This topic describes how to establish a ClassicLink connection to connect a classic network-type Elastic Compute Service (ECS) instance to an ApsaraDB RDS for PostgreSQL instance that resides in a virtual private cloud (VPC).
Background information
ApsaraDB RDS for PostgreSQL instances that use standard SSDs or enhanced SSDs (ESSDs) no longer support the classic network. We recommend that you use the VPC network type that is more secure compared with the classic network. If your ECS instance resides in the classic network, we recommend that you migrate your ECS instance to the same VPC as your RDS instance. This way, the instances can communicate over an internal network. If you do not want to migrate your classic network-type ECS instance, you can connect the classic network-type ECS instance to your VPC-type RDS instance by using the method that is described in this topic. For more information, see Migrate an ECS instance from the classic network to a VPC.
Prerequisites
The ECS instance resides in the classic network.
The RDS instance resides in a VPC.
The ECS instance and the RDS instance reside in the same region.
The private IP address of the ECS instance is added to an IP address whitelist of the RDS instance. For more information, see Configure an IP address whitelist.
Procedure
Enable ClassicLink for the VPC in which the RDS instance resides.
Log on to the ApsaraDB RDS console and go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
In the left-side navigation pane, click Database Connection.
Click the VPC ID to the right of Network Type to go to the VPC console.
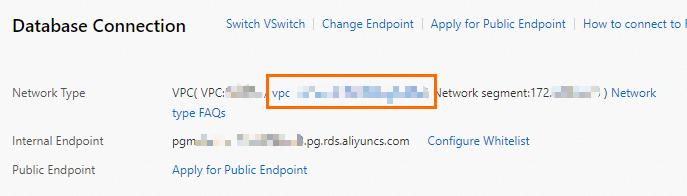
In the upper-right corner of the page that appears, click Enable ClassicLink.
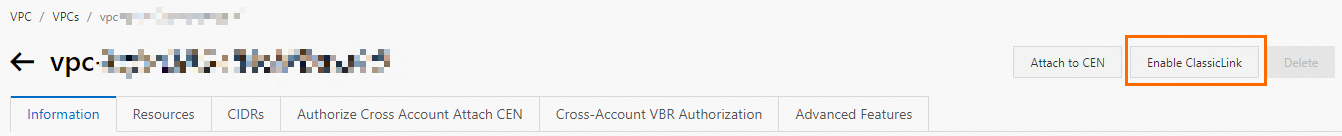
In the message that appears, click OK.
Configure a security group rule for ClassicLink for the ECS instance.
Log on to the ECS console.
In the left-side navigation pane, choose . In the top navigation bar, select a region.
Find the classic network-type ECS instance. Then, click the
 icon and choose Network and Security Group > Connect to VPC in the Actions column.
icon and choose Network and Security Group > Connect to VPC in the Actions column. In the dialog box that appears, configure the VPC parameter and click Confirm.
Click Go to the instance security group list and add ClassicLink rules.
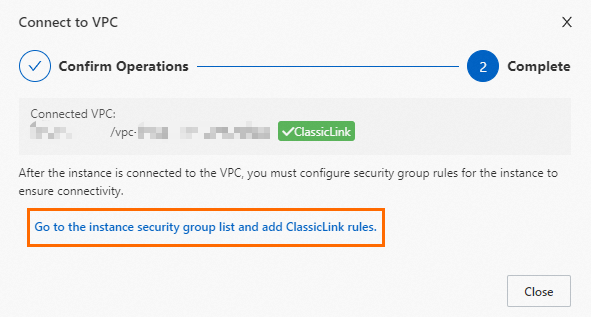
In the Actions column corresponding to the security group, click Manage Rules.
On the Security Group Rules page, click Add ClassicLink Rule in the upper-right corner. Configure the security group rule by setting the parameters described in the following table. Then, click OK.
Parameter
Description
Classic Security Group
The name of the security group for the classic network. You do not need to configure this parameter.
Select VPC
The VPC in which your want to add the rule.
VPC-type Security Groups
The security groups that you want to connect in the VPC.
Mode
The authorization method. In this example, Classic <=> VPC is selected.
Classic <=> VPC: This mode allows resources in the classic network and VPCs to access each other. We recommend that you select this mode.
Classic Network => VPCs: This mode allows only resources in the classic network to access resources in VPCs.
VPCs => Classic Network: This mode allows only resources in VPCs to access resources in the classic network.
Protocol Type
The protocol that is used in communication. In the example, Custom TCP is automatically selected. You do not need to change the value.
Port Range
The port range that is in the
xx/xxformat. For example, if you want to authorize port 5432 for communication., enter 5432/5432.Priority
The priority of the rule. A smaller value specifies a higher priority. Example:
1.Description
The description of the rule.
Connect to the ECS instance and run the following command to connect the ECS instance to the RDS instance by using the internal endpoint:
psql -h <Internal endpoint of the RDS instance> -U <Username of the RDS instance> -p <Port number> -d <Database name>NoteBefore you run the command, make sure that the PostgreSQL client is installed on the ECS instance and an account is created on the RDS instance. For more information about how to connect to an RDS instance, see Connect to an ApsaraDB RDS for PostgreSQL instance.