Security Center checks the AccessKey pairs of Alibaba Cloud accounts and Resource Access Management (RAM) users in source code that is stored on GitHub in real time. If Security Center detects AccessKey pair leaks, Security Center generates alerts. We recommend that you view and handle AccessKey pair leak events at the earliest opportunity. This topic describes the principles for the detection of AccessKey pair leaks and how to handle AccessKey pair leak events.
Principles
The AccessKey pair leak detection feature allows you to detect AccessKey pair information in public source code deployed on GitHub in real time. In most cases, source code is uploaded and disclosed by enterprise employees. If the source code contains AccessKey pairs, Security Center sends notifications to help you identify data leaks at the earliest opportunity.
Security Center detects AccessKey pair leaks only on GitHub source code platform.
If an employee of an enterprise uploads confidential source code to platforms such as GitHub, the AccessKey pairs of the Alibaba Cloud accounts that are owned by the enterprise may be leaked on the Internet. If the AccessKey pair of an Alibaba Cloud account is leaked, you may lose control of the resources within the account.
An AccessKey pair can be used by third parties only if both the AccessKey ID and AccessKey secret of the AccessKey pair are leaked. When Security Center detects an AccessKey pair leak of an Alibaba Cloud account or a RAM user, Security Center notifies the Alibaba Cloud account or the Alibaba Cloud account to which the RAM user belongs by using different methods based on whether the AccessKey secret is valid. The following methods are supported:
Alerts on the AccessKey pair leak detection page: Security Center generates an alert if an AccessKey pair leak is detected, regardless of whether the AccessKey secret is valid.
Prompts in the console: A prompt is displayed in the Security Center console or most Alibaba Cloud service consoles if an AccessKey pair leak is detected and the AccessKey secret is valid.
