This topic describes how to use virtual private cloud (VPC) firewalls to manage traffic between east-west network elements in different regions. You can enable VPC firewalls and configure access control policies for the VPC firewalls based on your business requirements.
Example
In this example, an enterprise deploys Development VPC 1 (172.16.0.0/12) and Production VPC 1 (10.0.0.0/8) in the China (Beijing) region, and Development VPC 2 (172.16.0.0/12) and Production VPC 2 (10.0.0.0/8) in the China (Shenzhen) region. The VPCs are connected by using Enterprise Edition transit routers of a Cloud Enterprise Network (CEN) instance. The following figure shows the network architecture. The enterprise has the following requirements for access control on VPCs in this network architecture:
The development VPC in each region can have one-way access to the production VPC in the corresponding region.
The development VPCs can have access to each other in different regions.
VPC access from other directions is forbidden.

Solution
For the preceding CEN-based network architecture, you can use the VPC Firewall feature of Cloud Firewall to perform centralized management. The solution consists of the following steps:
Create VPC firewalls for the transit routers in the China (Beijing) and China (Shenzhen) regions.
Configure traffic redirection scenarios for the VPC firewalls and select the Interconnected Instances type for each traffic redirection scenario to add each VPC to the traffic redirection scenario.
Configure access control policies for the VPC firewalls to implement access control.
The solution is easy to deploy, secure, and reliable, and supports flexible O&M. Enterprises can use this solution to perform security management for cloud networks.
Procedure
Step 1: Create VPC firewalls
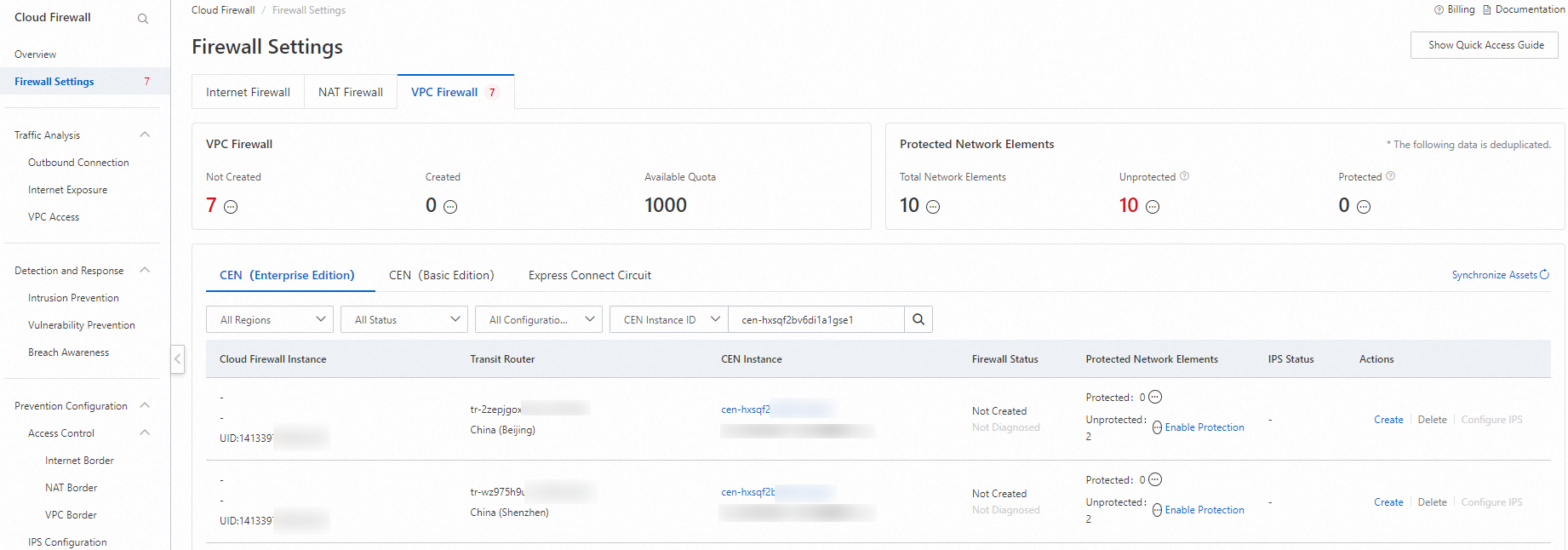
Log on to the Cloud Firewall console. In the left-side navigation pane, click Firewall Settings.
