After you add a website to Web Application Firewall (WAF), traffic that is destined for the website is redirected to WAF and then forwarded to the origin server. If the IP address of the origin server is exposed, attackers can bypass WAF and launch direct-to-origin attacks. You can configure access control policies for the origin server to allow inbound traffic only from the back-to-origin CIDR blocks of WAF. This topic describes how to configure access control policies for an origin server. In this topic, an Elastic Compute Service (ECS) instance that is added to a Server Load Balancer (SLB) instance is used as an example.
After you add your website to WAF, traffic is forwarded regardless of whether protection is configured for the origin server.
If you add the ECS instance and SLB instance to WAF in transparent proxy mode, all traffic on the traffic redirection ports is redirected to WAF. Attackers cannot bypass WAF to launch direct-to-origin attacks. In this case, you do not need to configure protection for the origin server.
Precautions
If you incorrectly configure access control policies for the origin server, security risks may arise. Before you configure protection for an origin server, take note of the following items:
Make sure that you add all domain names that are hosted on the ECS or SLB instance are added to WAF. If a domain name that is not added to WAF is used to attack the origin server, services of the other domain names that are hosted on the origin server are affected.
If the WAF cluster fails, traffic that is destined for your website is forwarded to the origin server to ensure service continuity. In this case, if you configured security group rules for the ECS instance or whitelists for the listeners of the SLB instance, the origin server cannot be accessed over the Internet.
If new back-to-origin CIDR blocks of WAF are added and you configured security group rules for the ECS instance or whitelists for the listeners of the SLB instance, HTTP 5XX status codes may be frequently returned. We recommend that you view the updates for the back-to-origin CIDR blocks of WAF in the WAF console on a regular basis and update relevant access control policies at the earliest opportunity.
If you no longer use WAF, you must delete the access control policies that you configured before you switch traffic back to the origin server. Otherwise, traffic cannot be sent to the origin server and service interruptions may occur.
Prerequisites
The origin server is an Alibaba Cloud ECS instance that is added to an SLB instance. For more information, see What is ECS and What is SLB?.
All domain names that are hosted on the ECS instance or SLB instance are added to WAF in CNAME record mode. For more information, see Add a domain name to WAF.
Step 1: Check whether the origin server has IP address exposure risks
Use Telnet to establish a connection from a host that is not deployed in Alibaba Cloud to your origin server by using the service port and the public IP address of your origin server.
If the connection is successful, the IP address of your origin server is exposed. In this case, attackers who obtain the public IP address can bypass WAF and launch direct-to-origin attacks.
If the connection fails, the IP address of your origin server is not exposed.
Example: Check whether you can connect to an origin server that is protected by WAF over ports 80 and 8080. If you can connect to the origin server over ports 80 and 8080, the IP address of the origin server is exposed.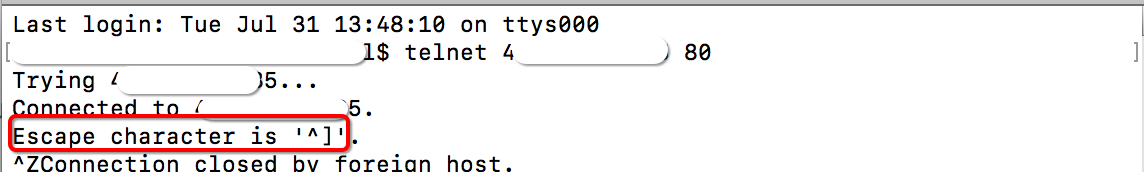
Step 2: Obtain the back-to-origin CIDR blocks of WAF
The back-to-origin CIDR blocks of WAF are updated on a regular basis. To avoid service interruptions, take note of update notifications and add the updated back-to-origin CIDR blocks to the security group rules and whitelists at the earliest opportunity.
Log on to the WAF console. In the top navigation bar, select the resource group and the region in which the WAF instance is deployed. The region can be Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, choose .
In the lower-right corner of the Service Information page, find the WAF IP Segments section and click Copy All IP Addresses.
The WAF IP Segments section displays the most recent back-to-origin CIDR blocks of WAF.
Step 3: Configure security group rules for the ECS instance
Obtain the back-to-origin CIDR blocks of WAF and configure security group rules for the ECS instance to allow inbound traffic only from the back-to-origin CIDR blocks of WAF.
Go to the security group list page.
Log on to the ECS console.
In the left-side navigation pane, choose .
In the upper-left corner of the top navigation bar, select a region.
Find the security group to which you want to add a rule and click Manage Rules in the Operation column.
Select a direction of security group rules.
If the security group resides in a virtual private cloud (VPC), click the Inbound or Outbound tab.
