If you need to perform identity authentication and authorization control in Service Mesh (ASM), you can configure an ASM security policy to implement JSON Web Token (JWT)-based authentication. This way, only requests that carry valid JWTs can access protected resources, which improves the security and privacy protection of service-to-service communications.
Background information
JWT is an open standard and is commonly used to authenticate and authorize users. A JWT carries user information and a field that stores encrypted user information. When you implement JWT-based authentication, the encrypted user information is decrypted and then compared with the input user information. This verifies the user identity.
Prerequisites
An application is deployed in the cluster that is added to the ASM instance.
An ingress gateway is deployed, and the IP address of the ingress gateway is obtained.
An Istio gateway and a virtual service are created to ensure that the following paths are accessible. For more information, see Step 1 to Step 3 in Use Istio resources to route traffic to different versions of a service.
http://${IP address of the ingress gateway}/productpage http://${IP address of the ingress gateway}/api/v1/products/1 http://${IP address of the ingress gateway}/static/jquery.min.js
Procedure
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the ASMSecurityPolicy page, click Create.
In the Create ASMSecurityPolicy dialog box, click JWT and then click OK.
In the JWT Config step of the configuration wizard, configure the parameters and click Next.
Parameter
Example
ASMSecurityPolicyName
test-jwt
Certification Rules
Issuer
testing@secure.istio.io
JWKS Source
jwks
Key
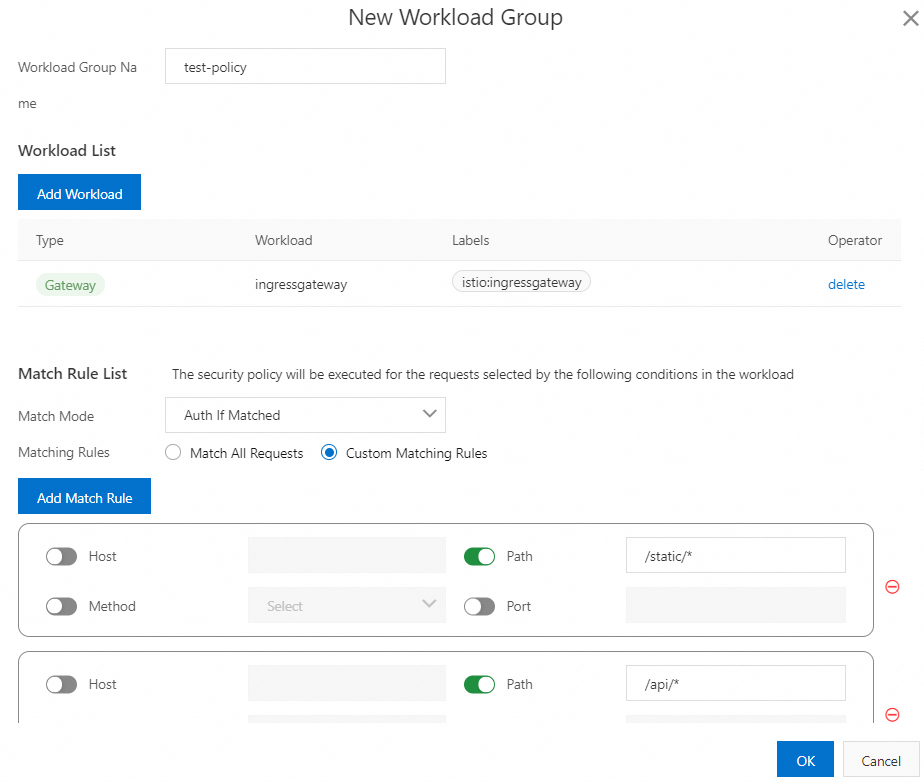
{ "keys":[ {"e":"AQAB","kid":"DHFbpoIUqrY8t2zpA2qXfCmr5VO5ZEr4RzHU_-envvQ","kty":"RSA","n":"xAE7eB6qugXyCAG3yhh7pkDkT65pHymX-P7KfIupjf59vsdo91bSP9C8H07pSAGQO1MV_xFj9VswgsCg4R6otmg5PV2He95lZdHtOcU5DXIg_pbhLdKXbi66GlVeK6ABZOUW3WYtnNHD-91gVuoeJT_DwtGGcp4ignkgXfkiEm4sw-4sfb4qdt5oLbyVpmW6x9cfa7vs2WTfURiCrBoUqgBo_-4WTiULmmHSGZHOjzwa8WtrtOQGsAFjIbno85jp6MnGGGZPYZbDAa_b3y5u-YpW7ypZrvD8BgtKVjgtQgZhLAGezMt0ua3DRrWnKqTZ0BJ_EyxOGuHJrLsn00fnMQ"}]}In the Workload and Match Rules step of the configuration wizard, click Add Workload Group. In the New Workload Group dialog box, configure the parameters, click OK, and then click Submit.
