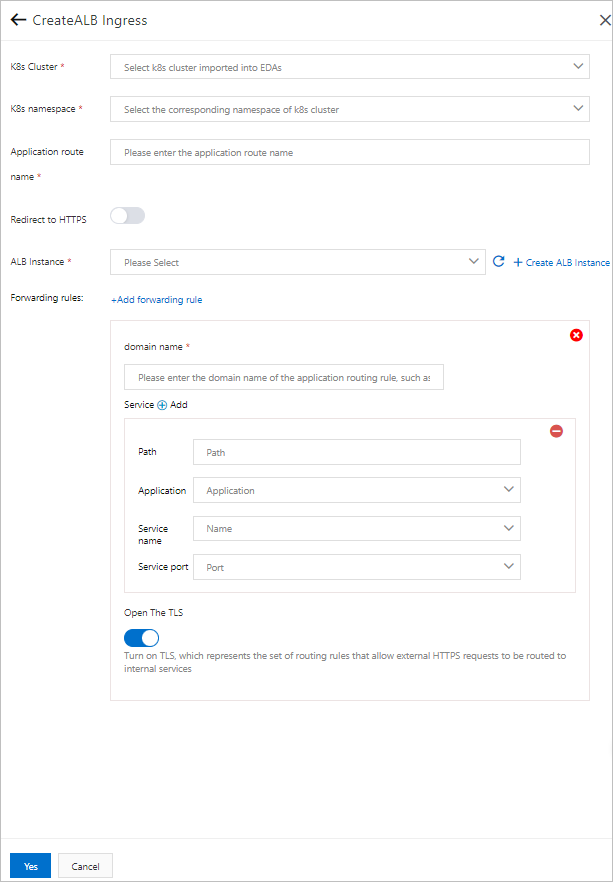
Enterprise Distributed Application Service (EDAS) allows you to create an application load balancer (ALB) Ingress for an application. An ALB Ingress can help manage ingress traffic in a more efficient manner based on an ALB instance. An ALB Ingress is compatible with an NGINX Ingress, and supports complex routing and automatic certificate discovery.
Prerequisites
- Add a Service
- The ALB Ingress controller is installed.
- You can install the ALB Ingress controller when you create a cluster by setting the Ingress parameter to ALB Ingress on the Component Configurations wizard page.
- You can also install the ALB Ingress controller for an existing cluster in which no ALB Ingress controller is installed. For more information, see Manage system components.
Background information
The ALB Ingress controller retrieves the changes to Ingresses from the API server
and dynamically generates AlbConfig objects when Ingress changes are detected. Then,
the ALB Ingress controller performs the following operations in sequence: create ALB
instances, configure listeners, create Ingress rules, and configure backend server
groups. The Service, Ingress, and AlbConfig objects interact with each other in the
following ways:
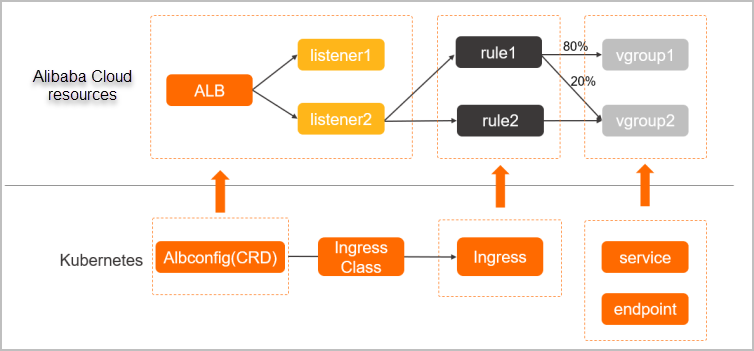
- A Service is an abstraction of an application that is deployed in a group of replicated pods.
- An Ingress contains reverse proxy rules and specifies the Service to which HTTP or HTTPS requests are routed. For example, an Ingress routes requests to different Services based on the hostnames and URLs in the requests.
- An AlbConfig object is a custom resource definition (CRD) object that the ALB Ingress controller uses to configure ALB instances and listeners. An AlbConfig object corresponds to one ALB instance.

Limits
- ALB instances that serve Ingresses are fully managed in EDAS. To avoid service interruptions caused by Ingress errors, we recommend that you do not modify these ALB instances in the ALB console.
- You cannot modify the Ingress resources created by EDAS. These resources have the
following labels:
edas-domain: edas-adminandedas-domain. You cannot modify or delete IngressClass and AlbConfig objects associated with Ingresses. These objects are named in theedas-{alb_id}format. - The cluster that uses a Flannel network plug-in supports only NodePort and LoadBalancer Services.
- If you need to configure HTTPS-based routing for an ALB Ingress, you must turn on Open The TLS for all routing rules of the Ingress.
- An ALB Ingress supports automatic certificate discovery. After you turn on Open The TLS for a routing rule of the ALB Ingress, you do not need to configure a Secret. However, you must purchase a unique certificate for the corresponding domain name in SSL Certificates Service. The certificate can be a wildcard certificate or single-domain certificate.
- To create an ALB Ingress for an application, you must bind an existing standard ALB instance to the Ingress. After you create the Ingress, the ALB instance bound to the Ingress cannot be reused by other clusters.