The K8s Service capability of Serverless App Engine (SAE) applications relies on the default DNS resolution service address on Alibaba Cloud. If you need to access internal domain names, you must configure external DNS servers through PrivateZone forwarding rules. This topic describes how to use PrivateZone forwarding rules to support both K8s Service internal resolution and targeted forwarding to external DNS systems, ensuring compatibility between the two and meeting hybrid DNS resolution requirements for your business.
Solution overview
Scenarios
This topic applies to scenarios where SAE applications need to rely on both the built-in authoritative functionality of Private DNS (PrivateZone) and compatible resolution from external DNS systems.
K8s Service resolution: After enabling K8s Service for an SAE application, accessing internal services through
Service Name(such asdemo.test.svc.cluster.local.cn-hangzhou) relies on built-in authoritative records automatically generated by PrivateZone.Internal domain name resolution: If you need to access domain names managed by self-built or third-party DNS systems (such as
www.example.com), the default DNS policy of SAE cannot resolve user's internal domain names. You need to configure PrivateZone forwarding rules to direct resolution requests for specific domain names (such aswww.example.com) to external DNS servers, enabling compatible resolution of both internal and external domain names.
Operation flow

External DNS server resolution process

Prerequisites
You need to set up a DNS Service in your existing business system.
Because there are multiple ways to set up DNS Service (such as setting up in ECS or installing CoreDNS components in container services), this example does not demonstrate the setup process.
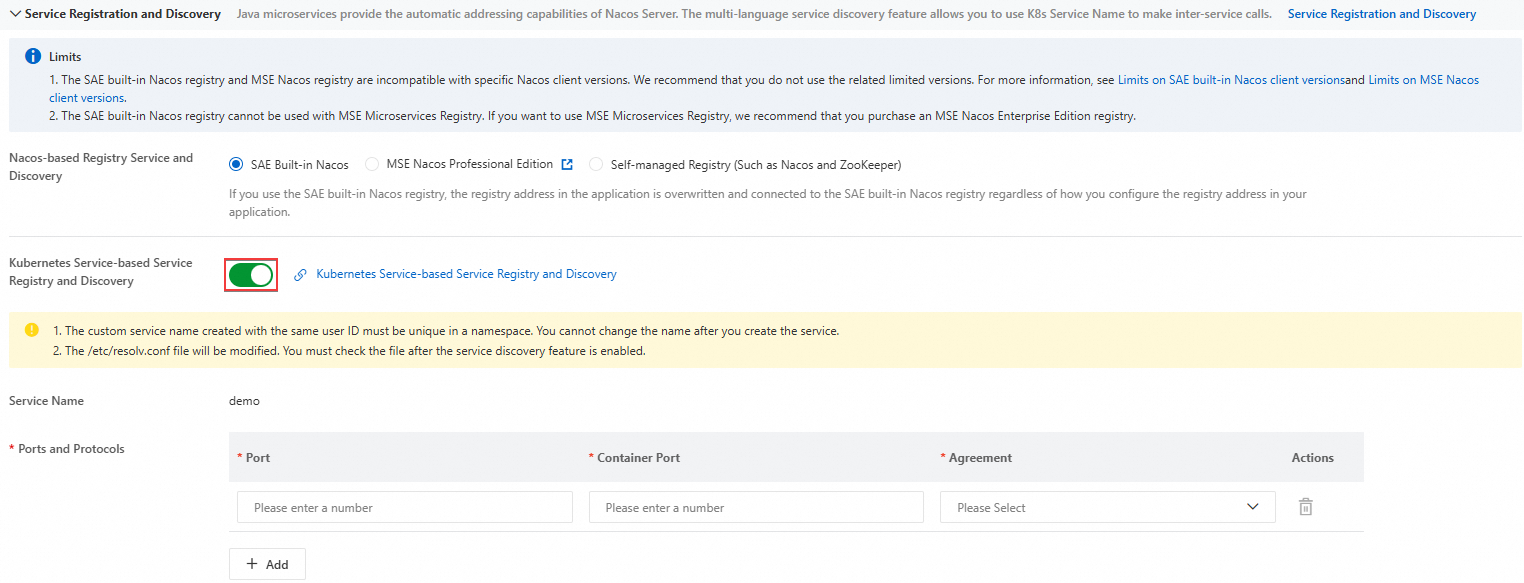
1. Enable K8s Service for SAE application
This topic only introduces the key steps. For detailed configuration, see Use a K8s ServiceName to configure application service access.