The following table describes how to configure the parameters in this example.
Parameter
Description
Workload Group Name
Set the parameter to test-policy.
Workload List
Click Add Workload.
In the Add Workload dialog box, select Gateway Scope.
In the Select workloads box, select the workload that you want to add, click the
 icon to add the selected workload to the selected box, and then click OK.
icon to add the selected workload to the selected box, and then click OK.
Match Rule List
The following two match modes are available:
Auth If Matched: Only requests that carry valid JWTs are allowed.
Bypass Auth If Matched: Requests that carry valid JWTs or do not carry JWTs are allowed. Requests that carry invalid JWTs are denied.
For this example, select Auth If Matched, set Matching Rules to Custom Matching Rules, click Add Match Rule, and then configure the following rules:
Rule 1: Turn on the Path switch and set the parameter to /static/*.
Rule 2: Turn on the Path switch and set the parameter to /api/*.
In the Complete step of the configuration wizard, the "ASMSecurityPolicy Creation successfully" message appears, indicating that the ASM security policy is created. You can click YAML to view the created resources, or click Complete to go back to the ASMSecurityPolicy page to view the created security policy.
Verify whether the JWT-based authentication configuration takes effect.
Run the following commands to perform access tests:
curl -I http://${IP address of the ingress gateway}/productpage # Status code 200 is returned. curl -I http://${IP address of the ingress gateway}/api/v1/products/1 # Status code 403 is returned. curl -I http://${IP address of the ingress gateway}/static/jquery.min.js # Status code 403 is returned. # Configure a JWT. TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjQ2ODU5ODk3MDAsImZvbyI6ImJhciIsImlhdCI6MTUzMjM4OTcwMCwiaXNzIjoidGVzdGluZ0BzZWN1cmUuaXN0aW8uaW8iLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.CfNnxWP2tcnR9q0vxyxweaF3ovQYHYZl82hAUsn21bwQd9zP7c-LS9qd_vpdLG4Tn1A15NxfCjp5f7QNBUo-KC9PJqYpgGbaXhaGx7bEdFWjcwv3nZzvc7M__ZpaCERdwU7igUmJqYGBYQ51vr2njU9ZimyKkfDe3axcyiBZde7G6dabliUosJvvKOPcKIWPccCgefSj_GNfwIip3-SsFdlR7BtbVUcqR-yv-XOxJ3Uc1MI0tz3uMiiZcyPV7sNCU4KRnemRIMHVOfuvHsU60_GhGbiSFzgPTAa9WTltbnarTbxudb_YEOx12JiwYToeX0DCPb43W1tzIBxgm8NxUg # Status code 200 is returned for all the following requests: curl -I http://${IP address of the ingress gateway}/productpage -H "Authorization: Bearer $TOKEN" curl -I http://${IP address of the ingress gateway}/api/v1/products/1 -H "Authorization: Bearer $TOKEN" curl -I http://${IP address of the ingress gateway}/static/jquery.min.js -H "Authorization: Bearer $TOKEN"According to the specified match mode and match rules, requests are allowed to access the paths that start with
/staticor/apionly when they carry valid JWTs, whereas requests are allowed to access the paths that start with/productpageonly when they carry valid JWTs or do not carry JWTs. The access results meet expectations. This indicates that the JWT-based authentication configuration takes effect.Modify the match mode and match rules of JWT-based authentication.
On the ASMSecurityPolicy page, find the JWT-based authentication policy that you want to modify and click Edit in the Actions column.
In the JWT Config step of the configuration wizard, click Next.
In the Workload and Match Rules step, find the workload group that you want to modify and click Edit in the Operator column.
In the New Workload Group dialog box, modify the match mode and match rules, click OK, and then click Submit.
The following table describes the parameter settings after the modification.
Parameter
Description
Match Mode
Select Bypass Auth If Matched.
