This topic describes how to use a tag policy to standardize tag-related operations.
Background information
The Tag Policy feature supports the single-account mode and resource directory mode. For more information, see Modes of the Tag Policy feature.
When you use the Tag Policy feature for the first time, we recommend that you enable the feature by using a test account that has a small number of resources. If the test is successful, you can enable the feature by using a production account.
Use the Tag Policy feature that is in single-account mode
Step 1: Enable the Tag Policy feature
Log on to the Resource Management console.
In the left-side navigation pane, choose Tag Policy > Settings.
On the Settings for Current Account tab, set Tag Policy to Enable.
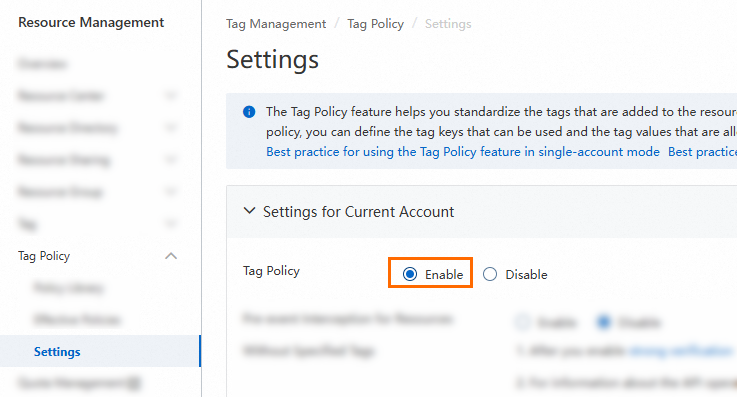
In the Enable Tag Policy dialog box, click Enable.
When you enable the Tag Policy feature, the system creates the service-linked role AliyunServiceRoleForTag. This role can resolve cross-service access issues. For more information, see Service-linked role for Tag.
Step 2: Create a tag policy
You can create and configure a tag policy to define the tags that must be added to a resource. This ensures that the tags added to the resource are compliant.
In the left-side navigation pane, choose Tag Policy > Policy Library.
On the Policy Library page, click Create Tag Policy.
In the Basic Information section, configure Policy Name and Policy Description.
In the Policy Details section, configure the policy details in one of the following modes:
Quick Mode (recommended)
Select a policy scenario and configure rules based on your business requirements.
Add Tags with Specified Tag Values to Resources
In a tag policy, you can specify tags that must be added to resources. You can also enable features such as automatic detection, automatic remediation, and pre-event interception for non-compliant tags based on the execution modes you specify for the tag policy.
Parameter
Description
Tag Key
Enter a tag key.
Specify Allowed Tag Values
The tag value that is allowed for the tag key. You can specify multiple tag values. You can also use an asterisk (*) as a wildcard to indicate any tag values.
Policy Execution Mode
Post-event Detection
Post-event detection is the default execution mode of a tag policy used in this scenario. You can enable the following detection rules based on your business requirements. You can view the detection results on the details page of the related effective policy.
Specify Resource Types for Detection: By default, post-event detection is performed for all the supported types of resources. You can specify resource types based on your business requirements. If you specify resource types, post-event detection is performed only for the specified types of resources.
Specify Resource Groups: By default, post-event detection is performed for resources in all resource groups. You can specify resource groups based on your business requirements. You can specify up to 20 resource groups.
NoteThe Tag Policy feature in resource directory mode does not support the Specify Resource Groups parameter.
Specify Region Scope: By default, post-event detection is performed for resources in all regions. You can specify regions based on your business requirements. You can specify up to 20 regions.
Specify Tag Scope: You can specify a tag scope based on your business requirements. After you specify a tag scope, post-event detection is performed only for resources with the specified tags. The tags you specify have an AND relation. You can specify up to 20 tags.
