Overview
Summary
Maintaining a well-functioning network architecture in the cloud is becoming a challenge for customers when they migrate to, use, or manage cloud resources. The first step for enterprises to migrate to the cloud is to connect their on-premises networks to Alibaba Cloud by using cloud services and technologies.
This topic describes how to use IPsec-VPN connections to connect branch networks to Alibaba Cloud. This topic provides a set of methods and design principles that are summarized based on the best practices of Alibaba Cloud architecture design, including stability, security, performance, scalability, observability, and self-service capabilities. Alibaba Cloud Well-Architected Framework helps you connect branch networks to Alibaba Cloud by using IPsec-VPN connections.
Terms
VPN Gateway: VPN Gateway provides secure and reliable network connections that connect enterprise data centers, office networks, and Internet clients to Alibaba Cloud through encrypted and private tunnels.
IPsec-VPN: IPsec-VPN connections are mainly used to connect branch networks of enterprises to the cloud. IPsec-VPN connections are a type of classic VPN connection, which support secure IP communication on the network layer. The IPsec protocol can encrypt and authenticate every data packet to ensure data security and integrity. IPsec-VPN tunnels are typically used to establish site-to-site connections and remote access. To establish IPsec-VPN connections, you need to configure settings on your device or gateway.

SSL-VPN: SSL-VPN connections are mainly used to connect mobile terminals to the cloud. SSL-VPN uses the SSL or TLS protocol to ensure connection security at the session layer. Unlike IPsec-VPN, SSL-VPN does not require users to install software. Users can access cloud resources from web browsers because SSL is supported by most modern browsers. SSL-VPN is more flexible, easier to configure, and especially suitable for remote access scenarios where users are allowed to access specific applications or services. Alibaba Cloud supports clients that use the following operating systems: Windows, Linux, macOS, and Android.

Cloud Enterprise Network (CEN): CEN is a high availability network that runs on the global private network of Alibaba Cloud. CEN uses transit routers to establish cross-region connections between VPCs. This enables VPCs to communicate with data centers and establish flexible, reliable, and enterprise-class networks in the cloud.
The method used to establish an IPsec-VPN connection varies based on the resource associated with the IPsec-VPN connection. For more information, see the following figures.
Associate with a VPN gateway: VPN gateways can be directly associated with virtual private clouds (VPCs) to connect the VPCs to other networks.

Associate with a transit router: IPsec connected can be directly attached to transit routers, which connect the VPCs to other networks.

Comparison between VPN gateways and transit routers
Item | VPN gateway | Transit router |
Associated resources | To create an IPsec-VPN connection, you must purchase a VPN gateway and associate the VPN gateway with a VPC. Your data center or branch network can communicate with the associated VPC or other networks through the associated VPC. | To create an IPsec-VPN connection, you do not need to purchase a VPN gateway or associate the VPN gateway with a VPC. You must create a CEN instance and create a transit router on the CEN instance. Your data center or branch network can communicate with all VPCs connected to the transit router or with other networks through the transit router. |
[Scalability] Billing methods | Subscription You can subscribe to resources on a monthly basis. You must pay for resources before you can use the resources. This billing method is ideal for customers on a tight budget | Pay-as-you-go You are charged for the amount of consumed resources. You can use resources before you pay for them. This billing method is ideal for customers whose businesses experience large traffic fluctuations. |
[Security] Supported encryption algorithms |
|
|
[Stability] Supported IPsec-VPN tunnel modes |
|
You can use multiple IPsec connections to implement high availability. |
[Scalability] Maximum bandwidth per IPsec-VPN connection | Maximum: 1,000 Mbit/s | Maximum (default): 1,000 Mbit/s You can use multiple IPsec connections to increase the bandwidth capacity. This feature is ideal for customers who require high bandwidth. |
[Performance] Maximum number of packets that can be transmitted through each IPsec-VPN connection per second | 120,000 | 120,000 |
Supported network types |
Encrypted tunnels are established over the Internet.
Encrypted tunnels are established by using private connections over Express Connect circuits. |
Encrypted tunnels are established over the Internet.
Encrypted tunnels are established by using private connections over Express Connect circuits. |
Supported access modes |
|
|
[Stability] high availability methods | Active/standby connections | Equal-cost multipath (ECMP) routing |
Design principles
VPN Gateway is a key service if you want to connect branch networks to the cloud over IPsec-VPN connections. VPN Gateway uses encrypted tunnels to establish secure and reliable private connections between enterprise data centers or branch networks and Alibaba Cloud VPCs. IPsec-VPN is a network connection technology based on routes. IPsec-VPN provides flexible traffic routing methods and allows you to configure and maintain VPN policies in an efficient manner. You can use IPsec-VPN to establish connections between VPCs and data centers, branch networks, and clients.

