After you purchase a Web Application Firewall (WAF) instance, Anti-DDoS Origin Basic can mitigate up to 5 Gbit/s of DDoS attacks for the WAF instance free of charge. Anti-DDoS Origin Basic scrubs traffic that is destined for the WAF instance to mitigate DDoS attacks and prevent blackhole filtering from being triggered due to traffic surges. This topic describes Anti-DDoS Origin Basic, how to prevent blackhole filtering, and how to deactivate blackhole filtering.
Anti-DDoS Origin Basic
Mitigation capabilities
Alibaba Cloud can mitigate up to 5 Gbit/s of DDoS attacks for a WAF instance free of charge. The thresholds that trigger blackhole filtering in Anti-DDoS Origin Basic vary based on the region. For more information, see View the thresholds that trigger blackhole filtering in Anti-DDoS Origin Basic.
How Anti-DDoS Origin Basic works
Anti-DDoS Origin Basic scrubs legitimate and malicious traffic that is destined for WAF and redirects suspicious DDoS attack traffic to a scrubbing device. The scrubbing device identifies and removes malicious traffic and redirects legitimate traffic to the original network. This way, legitimate traffic can be forwarded to WAF. This helps mitigate DDoS attacks.
Traffic scrubbing
If traffic to a WAF instance meets the trigger conditions for traffic scrubbing, Anti-DDoS Origin Basic scrubs the traffic. If traffic to your WAF instance is being scrubbed, a notification is sent to you. You can view the notification in the top banner section in the WAF 3.0 console.
Conditions
If the patterns of traffic to your WAF instance match the patterns of attack traffic and the traffic scrubbing threshold is reached, traffic scrubbing is triggered.
Patterns of attack traffic: Anti-DDoS Origin Basic uses the big data capabilities that are provided by Alibaba Cloud to learn the usual service traffic and uses algorithms to identify DDoS attacks.
Traffic scrubbing threshold: The threshold for traffic scrubbing varies based on the amount of traffic to your WAF instance. The public IP addresses that are protected by the same WAF instance have the same traffic scrubbing threshold, including public IP addresses protected by exclusive IP addresses and all protection nodes that are used for shared cluster-based intelligent load balancing.
NoteIf the amount of traffic to your WAF instance reaches the threshold, but the traffic is not identified as attack traffic, traffic scrubbing is not triggered.
Threshold
The methods that are used for traffic scrubbing include attack packet filtering, bandwidth throttling, and packet throttling. When you use Anti-DDoS Origin Basic, you must specify the following thresholds:
Scrubbing threshold based on bits per second (bps): When the amount of traffic to your WAF instance per second exceeds the threshold, traffic scrubbing is triggered.
Scrubbing threshold based on packets per second (pps). When the number of inbound packets per second exceeds the threshold, traffic scrubbing is triggered.
The traffic scrubbing threshold varies based on the actual amount of traffic to your WAF instance. The following table describes the threshold.
Type
Threshold
Maximum threshold based on bps (Unit: Mbit/s)
MAX (800, QPS × 4.5/150)
Maximum threshold based on pps (Unit: pps)
MAX (800000, QPS × 4.5)
To view the maximum traffic scrubbing threshold for your WAF instance, log on to the Traffic Security console.
View and specify the traffic scrubbing threshold
The system provides a default traffic scrubbing threshold. If the threshold is too high, traffic scrubbing is not triggered. You can specify a threshold based on your business requirements.
Log on to the Traffic Security console.
In the left-side navigation pane, click Assets.
In the top navigation bar, select the region in which your asset resides.
On the WAF tab, find the WAF instance for which you want to specify a traffic scrubbing threshold and view the default bps-based or pps-based threshold in the Traffic Scrubbing Threshold column.
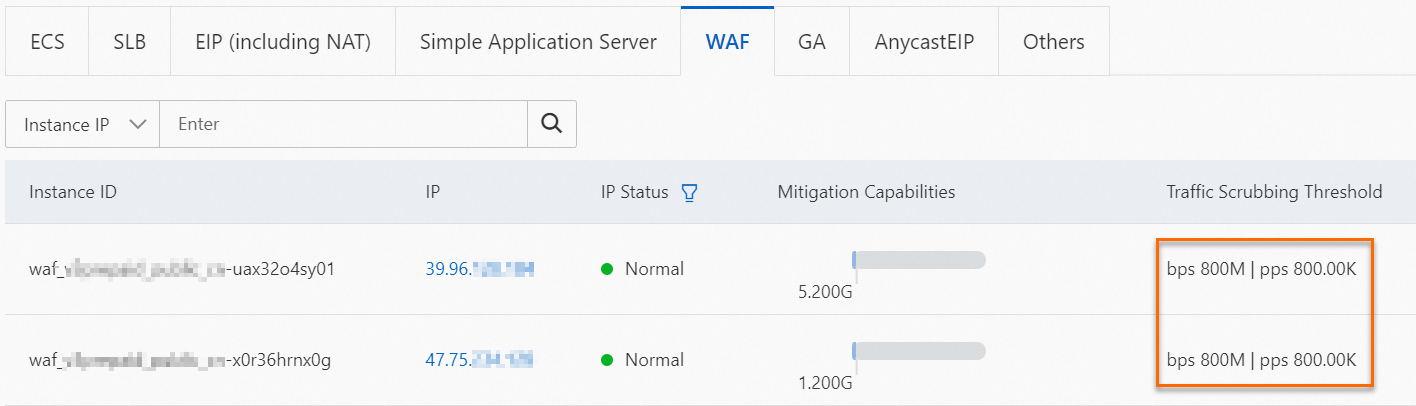
Optional. You can change the default bps-based or pps-based traffic scrubbing threshold based on your business requirements.