Specify Regular Expression of Resource Names: You can specify a regular expression based on your business requirements. After you specify a regular expression, post-event detection is performed only for resources whose names match this regular expression. For example, you can specify the regular expression
abc-.*. This indicates that post-event detection is performed for resources whose names start withabc-.Automatic Remediation: If you select this option, the system automatically remediates non-compliant tags. You must specify a scope for each tag value that you want to enable automatic remediation. The scope for each tag value must be unique.
Pre-event Interception
When you create a resource or add tags to an existing resource, the system performs a check. If the tags defined in the tag policy are not added to the resource, the resource creation or tag addition operation fails. For more information, see Enable pre-event interception of non-compliant tags.
Match Tag Values with Specified Regular Expression
You can specify a regular expression in a tag policy to limit the format of tag values. Tag values that do not match the regular expression can be automatically remediated.
Parameter
Description
Tag Key
Enter a tag key.
Specify Allowed Tag Values
Enter a regular expression to limit the format of tag values.
Policy Execution Mode
Post-event detection is the default execution mode of a tag policy used in this scenario. You can enable the following detection rules based on your business requirements. You can view the detection results on the details page of the related effective policy.
Specify Resource Types for Detection: By default, post-event detection is performed for all the supported types of resources. You can specify resource types based on your business requirements. If you specify resource types, post-event detection is performed only for the specified types of resources.
Specify Resource Groups: By default, post-event detection is performed for resources in all resource groups. You can specify resource groups based on your business requirements. You can specify up to 20 resource groups.
NoteThe Tag Policy feature in resource directory mode does not support the Specify Resource Groups parameter.
Specify Region Scope: By default, post-event detection is performed for resources in all regions. You can specify regions based on your business requirements. You can specify up to 20 regions.
Specify Tag Scope: You can specify a tag scope based on your business requirements. After you specify a tag scope, post-event detection is performed only for resources with the specified tags. The tags you specify have an AND relation. You can specify up to 20 tags.
Specify Regular Expression of Resource Names: You can specify a regular expression based on your business requirements. After you specify a regular expression, post-event detection is performed only for resources whose names match this regular expression. For example, you can specify the regular expression
abc-.*. This indicates that post-event detection is performed for resources whose names start withabc-.Automatic Remediation: If you select this option, the system automatically remediates non-compliant tags. You must specify a scope for each tag value that you want to enable automatic remediation. The scope for each tag value must be unique.
Automatically Inherit Tags for Resources from Resource Groups
After you add tags to a resource group, you can configure a tag policy to use the automatic tag inheritance feature. This feature allows resources that are added to or created in a resource group to automatically inherit the tags that are added to the resource group.
Parameter
Description
Tag Key
Enter a tag key.
For Tag Policy in single-account mode, you can click View Resource Groups with the Tag Key to view the resource groups to which the tag key is added.
Specify Resource Types for Detection
By default, all the supported types of resources are detected. You can specify resource types based on your business requirements. If you specify resource types, post-event detection is performed only for the specified types of resources.
Specify Resource Groups
By default, resources in all resource groups are detected. You can specify resource groups based on your business requirements. You can specify up to 20 resource groups.
NoteThe Tag Policy feature in resource directory mode does not support the Specify Resource Groups parameter.
Specify IDs of Resources to Be Excluded
You can specify the IDs of resources that do not inherit tags from the resource groups to which the resources belong. You can specify up to 20 resource IDs.
Specify Region Scope
By default, resources in all regions are detected. You can specify regions based on your business requirements. You can specify up to 20 regions.
Specify Tag Scope
You can specify a tag scope based on your business requirements. After you specify a tag scope, post-event detection is performed only for resources with the specified tags. The tags you specify have an AND relation. You can specify up to 20 tags.
You can click Add Policy Scenario and Tag Key to configure rules for multiple policy scenarios and tag keys.
JSON
In this mode, you need to specify the policy details in the JSON format. If you have high requirements for tag policies, use this mode. Before you use this mode, you must have a command of the syntax of a tag policy. For more information, see Syntax of a tag policy.