Notifications: Security Center sends notifications based on the notification settings if an AccessKey pair leak is detected and the AccessKey secret is valid. The notifications can be sent by internal message and email.

Configure alert notifications for AccessKey pair leaks
If an alert is generated for AccessKey pair leaks, Security Center notifies you by email or internal message.
By default, Security Center sends notifications when an alert is generated. You can also perform the following operations to specify a notification method: Choose Notification Settings in the left-side navigation pane of the Security Center console. On the Email/Internal Message tab, configure Notification Method for AccessKey Pair Leak Information. You can receive notifications only through the selected method. For more information, see Notification settings.
AccessKey pair leak events can cause serious risks. We recommend that you select all notification methods to receive notifications at the earliest opportunity.
By default, only account contacts receive notifications. If you want others to receive notifications, you can perform the following operations to add contacts:
On the Common Settings page, choose in the Notification Type column, and then click Modify in the corresponding Contact column to modify the message recipients.
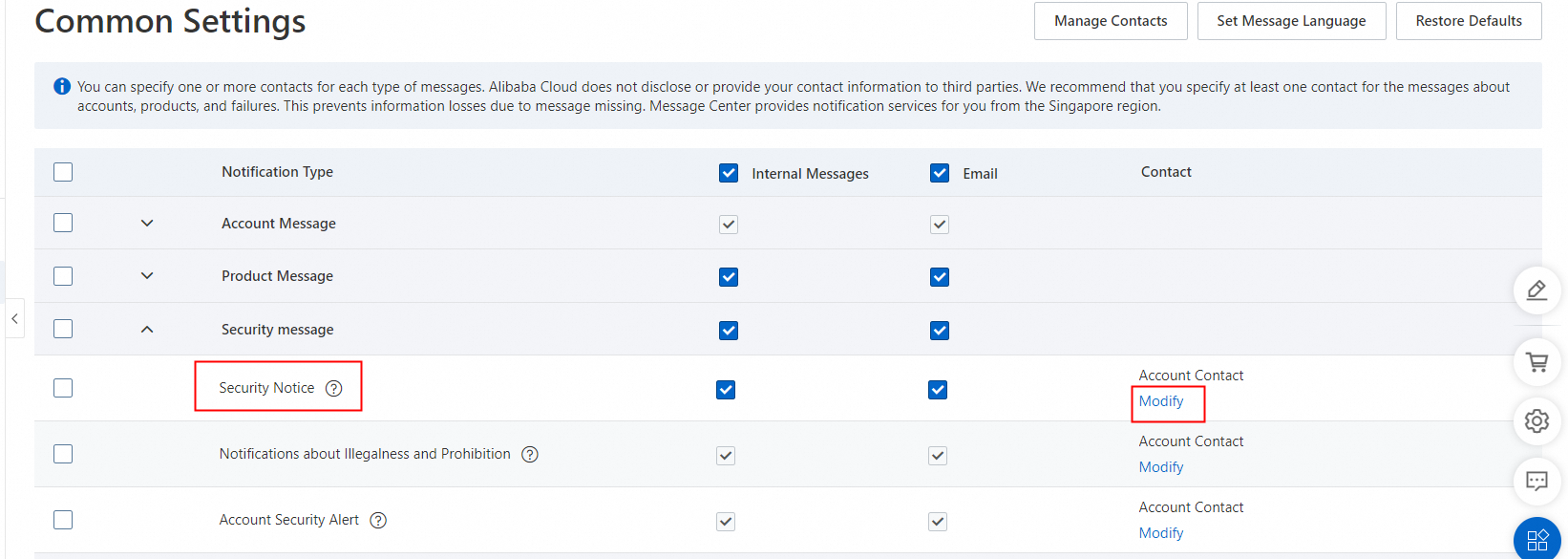
The modified notification recipients are also applied to other notifications sent by Security Center and to notifications sent by services such as Anti-DDoS and Web Application Firewall (WAF).
Handle AccessKey pair leak events
If you receive a notification for an AccessKey pair leak, the AccessKey pair of your Alibaba Cloud account or a RAM user is leaked. We recommend that you handle the leaked AccessKey pair at the earliest opportunity. After you handle the AccessKey pair leak event, handle the alert for the AccessKey pair leak in the Security Center console. To handle an AccessKey pair leak event, perform the following operations:
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
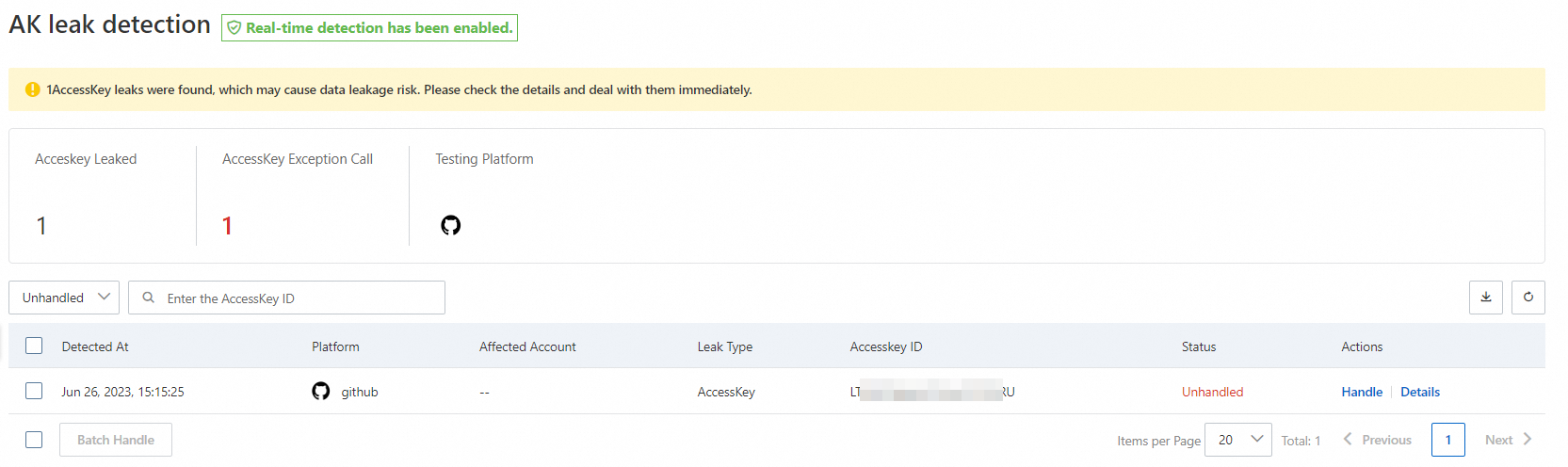
On the AccessKey Leak Detection page, view and handle AccessKey pair leak events.
