You can onboard assets from third-party cloud service providers to Security Center for centralized protection and management. These providers include Tencent Cloud, Huawei Cloud, Amazon Web Services (AWS), and Microsoft Azure. This topic explains how to onboard a third-party asset to Security Center.
Onboarding methods
Security Center offers two methods for onboarding third-party assets, each collecting different data. Choose a method based on the data you want to collect.
Method | Description | Data to collect |
If you use this method to onboard a third-party asset, the External host tag is added to the asset, and Security Center cannot identify the service provider of the asset. | IP address, hostname, operating system type, and CPU core count | |
This method allows Security Center to identify the asset's service provider and display it on the Host page. Important To use Security Center's protection capabilities after onboarding a third-party asset with this method, you must install the Security Center agent on the asset. | IP address, hostname, operating system type, CPU core count, virtual private clouds (VPCs) of the third-party cloud, asset status, region, and service provider |
Use the AccessKey pair of a third-party account
Security Center uses the AccessKey pair of an account created for the third-party cloud service provider to obtain read permissions on third-party assets and synchronize their information. This enables centralized protection and management of your cloud assets through Security Center.
Onboard assets of Tencent Cloud, Huawei Cloud, and AWS to Security Center
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, select .
On the tab, click Grant Permission and select Tencent Cloud, Huawei Cloud, or AWS from the drop-down list.
In the Add Assets Outside Cloud panel, create a RAM account for the cloud service provider as prompted and onboard third-party cloud servers to Security Center.
Log on to the platform of the third-party cloud service provider and create an AccessKey pair for the RAM account.
You can select Manual Configuration or Quick Configuration.
(Recommended) Manual Configuration: Manually create a RAM account for the third-party cloud service provider and grant the AccessKey pair of the RAM account to Security Center.
Select the corresponding feature in Permission Description based on the protection capabilities of Security Center that you want to use:
Host: Grant read permission for Elastic Compute Service under the third-party account of Security Center. If you need Security Center to provide security capabilities such as risk assessment and threat defense for third-party cloud assets, please select this parameter.
CSPM: Grant read permission for all cloud assets under the third-party account of Security Center. If you need to use the cloud security posture management (CSPM) feature to scan third-party cloud assets, select this parameter.
Agentic SOC: Grant read permissions for all cloud assets and write permissions for some cloud assets under the third-party account of Security Center. If you need to use the Agentic SOC feature to centrally manage logs of third-party cloud assets and handle responses, select this parameter.
NoteThe types of assets you can onboard to Security Center vary based on the cloud service provider. The types displayed below shall prevail.
You must grant the RAM account the permissions required by Security Center. Otherwise, Security Center cannot protect your third-party assets. Follow the instructions on the console to configure the permissions for the RAM account.
Quick Configuration: After you authorize Security Center to use the AccessKey pair of a Alibaba Cloud account, Security Center automatically creates the AccessKey pair for the RAM account.
NoteThis configuration only supports the protection of host assets. It does not support the use of the CSPM and Agentic SOC features.
In the Submit AccessKey Pair step, enter the obtained AccessKey pair and account name, and click Next.
The account name is used to distinguish the assets of different accounts under the same cloud service provider. We recommend that you set a name with a clear meaning based on its purpose.
On the Log Audit Settings page, configure the log data of the third-party assets, and click Next. If you do not need to add audit logs, click Skip.
ImportantConfiguring log audit is essential for obtaining data on check items in Cloud Infrastructure Entitlement Management (CIEM) of CSPM. If you do not configure this, Security Center will not be able to detect CIEM-related check items for third-party assets.
This configuration item is supported only for Tencent Cloud and AWS assets. Huawei Cloud assets do not require this configuration.
Before configuring log audit for Tencent Cloud assets, you must create a log topic in the Tencent Cloud console and complete the custom permission configurations. For more information, see Add cloud services for check.
Before configuring log audit for AWS assets, you must create an SQS queue in the AWS console and complete the custom permission policy configurations. For more information, see Add cloud services for check.
When you add the sub-account of Tencent Cloud, enter the obtained Kafka topic name, Kafka public endpoint, and logset ID of the log topic in sequence.
When you add the sub-account of AWS, enter the obtained region ID and name of the SQS queue in sequence.
On the Policy Configuration page, configure the region where the third-party assets are deployed and the data synchronization frequency, and click OK.
Parameter
Description
Select region
Select the region where the assets that you want to add reside. Security Center adds the data of the assets within the third-party account to the corresponding management center (China or Outside China) based on the data management center that you select in the upper-left corner of the console.
Region Management
If you select this option, Security Center automatically synchronizes the data of the newly created assets in the specified region within the third-party account to the current data management center.
If you do not select this option, newly created regions are not automatically added to Security Center for protection.
Host Asset Synchronization Frequency
Select the interval at which Security Center automatically synchronizes the data of third-party cloud servers. If you select Disable, the data is not synchronized.
NoteIf you select Host in Permission Description, you must configure this parameter.
Cloud Service Synchronization Frequency
Select the interval at which Security Center automatically synchronizes the data of third-party cloud services. If you select Disable, the data is not synchronized.
