Network Load Balancer (NLB) supports large-scale SSL offloading. You can deploy an NLB instance as an ingress for traffic and configure an SSL certificate and a certificate authority (CA) certificate to enable mutual authentication, which requires both the client and the server to provide digital certificates to prove their identities. This improves the security of your workloads.
Background information
One-way authentication: The client must verify the identity of the server. The server does not need to verify the identity of the client. The client downloads a public key certificate from the server for authentication. A connection can be established only after the identity of the server is verified.
Mutual authentication: The client downloads a server certificate (public key certificate) from the server and uploads a client certificate (public key certificate) to the server for authentication. A connection can be established only after the identities of both the client and the server are verified. Mutual authentication provides higher security.
Prerequisites
An NLB instance is created. For more information, see Create and manage an NLB instance.
Three Elastic Compute Service (ECS) instances are created. For information about how to create an instance, see Create an instance by using the wizard.
ECS01 and ECS02 are added to the NLB instance as backend servers. Different NGINX applications are deployed on ECS01 and ECS02.
ECS03 is used to generate self-signed server certificates and client certificates. OpenSSL is downloaded from the OpenSSL site and installed on ECS03. The version of OpenSSL is 1.1.1 or later. If you use an existing Linux server to generate self-signed certificates, you do not need to create ECS03.
A server group is created for the NLB instance, and ECS01 and ECS02 are added to the server group. In this example, the backend ports of ECS01 and ECS02 are set to 80.
ImportantThe backend protocol of the server group must be TCP. Requests sent from NLB to the backend server are SSL-decrypted, and backend servers do not need to perform SSL decryption on received requests.
You cannot associate listeners that use SSL over TCP with server groups for which client IP preservation is enabled. Make sure that the feature is disabled for the server group.
Step 1: Prepare a CA certificate
Log on to the Certificate Management Service console
In the left-side navigation pane, choose PCA Certificate Management.
On the PCA Certificate Management page, on the Private CAs tab, find the root CA certificate.
Click the
 icon next to the root CA certificate, find the private intermediate CA that you want to manage, and then click Apply for Certificate in the Actions column.
icon next to the root CA certificate, find the private intermediate CA that you want to manage, and then click Apply for Certificate in the Actions column. In the Apply for Certificate panel, set the parameters and click Confirm.
The following section describes the parameters that are relevant to this topic. For more information, see Manage private certificates.
Parameter
Description
Certificate Type
Select the type of private certificate that you want to purchase. In this example, Client Certificate is selected.
Personal Name
The unique identifier for the client user. Only required for a client certificate.
In this example, enter the domain name of the NLB instance.
Validity Period
Specify a validity period for the private certificate. The validity period of the private certificate cannot exceed the subscription duration of the Private Certificate Authority (PCA) service that you purchase.
In this example, the default validity period is used, which is 30 days.
The private certificate is issued immediately after the request is submitted. To view the details about the private certificate, find the private CA, click Certificates in the Actions column, and then view the information on the Certificates page.
Step 2: Prepare a server certificate
A browser verifies the identity of a server by checking whether the certificate sent by the server is issued by a trusted CA. This topic describes two methods that you can use to obtain a server certificate. You can purchase a server certificate from Certificate Management Service, or upload a self-signed certificate to Certificate Management Service.
Method 1: Purchase a server certificate
You can purchase server certificates from Certificate Management Service or from other service providers. For more information, see Purchase an SSL certificate.
Method 2: Upload a self-signed server certificate
Remotely log on to ECS03 and run the following command to generate a self-signed server certificate. Make sure that the CA certificate is stored on ECS03. The CA certificate files used in this example are
root.crtandroot.key.Run the following command to generate a private key for the server certificate:
sudo openssl genrsa -out server.key 4096Run the following command to generate a certificate signing request (CSR):
sudo openssl req -new -out server.csr -key server.keyConfigure the other parameters. Examples:
Country Name (2 letter code) [XX]:cn State or Province Name (full name) []:bj Locality Name (eg, city) [Default City]:bj Organization Name (eg, company) [Default Company Ltd]:alibaba Organizational Unit Name (eg, section) []:test Common Name (eg, your name or your servers hostname) []:www.example.com Email Address []:a.alibaba.com A challenge password []: An optional company name []:ImportantSet Common Name to the domain name that is associated with the server certificate. Make sure that the domain name is valid. Keep the values of the other parameters the same as those of the root certificate and the client certificate.
In this example, the NLB instance uses the custom domain name
www.example.comto provide external services. Therefore, Common Name is set towww.example.com.Run the following command to generate a public key for the server certificate:
sudo openssl x509 -req -in server.csr -out server.crt -signkey server.key -CA root.crt -CAkey root.key -CAcreateserial -days 3650The following figure shows the result.
