Microservices Engine (MSE) provides the traffic protection feature to detect traffic exceptions and attacks and report the events to Simple Log Service (SLS). Simple Log Service allows you to collect, store, and analyze log data. You can also create indexes for a large amount of data and query the data in real time. If traffic protection events are reported to Simple Log Service, you can conveniently monitor and analyze the events. This helps protect your network security. This topic describes how to report traffic protection events of MSE Microservices Governance to Simple Log Service. Traffic protection events are collected in the sentinel-block.log file.
Prerequisites
Simple Log Service is activated. For more information, see "Step 1: Activate Simple Log Service" in Getting Started.
A Container Service for Kubernetes (ACK) managed cluster is created. For more information, see Create an ACK managed cluster.
The traffic protection feature is enabled for MSE Microservices Governance, and traffic protection rules are configured. For more information, see Overview.
Install Logtail
This section describes how to install the Logtail component. If Simple Log Service is enabled when you create the ACK cluster, skip this section. For more information, see Install Logtail when you create a cluster.
If you use an ACK dedicated cluster or an ACK managed cluster, you can follow the instructions in this section to install Logtail in your ACK cluster.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the one you want to manage and click its name. In the left-side navigation pane, choose .
On the Logs and Monitoring tab, find the logtail-ds resource card and click Install.
Collect data
This section describes how to configure the data source of Simple Log Service. Sentinel logs are collected, parsed, and reported to Simple Log Service. For more information, see the Configure the data source and parsing format step in this topic.
Log on to the Simple Log Service console.
On the page that appears, click the Quick Data Import card. In the Import Data dialog box, enter Kubernetes in the search box, and click the Kubernetes - File card.
In the Select Logstore step, configure the Project and Logstore parameters, and click Next.
You can create a project whose name is in the k8s-log-{your ACK cluster ID} format or select a project from the Project drop-down list. You can select a Logstore from the Logstore drop-down list or create one. For more information about how to create a Logstore, see the Create a logstore section in the "Manage a Logstore" topic.
In the Machine Group Configurations step, select the Kubernetes-group-${your ACK cluster ID} machine group, add the machine group in the Source Machine Group list to the Applied Server Groups list, and then click Next.
If you select another project, create a server group as prompted.
In the Logtail Configuration step, configure the data source and parsing format. Click Next.
Parameter
Description
Configuration Name
Enter a configuration name.
File Path
Enter a file path in the
/${user_home}/logs/csp/sentinel-block.logformat. Replace${user_home}with the system home directory. In most cases, the system home directory is root.For more information about the file path, see Important logs.
Log Sample
Enter the following content:
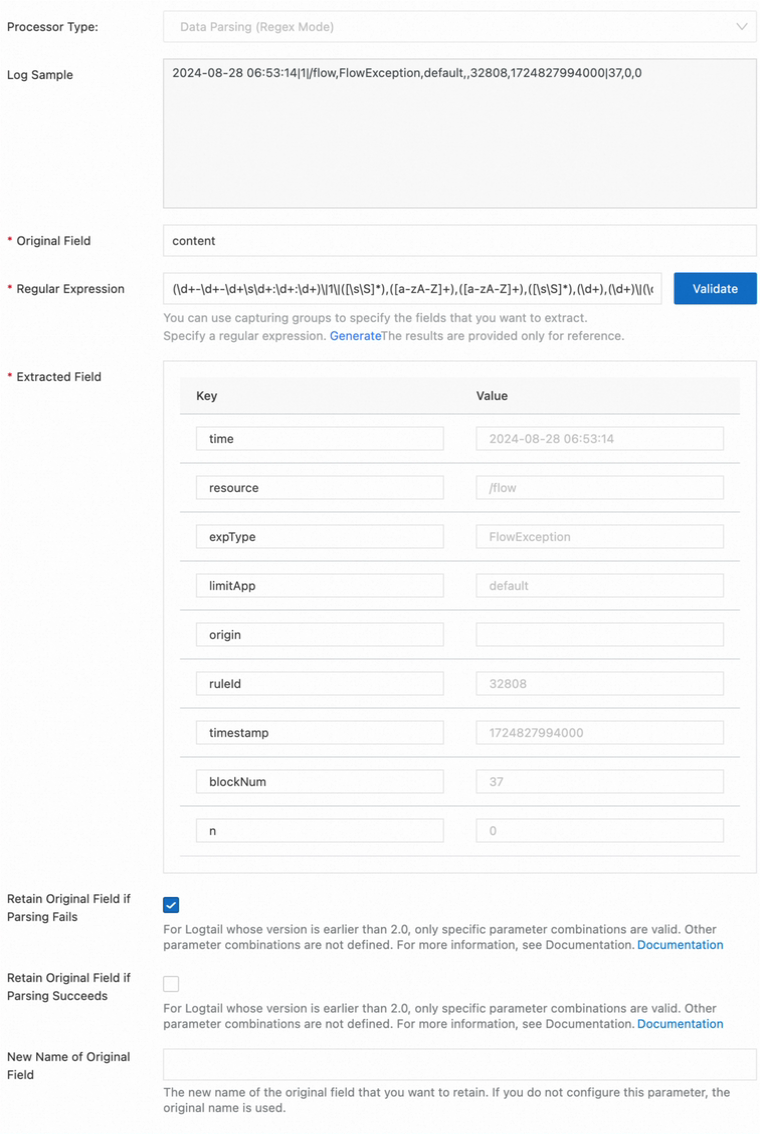
2024-08-28 06:53:14|1|/flow,FlowException,default,,32808,1724827994000|37,0,0Processing Method
Select Processors. The following figure shows the sample configurations for adding a processor of the Data Parsing (Regex Mode) type. You can configure key parameters by referring to the sample configurations, and configure other parameters based on your business requirements or keep the default parameter values.
