To implement precise control over the access permissions of users on services, you can configure a blacklist or whitelist in the corresponding security policies of Service Mesh (ASM). Blacklists and whitelists are common authorization mechanisms that prohibit or allow specified requests to access applications. ASM allows you to configure blacklists and whitelists to control east-west traffic and north-south traffic from multiple dimensions, such as IP addresses, HTTP domain names, and ports. This guarantees the security of applications in ASM. This topic describes how to configure a blacklist for east-west traffic in an ASM security policy.
Prerequisites
An ingress gateway is deployed, and the IP address of the ingress gateway is obtained. For more information, see Create an ingress gateway.
An application is deployed in your ASM instance. For more information, see Deploy an application in an ASM instance.
An Istio gateway and a virtual service are created. http://${IP address of the ingress gateway}/productpage can be accessed. For more information, see Step 1 to Step 3 in Use Istio resources to route traffic to different versions of a service.
Procedure
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the ASMSecurityPolicy page, click Create. In the Create ASMSecurityPolicy dialog box, click Black/White List, and then click OK.
In the Workload and Match Rules step of the configuration wizard, configure the parameters and click Submit.
Parameter
Description
ASMSecurityPolicyName
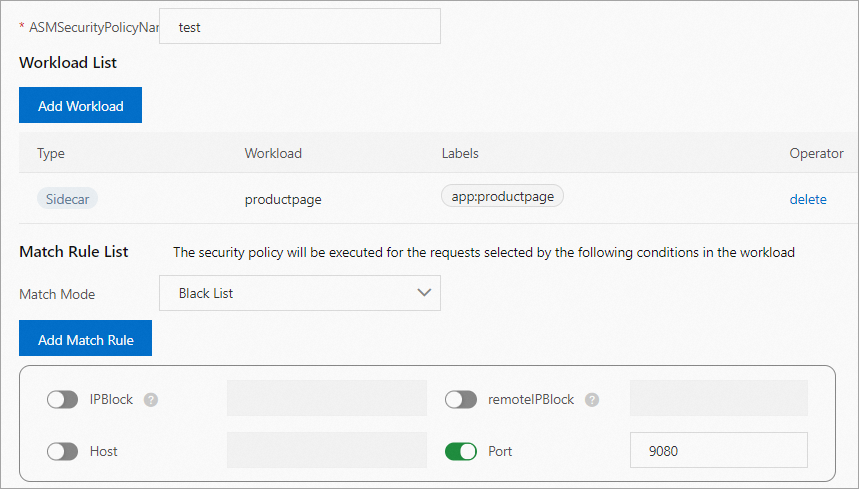
Set the name to test.
Workload List
Click Add Workload.
In the Add Workload dialog box, select Workload Scope. Set the Namespace parameter to default and the Workload Type parameter to Service.
In the Select workloads section, select productpage, click the
 icon to add the selected workload to the selected section, and then click OK.
icon to add the selected workload to the selected section, and then click OK.
Match Rule List
Select Black List for Match Mode, turn on Port, and then set the value to 9080. This setting indicates that all requests to access port 9080 of the productpage pod are denied.
In the Complete step of the configuration wizard, the "ASMSecurityPolicy Creation successfully" message appears, indicating that the ASM security policy is created. You can click YAML to view the created resources, or click Complete to go back to the ASMSecurityPolicy page to view the created security policy.
Run the following command to check whether the blacklist configurations take effect:
curl ${IP address of the ingress gateway}/productpage -IExpected output:
HTTP/1.1 403 Forbidden content-length: 19 content-type: text/plain date: Fri, 22 Dec 2023 03:07:26 GMT server: istio-envoy x-envoy-upstream-service-time: 10An HTTP
403status code is returned, indicating that access to the productpage service is denied. This indicates that the blacklist configurations take effect.
References
For more information about the concepts and features of ASM security policies, see Overview of ASM security policies.
You can enable the mesh audit feature to record or trace the daily operations of different users. You can also configure audit alerts for operations on ASM resources and send alert notifications to alert contacts in a timely manner when important resources change. For more information, see Use the KubeAPI operation audit feature in ASM and Configure audit alerts for operations on ASM resources.