If you want to use a custom domain name to expose a Knative Service, we recommend that you configure a certificate for the domain name to secure data transmission. Knative allows you to use a DomainMapping to configure a certificate to access Services over HTTPS.
Prerequisites
Knative is deployed in the ACS cluster. For more information, see Deploy Knative.
Step 1: Create a Knative Service
Log on to the ACS console. In the left-side navigation pane, click Clusters.
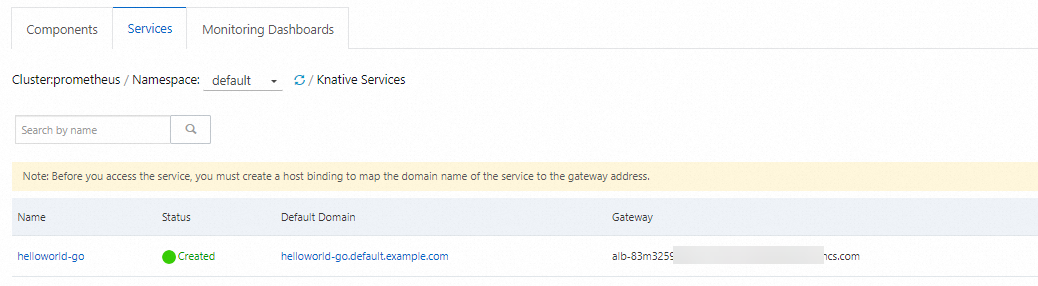
On the Clusters page, find the cluster that you want to manage and click its ID. In the left-side navigation pane of the cluster details page, choose .
On the Services tab of the Knative page, set Namespace to default and click Create from Template. Create a Knative Service named helloworld-go from the Sample Template provided in the console and click Create. Then, a Service named helloworld-go is created.
Step 2: Create a certificate that is managed as a Secret
In Knative, Secrets are used to store and manage sensitive information, such as keys, passwords, and certificates. In this example, OpenSSL is used to create a self-signed certificate. The certificate and private key files are encoded by using Base64 and stored in a Secret in the cluster. The following example shows how to create a self-signed certificate that is managed as a Secret.
Run the following OpenSSL commands to create a self-signed certificate:
openssl genrsa -out knativetop-key.pem 4096 openssl req -subj "/CN=helloworld.knative.top" -sha256 -new -key knativetop-key.pem -out knativetop.csr echo subjectAltName = DNS:helloworld.knative.top > extfile.cnf openssl x509 -req -days 3650 -sha256 -in knativetop.csr -signkey knativetop-key.pem -out knativetop-cert.pem -extfile extfile.cnfExpected output:
Signature ok subject=CN = helloworld.knative.top Getting Private keyUse Base64 to encode the
knativetop-key.pemandknativetop-cert.pemfiles in Step 1.Run the following command to use Base64 to encode the
knativetop-key.pemfile:cat knativetop-key.pem | base64Expected output:
a25hdGl2ZXRvcC1r******Run the following command to use Base64 to encode the
knativetop-cert.pemfile:cat knativetop-cert.pem | base64Expected output:
a25hdGl2ZXRvcC1jZ******==
Run the following command to create a Secret:
The Secret can be used in the TLS configuration of the Knative Service to securely access the domain name
helloworld.knative.top.kubectl create secret tls secret-tls --key knativetop-key.pem --cert knativetop-cert.pemExpected output:
secret/secret-tls created
Step 3: Create a DomainMapping
DomainMappings are resource objects in Knative. A DomainMapping maps a domain name to one or more Knative Services. You can create a DomainMapping to map a custom domain name to a Knative Service so that your applications can access the Service through the domain name.
Run the following command to create a file named
helloworld.knative.top.yaml:vim helloworld.knative.top.yamlOpen the vi editor, add the following YAML content, save the change, and then exit:
apiVersion: serving.knative.dev/v1beta1 kind: DomainMapping metadata: name: helloworld.knative.top namespace: default spec: ref: name: helloworld-go kind: Service apiVersion: serving.knative.dev/v1 # tls block specifies the secret to be used tls: secretName: secret-tlsRun the following command to deploy the resources defined in the
helloworld.knative.top.yamlfile to the ACK cluster:kubectl apply -f helloworld.knative.top.yamlExpected output:
domainmapping.serving.knative.dev/helloworld.knative.top createdRun the following command to verify the DomainMapping:
kubectl get domainmapping helloworld.knative.topExpected output:
NAME URL READY REASON helloworld.knative.top https://helloworld.knative.top True
Step 4: Access the Knative Service over HTTPS
Run the following command to access the Knative Service over HTTPS:
ALB
Add a listener on port 443 in the AlbConfig. The following code provides an example of adding a listener on port 443 for knative-internet:
apiVersion: alibabacloud.com/v1
kind: AlbConfig
metadata:
name: knative-internet
spec:
config:
...
listeners:
- port: 443
protocol: HTTPS # Valid values for protocol: HTTP, HTTPS, and QUIC.
...Run the following command to perform an access test:
# alb-ppcate4ox6******.cn-beijing.alb.aliyuncs.com is the address of the ALB Ingress.
curl -H "host: helloworld.knative.top" https://alb-ppcate4ox6******.cn-beijing.alb.aliyuncs.com -kMSE
# 8.141.XX.XX is the address of the MSE Ingress.
curl -H "host: helloworld-go.default.example.com" https://8.141.XX.XX -kASM
# 8.141.XX.XX is the address of the ASM Ingress.
curl -H "host: helloworld-go.default.example.com" http://8.141.XX.XX -kExpected output:
Hello Knative!References
You can configure probes to monitor the health status and availability of Knative Services. For more information, see Configure port probing in Knative.