View the details of an AccessKey pair leak event
To view the details of an AccessKey pair leak event, find the leak event and click Details in the Actions column. You can click the value of Username, File Name, or Repository Name in the File Details section to go to GitHub and view the source of the AccessKey pair leak.
Handle an AccessKey pair leak event
Security Center cannot automatically handle a leaked AccessKey pair or enable you to perform quick handling on a leaked AccessKey pair. You must manually handle the AccessKey pair in the RAM console and then log on to the Security Center console to handle the AccessKey pair leak event. You can manually handle a leaked AccessKey pair by using the following methods:
Contact relevant personnel to delete or hide related content on GitHub.
If you no longer use the AccessKey pair to call API operations and access Alibaba Cloud resources, delete or disable the leaked AccessKey pair and enable a new AccessKey pair. Make sure that your core business is not affected. For more information, see Delete an AccessKey pair for a RAM user and Disable an AccessKey pair for a RAM user.
After you manually handle a leaked AccessKey pair, you must find the AccessKey pair leak event on the AccessKey Leak Detection page and click Handle in the Actions column. In the dialog box that appears, select a handling method and click Handle Now.
Valid values include Manually Deleted, Manually Disabled AccessKey Pair, and Add to Whitelist.
NoteAfter you delete the information that involves the AccessKey pair and select a handling method, the status of the AccessKey pair leak event changes to Handled.
If you add the AccessKey pair leak event to the whitelist, the status of the event changes to Added to Whitelist. Then, the event is added to the Handled list.
If you want to remove the AccessKey pair leak event from the whitelist, find the event in the Handled list, go to the details page, and then click Cancel the whitelist.
View AccessKey pair call records
You can view the call records of AccessKey pairs to check whether leaked AccessKey pairs are used by attackers and understand the impact scope of AccessKey pair leak events. This section describes how to view AccessKey pair call records by timeline in the ActionTrail console.
You can also use the AccessKey pair audit feature of ActionTrail to query the Alibaba Cloud services that are accessed by using AccessKey pairs. This way, you can view AccessKey pair call records. For more information, see Query the logs of an AccessKey pair.
Log on to the Security Center console, go to the AccessKey Leak Detection page, and then copy the required AccessKey ID.
Log on to the ActionTrail console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region of the event that you want to query from the drop-down list.
Select AccessKey ID from the Read/Write Type drop-down list, paste the AccessKey ID in the search box, and then select a time range for the query.