Click Create.
Step 3: Attach the tag policy
After the tag policy is created, you must attach the policy to the current Alibaba Cloud account. This way, you can use the tag policy to standardize tags added to the resources within the account.
In the left-side navigation pane, choose Tag Policy > Policy Library.
On the Policy Library page, click the Current Account tab.
NoteIf the Tag Policy feature in resource directory mode is disabled, skip this step.
In the Attach message, click Attach.
The tag policy is attached to the Alibaba Cloud account that you use for logon.
Step 4: (Optional) View the effective policy
After the tag policy is attached to the current Alibaba Cloud account, you can view the effective policy of the account.
In the left-side navigation pane, choose Tag Policy > Effective Policies.
Click the tag key. On the page that appears, you can view the information about the effective policy for the current account. The information includes basic information, involved tag policies, detection results, and remediation records.
Step 5: Check whether the tag policy is in effect
You can use the current Alibaba Cloud account or a RAM user within the account to perform a tag-related operation to check whether the tag policy is in effect. For example, you apply a tag policy to a virtual private cloud (VPC), and the tag policy defines that the tag CostCenter:Beijing must be added to the VPC. When you add tags to the VPC, only the compliant tag CostCenter:Beijing is added to the VPC. Non-compliant tags such as costCenter:Shanghai fail to be added to the VPC. This indicates that the tag policy is in effect.
Use the Tag Policy feature that is in resource directory mode
For security purposes, we recommend that you create a RAM user within the management account of your resource directory, attach the AdministratorAccess policy to the RAM user, and then use the RAM user as the administrator of the resource directory. Perform the following operations by using the RAM user. For more information about how to create a RAM user and grant permissions to the RAM user, see Create a RAM user and Grant permissions to RAM users.
Step 1: Enable the Tag Policy feature
Log on to the Resource Management console.
In the left-side navigation pane, choose Tag Policy > Settings.
On the Settings for Resource Directory tab, set Tag Policy to Enable.
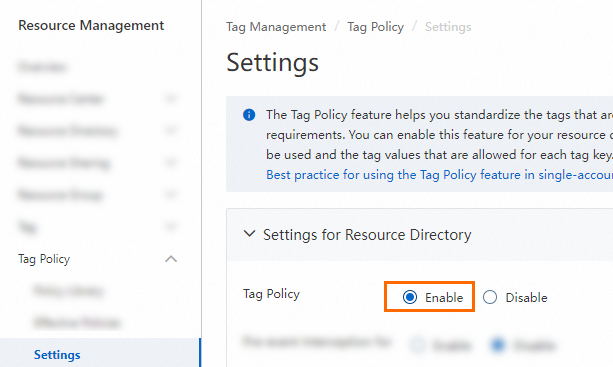 Note
NoteYou can also use the management account of a resource directory to enable the Tag Policy feature in single-account mode on the Settings for Current Account tab. This feature takes effect on the management account.
In the Enable Tag Policy dialog box, click Enable.
When you enable the Tag Policy feature, the system creates the service-linked role AliyunServiceRoleForTag. This role can resolve cross-service access issues. For more information, see Service-linked role for Tag.
Step 2: Create a tag policy
You can create and configure a tag policy to define the tags that must be added to a resource. This ensures that the tags added to the resource are compliant.
In the left-side navigation pane, choose Tag Policy > Policy Library.
On the Resource Directory tab of the Policy Library page, click Create Tag Policy.
In the Basic Information section, configure Policy Name and Policy Description.
In the Policy Details section, configure the policy details in one of the following modes:
Quick Mode (recommended)
Select a policy scenario and configure rules based on your business requirements.
Add Tags with Specified Tag Values to Resources
In a tag policy, you can specify tags that must be added to resources. You can also enable features such as automatic detection, automatic remediation, and pre-event interception for non-compliant tags based on the execution modes you specify for the tag policy.