On the VPC Firewall tab, find the transit routers in the China (Beijing) and China (Shenzhen) regions and click Create. For more information, see Configure a VPC firewall for an Enterprise Edition transit router.
Step 2: Create and enable traffic redirection scenarios
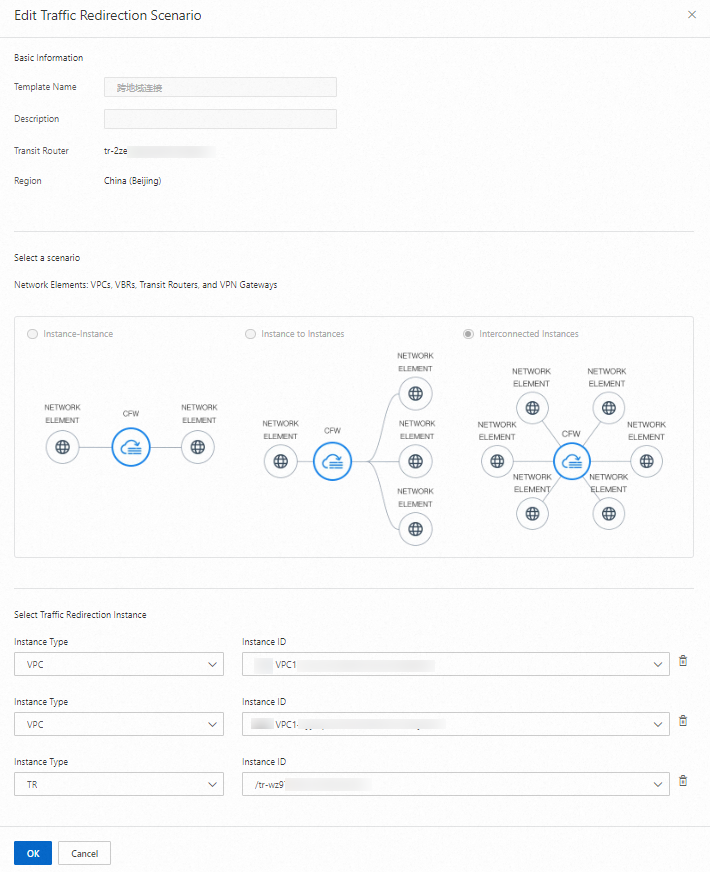
Find the VPC firewalls that are created for the transit routers in the China (Beijing) and China (Shenzhen) regions and click Details. On the Redirection Scenario tab, click Create Redirection Scenario to create a traffic redirection scenario for each VPC firewall.
When you create a traffic redirection scenario, select Interconnected Instances as the scenario type. Then, add the production VPC, development VPC, and peer transit router to the traffic redirection scenario.
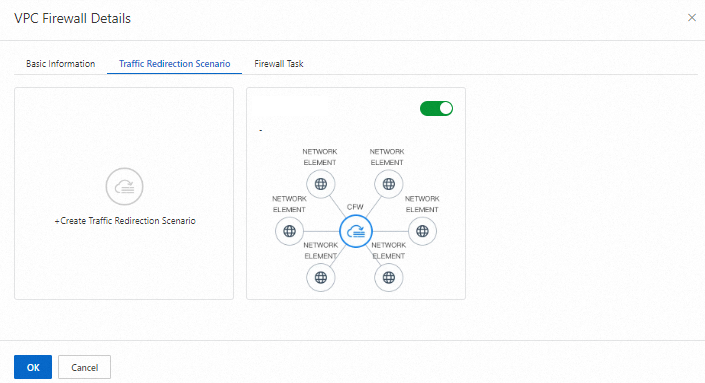
Enable the traffic redirection scenarios.
By default, a traffic redirection scenario is enabled after it is created. When you enable the VPC firewalls, make sure that the traffic redirection scenarios are also enabled.
