection capabilities. |
|
|
PoC testing for basic protection capabilities. | Minimal cluster deployment. |
|
|
Step 3: Add services to WAF
The procedures for adding services to WAF vary based on the connection type. Select the procedure based on the Cluster Type that you selected when you deployed the hybrid cloud cluster.
Reverse proxy mode
Log on to the WAF 3.0 console. In the top navigation bar, select the resource group and region of the WAF instance. You can select Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, click Onboarding.
On the Hybrid Cloud tab, click Reverse Proxy, and then click Add.
In the Configure Listener step of the wizard, complete the following configurations and click Next.
Configuration item
Description
Domain Name/IP Address
Enter the domain name or IP address that you want to protect. Description:
You can enter an exact-match domain name (for example,
www.aliyundoc.com) or a wildcard domain name (for example,*.aliyundoc.com).NoteA wildcard domain name does not match the corresponding primary domain name. For example,
*.aliyundoc.comdoes not matchaliyundoc.com.A wildcard domain name does not match subdomains at different levels. For example,
*.aliyundoc.comdoes not matchwww.example.aliyundoc.com.A wildcard domain name matches all subdomains at the same level. For example,
*.aliyundoc.commatcheswww.aliyundoc.comandexample.aliyundoc.com.If the protected object includes both an exact-match domain name and a wildcard domain name that can match the exact-match domain name, the mitigation rules for the exact-match domain name take precedence.
You can enter an IP address, such as 192.168.XX.XX.
Protocol Type
The protocol type and port information used by the website.
Select HTTP or HTTPS and enter the corresponding port number. Press the Enter key after you enter each port.
NoteThe port you enter must be within the range of cluster listener ports configured for the hybrid cloud cluster. If the port that your domain name or IP address needs to listen on is not within this range, you must first add a new listener port to the hybrid cloud cluster. For more information, see Step 2: Deploy a hybrid cloud cluster.
If you select HTTP, you do not need to configure other information.
If you select HTTPS, you must upload the associated SSL certificate to WAF so that WAF can listen on and protect the HTTPS service traffic of the website.
Purchase Certificate
Click Apply to go to the SSL certificate application page and quickly apply for a certificate.
After you configure the certificate as prompted, the certificate is automatically uploaded to WAF.
NoteQuick application only supports applying for paid Domain Validation (DV) certificates. To apply for other types of certificates, purchase them through Certificate Service. For more information, see Purchase a commercial certificate.
After you select HTTPS and configure the certificate, you can also perform the following operations based on your business needs:
HTTP2
If your website supports the HTTP/2 protocol, you can select HTTP2 to enable HTTP/2 service protection.
NoteThe port for the HTTP/2 protocol is the same as the port for the HTTPS protocol.
Advanced Settings
Whether Layer 7 Proxy, Such as Anti-DDoS Proxy or Alibaba Cloud CDN, Is Deployed in Front of WAF
Resource Group
Select the resource group to which the domain name belongs from the resource group list. If you do not select a resource group, the domain name is added to the Default Resource Group.
NoteYou can use Resource Management to create resource groups and manage cloud resources by dimensions such as business department or project. For more information, see Create a resource group.
In the Configure Forwarding Rule step of the wizard, configure the following settings and click Submit.
Configuration item
Description
Node Settings
Select a Protection Node Group and add the Origin Server Address to be added to the protection node group. This address is the origin IP address of the website, which is used to receive normal service requests (origin fetch requests) forwarded by WAF. Multiple protection node groups provide disaster recovery for each other. That is, if the origin server corresponding to node group A is unreachable, traffic is automatically switched to the origin server of node group B. Valid values:
IP
You can enter multiple IP addresses. Press the Enter key after you enter each IP address. You can add up to 20 origin IP addresses.
NoteIf you set multiple origin IP addresses, WAF automatically performs load balancing among them.
You can configure both IPv4 and IPv6 addresses, only IPv4 addresses, or only IPv6 addresses.
If you configure both IPv4 and IPv6 addresses, requests from IPv6 clients are forwarded to the IPv6 origin server, and requests from IPv4 clients are forwarded to the IPv4 origin server.
If you configure only IPv4 addresses, both IPv4 and IPv6 requests are fetched from the origin server over IPv4. That is, WAF forwards requests to the IPv4 origin server address you set.
If you configure only IPv6 addresses, both IPv4 and IPv6 requests are fetched from the origin server over IPv6. That is, WAF forwards requests to the IPv6 origin server address you set.
Domain Name (Such as CNAME)
When you enter an origin URL, only origin fetch over IPv4 is supported (origin fetch over IPv6 is not supported). That is, WAF only forwards client requests to the IPv4 address resolved from the origin URL (WAF does not resolve the IPv6 address of the origin URL).
Standby Link Back-to-origin
After you enable backup link for origin fetch, if all origin URLs in the primary link are unreachable, the WAF cluster automatically forwards traffic to the backup link origin IP address to achieve high link availability. When the primary link origin IP address recovers, the WAF cluster automatically forwards traffic back to the primary link origin IP address.
You can configure a backup link for origin fetch only after you enable origin fetch retry.
If one of your websites is deployed on multiple protection nodes, you can click Add Protection Node to add multiple protection nodes to WAF at the same time.