Parameter
Description
Tag Key
Enter a tag key.
Specify Allowed Tag Values
The tag value that is allowed for the tag key. You can specify multiple tag values. You can also use an asterisk (*) as a wildcard to indicate any tag values.
Policy Execution Mode
Post-event Detection
Post-event detection is the default execution mode of a tag policy used in this scenario. You can enable the following detection rules based on your business requirements. You can view the detection results on the details page of the related effective policy.
Specify Resource Types for Detection: By default, post-event detection is performed for all the supported types of resources. You can specify resource types based on your business requirements. If you specify resource types, post-event detection is performed only for the specified types of resources.
Specify Resource Groups: By default, post-event detection is performed for resources in all resource groups. You can specify resource groups based on your business requirements. You can specify up to 20 resource groups.
NoteThe Tag Policy feature in resource directory mode does not support the Specify Resource Groups parameter.
Specify Region Scope: By default, post-event detection is performed for resources in all regions. You can specify regions based on your business requirements. You can specify up to 20 regions.
Specify Tag Scope: You can specify a tag scope based on your business requirements. After you specify a tag scope, post-event detection is performed only for resources with the specified tags. The tags you specify have an AND relation. You can specify up to 20 tags.
Specify Regular Expression of Resource Names: You can specify a regular expression based on your business requirements. After you specify a regular expression, post-event detection is performed only for resources whose names match this regular expression. For example, you can specify the regular expression
abc-.*. This indicates that post-event detection is performed for resources whose names start withabc-.Automatic Remediation: If you select this option, the system automatically remediates non-compliant tags. You must specify a scope for each tag value that you want to enable automatic remediation. The scope for each tag value must be unique.
Pre-event Interception
When you create a resource or add tags to an existing resource, the system performs a check. If the tags defined in the tag policy are not added to the resource, the resource creation or tag addition operation fails. For more information, see Enable pre-event interception of non-compliant tags.
Match Tag Values with Specified Regular Expression
You can specify a regular expression in a tag policy to limit the format of tag values. Tag values that do not match the regular expression can be automatically remediated.
Parameter
Description
Tag Key
Enter a tag key.
Specify Allowed Tag Values
Enter a regular expression to limit the format of tag values.
Policy Execution Mode
Post-event detection is the default execution mode of a tag policy used in this scenario. You can enable the following detection rules based on your business requirements. You can view the detection results on the details page of the related effective policy.
Specify Resource Types for Detection: By default, post-event detection is performed for all the supported types of resources. You can specify resource types based on your business requirements. If you specify resource types, post-event detection is performed only for the specified types of resources.
Specify Resource Groups: By default, post-event detection is performed for resources in all resource groups. You can specify resource groups based on your business requirements. You can specify up to 20 resource groups.
NoteThe Tag Policy feature in resource directory mode does not support the Specify Resource Groups parameter.
Specify Region Scope: By default, post-event detection is performed for resources in all regions. You can specify regions based on your business requirements. You can specify up to 20 regions.
Specify Tag Scope: You can specify a tag scope based on your business requirements. After you specify a tag scope, post-event detection is performed only for resources with the specified tags. The tags you specify have an AND relation. You can specify up to 20 tags.
Specify Regular Expression of Resource Names: You can specify a regular expression based on your business requirements. After you specify a regular expression, post-event detection is performed only for resources whose names match this regular expression. For example, you can specify the regular expression
abc-.*. This indicates that post-event detection is performed for resources whose names start withabc-.Automatic Remediation: If you select this option, the system automatically remediates non-compliant tags. You must specify a scope for each tag value that you want to enable automatic remediation. The scope for each tag value must be unique.
Automatically Inherit Tags for Resources from Resource Groups
After you add tags to a resource group, you can configure a tag policy to use the automatic tag inheritance feature. This feature allows resources that are added to or created in a resource group to automatically inherit the tags that are added to the resource group.
Parameter
Description
Tag Key
Enter a tag key.