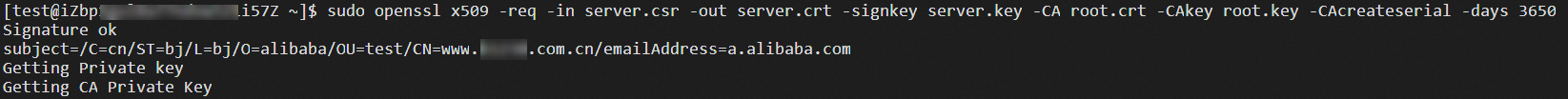
Run the following command to create a folder to store server certificate files:
sudo mkdir -p /root/sslRun the following command to copy the server certificate to the folder:
sudo cp server.crt /root/ssl sudo cp server.key /root/sslRun the following command to view the server certificate
server.crtand the private keyserver.keyof the server certificate:cd /root/ssl lsThe following figure shows the result.
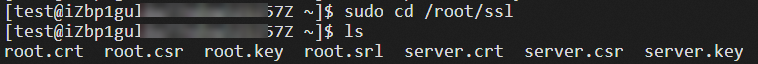
In this example, a Windows client is used. Open the command-line interface (CLI) on the Windows client and run the following commands to export the server certificate files generated in Step 1 to the local desktop:
scp root@IPaddress:/root/ssl/server.crt C:\Users\Public\Desktop #Replace 'IPaddress' with the IP address of the server that generates the server certificate scp root@IPaddress:/root/ssl/server.key C:\Users\Public\Desktop #Replace 'IPaddress' with the IP address of the server that generates the server certificateLog on to the Certificate Management Service console.
In the left navigation pane, choose .
Click the Manage Uploaded Certificates tab and click Upload Certificate.
In the Upload Certificate panel, set the following parameters and click OK.
For more information, see Upload an SSL certificate.
Parameter
Description
Certificate Algorithm
In this example, Internationally Accepted Algorithm is selected.
Certificate Name
Enter a name for the certificate that you want to upload.
Certificate File
Enter the content of the PEM-encoded CA certificate file.
You can use one of the following methods to enter the content. Method 1: Use a text editor to open the CA certificate file in the PEM or CRT format. Then, copy the content to the Certificate File field. Method 2: Click Upload and Parse File below the Certificate File field. Then, select the CA certificate file from your computer to upload the content of the file.
In this example, the server certificate file
server.crtis uploaded.Certificate Key
Enter the content of the PEM-encoded private key file.
You can use one of the following methods to enter the content. Method 1: Use a text editor to open the private key file in the KEY format. Then, copy the content to the Add Private Key field. Method 2: Click Upload and Parse File below the Add Private Key field. Then, select the private key file from your computer to upload the content of the file.
In this example, the private key file
server.keyis uploaded.Certificate Chain
Enter the content of the certificate chain file. This parameter is ignored in this example.
Step 3: Prepare a client certificate
You can use one of the following methods to prepare a client certificate based on your business requirements:
Log on to the Certificate Management Service console.
In the left-side navigation pane, choose PCA Certificate Management.
On the PCA Certificate Management page, on the Private CAs tab, find the root CA certificate.
For more information about how to purchase a root CA certificate, see Purchase and enable a private CA.
Find the root CA certificate and click the
 icon. Then, find the subordinate CA certificate and click Certificates in the Actions.
icon. Then, find the subordinate CA certificate and click Certificates in the Actions. On the Certificates page, find the private certificate that you want to download and click Download in the Actions column.
In the Download Certificate dialog box, select a certificate format and click Confirm and Download. In this example, the CRT format is selected, the client certificate is
client.crt, and the certificate private key isclient.key.Convert the client certificate to a browser-recognizable PKCS12 file.
Remotely log on to ECS03. For more information, see Guidelines on instance connection.
Run the following command to create a folder to store the client certificate:
sudo mkdir -p /root/ca/usersUpload the client certificate
client.crtand certificate private keyclient.keyto the users directory.Run the following command to convert the client certificate to a PKCS12 file:
sudo openssl pkcs12 -export -clcerts -in /root/ca/users/client.crt -inkey /root/ca/users/client.key -out /root/ca/users/client.p12Follow the instructions to set an encryption key for the certificate private key.
Enter the password that is used to export the client certificate. This password is used to encrypt the client certificate and is required for installing the client certificate.
The following figure shows the result.
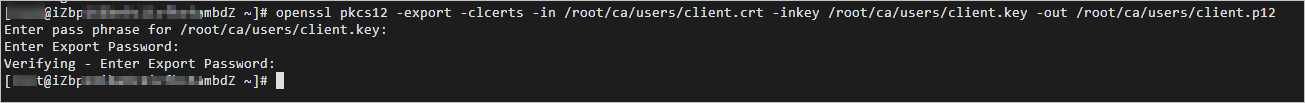
Run the following commands to view the generated client certificate:
cd /root/ca/users lsThe following figure shows the result.