Public Cloud Disaster Recovery
After you enable this feature, services can be switched to the public cloud link for disaster recovery. If the hybrid cloud link fails, you can point the DNS record corresponding to the domain name to the CNAME address assigned by the public cloud disaster recovery link. Traffic is protected by the public cloud cluster and then forwarded to the server address. You need to add the Origin Server Address for disaster recovery. The configuration requirements are the same as those for the Origin Server Address in Node Settings. For more information, see Server address configuration requirements.
Load Balancing Algorithm
If the origin server has multiple server addresses, you can select an algorithm for load balancing among the server addresses when WAF forwards origin fetch requests to the origin server. Valid values:
Round-robin: Forwards client requests sequentially to each server in the origin server address list. This is ideal for scenarios with multiple origin servers that require even load distribution.
IP hash: Forwards requests from the same client to the same origin server. This is suitable for scenarios that require session consistency, but may result in an unbalanced load.
Advanced HTTPS Settings
Enable HTTP Routing
The back-to-origin port is 80 by default. You can change this port as needed.
Origin SNI
You can then set a value for the Server Name Indication (SNI) extension field. Valid values:
Same as the actual request host
The origin SNI value is the same as the value of the Host field in the HTTP request header. For example, if the added domain name is
*.aliyundoc.comand the Host in the client request iswww.aliyundoc.com, the origin SNI iswww.aliyundoc.com.Custom
Specify a fixed SNI value, which can be different from the Host field. You can use this only when the origin server has special configuration requirements, such as needing to direct requests from multiple domain names to a specific backend service.
Other Advanced Settings
Change the DNS record of the domain name.
ImportantBefore you change the DNS record of the domain name, make sure that the forwarding configuration has taken effect by performing a local verification. If you change the domain name's DNS record before the website forwarding configuration in WAF takes effect, your services may be interrupted. For more information, see Local verification.
You need to change the DNS record only when you add a domain name. You can skip this step when you add an IP address.
Change the DNS A record of the domain name to resolve the domain name to the protection node group IP address.
If you enabled Public Cloud Disaster Recovery in Step 5, change the DNS CNAME record of the domain name and resolve the domain name to the public cloud CNAME before you switch to the disaster recovery link.
NoteIf you use Alibaba Cloud DNS, you can log on to the Alibaba Cloud DNS console to change the A record and CNAME record of the domain name. For more information, see Change DNS settings.
After the service is added, WAF automatically generates a protected object and enables the web core protection rules for it by default. You can go to the page to view the automatically added protected object and configure mitigation policies for it. For more information, see Overview of mitigation settings.
SDK integration mode
In SDK integration mode for hybrid clouds, you can deploy an SDK on your unified access gateway to copy service traffic from the gateway to a bypass WAF cluster for detection. This separates service forwarding from detection. To add services to WAF in SDK integration mode, submit a ticket to contact a product technical expert.
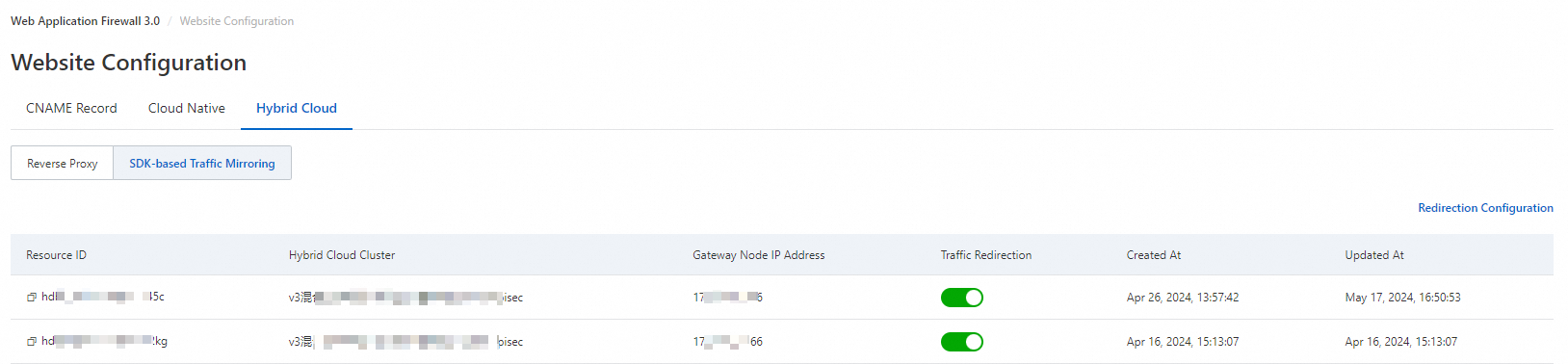
After the SDK and the Hybrid Cloud WAF cluster are deployed, you can perform the following operations:
View the mapping between the IP address of the forwarding node where the SDK is located and the hybrid cloud cluster and protection node group, and view the status of the forwarding node where the SDK is located
Log on to the Web Application Firewall 3.0 console
In the navigation pane on the left, click Onboarding.
On the Hybrid Cloud tab, click SDK Integration.
You can view the mapping relationship and status of the forwarding node IP address in the provisioning list.
Add a protected object
After the service is added, WAF does not automatically add the website domain name as a protected object. You must go to the Protected Objects page in the WAF console to add the domain name or URL that is added to WAF in SDK integration mode as a protected object. For more information, see Configure protected objects and protected object groups.
Configure mitigation policies for the protected object
After you add the protected object, you must configure mitigation policies for it. For more information, see Overview of mitigation settings.