For Tag Policy in single-account mode, you can click View Resource Groups with the Tag Key to view the resource groups to which the tag key is added.
Specify Resource Types for Detection
By default, all the supported types of resources are detected. You can specify resource types based on your business requirements. If you specify resource types, post-event detection is performed only for the specified types of resources.
Specify Resource Groups
By default, resources in all resource groups are detected. You can specify resource groups based on your business requirements. You can specify up to 20 resource groups.
NoteThe Tag Policy feature in resource directory mode does not support the Specify Resource Groups parameter.
Specify IDs of Resources to Be Excluded
You can specify the IDs of resources that do not inherit tags from the resource groups to which the resources belong. You can specify up to 20 resource IDs.
Specify Region Scope
By default, resources in all regions are detected. You can specify regions based on your business requirements. You can specify up to 20 regions.
Specify Tag Scope
You can specify a tag scope based on your business requirements. After you specify a tag scope, post-event detection is performed only for resources with the specified tags. The tags you specify have an AND relation. You can specify up to 20 tags.
You can click Add Policy Scenario and Tag Key to configure rules for multiple policy scenarios and tag keys.
JSON
In this mode, you need to specify the policy details in the JSON format. If you have high requirements for tag policies, use this mode. Before you use this mode, you must have a command of the syntax of a tag policy. For more information, see Syntax of a tag policy.
Click Create.
Step 3: Attach the tag policy
After the tag policy is created, you must attach the tag policy to the Root folder, a specific folder, or a specific member. This way, you can use the tag policy to standardize the tags added to the resources within the members.
In the left-side navigation pane, choose Tag Policy > Policy Library.
On the Policy Library page, click the Resource Directory tab.
Find the desired tag policy and click Attach in the Actions column.
In the Attach dialog box, select the objects to which you want to attach the tag policy, and click Attach.
The effective scope of the tag policy varies based on the object type.
Root folder: If you attach the tag policy to the Root folder, the tag policy takes effect for all members in the resource directory.
Specific folder: If you attach the tag policy to a specific folder, the tag policy takes effect only for all members in the folder.
Specific member: If you attach a tag policy to a specific member, the tag policy takes effect only for the member.
NoteIf you enable only the Tag Policy feature in resource directory mode, you cannot attach tag policies to the management account of your resource directory. You can create tag policies for and attach tag policies to the account only after you enable the Tag Policy feature in single-account mode.
Step 4: (Optional) View the effective policy
After the tag policy is attached, you can use the RAM user to view the effective policy of the Root folder, the specific folder, or the specific member. You can use a member to view the effective policy of the member. An effective policy is obtained based on the inheritance relationship of a tag policy. For more information, see Inheritance of a tag policy and calculation of an effective tag policy.
In the left-side navigation pane, choose Tag Policy > Effective Policies.
View the related effective policy.
Click the All Members tab to view the members to which tag policies are attached in the resource directory. You can click View Detection Results in the Actions column that corresponds to a member. On the page that appears, you can view the information about the effective policy for the member. The information includes basic information, involved tag policies, detection results, and remediation records.
Click the Resource Directory tab to view the effective policies that are attached to the folders and members in the resource directory. You can click a tag key. On the page that appears, you can view the information about the effective policy for the folder or member. The information includes basic information, involved tag policies, detection results, and remediation records.
Step 5: Check whether the tag policy is in effect
Use the RAM user to access a member to which the tag policy is attached.
For more information, see Use a member to log on to the Alibaba Cloud Management Console.
Perform a tag-related operation on a resource within the member to check whether the tag policy is in effect.
For example, you apply a tag policy to a VPC, and the tag policy defines that the tag
CostCenter:Beijingmust be added to the VPC. When you add tags to the VPC, only the compliant tagCostCenter:Beijingis added to the VPC. Non-compliant tags such ascostCenter:Shanghaifail to be added to the VPC. This indicates that the tag policy is in effect.