Step 3: Configure access control policies for the VPC firewalls
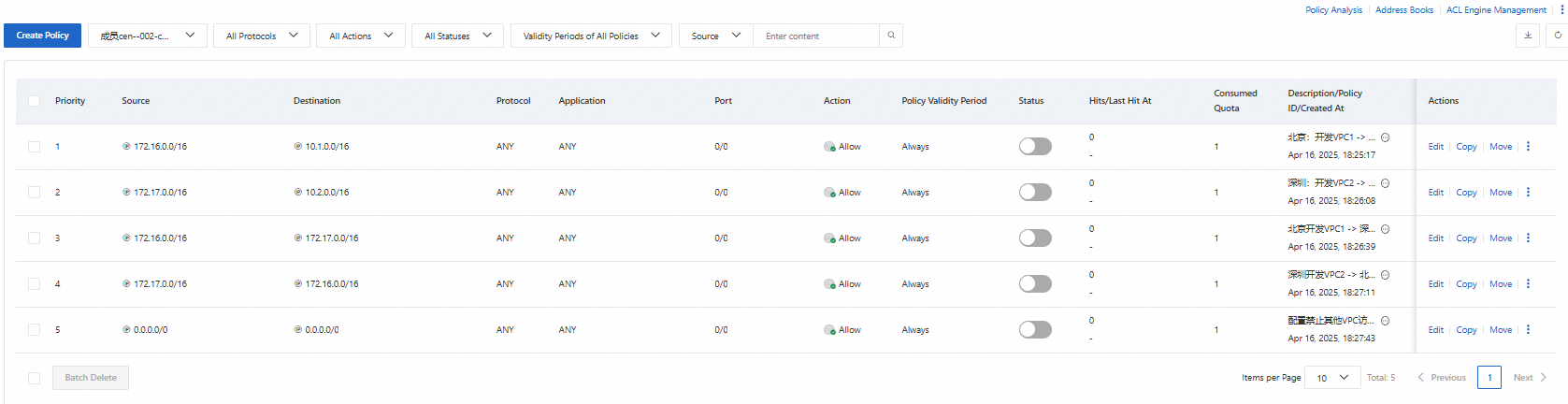
On the page, configure access control policies. The following table describes the access control policies. For more information, see Create an access control policy for a VPC firewall.
The access control policies apply to traffic that is redirected to the CEN instance and the VPC firewalls in the China (Beijing) and China (Shenzhen) regions.
Access control policy | Source | Destination | Protocol | Port | Application | Action | Priority | Policy validity period | Status |
Development VPC 1 to Production VPC 1 in the China (Beijing) region | 172.16.0.0/16 | 10.1.0.0/16 | ANY | ANY | ANY | Allow | 1 | Always | Enabled |
Development VPC 2 to Production VPC 2 in the China (Beijing) region | 172.17.0.0/16 | 10.2.0.0/16 | ANY | ANY | ANY | Allow | 2 | Always | Enabled |
Development VPC 1 in the China (Beijing) region to Development VPC 2 in the China (Shenzhen) region | 172.16.0.0/16 | 172.17.0.0/16 | ANY | ANY | ANY | Allow | 3 | Always | Enabled |
Development VPC 2 in the China (Shenzhen) region to Development VPC 1 in the China (Beijing) region | 172.17.0.0/16 | 172.16.0.0/16 | ANY | ANY | ANY | Allow | 4 | Always | Enabled |
Other VPCs to the cloud assets | 0.0.0.0/0 | 0.0.0.0/0 | ANY | ANY | ANY | Deny | 5 | Always | Enabled |
The following figure shows an example.
Step 4: Verify the configurations
Run the ping command to simulate traffic from the private IP addresses of the Elastic Compute Service (ECS) instances in the four VPCs.
For example, you can log on to an ECS instance in Development VPC 1 in the China (Beijing) region and ping the private IP address of an ECS instance in Production VPC 1 in the China (Beijing) region.
Check whether traffic between the network elements is managed by VPC firewalls.
Log on to the Cloud Firewall console. In the left-side navigation pane, choose . On the tab, view the access logs of the network elements on the VPC boundary.