Find the WAF instance for which you want to change the traffic scrubbing threshold and click the IP address of the instance.
In the IP Address Details panel, click Traffic Mitigate Settings.
In the Traffic Mitigate Settings dialog box, configure the Scrubbing Threshold parameter and click OK.
Default: Anti-DDoS Origin Basic adjusts the traffic scrubbing threshold based on the amount of traffic to the WAF instance.
- Manual setting: You can select a specific threshold that includes Traffic and Packets per Second. Note If DDoS attacks are detected and the throughput or the packets per second (pps) reaches the selected value, traffic scrubbing is triggered.If you select Manual setting, take note of the following items:
- Configure a traffic scrubbing threshold that is slightly greater than the actual throughput and pps. If the threshold is significantly greater than the actual throughput or pps, the protection effect is compromised. If the threshold is significantly less than the actual throughput or pps, normal traffic may be scrubbed.
- If normal traffic is scrubbed, we recommend that you increase the traffic scrubbing threshold.
- During large promotions or activities for a website, we recommend that you increase the traffic scrubbing threshold.
Blackhole filtering
When the peak legitimate traffic to a WAF instance exceeds 5 Gbit/s, blackhole filtering is triggered. Legitimate traffic and malicious traffic to the WAF instance is routed to a black hole and dropped from the network.
The public IP addresses that are protected by the same WAF instance have the same traffic scrubbing threshold. The public IP addresses include public IP addresses protected by exclusive IP addresses and all protection nodes that are used for shared cluster-based intelligent load balancing.
In this case, a notification is displayed in the top banner section in the WAF 3.0.
To prevent your website from being inaccessible for a long period of time due to blackhole filtering, we recommend that you select Alert on DDoS blackhole and specify contacts to whom notifications are sent on the Voice Message Management page in Message Center. For more information, see Configure alert notifications in Message Center.
After you select Alert on DDoS blackhole on the Voice Message Management page, you can receive a voice message when blackhole filtering is triggered for your WAF instance. This way, you can handle the issue at the earliest opportunity.
How to prevent blackhole filtering
The stronger the mitigation capability of Anti-DDoS Origin Basic, the greater the threshold for blackhole filtering. If the mitigation capability of Anti-DDoS Origin Basic cannot meet your business requirements, you can purchase an Anti-DDoS instance of a paid edition, such as Anti-DDoS Origin and Anti-DDoS Proxy, to improve the DDoS mitigation capability and prevent blackhole filtering. For information about DDoS editions, see Scenario-specific anti-DDoS solutions.
How to deactivate blackhole filtering
Manual deactivation: If you want to immediately deactivate blackhole filtering, click Deactivate Blackhole Filtering in the top banner section in the WAF console. For more information, see Best practices for automatic deactivation of blackhole filtering.
Automatic deactivation: Wait for Anti-DDoS Origin Basic to automatically deactivate blackhole filtering.
To view the time when blackhole filtering is automatically deactivated, go to the Assets page in the Traffic Security console. The duration of blackhole filtering increases with the frequency of its activation for a user ID.
Exclusive IP addresses or shared cluster-based intelligent load balancing and blackhole filtering
Enabling exclusive IP addresses or shared cluster-based intelligent load balancing cannot prevent blackhole filtering, but can ensure that legitimate traffic is forwarded from WAF to the origin servers.
If traffic to a WAF instance is being scrubbed or the WAF instance is in the blackhole state, you cannot enable exclusive IP addresses or shared cluster-based intelligent load balancing.
Enable an exclusive IP address
By default, all domain names that are added to the same WAF instance share a WAF IP address that is used to listen to traffic to the domain names. An exclusive IP address is an IP address that is assigned to a specific domain name and is used to listen to traffic to the domain name. For more information, see Enable an exclusive IP address.
