If the cloud-native gateway and the node where the backend service is deployed are in different security groups, you must configure a security group rule to grant the cloud-native gateway access to the backend service.
Background information
A security group is a virtual firewall that controls the inbound and outbound traffic of Elastic Compute Service (ECS) instances and Elastic Network Interfaces (ENIs) within the group. This enhances the security of your ECS instances. Security groups provide stateful inspection and packet filtering, allowing you to define security domains in the cloud based on security group attributes and rule configurations. For more information, see Security group overview.
When you create a cloud-native gateway, you must select a VPC and a security group type. We recommend that you select the same security group type as the one to which the backend service belongs. Based on your selection, the cloud-native gateway creates a managed security group to manage its instance nodes. Because the cloud-native gateway and the node where the backend service is deployed are in different security groups, you must grant the cloud-native gateway permission to access the required port range in the backend service's security group.
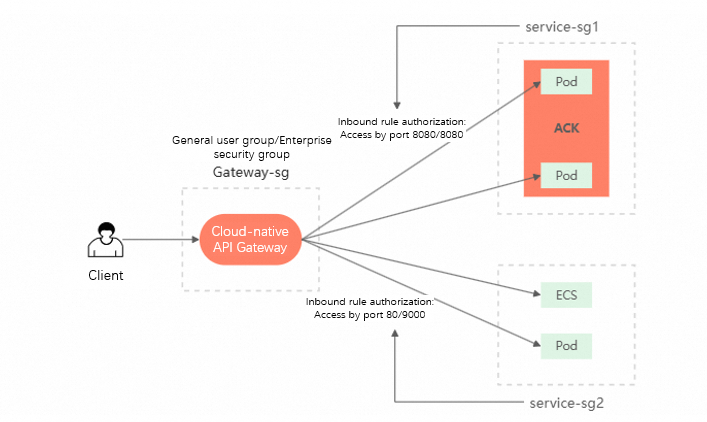
Step 1: Obtain the security group of the node on which the destination service is deployed
Upstream services associated with a cloud-native gateway are typically deployed in containers or on ECS instances. You can obtain the security group ID in the following ways.
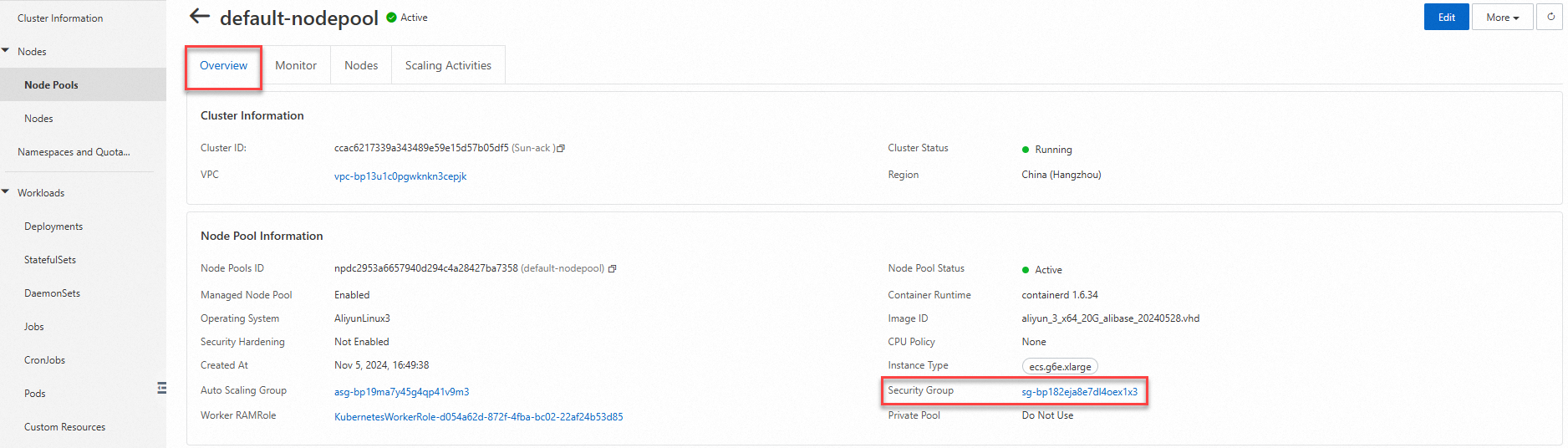
Backend service deployed in an ACK managed cluster
Log on to the ACK console. In the navigation pane on the left, click Clusters.
On the Clusters page, find the cluster to manage and click its name. In the left-side navigation pane, choose .
On the Node Pools page, click the destination node and select the Basic Information tab to obtain the security group ID.
Backend service deployed in an ACK Serverless cluster
Log on to the ACK console. In the navigation pane on the left, click Clusters.
On the Clusters page, click the name of the destination cluster. Then, click the Basic Information tab to find the security group ID.