On the Deploy Application page of the target SAE application, in the Service Registration and Discovery section, enable Kubernetes Service-based Service Registry and Discovery, and then configure Port, Container Port, and Protocol.
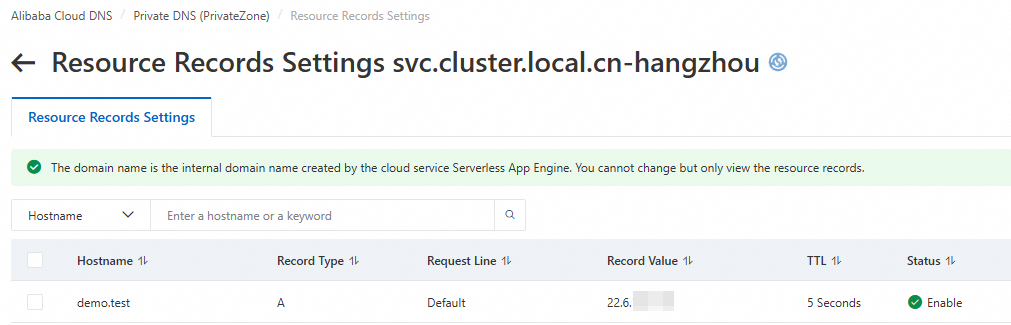
After enabling K8s Service, the system adds a DNS record in the Private DNS (PrivateZone). You can view the DNS record on the Built-in Authoritative Module tab in the Alibaba Cloud DNS console.
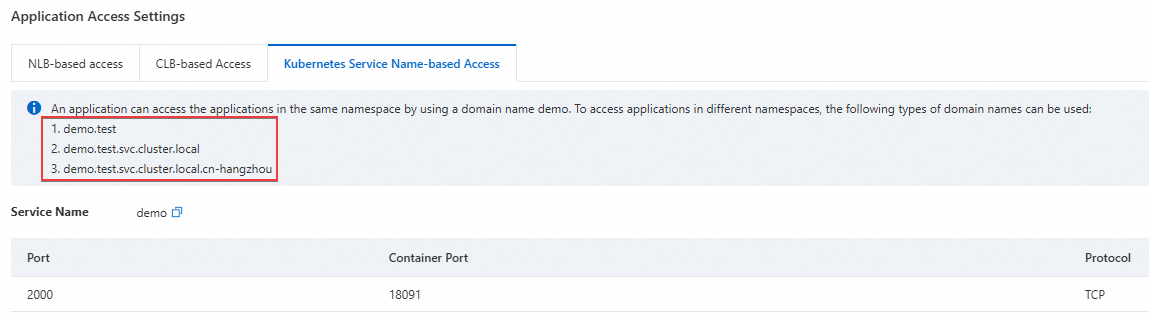
On the Application Information tab of the Basic Information page, find the Application Access Settings section, and copy the access address on the Kubernetes Service Name-based Access tab.
2. Test resolution results before configuration
Use Webshell to log on to the instance of the target SAE application, and then use the nslookup or dig command to resolve the target domain name.
In this example, the domain name of the external DNS server to be resolved iswww.example.com, and the internal IP address is192.168.2.54.
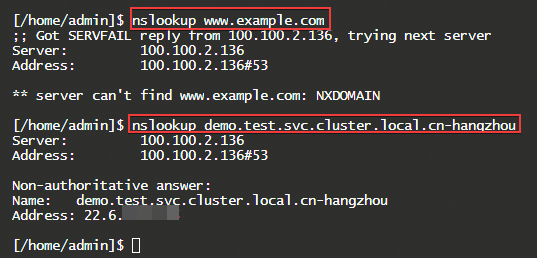
The forward DNS lookup results are as follows:
Unable to resolve to the IP address of the external DNS system.
NoteAfter completing the following steps, you can forward resolution requests to the external DNS system.