Regular Expression
(\d+-\d+-\d+\s\d+:\d+:\d+)\|1\|([\s\S]*),([a-zA-Z]+),([a-zA-Z]+),([\s\S]*),(\d+),(\d+)\|(\d+),0,(\d+)
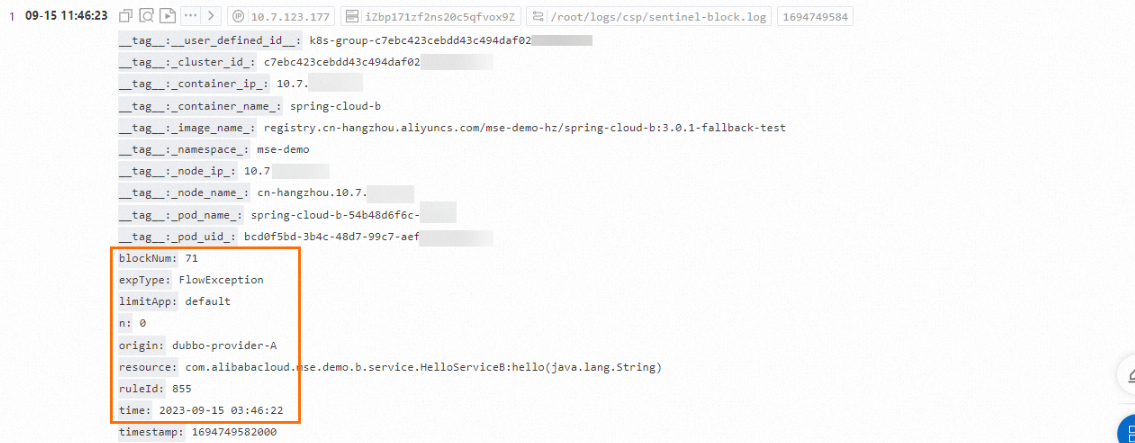
In the Query and Analysis Configurations step, wait until the Preview Data section on the right side of the page is automatically refreshed. Add and modify the index fields that are described in the following table, and click Next.
Field
Type
Alias
__tag__:_namespace_
text
namespace
__tag__:container_name_
text
appName
ruleId
long
Not required
resource
text
time
text
expType
text
blockNum
double
Click Query Log to return to the project page.
Verify metric reporting
Log on to the Simple Log Service console.
In your project, check that metrics are reported to your Logstore of Simple Log Service.
FAQ
What do I do if no logs are displayed in the Simple Log Service console?
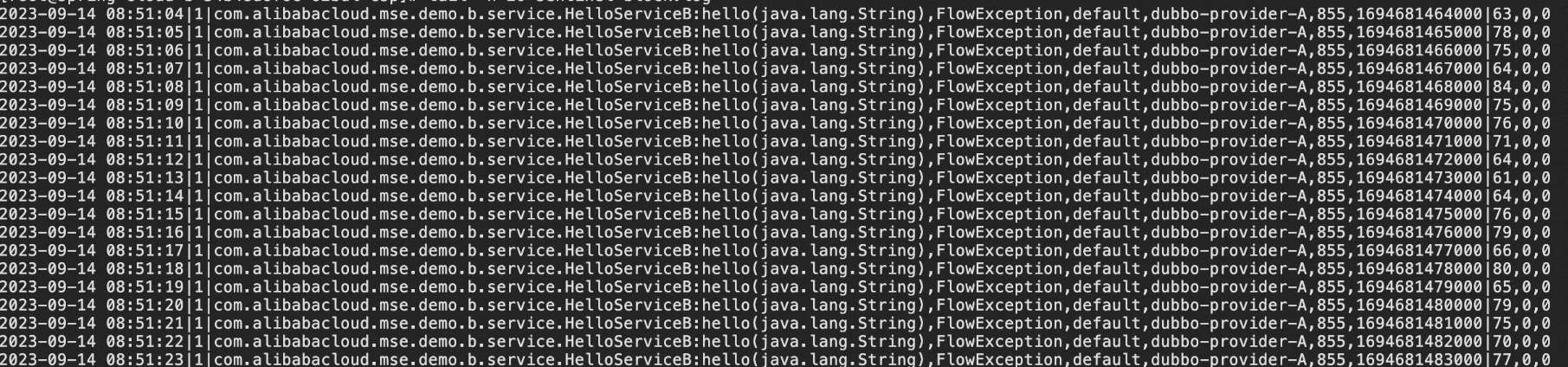
Log on to the ACK console and click the desired cluster. On the Overview page, click Open Cloud Shell. Run the following command:
cd ~/logs/csp/ # Replace the path with the actual log path.
tail -n 10 sentinel-block.logIf the following information is returned, throttling logs are generated. If no logs are generated, check whether the prerequisites are met. Check whether the traffic protection rules that you configure in the MSE console are valid and whether throttling occurs.
References
Configure a traffic protection alert based on Simple Log Service