Enterprise Distributed Application Service (EDAS) allows you to create a Hypertext Preprocessor (PHP) application from source code and deploy the application in a Container Service for Kubernetes (ACK) cluster or a ACK Serverless cluster. EDAS also provides diverse features for managing applications, such as application scaling, monitoring and alerting, load balancing, and throttling and degradation. The procedure for deploying a PHP application in an ACK cluster is similar to that for deploying a PHP application in a ACK Serverless cluster. This topic describes how to build a PHP application from source code and deploy the application in an ACK cluster.
Prerequisites
EDAS and ACK are activated for your Alibaba Cloud account. For more information, see the following topics:
ACK default roles are granted to your account. For more information, see ACK roles.
Step 1: Create an ACK cluster
Log on to the ACK console and create an ACK cluster. For more information, see Create a managed Kubernetes cluster.
If you want to create an ACK Serverless cluster, set the VPC parameter to Create VPC and set the Service Discovery parameter to PrivateZone. This allows the ACK Serverless cluster to use Alibaba Cloud Service Mesh (ASM) after the cluster is imported to EDAS. If you set the VPC parameter to Select Existing VPC, check whether the cluster contains virtual private cloud (VPC) and vSwitch resources after you create the cluster. For more information, see Create an ACK Serverless cluster.
Step 2: Import an ACK cluster to the EDAS console
By default, the ack-ahas-sentinel-pilot, ack-arms-pilot, and ack-arms-prometheus components are installed when you import an ACK cluster to EDAS in the EDAS console. The ack-ahas-sentinel-pilot component is an application protection component for throttling and degradation. The ack-arms-pilot component is an Application Real-Time Monitoring Service (ARMS) component. The ack-arms-prometheus component is a Prometheus monitoring component.
Log on to the EDAS console. In the left-side navigation pane, choose .
In the top navigation bar, select the region in which your ACK cluster resides, and click Synchronize Container Service Kubernetes Cluster.
Find the ACK cluster that is synchronized to EDAS and click Import in the Actions column.
In the Precheck for Import dialog box, click Continue.
In the Import Kubernetes Cluster dialog box, select the microservice namespace to which you want to import the ACK cluster from the Microservice Namespace drop-down list, turn on or off Service Mesh based on your business requirements, and then click Import.
If the value in the Cluster Status column is Running and the value in the Import Status column is Imported for the ACK cluster, the cluster is imported to EDAS.
Step 3: Deploy your PHP application to the ACK cluster
Log on to the EDAS console.
In the left-side navigation pane, choose . In the top navigation bar, select a region. In the upper part of the Applications page, select a microservices namespace from the Microservices Namespace drop-down list. Then, click Create Application in the upper-left corner of the Applications page.
In the Basic Information step, set the parameters in the Cluster Type and Application Runtime Environment sections and click Next.
Section
Description
Cluster Type
The type of the cluster in which you want to deploy the application. In this example, select Kubernetes Clusters.
Application Runtime Environment
The runtime environment of the application. In this example, select PHP. An image built by EDAS provides a runtime environment for PHP 7.3 and Apache 2.4. Specific frequently used PHP plug-ins are installed in the runtime environment.
