Alibaba Cloud recently discovered a remote code execution (RCE) vulnerability in Apache Log4j2 and reported the vulnerability to Apache. This topic describes the impacts of the vulnerability and provides security suggestions for customers and cloud services.
Impacts
Fully managed Flink deployments are isolated between users from each other because the fully managed Flink service of each user runs in an isolated environment. In most cases, this vulnerability cannot be exploited by external attackers. Before you run a fully managed Flink deployment, you must check the whitelist for accessing external resources, especially the connections between your deployment and external Java Naming and Directory Interface (JNDI) resources, such as Lightweight Directory Access Protocol (LDAP) and remote method invocation (RMI) resources. If your fully managed Flink deployment has permissions to access the external JNDI resources, attackers may exploit this vulnerability to access these resources. This may pose system security risks.
Security suggestions
-
Temporary solution for customers
-
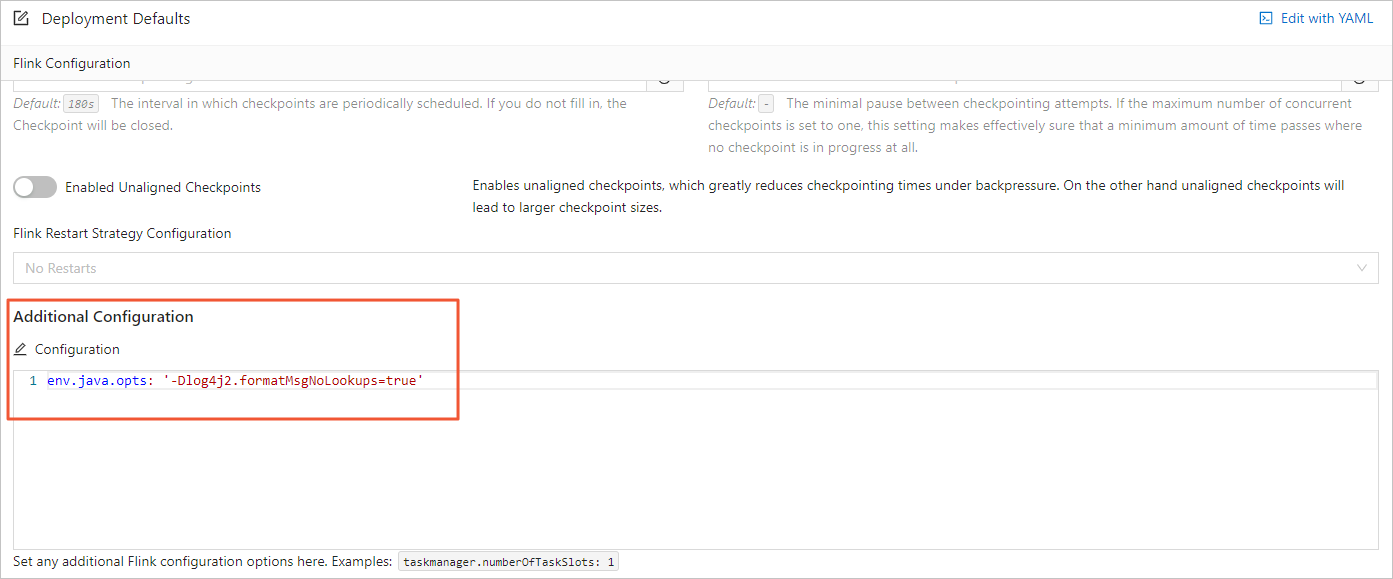
In the left-side navigation pane of the console of fully managed Flink, click . On the Deployment Defaults tab of the Configurations page, add the following Java Virtual Machine (JVM) configuration to the Other Configuration field.
env.java.opts: '-Dlog4j2.formatMsgNoLookups=true'This way, the lookup feature of Log4j 2 is disabled, and the security risks that are caused by this feature are prevented. The following figure shows the configuration.
 Note
NoteAfter you add the configuration to the Other Configuration field on the Deployment Defaults tab for a deployment that is not run, the configuration takes effect for all the deployments that you create later. For the deployment that is running, you can add the
env.java.opts: '-Dlog4j2.formatMsgNoLookups=true'configuration to the Other Configuration field in the Parameters section of the Configuration tab. For more information, see How do I configure custom running parameters for a job? -
Check the log configuration and modify the configuration based on your business requirements.
-
Find PatternLayout in the log configuration and replace the context lookup mode such as
${ctx:loginId}or$${ctx:loginId}with the Thread Context Map mode, such as%X, %mdc, or %MDC. -
Remove the context lookup mode such as
${ctx:loginId}or$${ctx:loginId}from the log configuration. In context lookup mode, malicious data can be injected and parsed by Log4j.
-
-
Restart the deployment to allow the modification to take effect.
-
-
Solution for the fully managed Flink service
-
Ververica Runtime (VVR) 1.X: Log4j 2 is not used in this version. Therefore, this version is not affected by the vulnerability. However, technical support for VVR 1.X is no longer provided. We recommend that you update VVR 1.X to the latest version to enjoy more powerful features and service protection.
-
VVR 2.X, VVR 3.X, and VVR 4.X: A version was released on December 31, 2021 to fix this vulnerability. Pay attention to the release announcement and upgrade your deployment to the latest version at the earliest opportunity to prevent security risks.
NoteMajor versions may not be compatible with each other. To ensure version compatibility before and after the update, update the version of your deployment to the latest minor version in the current major version of the deployment.
-
References
The preceding references are provided at third-party websites. When you access the websites, the websites may fail to be accessed or access to the websites may be delayed.