NoteIf you select CSPM in Permission Description, you must configure this parameter.
AK Service Status Check
Select the interval at which Security Center automatically checks the validity of the AccessKey pair of the third-party account. If you select Disable, the validity is not checked.
Click Synchronize Assets to synchronize the assets within the third-party account to Security Center.
If you use the AccessKey pair of a Alibaba Cloud account, the data of the assets within all RAM accounts of the Alibaba Cloud account is automatically synchronized to Security Center.
If you use the AccessKey pair of a RAM account, the data of the assets within the RAM account is automatically synchronized to Security Center.
Onboard assets from Microsoft Azure
Log on to the Security Center console. In the upper-left corner of the console, select the region where the assets you want to protect are located: China or Outside China.
In the left-side navigation pane, select .
On the tab, click Grant Permission. In the drop-down list, select the multicloud service provider you want to onboard (Microsoft Azure).
In the Add Assets Outside Cloud panel, follow the instructions to create a RAM account for the corresponding cloud service provider and establish a connection between the third-party cloud server and Security Center.
Create a RAM account for the third-party cloud service provider.
Follow the instructions on the console. You must log on to the platform of the third-party cloud service provider, manually create a Microsoft Azure account for Security Center, and obtain the
appId,displayName,name,password, andtenantinformation from the execution result of the operation command.ImportantYou must grant the read-only permissions on Microsoft.Compute permissions resources to the RAM account that you created.
On the Submit AccessKey Pair wizard page, enter the Enter an AppID, Enter a password, tenant, and Domain that you obtained in the preceding step, select the asset type you want to onboard, and click Next.
The supported asset type for integration is Host Assets, which indicates granting read permission for Elastic Compute Service under a third-party cloud platform account in the Security Center.
On the Log Audit Settings page, configure the log data of the third-party assets, and click Next. If you do not need to add audit logs, click Skip.
ImportantConfiguring log audit is essential for obtaining data on check items in Cloud Infrastructure Entitlement Management (CIEM) of CSPM. If you do not configure this, Security Center will not be able to detect CIEM-related check items for third-party assets.
This configuration item is supported only for Tencent Cloud and AWS assets. Huawei Cloud assets do not require this configuration.
Before configuring log audit for Tencent Cloud assets, you must create a log topic in the Tencent Cloud console and complete the custom permission configurations. For more information, see Add cloud services for check.
Before configuring log audit for AWS assets, you must create an SQS queue in the AWS console and complete the custom permission policy configurations. For more information, see Add cloud services for check.
When you add the sub-account of Tencent Cloud, enter the obtained Kafka topic name, Kafka public endpoint, and logset ID of the log topic in sequence.
When you add the sub-account of AWS, enter the obtained region ID and name of the SQS queue in sequence.
On the Policy Configuration page, configure the region where the third-party assets are deployed and the data synchronization frequency, and click OK.
Parameter
Description
Select region
Select the region where the assets that you want to add reside. Security Center adds the data of the assets within the third-party account to the corresponding management center (China or Outside China) based on the data management center that you select in the upper-left corner of the console.
Region Management
If you select this option, Security Center automatically synchronizes the data of the newly created assets in the specified region within the third-party account to the current data management center.
If you do not select this option, newly created regions are not automatically added to Security Center for protection.
Host Asset Synchronization Frequency
Select the interval at which Security Center automatically synchronizes the data of third-party cloud servers. If you select Disable, the data is not synchronized.
NoteIf you select Host in Permission Description, you must configure this parameter.
Cloud Service Synchronization Frequency
Select the interval at which Security Center automatically synchronizes the data of third-party cloud services. If you select Disable, the data is not synchronized.
NoteIf you select CSPM in Permission Description, you must configure this parameter.
AK Service Status Check
Select the interval at which Security Center automatically checks the validity of the AccessKey pair of the third-party account. If you select Disable, the validity is not checked.