Matching Rules
Remove the
/api/*matching rule and keep only the/static/*matching rule.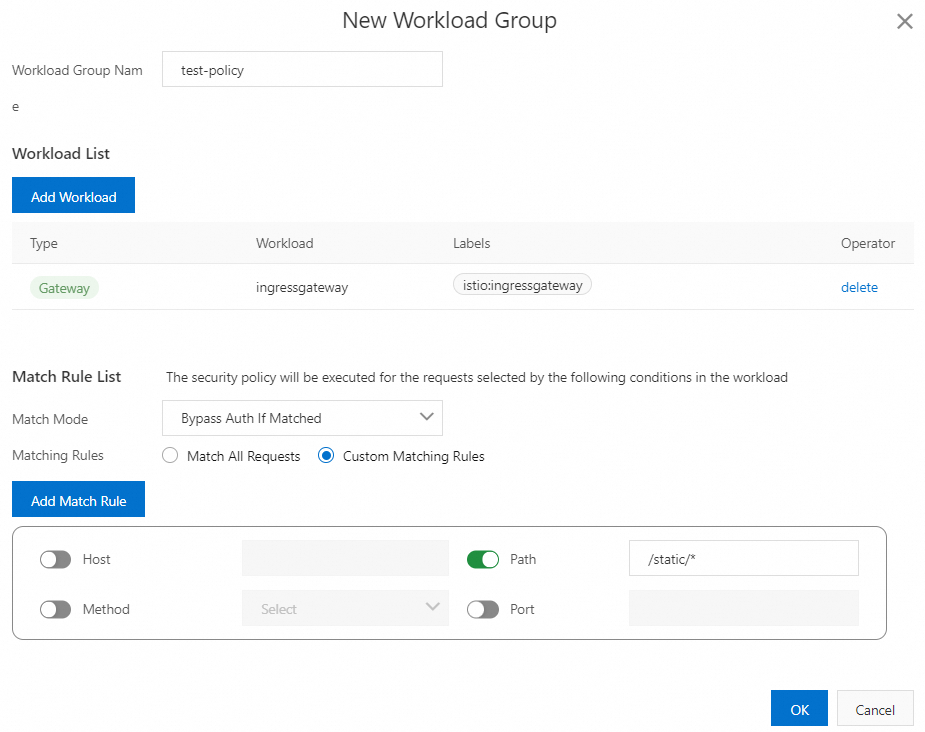
Run the following commands to check whether the modified JWT-based authentication configuration takes effect:
curl -I http://${IP address of the ingress gateway}/productpage # Status code 403 is returned. curl -I http://${IP address of the ingress gateway}/api/v1/products/1 # Status code 403 is returned. curl -I http://${IP address of the ingress gateway}/static/jquery.min.js # Status code 200 is returned. # Configure a JWT. TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjQ2ODU5ODk3MDAsImZvbyI6ImJhciIsImlhdCI6MTUzMjM4OTcwMCwiaXNzIjoidGVzdGluZ0BzZWN1cmUuaXN0aW8uaW8iLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.CfNnxWP2tcnR9q0vxyxweaF3ovQYHYZl82hAUsn21bwQd9zP7c-LS9qd_vpdLG4Tn1A15NxfCjp5f7QNBUo-KC9PJqYpgGbaXhaGx7bEdFWjcwv3nZzvc7M__ZpaCERdwU7igUmJqYGBYQ51vr2njU9ZimyKkfDe3axcyiBZde7G6dabliUosJvvKOPcKIWPccCgefSj_GNfwIip3-SsFdlR7BtbVUcqR-yv-XOxJ3Uc1MI0tz3uMiiZcyPV7sNCU4KRnemRIMHVOfuvHsU60_GhGbiSFzgPTAa9WTltbnarTbxudb_YEOx12JiwYToeX0DCPb43W1tzIBxgm8NxUg # Status code 200 is returned for all the following requests: curl -I http://${IP address of the ingress gateway}/productpage -H "Authorization: Bearer $TOKEN" curl -I http://${IP address of the ingress gateway}/api/v1/products/1 -H "Authorization: Bearer $TOKEN" curl -I http://${IP address of the ingress gateway}/static/jquery.min.js -H "Authorization: Bearer $TOKEN"According to the new match mode and match rule, requests are allowed to access the paths that start with
/staticonly when they do not carry JWTs or carry valid JWTs. Other requests are allowed only when they carry valid JWTs. The access results meet expectations. This indicates that the new JWT-based authentication configuration takes effect.
References
For more information about the concepts and features of ASM security policies, see Overview of ASM security policies.
You can enable the mesh audit feature to record or trace the daily operations of different users. You can also configure audit alerts for operations on ASM resources and send alert notifications to alert contacts in a timely manner when important resources change. For more information, see Use the KubeAPI operation audit feature in ASM and Configure audit alerts for operations on ASM resources.