Function Compute supports the multi-dimensional classification and management of functions using tags. This helps you quickly retrieve resources. You can also use tags to implement fine-grained access control. By granting different permissions to different Resource Access Management (RAM) users or user groups, you can isolate resources among RAM users and improve the efficiency of security management.
Scenarios
An enterprise has created multiple functions using an Alibaba Cloud account. The enterprise needs to grant permissions on different functions to different teams based on business groups. The enterprise wants each team to be able to view and manage only the functions for which they are granted permissions, and not be able to view or manage other functions.
For example:
Developer team: Can manage only functions related to the development environment.
O&M team: Can manage only functions related to the production environment.
Precautions
To follow the Principle of Least Privilege (PoLP), do not attach high-privilege policies, such as
AliyunFCFullAccessorAliyunFCReadOnlyAccess, to RAM users. Otherwise, you cannot use tags to manage permissions on functions by group as described in this topic.RAM users must use tag filtering to view and manage the functions for which they are granted permissions. Otherwise, RAM users cannot view any functions.
Ensure that the region that a RAM user selects when performing operations is the same as the region where the functions in the resource group are located.
RAM users in a RAM user group automatically inherit the permissions of the RAM user group.
Sub-resources and configurations of a function, such as aliases, triggers, function asynchronous configurations, function concurrent configurations, instances, VPC attachments, and asynchronous tasks, inherit the access control settings of the function. They can be managed only by RAM users who have the corresponding tags.
Flow overview
Use tags to identify functions for different teams
Plan two tags to identify the developer team and the operator team.
Group RAM users
Create two RAM users, one for the developer team and one for the operator team. Add the RAM users of each team to the corresponding RAM user group.
Grant permissions to RAM user groups based on tag-based authentication
Create two custom policies that use the Condition element for tag-based authentication to define the resource scope. Then, attach the different access policies to the different RAM user groups. RAM users in the user groups inherit the permissions of their respective user groups.
The following table describes the detailed plan:
Team | RAM user group | RAM access policy | Tag |
developer team | developer | FCPolicyForDevTeam |
|
operator team | operator | FCPolicyForOpsTeam |
|
Procedure
Create functions and attach tags.
Log on to the Function Compute console using your Alibaba Cloud account, create functions, and attach the
team:devtag to some functions and theteam:opstag to other functions. For more information about how to attach tags, see Configure tags.Create RAM users.
Log on to the RAM console using your Alibaba Cloud account and create two RAM users. For more information, see Create a RAM user.
Create RAM user groups and add RAM users. After being added, the RAM users inherit the permissions of their respective RAM user groups.
Log on to the RAM console using your Alibaba Cloud account to create two user groups named developer and operator, and add the two previously created RAM users to the developer and operator groups, respectively. For more information, see Create a RAM user group and Add a RAM user to a RAM user group.
Create custom policies.
Access policies are categorized into system policies and custom policies. You can select the appropriate type of access policy based on your needs. This topic provides an example of granting custom policies to user groups.
Log on to the RAM console using your Alibaba Cloud account, and then create a custom policy.
Assume that the custom policy created for the developer team is named FCPolicyForDevTeam. The following is a sample policy.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "fc:*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/team": [ "dev" ] } } }, { "Effect": "Allow", "Action": "fc:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/team": [ "dev" ] } } }, { "Effect": "Allow", "Action": [ "fc:ListTaggedResources", "tag:ListTagKeys", "fc:GetAccountSettings" ], "Resource": "*" }, { "Effect": "Deny", "Action": [ "fc:UntagResources", "fc:TagResources" ], "Resource": "*" } ] }Assume that the custom policy created for the operator team is named FCPolicyForOpsTeam. The following is a sample policy.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "fc:*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/team": [ "ops" ] } } }, { "Effect": "Allow", "Action": "fc:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/team": [ "ops" ] } } }, { "Effect": "Allow", "Action": [ "fc:ListTaggedResources", "tag:ListTagKeys", "fc:GetAccountSettings" ], "Resource": "*" }, { "Effect": "Deny", "Action": [ "fc:UntagResources", "fc:TagResources" ], "Resource": "*" } ] }
The following table describes the policies.
Policy
Description
{ "Effect": "Allow", "Action": "fc:*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/team": [ "dev" ] } } }Allows a RAM user to filter functions using the tag
team:dev, and requires the RAM user to specify the tagteam:devwhen creating a function.{ "Effect": "Allow", "Action": "fc:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/team": [ "dev" ] } } }Restricts a RAM user to performing management operations only on functions tagged with
team:dev.{ "Effect": "Allow", "Action": [ "fc:ListTaggedResources", "tag:ListTagKeys", "fc:GetAccountSettings" ], "Resource": "*" },Allows viewing the list of all tags for Function Compute functions and retrieving account information.
{ "Effect": "Deny", "Action": [ "fc:UntagResources", "fc:TagResources" ], "Resource": "*" },Disallows detaching and attaching tags.
