After you install the Security Center agent, the agent starts processes such as AliYunDun and AliYunDunMonitor on your server. These processes enable features such as information collection and threat detection. You can check the process status to determine if the protection features are active.
Agent architecture
The Security Center agent uses a modular architecture. It is composed of core processes and functional processes. This architecture ensures the stable operation of basic features and the efficient scheduling of advanced features.
Core processes: Processes such as
AliYunDun,AliYunDunMonitor, andAliYunDunUpdateare core processes. They are responsible for maintaining a heartbeat connection with Security Center, reporting basic security data, and performing self-updates. These processes ensure reliable runtime operation of the agent.Functional processes: Processes such as
AliHipsandAliNetare functional processes. They are downloaded and started on demand after you enable the corresponding advanced protection features, such as Malicious Host Behavior Prevention or Web Tamper Proofing, in the console.
Process details
To prevent issues with agent features, do not manually terminate or delete the related processes and files.
To delete agent-related files, turn off the agent self-protection based on the agent capability configuration.
Core processes
Core processes are fundamental to ensuring communication between the agent and the cloud and the reliable operation of basic monitoring features. They start automatically after the agent is installed.
Starting from version aegis_12_3x, the AliSecureCheckAdvanced and AliDetect processes are merged into AliSecCheck. Earlier versions are not affected.
Process name | Folder of the process file | Feature description |
|
| Communicates with Security Center. It is responsible for reporting heartbeats, receiving instructions, reporting data, and performing agent self-protection. |
|
| Responsible for host security monitoring. This includes collecting and detecting information about assets, processes, ports, and accounts. |
|
| Responsible for automatic updates of the agent version and rule library. |
|
| Responsible for running security scan and detection tasks. This includes vulnerability scans, compliance baseline checks, and runtime detection of malicious programs such as mining programs and trojans. |
Functional processes
Functional processes are associated with specific paid features. They start only after the corresponding features are enabled.
Process name | Folder of the process file | Feature description | Start condition |
|
| Provides network-layer protection. It blocks network behaviors such as malicious IP access and outbound attacks. | Enable Malicious Network Behavior Prevention. |
|
| Provides host intrusion prevention. It blocks malicious host behaviors, provides anti-ransomware capabilities, and prevents web shell connections. | Enable one of the following features: Malicious Host Behavior Prevention, Anti-ransomware (Bait Capture), or Webshell Prevention. |
|
| Performs web tamper proofing and core file monitoring. | Enable Web Tamper Proofing or Core File Monitoring. |
|
| Performs tasks such as generating security reports, anomaly detection, and real-time monitoring. | Enable Anti-ransomware for Servers. |
|
| Performs tasks such as data backup, data restoration, fault monitoring, and task scheduling. | |
|
| The database backup proxy process. It performs tasks such as initial database backups, incremental backups, database backup restoration, scheduling and management, and logging and monitoring. | Enable Anti-ransomware for Databases. |
Relationship between processes and features
Feature name | Related process | Edition and protection level | Documentation |
Agent Protection |
| Not Required | |
Malicious Network Behavior Prevention |
|
| |
Malicious Host Behavior Prevention |
|
| |
Anti-ransomware (Bait Capture) |
|
| |
Webshell Prevention |
|
| |
Web Tamper Proofing |
| Not Required Important This feature is a value-added service that you must purchase separately. | |
Core File Monitoring |
|
| |
Anti-ransomware for Servers |
| Not Required Important This feature is a value-added service (Managed Anti-ransomware) that you must purchase separately. | |
Anti-ransomware for Databases |
| Not Required Important This feature is a value-added service (Managed Anti-ransomware) that you must purchase separately. |
Relationship between processes and agent status
Security Center evaluates the online status of the agent by monitoring the communication between the AliYunDun process and the cloud. The agent status changes from "Online" to "Offline" in either of the following situations:
You can view the agent status of your server on the Host page: Offline (![]() ) or Online (
) or Online (![]() ).
).
Security Center detects that the communication with the agent is interrupted. For example, a network exception occurs, the
AliYunDunprocess is terminated, or the agent is uninstalled.Security Center does not receive any information, such as heartbeats or security data, from the agent within 10 hours.
Running permissions and file locations
Process running permissions
To provide comprehensive security monitoring and protection, the agent processes must run with high privileges in the operating system. High privileges are required to perform underlying operations such as kernel-level monitoring, file system protection, network behavior analysis, and process self-protection.
On Linux systems, the processes run as the
rootaccount.On Windows systems, the processes run as the
SYSTEMaccount.
Default process file paths
Windows systems
32-bit: C:\Program Files\Alibaba\aegis.
64-bit: C:\Program Files (x86)\Alibaba\aegis.
Linux systems: /usr/local/aegis.
Methods to check process status
You can use the following commands to quickly check if the agent processes and services are running properly. The following examples use core processes.
Linux
Command to view processes:
# Check the core processes. AliYunDun, AliYunDunMonitor, and AliYunDunUpdate must all exist.
ps -ef | grep -E 'AliYunDun|YunDunMonitor|YunDunUpdate'
# Check the service status. The status should be active (running).
systemctl status aegis
Example of normal status output:
root 5472 1 0 Sep10 ? 00:00:18 /usr/local/aegis/aegis_update/AliYunDunUpdate
root 5524 1 0 Sep10 ? 00:01:34 /usr/local/aegis/aegis_client/aegis_12_61/AliYunDun
root 5546 1 0 Sep10 ? 00:03:13 /usr/local/aegis/aegis_client/aegis_12_61/AliYunDunMonitor
● aegis.service - LSB: Aegis service
Loaded: loaded (/etc/rc.d/init.d/aegis; generated)
Active: active (running) since Mon 2023-10-30 10:00:00 CST; 1 day 2h ago
Windows
Method 1: View the processes in Task Manager
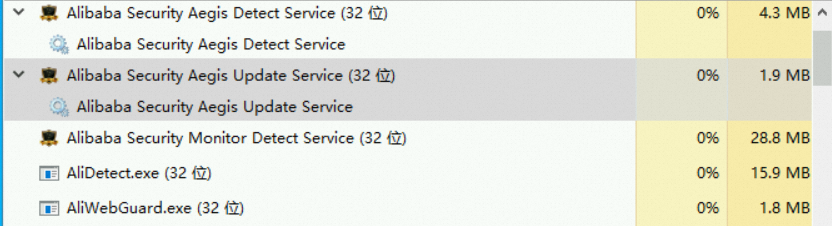
Method 2: Run commands in PowerShell
Command to view processes:
# Check the core processes. Get-Process | Where-Object {$_.Name -match '^(AliYunDun|AliYunDunMonitor|AliYunDunUpdate)$'} # Check the service status. The status should be Running. Get-Service | Where-Object {$_.Name -match 'Aegis|AliYunDun'}Example of normal status output:
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName ------- ------ ----- ----- ------ -- -- ----------- 380 26 15948 19656 615.75 6072 0 AliYunDun 599 31 47576 37356 968.73 2488 0 AliYunDunMonitor 257 14 8072 11336 232.03 2904 0 AliYunDunUpdate Status Name DisplayName ------ ---- ----------- Running Alibaba Securit... Alibaba Security Aegis Detect Service Running Alibaba Securit... Alibaba Security Aegis Update Service