Stability: IPsec-VPN connections connect data centers to Alibaba Cloud. The stability of IPsec-VPN connections determines the stability of the hybrid-cloud network. Therefore, you must fully assess the stability design.
Security: IPsec-VPN connections establish communication between data centers and Alibaba Cloud. Connection encryption and security are highly important. Some industries may have special encryption requirements, such as SM certificates. When you design IPsec-VPN connections, you must fully assess the security and encryption design.
Scalability: IPsec-VPN connections are tunnels between data centers and Alibaba Cloud. Many enterprises are challenged by low bandwidth utilization and resource waste issues. You must allocate sufficient bandwidth resources for peak hours while reducing resource waste for off-peak hours, such as using the pay-as-you-go billing method for cost optimization. You can also scale up the bandwidth capacity close to leased lines.
Key design
Stability
Device high availability: IPsec-VPN adopts the hot-standby architecture to implement failover within a few seconds, enable session persistence, and ensure zero service downtime.
Connection high availability: By default, all VPN gateways support the dual-tunnel mode, which implements failover within seconds. IPsec connections can be attached to transit routers to establish high availability connections based on ECMP routing.
You can upgrade single-tunnel IPsec-VPN connections to dual-tunnel IPsec-VPN connections. For more information, see Upgrade a VPN gateway to enable the dual-tunnel mode. An IPsec-VPN connection in dual-tunnel mode has an active tunnel and a standby tunnel. If the active tunnel is down, the standby tunnel takes over to ensure service availability. A VPN gateway is unavailable during the upgrade process. The existing connections are interrupted. We recommend that you upgrade a VPN gateway during a network maintenance window to prevent service interruptions.
User-level high availability: On the customer side, deploy multiple on-premises gateway devices to implement failover.
Active/standby connections by using IPsec-VPN and an Express Connect circuit: In addition to using IPsec-VPN connections to ensure stability and high availability, you can combine IPsec-VPN connections with an Express Connect circuit to improve the stability of your architecture. You can use static routes or BGP dynamic routing to connect on-premises gateway devices in your data center to VPN gateways. However, to connect on-premises gateway devices to VBRs, you must enable BGP dynamic routing.
Security and compliance
VPN Gateway uses the Internet Key Exchange (IKE) and IPsec protocols to encrypt and secure data transmission.
IKE versions:
If you use an SM VPN gateway, only IKEv1 is supported. If you use a standard VPN gateway, IKEv1 and IKEv2 are supported.
Compared with IKEv1, IKEv2 simplifies security association (SA) negotiations and provides better support for scenarios in which communication is established among multiple CIDR blocks. We recommend that you use IKEv2, which is the default version.
Encryption algorithms:
If you use a standard VPN gateway, Advanced Encryption Standard (AES)-128, AES-192, AES-256, Data Encryption Standard (DES), and Triple DES are supported.
If you use an SM VPN gateway, SM4 is supported, which is the default encryption algorithm.
NoteIf the bandwidth of the VPN gateway is 200 Mbit/s or higher, we recommend that you select the AES, AES-192, or AES-256 encryption algorithm. The Triple DES encryption algorithm is not recommended. AES is a symmetric-key encryption algorithm that provides high-strength encryption and decryption. It ensures secure data transmission and has minor impacts on the network latency, throughput, and forwarding performance. 3des is a triple data encryption algorithm. It compromises the forwarding performance because it is time-consuming and complex.
Authentication algorithms:
If you use a standard VPN gateway, Secure Hash Algorithm 1 (SA-1), MD5, SHA-256, SHA-384, and SHA-512 are supported. The default authentication algorithm is SA-1.
If you use an SM VPN gateway, only SM3 is supported, which is the default authentication algorithm.
Compliance: Alibaba Cloud VPN Gateway provides services in compliance with the policies and regulations of the Chinese mainland. You can use VPN Gateway to establish only intra-border connections. In cross-border communication scenarios, we recommend that you use cross-border lines of CEN.
Performance
High bandwidth: Each IPsec connection supports up to 1,000 Mbit/s of bandwidth. If you need to increase the bandwidth, you can attach multiple IPsec connections to transit routers. Your data center and VPN gateway can communicate over multiple IPsec-VPN connections.
High number of packets per second: Each IPsec connection supports up to 120,000 packets per second, which equals 256 bytes.
Each transit router supports 16 single-tunnel IPsec-VPN connections that have ECMP enabled.
Scalability
IPsec-VPN connections are ready to use after activation. Configurations immediately take effect. In addition, you can attach multiple IPsec connections to a transit router to scale up the bandwidth capacity.
Each transit router supports 16 single-tunnel IPsec-VPN connections that have ECMP enabled.
Observability
You can use CloudMonitor and Network Intelligence Service (NIS) to monitor VPN gateways and IPsec connections, and create threshold-triggered alert rules for VPN gateways. This helps you identify data transfer anomalies at the earliest opportunity.