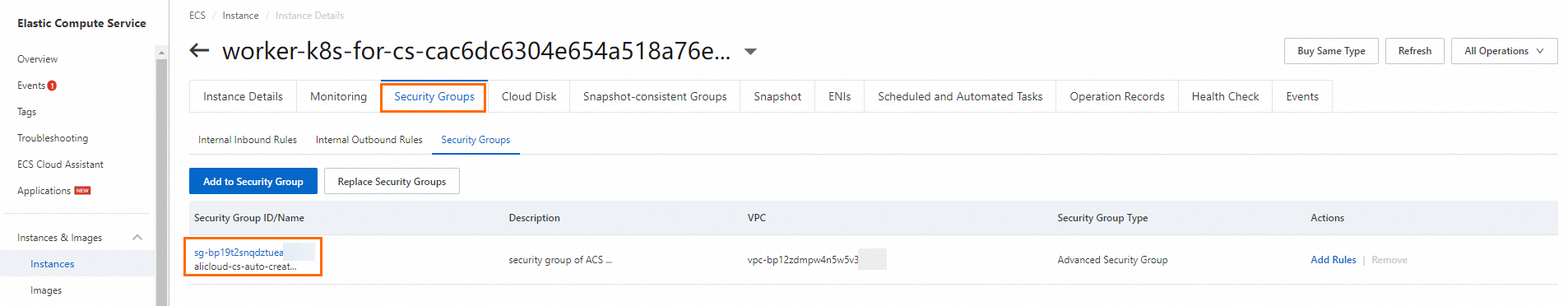
Backend service deployed on an ECS instance
Log on to the ECS console.
In the left-side navigation pane, choose .
On the Instances page, click the ECS instance where the destination service is deployed, and then click the Security Groups tab to obtain its security group ID.
Step 2: Add a security group authorization rule
Log on to the MSE console.
In the left-side navigation pane, choose Cloud-native Gateway > Gateways. In the top navigation bar, select a region.
On the Gateways page, click the name of the target gateway. In the navigation pane on the left, click Overview and then select the Security Group Authorization tab.
Click Add Security Group Rule. In the Security Group ID text box, paste the security group ID from Step 1 and select the security group.

For Port Range, enter a port range for the security group authorization in the Start Port/End Port format.
You can enter multiple port ranges. After you enter a port range, press Enter to apply it.

Click Save.
The cloud-native gateway generates a corresponding rule.

The security group rule created in the cloud-native gateway is also displayed in the security group to which the target node belongs.
Delete a security group authorization rule
Log on to the MSE console.
In the left-side navigation pane, choose Cloud-native Gateway > Gateways. In the top navigation bar, select a region.
On the Gateways page, click the ID of the gateway.
In the navigation pane on the left, click Overview. On the Add Security Group Rule tab, find the rule that you want to delete, click Delete in the Actions column, and then click OK.
By default, only the security group rule for the cloud-native gateway is deleted. To also delete the rule from the security group of the destination node, select Cascade Delete The Preceding Inbound Rules In This Security Group.
FAQ
Question 1: I have granted permissions to the security group. Why am I unable to access the service?
You can perform the following steps to troubleshoot the issue:
First, check whether the service is deployed on the correct node.
For example, the service is deployed on Node A, but you granted permissions to the security group to which Node B belongs.
Check whether multiple security groups are configured for the target node.
If multiple security groups are configured, we recommend that you grant permissions to each security group.
Question 2: I have granted permissions to the security group. I was able to access the service from the gateway, but now the access fails. Why?
You can perform the following steps to troubleshoot the issue:
First, make sure that the service is running as expected.
You can run the
curlcommand on other nodes in the same security group to check the service connectivity.Check whether the port exposed by the published service has changed.
For example, the port was 8080 and you granted permissions only to port 8080 for the cloud-native gateway. If the port is later changed to 8081, you must modify the port in the security group authorization rule. To prevent this issue, we recommend that you specify a wider port range, such as 1/65535, when you configure the security group authorization.