Security Center provides various features, such as Malicious Host Behavior Prevention, anti-ransomware, and webshell prevention. You can enable the features to protect your server. This topic describes the features that you can enable on the Host Protection Settings tab, and how to enable the features.
Proactive Defense
Overview
Proactive defense automatically intercepts common viruses, malicious network connections, and webshell connections. Proactive defense also allows you to use bait to capture ransomware. The following table describes the features of proactive defense.
Feature | Supported edition | Description |
Malicious Host Behavior Prevention | Anti-virus, Advanced, Enterprise, and Ultimate | The Malicious Host Behavior Prevention feature can help you automatically detect and remove common network viruses, such as ransomware, DDoS trojans, mining programs, trojans, malicious programs, webshells, and computer worms. After you purchase Security Center Anti-virus or higher, Security Center automatically enables the Malicious Host Behavior Prevention feature for all your servers. Note A computer virus is a type of malicious program. The virus can write malicious code to normal program files for execution. This causes a large number of normal programs to be infected and detected as virus hosts. Computer viruses jeopardize system processes. If system processes are unexpectedly terminated, system stability risks arise. Security Center does not automatically quarantine computer viruses. You must manually handle the viruses. |
Anti-ransomware (Bait Capture) | Anti-virus, Advanced, Enterprise, and Ultimate | This feature uses bait to capture new types of ransomware and analyzes the patterns of the new types of ransomware to protect your servers. The bait files that are configured on your servers by Security Center are used only to capture new types of ransomware. The files do not interrupt your services. You can go to page, click CWPP tab, and set Alert Type to Precision defense to view the removed ransomware. |
Webshell Prevention | Enterprise and Ultimate | After you enable this feature, Security Center automatically intercepts suspicious connections that are initiated by known webshells and quarantines related files. You can go to page, click CWPP tab, and view the related alerts and quarantined files. For more information, see Evaluate and handle security alerts and Evaluate and handle security alerts. Note After you purchase Security Center Enterprise or Ultimate, Security Center automatically enables the webshell prevention feature for all your servers. |
Malicious Network Behavior Prevention | Advanced, Enterprise, and Ultimate | After you enable this feature, Security Center intercepts the abnormal network behavior between your servers and disclosed malicious access sources. This reinforces the security of your servers. |
User Experience Optimization in Proactive Defense | Enterprise and Ultimate | After you enable this feature, Security Center collects the kdump data of your servers for protection analysis when the servers unexpectedly shut down or the defense capability is unavailable. This continuously enhances the protection capability of Security Center. |
If all features in the Proactive Defense section are disabled, Security Center sends alerts only when viruses are detected. You must log on to the Security Center console and manually handle the alerts. We recommend that you enable all features in the Proactive Defense section to reinforce the security of servers. For more information, see Evaluate and handle security alerts.
Enable the features of proactive defense
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the tab, turn on Malicious Host Behavior Prevention, Anti-ransomware (Bait Capture), Webshell Prevention, and Malicious Network Behavior Prevention in the Proactive Defense section.
After you turn on all switches in the Proactive Defense section, Security Center enables the following features for your servers: malicious host behavior prevention, anti-ransomware, webshell prevention, and defense against access to malicious sources.
Click Manage to the right of each feature to configure the detection scope. In the panel that appears, select the servers for which you want to enable a feature and click OK.
After you turn on Malicious Host Behavior Prevention, Anti-ransomware (Bait Capture), Webshell Prevention, and Malicious Network Behavior Prevention in the Proactive Defense section, Security Center automatically blocks the programs and processes that are related to the detected viruses and intercepts suspicious connections.
Optional. Select User Experience Optimization in Proactive Defense.
After you select User Experience Optimization in Proactive Defense, Security Center collects server data that reflects the security of the servers in the case of exceptions. We recommend that you select User Experience Optimization in Proactive Defense to reinforce the security of your servers.
What to do next
You can go to page, click CWPP tab, and view the viruses that are quarantined by proactive defense in the list of precision defense. To view the viruses, select Handled from the status drop-down list and click Precision defense below Alert Type.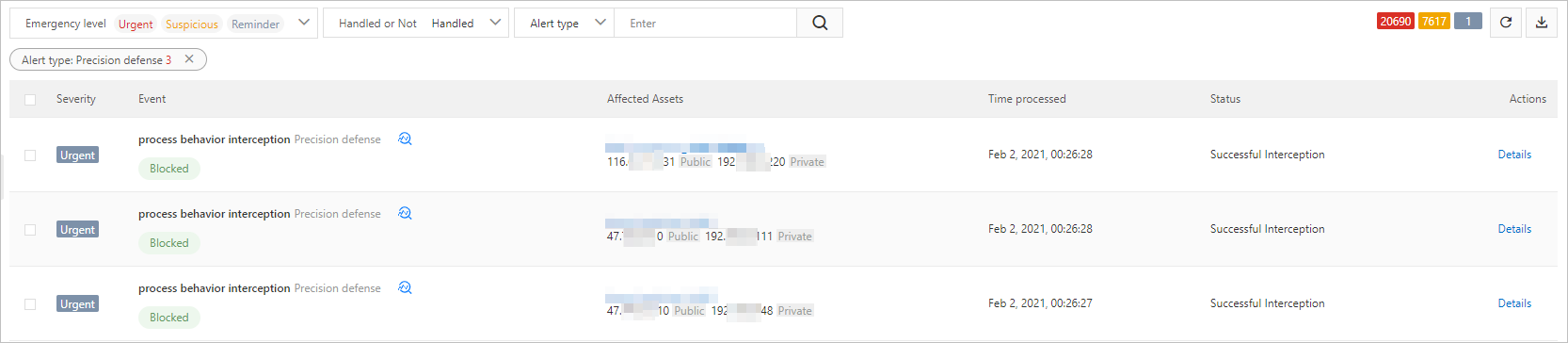
False positives or quarantine failures may occur after you turn on Malicious Host Behavior Prevention, Anti-ransomware (Bait Capture), and Webshell Prevention.
