An egress gateway is an edge gateway that connects internal and external networks. An egress gateway is used to control network traffic and enable remote access and communications. Microservices Engine (MSE) cloud-native gateways can serve as egress gateways to provide stable, efficient, and secure egress services for Container Service for Kubernetes (ACK) clusters to meet business requirements for egress traffic management and security control.
Benefits of MSE cloud-native gateways
MSE cloud-native gateways provide managed gateway services and are deployed in standalone mode. MSE cloud-native gateways are not affected by ACK clusters and provide high stability.
MSE cloud-native gateways provide a variety of Layer-7 HTTP protocol governance capabilities, including IP address blacklists and whitelists, throttling, load balancing, Transport Layer Security (TLS) offloading, traffic mirroring, and header control.
You do not need to enable Internet access for all pods in an ACK cluster. You need to only enable Internet access for the MSE cloud-native gateway to provide higher access control capabilities. If you enable Internet access for the MSE cloud-native gateway, you must enable Source Network Address Translation (SNAT) for the vSwitch to which the gateway is attached.
Deployment architecture
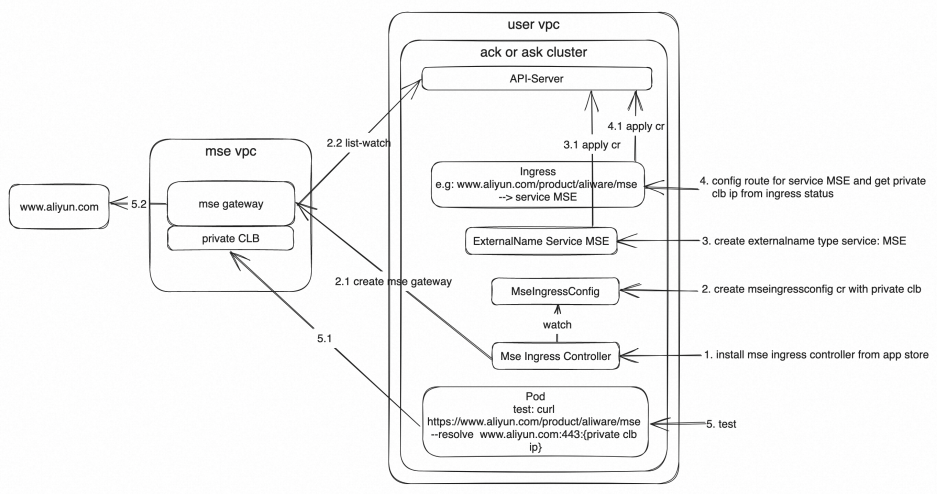
Procedure
Step 1: Install MSE Ingress Controller
Install MSE Ingress Controller in an existing ACK cluster or ACK Serverless cluster. You can also install MSE Ingress Controller when you create a cluster. For more information, see the "Install the MSE Ingress Controller component" section in Manage the MSE Ingress Controller component.
Step 2: Create an MseIngressConfig resource to create an MSE cloud-native gateway or associate the created MseIngressConfig resource with an existing MSE cloud-native gateway
MseIngressConfig is a CustomResourceDefinition (CRD) that is provided by MSE Ingress Controller. You can create an MseIngressConfig resource and use the created MseIngressConfig resource to create an MSE cloud-native gateway. You can also associate the created MseIngressConfig resource with an existing MSE cloud-native gateway. For more information, see the "Create a cloud-native gateway" section in Configure an MseIngressConfig.
You need to only create an internal-facing Classic Load Balancer (CLB) instance when you create a gateway. Sample configuration:
apiVersion: mse.alibabacloud.com/v1alpha1
kind: MseIngressConfig
metadata:
name: egress-gateway
spec:
name: egress-gateway
common:
instance:
spec: 2c4g
replicas: 3
network:
vSwitches:
- "vsw-xxxx" # The ID of the vSwitch that is associated with the MSE cloud-native gateway. You must configure the vSwitch ID when you create a gateway.
privateSLBSpec: slb.s2.smallIf you do not select Configure SNAT for VPC when you create an ACK cluster or ACK Serverless cluster, the created cluster cannot access the Internet. You must configure SNAT for the MSE cloud-native gateway to support Internet access.
To support Internet access, you must use SNAT entries of a network address translation (NAT) gateway. For more information about how to create a NAT gateway, see Use the SNAT feature of an Internet NAT gateway to access the Internet. Perform Step 3: Create an SNAT entry to create an SNAT entry. In this operation, select Specify vSwitch and add the vSwitch ID in the MseIngressConfig resource to the entry.
Step 3: Create a Kubernetes service of the ExternalName type and associate the service with an external service
Create a Kubernetes service of the ExternalName type and map the service name to the name of the external Domain Name System (DNS). For example, if you want to access the Alibaba Cloud MSE product page from the Kubernetes cluster, you can use the following configuration:
apiVersion: v1
kind: Service
metadata:
name: aliyun-svc-external
namespace: default
spec:
externalName: www.aliyun.com
ports:
- name: port1
port: 80
protocol: TCP
targetPort: 80
- name: port2
port: 443
protocol: TCP
targetPort: 443
type: ExternalNameStep 4: Configure a routing rule for the service of the ExternalName type
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: mse-ingress
namespace: default
spec:
ingressClassName: mse
rules:
- host: www.aliyun.com # The domain name.
http:
paths:
- backend:
service:
name: aliyun-svc-external # The name of the service of the ExternalName type.
port:
number: 80
path: /product/aliware/mse # The MSE access path.
pathType: PrefixAfter you save the preceding configurations as a file named mse-ingress.yaml, run the kubectl apply -f mse-ingress.yaml command to apply the configuration. Then, run the kubectl get ingress mse-ingress -o yaml command to view information about Ingress resources and obtain the CLB IP address of the MSE cloud-native gateway. Sample configuration:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
nginx.ingress.kubernetes.io/backend-protocol: HTTPS # The HTTPS protocol that is used for the service routing from the gateway to the backend Alibaba Cloud services.
name: mse-ingress
namespace: default
spec:
ingressClassName: mse
rules:
- host: www.aliyun.com
http:
paths:
- backend:
service:
name: aliyun-svc-external
port:
number: 443
path: /product/aliware/mse
pathType: Prefix
status:
loadBalancer:
ingress:
- ip: xx.xx.xx.xx # The CLB IP address of the MSE cloud-native gateway.Step 5: Test access to MSE by using a pod
curl http://www.aliyun.com/product/aliware/mse --resolve www.aliyun.com:80:xx.xx.xx.xxxx.xx.xx.xx indicates the CLB IP address that is obtained in Step 4.
References
For more information about how to use other advanced features of MSE cloud-native gateways based on Ingress resources, see Advanced usage of MSE Ingress.