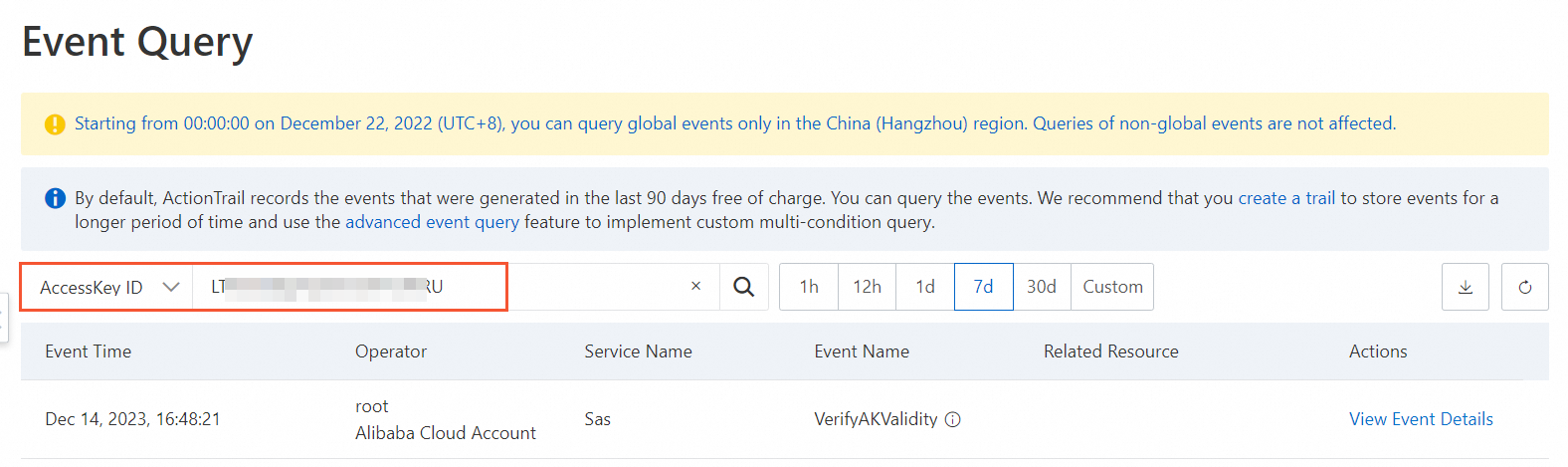
In the list of events, find the required event and click View Event Details in the Actions column to view the details of the event.
For information about fields in management events, see Management event structure.
Continuously pay attention to abnormal AccessKey pair calls
After you handle an AccessKey pair leak event in a timely manner, we recommend that you continuously pay attention to abnormal AccessKey pair calls. This can prevent the occurrence of similar events, help you respond fast when an AccessKey pair leak occurs, and reduce the impact of the event. The following sections describe the methods to continuously pay attention to abnormal AccessKey pair calls. You can use one or more methods based on your requirements.
Monitor abnormal AccessKey pair calls from the attack perspective
Security Center accumulates many years of attack defense experience and builds a large number of large models. Security Center can detect common abnormal AccessKey pair calls. For example, the IP address that initiates the call request performed attacks, the IP address calls AccessKey pairs of multiple users at a time, the called API operation is sensitive, and the AccessKey pair was once leaked. To view alerts for abnormal AccessKey pair calls in the Security Center console, perform the following operations:
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
NoteIf you have activated the Agentic SOC feature, the left-side navigation pane will change to .
Select Cloud threat detection for Alert Type to check whether an alert is generated for abnormal AccessKey pair calls.
If such an alert is generated, you need to view the alert details to check whether the AccessKey pair call is normal.
(Optional) Configure alert notifications.
You can configure alert notification methods in the Security Center console. In the left-side navigation pane, choose System Settings > Notification Settings. On the Email/Internal Message tab, find Alert in the Notification Item column and then configure notification methods. This way, you can receive alerts for abnormal AccessKey pair calls in a timely manner. The Basic Edition of Security Center supports only the internal message notification method. For more information, see Notification settings.
Monitor abnormal AccessKey pair calls made by Alibaba Cloud accounts
ActionTrail provides built-in alerts to monitor abnormal AccessKey pair calls made by Alibaba Cloud accounts. In the ActionTrail console, you can enable the built-in alerts Alert of Frequency of AK Abnormal Usage and Root Account AK Usage Detection. This way, you can receive notifications when an abnormal AccessKey pair call occurs. For more information, see Configure event alerts.
Detect abnormal AccessKey pair calls based on historical behaviors
The Insights feature provided by ActionTrail allows you to analyze AccessKey pairs that have abnormal call rates based on historical behaviors and identify abnormal behaviors in a timely manner. For information about how to enable Insights and view Insights events, see Query Insights events in the ActionTrail console.
Recommendations
We recommend that you do not use the AccessKey pair of an Alibaba Cloud account.
Do not hard code an AccessKey pair into your code. You can manage your AccessKey pair by configuring environment variables. For more information, see Credential security solutions.
Use a private GitHub code repository to manage code or build an internal code hosting system to prevent leaks of source code and sensitive information.