If some files are quarantined due to false positives, you can restore the quarantined files in the Quarantined Files panel. For more information, see Evaluate and handle security alerts.
You can go to page, click CWPP tab, and manually quarantine files that Security Center fails to quarantine. For more information, see Evaluate and handle security alerts.
Webshell Detection and Removal
The feature of webshell detection and removal uses engines developed by Alibaba Cloud to scan for common webshell files, supports scheduled scan tasks, provides real-time protection, and allows you to quarantine webshell files with one click. The feature scans servers and web directories for webshells and trojans at regular intervals. Security Center runs webshell detection tasks on your servers and generates alerts only after you enable webshell detection and removal for your servers. The following list explains how the webshells are detected and removed:
Performs static detection by scanning the entire web directory every day at midnight. Dynamic detection is triggered when changes occur in web directory files.
Supports configuration of the asset scope for web shell detection.
Supports isolation, recovery, and ignoring of detected webshell files.
Security Center Basic detects only some types of webshells. If you want to detect all types of webshells, we recommend that you upgrade Security Center Basic to the Anti-virus, Advanced, Enterprise, or Ultimate edition. For more information, see Upgrades and downgrades.
Enable webshell detection and removal for servers
Security Center enables webshell detection and removal feature by default for servers on which the Security Center agent is installed. We recommend you enable webshell detection and removal feature for servers that provide public web services. If your server is completely isolated from the internet, you can follow the steps below to disable webshell detection and removal feature for your server.
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the tab, click Manage in the Webshell Detection and Removal section.
In the Configure Servers for Webshell Detection and Removal panel, clear the servers for which you want to disable webshell detection and removal and click OK.
Handle webshell alerts
After you enable webshell detection and removal for your servers, you can view the alerts whose type is Webshell on the CWPP tab of page when Security Center detects security threats such as webshell files on your servers. If you do not handle the alerts, the alerts may pose threats to your servers. We recommend that you handle the alerts at the earliest opportunity.
The one-click webshell alert handling feature is not available in the Basic edition of Security Center. Users of the Anti-virus edition or higher can isolate the detected webshell files with one click in the console. For more information, see Evaluate and handle security alerts.
Dynamic adaptive threat detection capability
By default, the adaptive threat detection feature is disabled. You must manually enable the feature. If Security Center detects a high-risk intrusion on your server after the adaptive threat detection feature is enabled, Security Center automatically enables the strict alert mode for your server for seven days. In this mode, all protection rules and security engines are enabled to detect intrusions in a more comprehensive manner.
If you manually configure a protection mode for your server during the seven-day period, the server runs in the configured protection mode. After the seven-day period elapses, the strict alert mode is not automatically disabled, and the server continues to run in the protection mode that you configured.
Limits
Version limitations
Required subscription: Enterprise or Ultimate. If you are using a different edition, you must upgrade.
NoteThe protection edition for the server must be set to the edition that you purchased. For more information, see Attach a protection edition to a server.
Pay-as-you-go: This billing method is required for Host and Container Security. To enable it, see Purchase.
NoteThe server protection level must be set to Host Protection or Host and Container Protection. For more information, see Attach a protection level to a server.
Enable adaptive threat detection
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the tab, turn on Dynamic Adaptive Threat Detection in the Adaptive Threat Detection Capability section.
NoteIf you have not authorized Security Center to access your cloud resources, you must complete the authorization by following the on-screen instructions. This way, Security Center is authorized to access your cloud resources. After the authorization is successful, Resource Access Management (RAM) automatically creates a service-linked role named AliyunServiceRoleForSas. Security Center can assume this role to access your cloud resources and protect the resources. For more information, see Service-linked roles for Security Center.
Alert Settings
Security Center supports different alert modes for servers to meet your security requirements in different scenarios. By default, Security Center enables Balanced Mode for all servers that are added to Security Center. In this mode, Security Center attempts to detect as many risks as possible while minimizing the false positive rate. This mode has been tested by Alibaba Cloud experts.
Change the alert mode
If you want to detect risks on servers in a stricter manner, you can change the alert mode to Strict Mode for the servers.
After Strict Mode is enabled, Alibaba Cloud detects more suspicious behavior and generates alerts. However, the false positive rate is higher in this mode. We recommend that you enable this mode during major events.
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the tab, click Manage to the right of Protected Assets for Strict Mode in the Alert Settings section.
Select the servers for which you want to enable Strict Mode and click OK.
References
If you need to make different host-specific malicious behavior defense rules for different servers, you can enable the malicious behavior defense feature of Security Center.