Successfully resolved to the record value based on the K8s Service Name access address. This record value can be verified on the Built-in Authoritative Module tab in the Alibaba Cloud DNS console.
3. Create an outbound endpoint
Log on to the Alibaba Cloud DNS console.
In the left-side navigation pane, click Private DNS (PrivateZone). In the upper-right corner of the page, select Configuration Mode, and then click Forward Module.
On the Forward Module tab, select the Outbound Endpoint tab, and then click Create Outbound Endpoint.
In the Create Outbound Endpoint dialog box, configure the Endpoint Name, Outbound VPC, Security Group, and Source IP Address of Outbound Traffic, and then click OK.
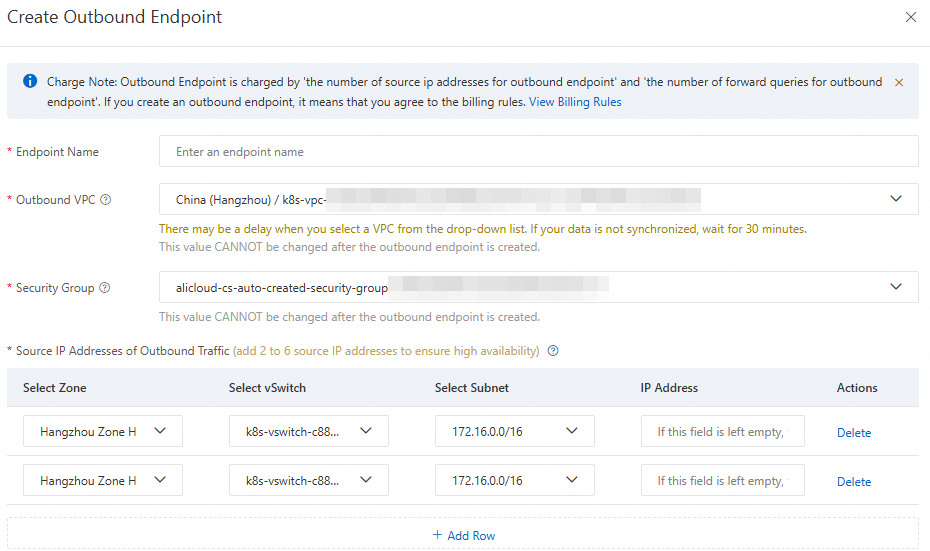
Endpoint Name: The name of the endpoint being created. Name it according to your actual business requirements.
Outbound VPC: All outbound DNS query traffic from Forward Module will be forwarded through this VPC.
ImportantOnce an outbound endpoint is created, the "Outbound VPC" cannot be modified to avoid accidental operations that may interrupt online traffic.
Security Group: The rules in the security group will be applied to the outbound VPC.
ImportantKeep port 53 open for outbound traffic in the security group. Inbound rules do not affect the forwarding function.
Currently, only non-managed security groups are supported.
Source IP Address of Outbound Traffic: Available IP addresses in the subnet of the available zone.
ImportantTo ensure high availability, the resolver requires at least two outbound source IP addresses, and it is recommended that these two IP addresses be distributed in different zones. The resolver allows a maximum of six outbound source IP addresses.
If no IP address is configured, the system will automatically assign one.
If the external DNS server has a public IP address, you need to configure a public NAT Gateway to ensure that the IP can access the Internet.
4. Configure forwarding rules and effective scope
4.1 Configure forwarding rules
Go to the Private DNS (PrivateZone) page. On the Forward Module tab, click Forwarding Rules, and then click Create Forwarding Rule.
In the Create Forwarding Rule panel that appears, configure the forwarding rule parameters, and then click OK.
