When you use the Global Active Database (GAD) feature of ApsaraDB RDS for the first time, you must create a default role named AliyunDTSDefaultRole and attach the system policy AliyunDTSRolePolicy to this role. This allows Data Transmission Service (DTS) to access your RDS and DTS resources for the further configuration and management of GAD. The authorization does not impact the performance of the RDS instance.
If you log on to the RAM console using your Alibaba Cloud account and find that your account is already authorized, skip the operations in this topic and start from creating a GAD instance group.
Prerequisites
An Alibaba Cloud account is created. For more information, see Create an Alibaba Cloud account.
Policy description
The AliyunDTSRolePolicy policy is used to grant permissions to the default role AliyunDTSDefaultRole. These permissions allow DTS to manage multiple cloud resources such as ApsaraDB for RDS, ECS, PolarDB, ApsaraDB for MongoDB, ApsaraDB for Redis, PolarDB-X, DataHub, and Elasticsearch. For more information, see AliyunDTSRolePolicy.
For more information about policies, see Policy structure and syntax.
Method 1: Authorize through the RAM Quick Authorization page (recommended)
Use your Alibaba Cloud account to access the RAM Quick Authorization page for AliyunDTSDefaultRole. Then, click Authorize on the page and wait until the authorization is completed.
Method 2: Authorize in the RAM console
Find the default role.
Log on to the RAM console.
Optional: In the left-side navigation pane, choose .
In the text box next to Create Role, enter AliyunDTSDefaultRole, and click the search icon.
NoteIf the role AliyunDTSDefaultRole is not found, we recommend that you use Method 1 of this topic for authorization.
Click the role name in the search results.
Grant the required permissions to the RAM role.
On the Permissions tab, click Precise Permission.
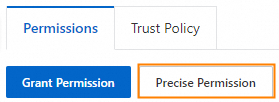
Optional. In the Precise Permission panel, select System Policy for the Type parameter.

In the Policy Name field, enter AliyunDTSRolePolicy.
Click OK.
To verify the authorization, click the
 icon on the right side of the Permissions tab to refresh the page.
icon on the right side of the Permissions tab to refresh the page.
After the required permissions are granted, click Close.
View the authorization result
You can perform the following steps to view the result of authorization by using the default role.
Log on to the RAM console.
Optional: In the left-side navigation pane, choose .
In the text box next to Create Role, enter AliyunDTSDefaultRole, and click the search icon.
Click the role name in the search results.
Click AliyunDTSDefaultRole to view the details.
If both of the following conditions are met, the authorization is successful:
On the Trust Policy tab,
dts.aliyuncs.comis included in the Service field.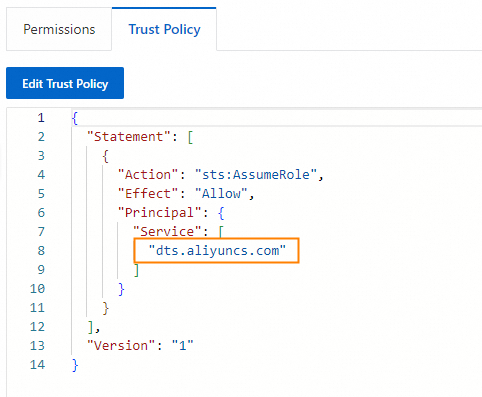
On the Permissions tab, the AliyunDTSRolePolicy policy exists.
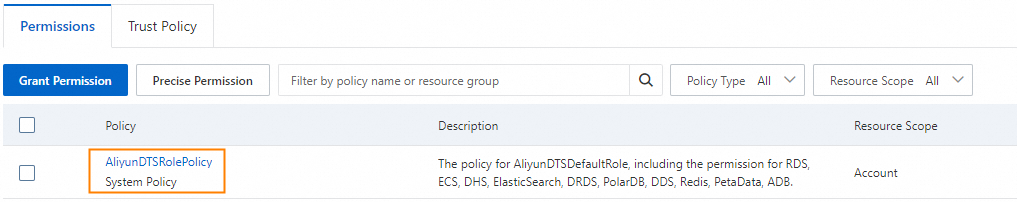
If one of the preceding conditions is not met, the authorization fails. You must grant the permissions again.
Delete the role AliyunDTSDefaultRole. Authorize again.
NoteWe recommend that you use Method 1 of this topic for authorization.
For more information about how to delete a RAM role, see Delete a RAM role.