Self-service capabilities
Diagnostics and troubleshooting
VPN Gateway supports multiple diagnostic tools.
You can view the logs of IPsec-VPN connections and SSL-VPN connections, and error codes of IPsec-VPN connections in the VPN Gateway console. After you activate NIS for VPN Gateway, you can troubleshoot VPN Gateway issues by using features such as VPN gateway diagnostics and the reachability analyzer.
The following table describes the diagnostic tools.
Diagnostic tool and references | Description |
You can use this feature to troubleshoot issues that occur when you use a VPN gateway, such as IPsec negotiation failures, incorrect route configurations of the VPN gateway, and abnormal status of the VPN gateway. The system provides suggestions based on the issue that is detected. | |
You can use this feature to check the connectivity between resources that use a VPN gateway. This helps you troubleshoot data transfer issues. | |
This topic provides answers to the frequently asked questions (FAQ) about IPsec-VPN connections. You can troubleshoot an IPsec-VPN connection issue based on the error code and log data of the IPsec-VPN connection displayed in the VPN Gateway console. For more information, see the Common IPsec-VPN connection issues and solutions section of the "Troubleshoot IPsec-VPN connection issues" topic. | |
This topic describes common negotiation issues and connectivity issues of IPsec-VPN connections and provides solutions. | |
If you encounter issues when you use IPsec-VPN connections, you can troubleshoot the issues based on this topic. |
Best practices
Connect to the DMZ VPC through a VPN gateway (active/standby tunnels)
Scenario: If a branch office or employees need to access each other or cloud resources, you can deploy a VPN gateway to establish communication. Multiple service VPCs can use the VPN gateway in the demilitarized zone (DMZ) VPC to access cloud resources over encrypted connections.
Key design of a DMZ VPC: Deploy a VPN gateway in the DMZ VPC, and use the VPN gateway to connect branch networks. After the DMZ VPC is connected to the transit router in the region, the DMZ VPC can access VPC, VBRs, and VPN gateways in the current or other regions.
Key design of VPN gateways
VPN gateway type: Select a standard or SM VPN gateway. The gateway type cannot be changed after the VPN gateway is created. Proceed with caution.
Tunnel mode: We recommend that you select the dual-tunnel mode, which supports active-standby tunnels, dual zones, and dual vSwitches. A dual-tunnel VPN gateway supports disaster recovery based on two public IP addresses and two zones.
Access services:
If you want to connect branch networks to the cloud, enable the IPsec-VPN feature and create an IPsec tunnel.
If you want to connect non-iOS clients to the cloud, enable the SSL-VPN feature and configure an SSL-VPN server.
If you want to connect iOS clients to the cloud, enable the SSL-VPN feature and configure an IPsec server.

Connect to a transit router through an IPsec tunnel (ECMP routing)
Scenario: If branch networks want to access each other or cloud resources, you can connect the branch networks to a transit router by using IPsec tunnels. You can attach multiple IPsec connections to a transit router. A data center can connect to a VPC over multiple IPsec-VPN connections, which can balance network traffic and provide a higher bandwidth capacity for private connections between the data center and the VPC.
Key design of ECMP routing based on multiple IPsec connections:
Alibaba Cloud: Configure multiple IPsec-VPN connections and attach them to a transit router. Add routes to the route table of the transit route to route traffic to the IPsec-VPN connections for ECMP routing. This way, cross-zone IPsec-VPN connection redundancy is guaranteed and the total bandwidth of IPsec-VPN tunnels is increased (1 Gbit/s per tunnel x Number of tunnels).
Branch networks: We recommend that you prepare multiple gateway devices and create a tunnel on each gateway device. Specify the gateway devices as next hops for ECMP routing. This way, multi-gateway device (multi-tunnel) disaster recovery is implemented and the total bandwidth of IPsec-VPN tunnels is increased (1 Gbit/s per tunnel x Number of tunnels).
NoteYou can also create multiple IPsec tunnels on only one device. However, single points of failure (SPOFs) occur if this device fails.