The blackhole status of an exclusive IP address is unrelated to that of a shared WAF IP address.
If you disable an exclusive IP address that is in the blackhole state, DDoS attacks against the exclusive IP address may be redirected to the shared WAF IP address.
Enable shared cluster-based intelligent load balancing
After you enable intelligent load balancing for a WAF instance, the instance is allocated at least three protection nodes in different regions to implement automatic disaster recovery across nodes and regions. WAF uses the intelligent DNS resolution feature and the least response time algorithm to shorten the path and minimize latency when requests are forwarded to the origin servers. For more information, see Intelligent load balancing.
After you enable shared cluster-based intelligent load balancing, WAF automatically uses another protection node to ensure that legitimate traffic is forwarded to the origin servers when blackhole filtering is triggered for a protection node in a region.
After you disable shared cluster-based intelligent balancing, traffic that is protected by the protection node cannot be forwarded to the origin servers when blackhole filtering is triggered for a protection node.
FAQ
Multiple domain names are added to my WAF instance. How do I check which domain name is under attack?
Attackers can resolve a domain name that is added to WAF to obtain the IP address of the WAF instance. Then, the attackers launch DDoS attacks on the IP address. DDoS attacks target the IP address of a WAF instance. You cannot determine which domain name is under attack based on attack traffic.
However, you can change the DNS records of domain names to determine the attacked domain name. For example, you can resolve specific domain names to WAF and the rest of the domain names to other services, such as Elastic Compute Service (ECS), Alibaba Cloud CDN, or Server Load Balancer (SLB). If blackhole filtering is no longer triggered after this operation, the attacked domain name is among the domain names that you resolved to the other services. However, this method is complicated and may cause specific assets to be exposed on the Internet, such as the IP address of the origin server. More serious security issues may arise. We recommend that you do not use this method to determine the attacked domain name.
Blackhole filtering is triggered for my WAF instance. Can I prevent this issue by changing the IP address of my WAF instance?
No, you cannot prevent blackhole filtering by changing the IP address of your WAF instance.
If you remove all domain names from your WAF instance and readd the domain names to your WAF instance or release your WAF instance and purchase a new WAF instance when traffic to the instance is being scrubbed or the instance is in the blackhole state, WAF assigns the IP address that was under DDoS attacks to your WAF instance or the new WAF instance.
NoteIf you want WAF to assign a new IP address to your WAF instance, perform the following operations:
Remove all domain names from your WAF instance and readd the domain names to your WAF instance.
Enable exclusive IP addresses and shared-cluster intelligent load balancing.
If attackers want to attack your domain name, the attackers can ping your domain name to obtain the IP address of your WAF instance regardless of whether you change the IP address.
What is the difference between DDoS attacks and HTTP flood attacks? Why is WAF unable to defend against DDoS attacks?
DDoS attacks are common at Layer 4, and HTTP flood attacks are common at Layer 7. HTTP flood attacks may use HTTP GET or POST requests. WAF can defend against HTTP flood attacks. However, to defend against DDoS attacks, WAF must be able to receive a huge volume of traffic before WAF can scrub the traffic. In this case, WAF cannot provide sufficient bandwidth. We recommend that you use Anti-DDoS to defend against DDoS attacks.
Which is the preferred method of protection against HTTP flood attacks, Anti-DDoS or WAF?
HTTP flood attacks are a type of DDoS attack. This type of attack exploits the normal behavior of the HTTP protocol by sending an excessive number of requests to a web server in a short period of time. This makes the web server unable to handle legitimate traffic.
To use WAF to defend against HTTP flood attacks, you can configure protection policies based on your business requirements. For example, to specify the protected paths and thresholds for triggering protection, you can configure custom rate limiting rules. To specify the actions that WAF performs on requests that meet specific conditions, you can configure custom access control rules. To block requests from specific regions, you can configure the region blacklist. For example, if your website targets users inside China, you can block requests from regions outside China to mitigate this type of attack. To defend against crawlers, you can enable the bot management module.
Anti-DDoS Proxy supports automatic protection against complex HTTP flood attacks and automatically adjusts protection policies based on actual scenarios. The intelligent protection automatically learns traffic patterns and uses algorithms to analyze attacks. Then, the feature applies accurate access control rules to adjust protection modes and detect and block attacks at the earliest opportunity.
Anti-DDoS Proxy provides stronger mitigation capabilities against DDoS attacks than WAF. WAF provides more fine-grained access control and rate limiting capabilities for applications than Anti-DDoS Proxy. If you want to defend against a high volume of DDoS attacks, we recommend that you use Anti-DDoS Proxy. If you want to defend against a low volume of DDoS attacks, configure fine-grained access control policies, and defend against crawlers, we recommend that you use WAF.