In the Configurations step, configure the environment information, basic information, source code, and image settings for the application, and click Next.
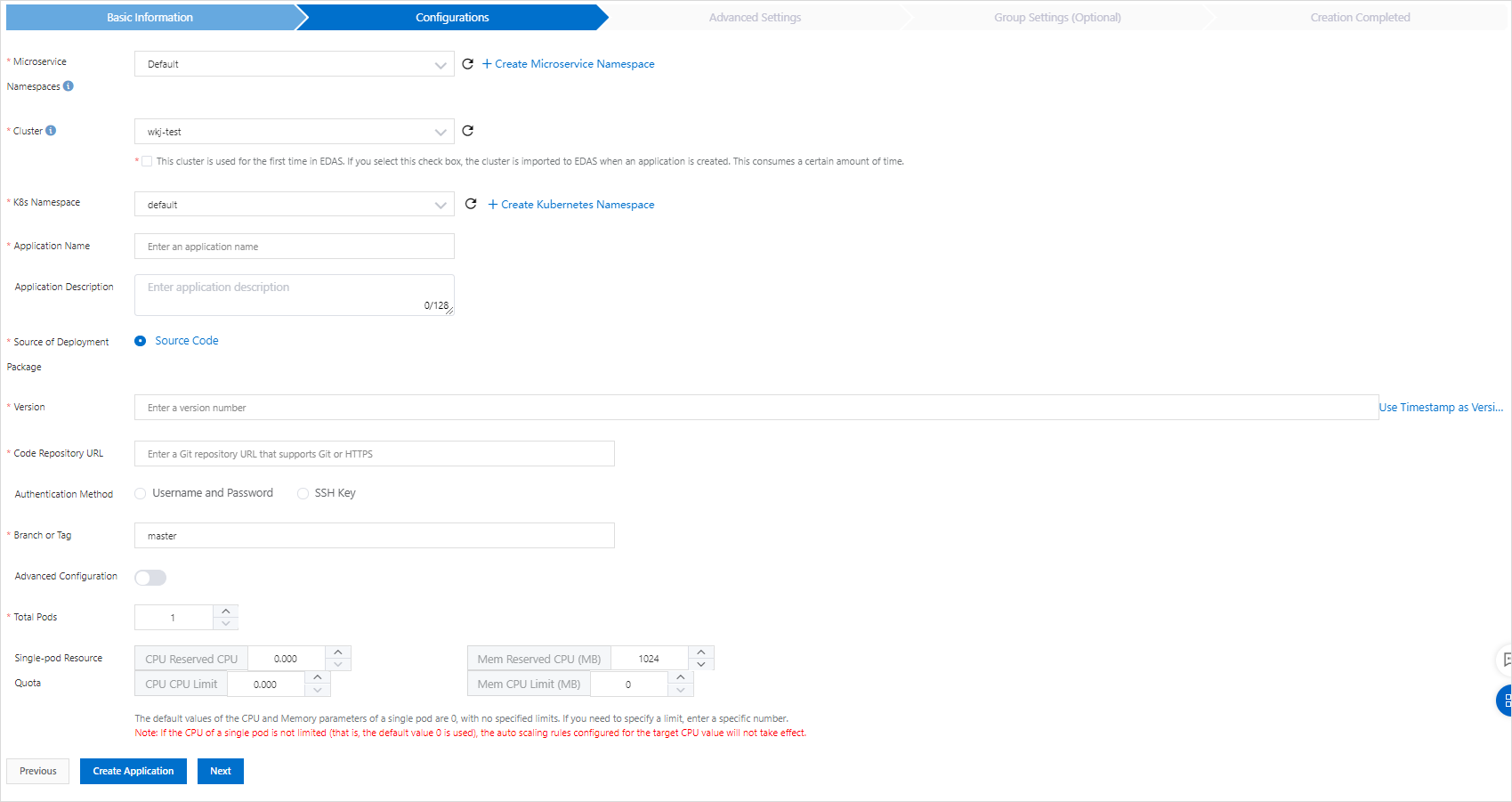
Parameter
Description
Microservice Namespace
The microservices namespace of the ACK cluster. If you have not created a microservices namespace or do not select a microservices namespace, this parameter is set to Default.
If you have not created a microservice namespace or you want to create another microservice namespace, click Create Microservice Namespace to create a microservice namespace. For more information, see the "Create a namespace" section of the Manage microservice namespaces topic.
Cluster
The cluster in which you want to deploy the application. Select the imported ACK cluster from the Cluster drop-down list.
If the selected Kubernetes cluster is not imported to EDAS, select This cluster is used for the first time in EDAS. If you select this check box, the cluster is imported to EDAS when an application is created. This consumes a certain amount of time. Then, check whether Alibaba Cloud Service Mesh is activated.
NoteYou can select a cluster that is not in the microservices namespace in which you want to deploy the application.
K8s Namespace
The Kubernetes namespace of the cluster. Internal system objects are allocated to different Kubernetes namespaces to form logically isolated projects, groups, or user groups. This way, these projects, groups, or user groups can be separately managed but still share the resources of the entire cluster. Valid values:
default: the default Kubernetes namespace. If no Kubernetes namespace is specified for an object, the default Kubernetes namespace is used.
kube-system: the Kubernetes namespace for the objects that are created by the system.
kube-public: the Kubernetes namespace that is automatically created and can be read by all users, including users who are not authenticated.
In this example, select default.
If you want to create a custom Kubernetes namespace, click Create Kubernetes Namespace. In the dialog box that appears, enter a name for the Kubernetes namespace in the K8s Namespace field. The name can contain digits, lowercase letters, and hyphens (-), and can be 1 to 63 characters in length. It must start and end with a letter or a digit.
Application Name
The name of the application. The name must start with a letter and can contain digits, letters, and hyphens (-). The application name must be 1 to 36 characters in length.
Application Description
The description of the application. The description must be 1 to 128 characters in length.
Source of Deployment Package
The way in which you want to specify the deployment package. This parameter is fixed to Source Code.
Version
The version of the application. You can specify a custom version number or click Use Timestamp as Version Number to generate a version number.
Code Repository URL
The URL of the code repository that you want to use to deploy the PHP application. Specify a URL that supports the HTTPS or Git protocol.
Authentication Method
The type of information used for authentication. If your code repository is a private repository, you must set this parameter. Valid values:
Username and Password: Select a secret that you have created. If no secret is available, perform the following steps to create a secret:
On the right side of the Username and Password field, click Create Secret.
In the Create Secret dialog box, set the Secret Name, Username, and Password parameters.
In the dialog box, click Create.