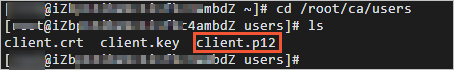
In this example, a Windows client is used. Open the CLI and run the following command to export the client certificate:
scp root@IPaddress:/root/ca/users/client.p12 C:\Users\Public\Desktop #Replace 'IPaddress' with the IP address of the server that generates the client certificate
Step 4: Install the client certificate
Install the client certificate on your client. In this example, a Windows client and a Linux client are used to show how to install the client certificate.
Windows client
Import the client certificate to Microsoft Edge.
Open Microsoft Edge and choose .
In the left-side navigation pane, click the Privacy, search, and services tab. Then, click Manage certificates in the Security section and import the PKCS12 file. In this step, you must enter the password that is used to export the client certificate in Step 3: Prepare a client certificate.
Linux client
If ECS03 is used to generate the client certificate, the client certificate is stored in the directory of ECS03. If another Linux client is used to generate the client certificate, perform the following steps to copy the certificates to the directory of the Linux client first:
Log on to the Linux client. Run the following commands to copy the client certificate, server certificate, and root certificate to a directory:
Run the following command to create a folder:
sudo mkdir /root/caRun the following command to modify the directory permissions:
sudo chmod 700 /root/caRun the following command to copy the certificates to the Linux client directory:
The following path is for reference only. Specify the actual path that you use.
sudo scp home@IPaddress:/root/ca/users/client.crt /root/ca //Replace 'IPaddress' with the IP address of the server that generates the client certificate sudo scp home@IPaddress:/root/ca/root.crt /root/ca //Replace 'IPaddress' with the IP address of the server that generates the root certificate sudo scp home@IPaddress:/root/ca/root.key /root/ca //Replace 'IPaddress' with the IP address of the server that generates the root certificate sudo scp home@IPaddress:/root/ssl/server.crt /root/ca //Replace 'IPaddress' with the IP address of the server that generates the server certificate sudo scp home@IPaddress:/root/SSL/server.key /root/ca //Replace 'IPaddress' with the IP address of the server that generates the server certificate
Step 5: Configure mutual authentication for a listener that uses SSL over TCP
Log on to the NLB console.
In the top navigation bar, select the region of the NLB instance.
On the Instances page, find the NLB instance, and click Actions in the Create Listener column.
In the Configure Listener step, set the following parameters and click Next.
The following table describes only some of the parameters. Keep the default values for other parameters. For more information, see Create a listener that uses SSL over TCP.
Parameter
Procedure
Listener Protocol
Select a listener protocol. In this example, TCPSSL is selected.
Listener Port
Specify a port on which the NLB instance listens. The NLB instance uses the port to receive requests and forward the requests to backend servers. Port 443 is used in this example.
In the Configure SSL Certificates step, select the server certificate specified in Step 2: Prepare a server certificate from the Server Certificate drop-down list.
Turn on Enable Mutual Authentication. Select the CA certificate purchased in Step 1 from the Default CA Certificate drop-down list.
Select a TLS Security Policy and click Next.
In the Select Server Group step, select the server group that you created and view the information about the backend servers ECS01 and ECS02. In this example, the ports of the backend servers are set to 80. Then, click Next.
In the Configuration Review step, confirm the configurations and click Submit.
Step 6: Verify mutual authentication
Windows client
Go to the NLB Instances page, click the ID of the NLB instance that you want to manage, and then click the Listener tab to view the health check status of the listeners that use SSL over TCP.
If the Health Check Status column displays Healthy, the backend servers can process requests forwarded by the NLB listener.
Enter
https://The domain name associated with the server certificatein the address bar of your browser, for example,https://www.example.com. In the dialog box that appears, select the certificate that is used to verify the identity of the client, and click OK.
To avoided issues caused by caching on the browser, we recommend that you access the domain name in private browsing mode when you test Layer 4 load balancing. The results show that the requests were distributed to ECS01 and ECS02.
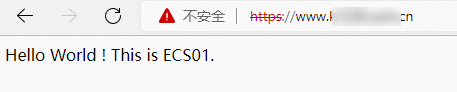
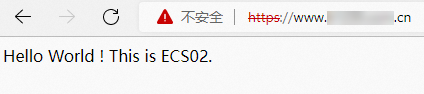
Linux client
Log on to the Linux client where the root certificate, server certificate, and client certificate are stored, and run the following commands to test mutual authentication:
sudo curl --cert /root/ca/client.crt --key /root/ca/client.key --cacert /root/ca/root.crt www.example.comwww.example.com is the domain name that is associated with the server certificate.
The following echo reply packet shows that both the client and the server passed mutual authentication, and requests are distributed to ECS01 and ECS02. 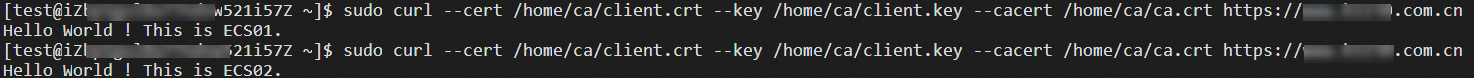
 > Settings
> Settings