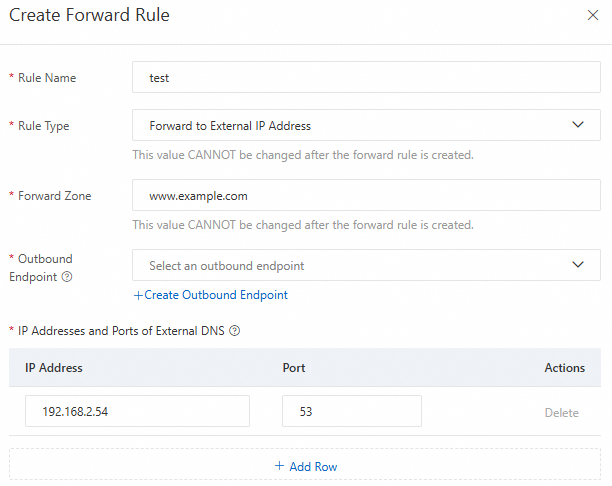
Rule Name: Customize the rule name according to your business needs and business meaning.
Rule Type: Currently, only forwarding to external IP addresses is supported.
Forwarding Domain (Zone): Configure the domain name (Zone) that needs to be forwarded for resolution.
ImportantForwarding of all domain names (root domain) is supported. Enter a period:
..Forwarding of top-level domains is supported. For example, you can enter:
com,cn,top, etc.If a resolution request matches multiple forwarding domains at the same time, such as:
example.com,com,., etc., according to the longest Zone matching priority rule, the resolution request will matchexample.com.
Outbound Endpoint: Select the outbound endpoint name configured in the previous step.
IP Address and Port of External DNS System: The IP address and port of the target server to which DNS query traffic is forwarded. You can create a maximum of six, and both private IP addresses and public IP addresses are supported.
ImportantIP addresses within the following address ranges are reserved by the system and cannot be configured as IP addresses for external DNS systems:
100.100.2.136~100.100.2.138, 100.100.2.116~100.100.2.118.If the external DNS server you specify has a public IP address, and the ECS in your outbound endpoint VPC does not have a public IP address, please activate NAT Gateway and configure private SNAT entry for NAT Gateway.
4.2 Configure the effective scope of forwarding rules
Click Actions in the column of the created forwarding rule, and then click Effective Scope of Forwarding Rule. In the Effective Scope of Forward Zone panel that appears, configure the VPC where the associated forwarding domain rule takes effect, and then click OK.
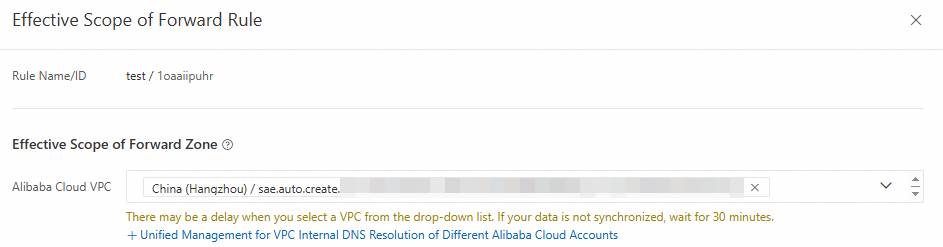
The VPC associated here must be the same as the VPC where the target SAE application is located.
You can associate a forwarding rule only with a VPC that is in the same region as the outbound endpoint specified for the rule.
When different forwarding rules are associated with the same VPC, the forwarding domains cannot be the same.
When a forwarding rule and a built-in authoritative domain name have the same effective scope, the forwarding domain can be the same as the built-in authoritative domain name, and domain name resolution requests in the associated VPC are processed by the built-in authority first.
Cross-account VPC association is supported. For more information, see Associate VPCs across accounts.
5. Verify resolution results
Use Webshell to log on to the instance of the target SAE application, and then use the nslookup or dig command to resolve the target domain name.
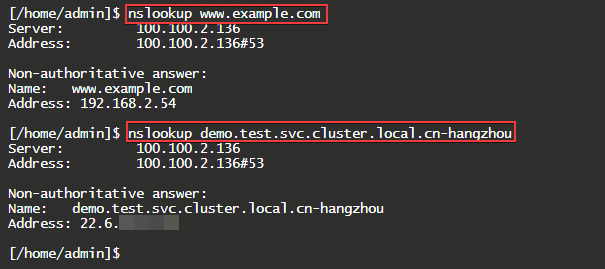
The forward DNS lookup results show that:
Successfully resolved to the IP address of the external DNS system.
Successfully resolved to the record value based on the K8s Service Name access address.
This proves that the DNS Forward Module configuration is successful.