SSH Key: Specify the SSH key provided by EDAS in the code repository. For more information, see Configure an SSH public key when you deploy an application by using source code.
Branch or Tag
The branch or tag of the code repository.
Advanced Configuration
Optional. The advanced configurations of the application. You can turn on Advanced Configuration and set the following parameters:
Clone Submodule: Use a Git repository as a subdirectory of another Git repository. This feature allows you to clone a repository to your project and separately submit your application code.
Working Directory: Specify a directory in which the files you are processing are to be stored. All the operations related to Git are performed in this directory.
Output Path: Specify a directory in which Git output files are to be stored.
Total Pods
The number of pods on which you want to deploy an application.
Single-pod resource quota
The amount of CPU and memory resources that you want to reserve for a pod. To set a limit, enter a numeric value. The default value 0 indicates that no limit is set on the CPU and memory quotas.
Optional: Configure the advanced settings for the application. Then, click Create Application.
Configure environment variables.
When you create the application, pass the environment variables that you configure to the container to be generated. This way, you do not need to repeatedly add frequently used environment variables.
If you are using a MySQL image, you can configure the following environment variables:
MYSQL_ROOT_PASSWORD: required. Allows you to set a MySQL root password.
MYSQL_USER and MYSQL_PASSWORD: optional. Allows you to create an account in addition to the root account and set a password.
MYSQL_DATABASE: optional. Allows you to specify the database that you want to create when the container is generated.
If you are using another type of image, configure the environment variables as needed.
Configure persistent storage.
In ACK clusters, the physical storage of a native volume object is not persistent. This means that the volume object is a temporary storage object and has the same lifecycle as a Kubernetes pod. You can use File Storage NAS (NAS) to persistently store instance data. This way, if an instance is updated or migrated, the instance data is retained.
NoteBefore you configure persistent storage, make sure that you have activated NAS for the Alibaba Cloud account that you use to access EDAS. To use NAS, make sure that the Alibaba Cloud account has sufficient balance or the billing method is pay-as-you-go.
Parameter
Description
PVC Mount
We recommend that you configure persistent storage by specifying PVC Mount. This method allows you to use Alibaba Cloud Elastic Block Storage (EBS), file storage systems, Object Storage Service (OSS), and local disks for storage when you create an application. The file storage systems include File Storage NAS (NAS) and Cloud Paralleled File System (CPFS). Before you specify PVC Mount, you need to create a persistent volume (PV) by referring to the corresponding steps in the topic of the storage service that you want to use. Then, you can mount the PVC on this page.
For more information about how to create a PVC, see NAS volume overview, OSS volume overview, and the overview of local storage volumes Overview.
NoteIf you have configured PVC Mount by using YAML files, the PVCs are not displayed in the Select PVC drop-down list. However, the PVC mount configurations are retained during application deployment. We recommend that you configure PVC Mount when you deploy applications in EDAS.
Select PVC
Select a PVC from the drop-down list. If no PVC is available, create a PVC. For more information, see Create a PVC.
Mount Configuration
Set the Mount Directory and Mount Mode parameters.
Configure application lifecycle management.
Parameter
Description
PostStart
A container hook. The hook is immediately triggered after a container is created. The hook does not pass parameters to the corresponding hook handler. If the corresponding hook handler fails to be executed, the container is stopped and the restart policy of the container is used to determine whether to restart the container. For more information, see Container Lifecycle Hooks.
PreStop
A container hook. The hook is triggered before a container is deleted. The corresponding hook handler must be completely executed before the request to delete the container is sent to the Docker daemon. The Docker daemon sends a SIGTERM signal to itself to delete the container, regardless of the execution result of the corresponding hook handler. For more information, see Container Lifecycle Hooks.
Liveness
A probe that monitors your container status. The probe checks whether your applications are healthy. If an application is unhealthy, its corresponding container is deleted and re-created. For more information, see Pod Lifecycle.
Readiness
A probe that monitors your container status. The probe checks whether your applications have been started and are running as expected. If an application is not running as expected, the container status is updated. For more information, see Pod Lifecycle.
After the settings are configured, click Create Application. In the Creation Completed step, click Create Application.
The application requires several minutes to be deployed. During the process, you can view the deployment progress of the application on the Change List page. After the application is deployed, the Application Overview page appears. On this page, you can check the status of the pod. If the pod is in the Running state, the application is released. You can click the state of the pod to view the advanced settings of the application instance, such as Deployment, Pod, and Startup Command.
FAQ
How do I view the error log that tracks image-based application deployment?
If you fail to use an image to deploy an application, you can view the error log on the Change List page. For more information, see View application changes.
What to do next
After you deploy the application, add an Internet-facing Server Load Balancer (SLB) instance to allow access to the application over the Internet. You can also add an internal-facing SLB instance so that all the nodes in the same VPC can access the application by using this internal-facing SLB instance. For more information, see Bind CLB instances or Reuse a CLB instance.