Encrypt connections over an Express Connect circuit by using a private VPN gateway
Scenario: Express Connect does not support encryption. To improve network security, you can use an IPsec-VPN connection to encrypt a private connection between a data center and a VPC over an Express Connect circuit.
Private connection encryption: After you establish a private connection between a data center and a VPC through an Express Connect circuit and CEN, you can establish an encrypted tunnel between a private VPN gateway and an on-premises gateway device. You can configure routes to route network traffic between the data center and the VPC to the encrypted tunnel. This way, network traffic transmitted through the tunnel is encrypted.
Key design of routing: VBRs and VPN gateways use different protocols. You can use the following routing methods: static routes for the VBR and VPN gateway, static routes for the VBR but BGP dynamic routing for the VPN gateway, and BGP dynamic routing for the VBR and VPN gateway.

Scenarios
Telecommuting: Allows employees to access the enterprise internal networks over encrypted private connections from remote terminals. VPN gateways allow employees to remotely access files and applications in the same way as they are in the office. This improves data transmission security and prevents data leaks. For multinational companies, VPN gateways are an important tool for maintaining day-to-day operations. For example, consultants of international consulting companies who are frequently on trip can use VPN gateways to access the enterprise internal network.
Secure data transmission: For companies that are sensitive to data transmission security, VPN gateways can establish secure tunnels. Connection encryption protects Internet data transmission against interceptions. This is a business-critical feature for financial institutions and legal advice agencies. For example, legal advice agencies exchange confidential files with customers over VPN gateways to protect customer privacy and sensitive information.
Disaster recovery for connections to the cloud: You can create an IPsec-VPN connection and an Express Connect circuit at the same time to implement disaster recovery. The IPsec-VPN connection and Express Connect circuit provide active/standby connections between your data center and Alibaba Cloud.
Virtualize the architecture on CADT
Connect to VPCs by using IPsec-VPN connections
Scenario | Item | References |