In this example, an ECS instance in Development VPC 1 in the China (Beijing) region accesses an ECS instance in Production VPC 1 in the China (Beijing) region. This example shows how to view traffic logs to check whether traffic is allowed.
To check whether traffic between the two ECS instances is allowed, set the source IP address to the private IP address of the ECS instance in Development VPC 1 and the destination IP address to the private IP address of the ECS instance in Production VPC 1 in the China (Beijing) region. The hit policy is the access control policy that manages the one-way traffic from Development VPC 1 to Production VPC 1 in the China (Shenzhen) region. This indicates that traffic between the two ECS instances is managed by the VPC firewall.
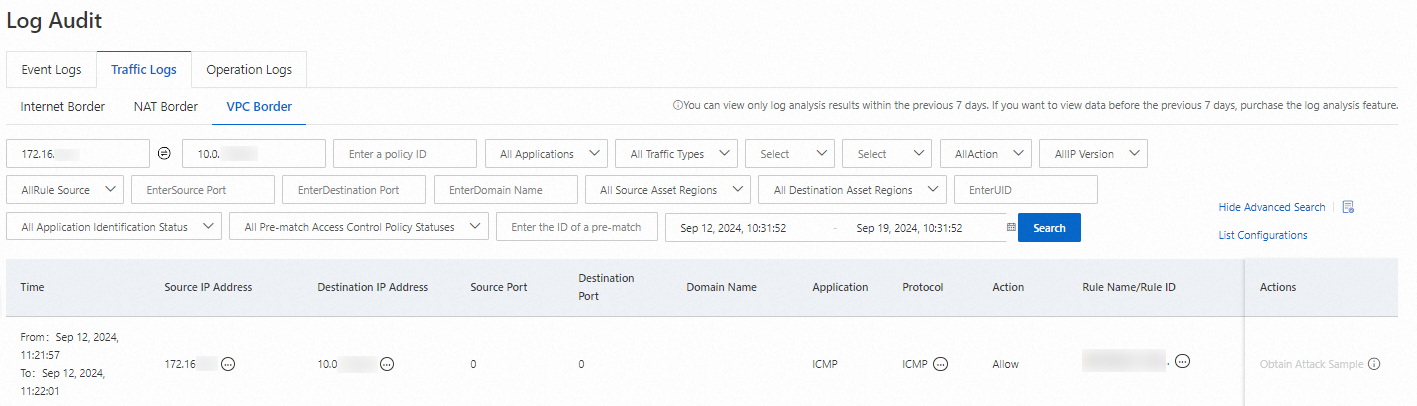
You can use the preceding method to check whether traffic between other VPCs meets your business requirements.
The following table describes traffic between VPCs in this scenario. You can compare the access logs that you query with the content in the table.
Network element
Traffic destination
Traffic control result
ECS instance in Development VPC 1 in the China (Beijing) region
ECS instance in Production VPC 1 in the China (Beijing) region
Allow
ECS instance in Development VPC 2 in the China (Shenzhen) region
Allow
ECS instance in Production VPC 2 in the China (Shenzhen) region
Deny
ECS instance in Production VPC 1 in the China (Beijing) region
ECS instance in Development VPC 1 in the China (Beijing) region
Deny
ECS instance in Development VPC 2 in the China (Shenzhen) region
Deny
ECS instance in Production VPC 2 in the China (Shenzhen) region
Deny
ECS instance in Development VPC 2 in the China (Shenzhen) region
ECS instance in Development VPC 1 in the China (Beijing) region
Allow
ECS instance in Production VPC 1 in the China (Beijing) region
Deny
ECS instance in Production VPC 2 in the China (Shenzhen) region
Allow
ECS instance in Production VPC 2 in the China (Shenzhen) region
ECS instance in Development VPC 1 in the China (Beijing) region
Deny
ECS instance in Production VPC 1 in the China (Beijing) region
Deny
ECS instance in Development VPC 2 in the China (Shenzhen) region
Deny
References
Cloud Firewall provides the automated policy analysis feature that you can use to analyze the access control policies configured on the VPC boundary in a timely and efficient manner.
Cloud Firewall provides a built-in intrusion prevention system (IPS) to block malicious traffic on the VPC boundary. For more information, see IPS overview.