This prevents RAM users from breaking permission fencing by modifying tags.
{ "Effect": "Allow", "Action": [ "log:Get*", "log:List*", "log:Query*", "log:CreateProject", "log:CreateLogStore", "log:CreateIndex" ], "Resource": "*" },Allows Function Compute to create and read logs.
{ "Effect": "Allow", "Action": [ "fc:GetLayerVersionByArn", "fc:ListLayers", "fc:PutLayerACL", "fc:ListLayerVersions", "fc:CreateLayerVersion", "fc:DeleteLayerVersion", "fc:GetLayerVersion" ], "Resource": "*" },Allows using layer-related features.
{ "Effect": "Allow", "Action": [ "fc:ListCustomDomains", "fc:GetCustomDomain", "fc:DeleteCustomDomain", "fc:UpdateCustomDomain", "fc:CreateCustomDomain" ], "Resource": "*" },Allows using custom domain name-related features.
{ "Effect": "Allow", "Action": [ "ram:ListRoles" ], "Resource": "*" },Allows querying the list of roles when you configure a function role.
NoteTo configure and use products such as OSS, NAS, and VPC in FC, you must also grant the required permissions for these products. For more information, see Access Policies and Examples.
Grant permissions to the RAM user groups.
Attach the custom policies FCPolicyForDevTeam and FCPolicyForOpsTeam to the developer and operator user groups, respectively.
Attach the system policies AliyunRAMFullAccess and AliyunECSFullAccess to the developer and operator user groups. After the permissions are granted, RAM users in these user groups can create functions with the specified tags, create RAM users and user groups, and create and attach access policies.
For more information, see Grant permissions to a RAM user group.
The following figure shows the recommended policies for the developer user group.
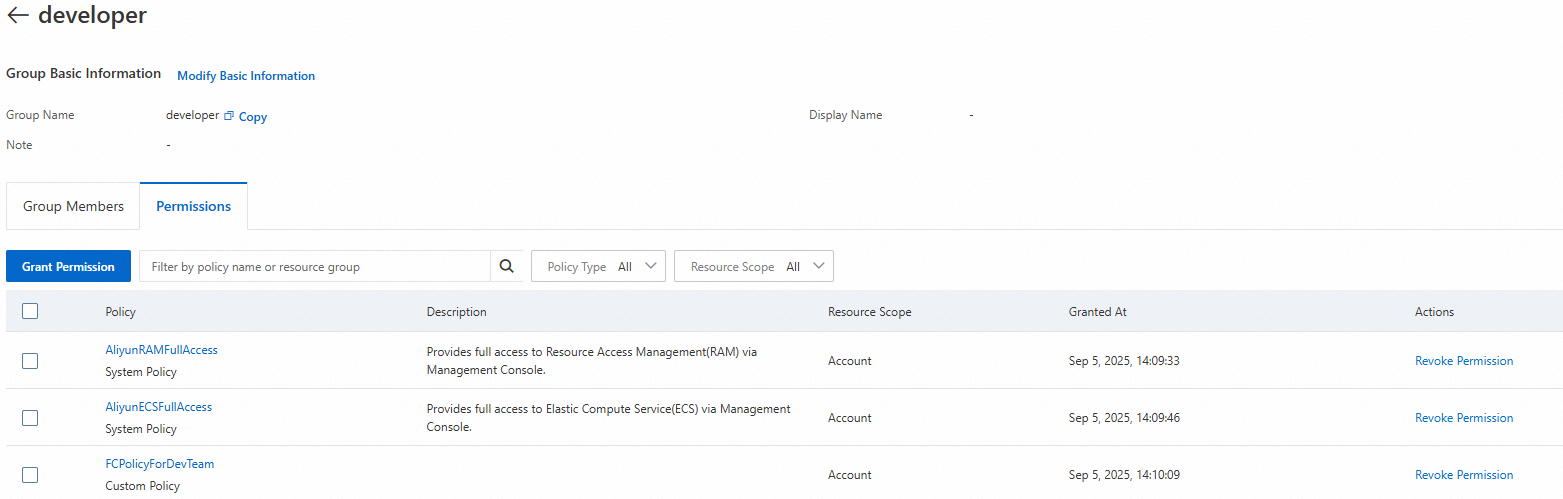
Verify the results
Log on to the Function Compute console as each of the two RAM users. In the navigation pane on the left, choose .
For more information, see Log on to the Alibaba Cloud Management Console as a RAM user.
In the top menu bar, select a region, and then on the Functions page, click Tag Filtering and filter by the corresponding Tag Key and Tag Value to query and manage the authorized functions.
A RAM user can view and manage functions that have a specific tag only if the user selects a tag that is included in the policies granted to the user group to which the user belongs. Otherwise, the RAM user cannot view any functions.
For example, a RAM user in the developer RAM user group can filter authorized functions using the tag
team:dev.