Connect to VPCs by using IPsec-VPN connections | Template ID | MXQCLVXC1E3J9GOZ |
Virtualized deployment template | ||
CADT API examples |
Visualized deployment architecture:
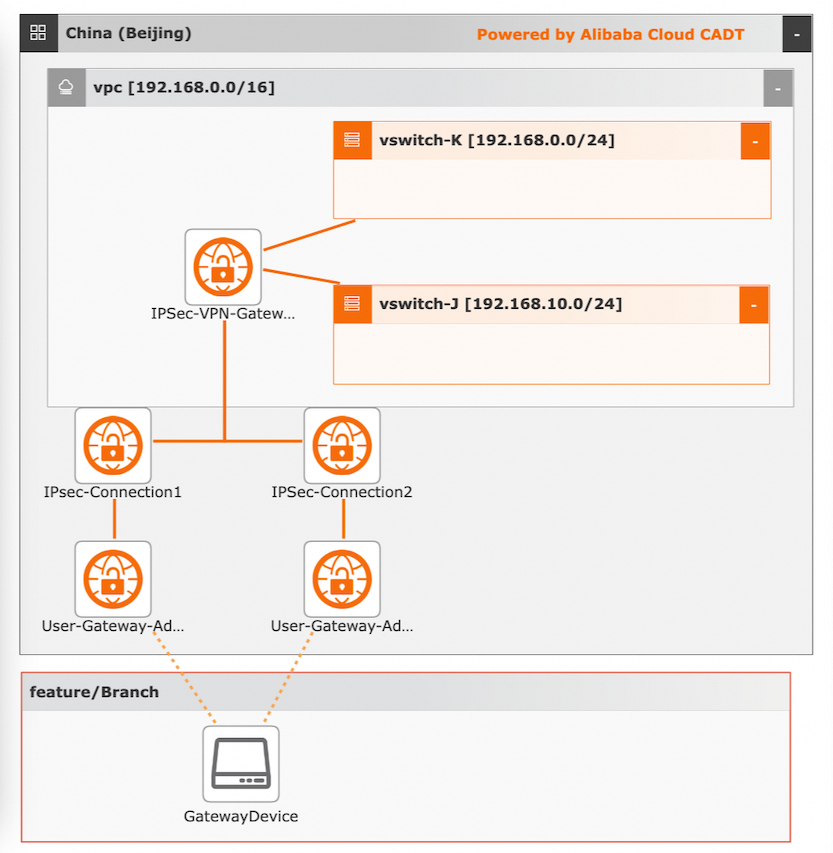
Procedures:
Visualized deployment
Create required cloud resources, including one VPC, two vSwitches, one VPN gateway, two IPsec-VPN connections, and two customer-side gateways with specific addresses.
Create an application based on a template. The default region is China (Beijing). Create the cloud resources, instead of using existing cloud resources.
Save and verify the application, and calculate the fees. In this example, the cloud resources use the pay-as-you-go billing method.
Confirm the configurations, select a protocol, and start the deployment of all resources.
API calls
Call the corresponding API operations to deploy and use cloud resources.
Refer to the documentation to initialize the configurations by using a command-line interface (CLI).
Refer to the sample YAML file to deploy and output the architecture.
If you want to modify the configurations, such as VPC and vSwitch, change the value of the ID field for a specific resource.
Connect to transit routers over IPsec tunnels
Scenario | Item | References |
Connect to transit routers over IPsec tunnels | Template ID | PDKTO11YPWOW43CY |
Virtualized deployment template | ||
CADT API examples |
Visualized deployment architecture:
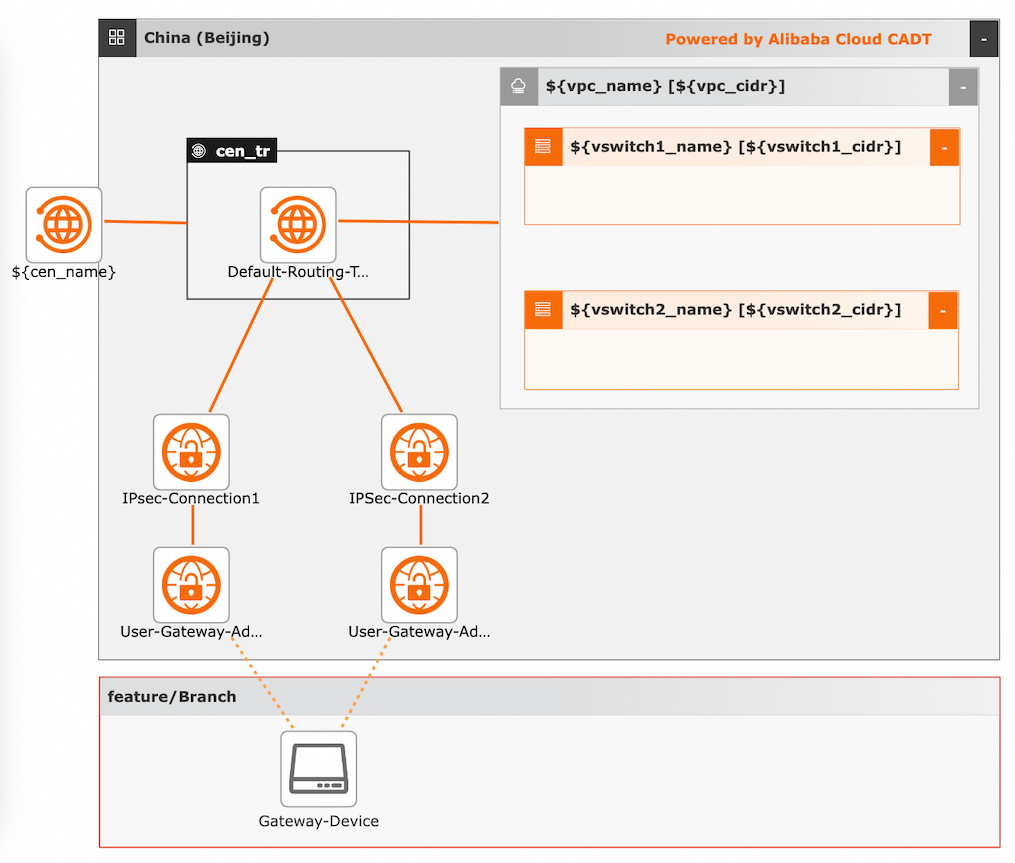
Procedures:
Visualized deployment
Create required cloud resources, including one VPC, two vSwitches, two IPsec-VPN connections, two customer-side gateways with specific addresses, one CEN instance, and one transit router.
Create an application based on a template. The default region is China (Beijing). Create the cloud resources, instead of using existing cloud resources.
Save and verify the application, and calculate the fees. In this example, the cloud resources use the pay-as-you-go billing method.
Confirm the configurations, select a protocol, and start the deployment of all resources.
API calls
Call the corresponding API operations to deploy and use cloud resources.
Refer to the documentation to initialize the configurations by using a command-line interface (CLI).
Refer to the sample YAML file to deploy and output the architecture.
If you want to modify the configurations, such as VPC and vSwitch, change the value of the ID field for a specific resource.