If the security group resides in the classic network, click the Inbound, Outbound, Internet Ingress, or Internet Egress tab.
Add a security group rule that has the highest priority to allow inbound traffic only from the back-to-origin CIDR blocks of WAF.
On the Inbound tab of the Access Rule section, click Add Rule.
Configure the parameters and click Save. The following table describes the parameters.
Parameter
Description
Action
Select Allow.
Priority
Enter 1, which specifies the highest priority.
Protocol Type
Select Custom TCP.
Port Range
Select HTTP (80) and HTTPS (443).
Authorization Object
Paste the back-to-origin CIDR blocks that you obtained to the Source field.
Description
Enter a description for the security group rule. Example: Allow inbound traffic from the WAF back-to-origin CIDR blocks.
ImportantIf your origin server uses IP addresses and ports other than the specified WAF back-to-origin CIDR blocks and HTTP or HTTPS ports to communicate with applications, you must add the IP addresses and ports to the security group rule.
After you add the security group rule, the rule receives the highest priority in the security group. This way, the ECS instance allows all inbound traffic from the WAF back-to-origin CIDR blocks.
WarningMake sure that you add all WAF back-to-origin CIDR blocks to the security group rule. Otherwise, access exceptions may occur.
Add a security group rule that has the lowest priority to deny inbound traffic from other CIDR blocks.
On the Inbound tab of the Access Rule section, click Add Rule.
Configure the parameters and click Save. The following table describes the parameters.
Parameter
Description
Action
Select Deny.
Priority
Enter 100, which specifies the lowest priority.
Protocol Type
Select Custom TCP.
Port Range
Select HTTP (80) and HTTPS (443).
Authorization Object
Enter 0.0.0.0/0 in the Source field. 0.0.0.0/0 specifies all CIDR blocks.
Description
Enter a description for the security group rule. Example: Block all inbound traffic.
After you add the security group rule, the ECS instance blocks inbound traffic from all CIDR blocks except the back-to-origin CIDR blocks of WAF. This way, all service traffic passes through WAF before the traffic reaches the ECS instance.
Step 4: Configure access control policies for the SLB instance
If you added your origin server to an SLB instance, you must configure an access control policy (whitelist) for the SLB instance to allow inbound traffic only from the back-to-origin CIDR blocks of WAF.
The following section describes how to configure an access control policy. In this example, a Classic Load Balancer (CLB) instance is used. If you use an Application Load Balancer (ALB) instance, configure an access control policy based on the following steps and the description in the Access control topic.
- Log on to the CLB console.
In the top navigation bar, select the region where the CLB instance is deployed.
In the left-side navigation pane, choose CLB > Access Control.
Create an access control list (ACL).
On the Access Control page, click Create ACL.
In the Create ACL panel, configure the parameters and click Create. The following table describes the parameters.
Parameter
Description
ACL Name
Enter a name for the ACL. Example: WAF back-to-origin CIDR blocks.
Add Multiple Addresses/CIDR Blocks and Descriptions
Copy and paste all WAF back-to-origin CIDR blocks.
Enter one CIDR block in each line. Press the Enter key to start a new line.
NoteAll WAF back-to-origin CIDR blocks that are copied are separated by commas (,). Before you paste the CIDR blocks, we recommend that you use a text editor that supports extension replacement to replace the commas (,) with line breaks (\n).
Configure whitelists for listeners.
In the left-side navigation pane, choose .
On the Instances page, find the instance that you want to manage and click the ID of the instance.
On the Listener tab, find the listener for which you want to configure a whitelist, click the
 icon in the Actions column, and then click Configure Access Control.
icon in the Actions column, and then click Configure Access Control. Select a listener based on the type of service that is protected by WAF:
If HTTP services are added to WAF, select an HTTP listener.
If HTTPS services are added to WAF, select an HTTPS listener.
If HTTP and HTTPS services are added to WAF, select an HTTP listener and an HTTPS listener.
In the Configure Access Control panel, turn on Enable Access Control and configure the parameters. The following table describes the parameters.
Parameter
Description
Access Control Method
Select Whitelist to allow specific IP addresses to access the CLB instance.
Access Control List
Select the ACL that you created for the WAF back-to-origin CIDR blocks.
After the preceding configurations are complete, the CLB instance allows inbound traffic from WAF back-to-origin CIDR blocks.
What to do next
After you configure security group rules for the ECS instance or whitelists for the listeners of the SLB instance, we recommend that you check whether you can connect to the origin server over ports 80 and 8080. This way, you can determine whether the configurations are in effect.
If you cannot connect to the origin server over port 80 or 8080 but the service runs as expected, the configurations are in effect.