Verify results
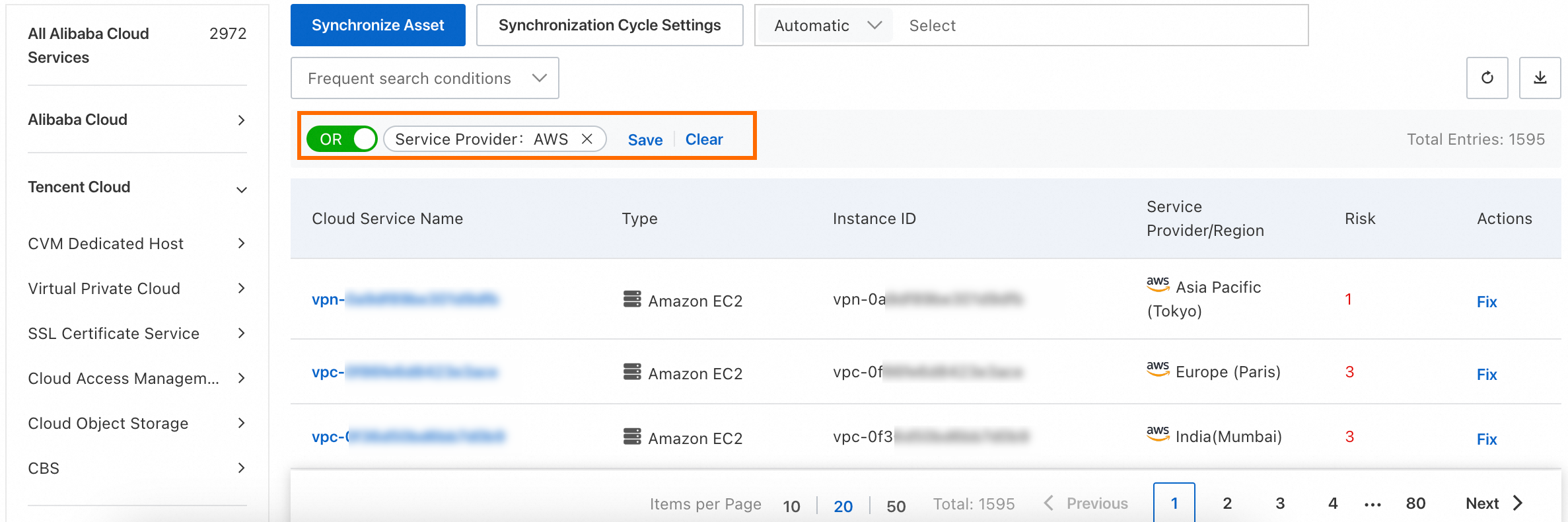
After you onboard third-party assets to Security Center, you can view the assets on the Assets page.
View assets that are onboarded based on the Host Assets type
You can go to the page to view the third-party cloud servers that are onboarded to Security Center. For more information, see Server assets.
View assets that are onboarded based on the Cloud product configuration check type
You can go to the page to view the third-party assets that are added to Security Center based on the Cloud product configuration check type.
You can find an asset and click View in the Actions column to view the basic information about the asset and the configuration check results of the asset. For more information, see View information about cloud services and CSPM Overview.
What to do next
If you use the AccessKey pair of the RAM account that is authorized to manage the assets to onboard third-party assets to Security Center, you must install the Security Center agent on the assets. This way, you can use the protection capabilities of Security Center.
More operations
You can view, modify, or delete the onboarding policies of third-party cloud assets on the page.
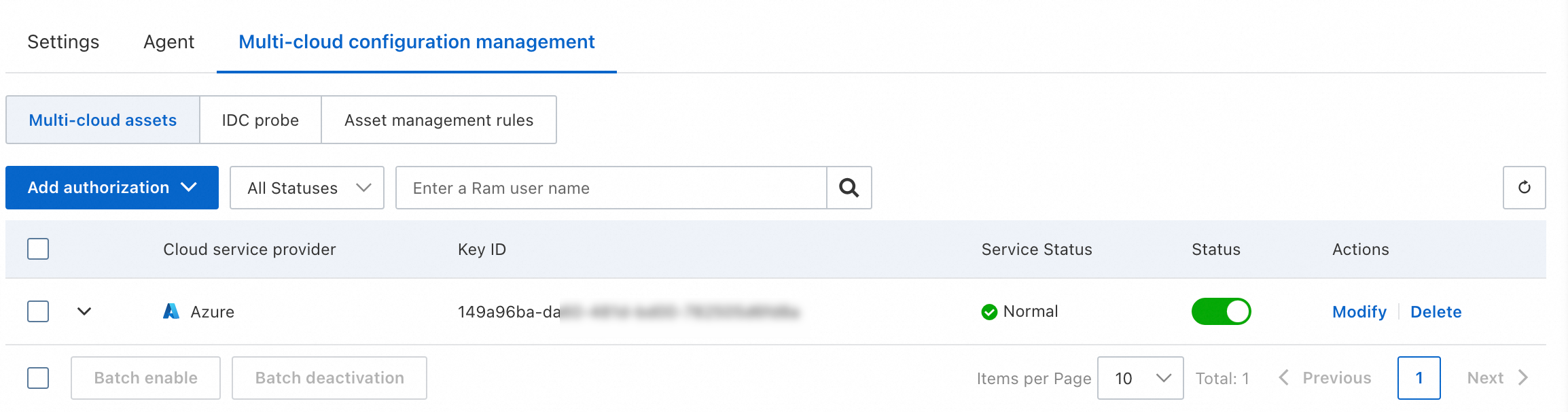
You can click the
 icon to the right of a policy to view the permission information and service status of the policy.
icon to the right of a policy to view the permission information and service status of the policy. The Service Status parameter of a policy is displayed as Normal only when the value of the Service Status parameter is Normal for all permissions specified in the policy. If the service status of a permission is abnormal, move the pointer over the
 icon in the Service Status column to view the cause.
icon in the Service Status column to view the cause. You can click Modify in the Actions column of a policy or a permission to modify the information about the policy, such as the AccessKey secret, asset type, and region.
You can enable, disable, or delete policies or permissions based on your business requirements.
After you disable or delete policies or permissions, Security Center no longer synchronizes assets of the cloud service provider based on the policy or permission.