Certificate Management Service (Original SSL Certificate) is an Alibaba Cloud platform for certificate issuance and management. You can deploy certificates directly to your data plane clusters from the Certificate Management Service console. These certificates can be used on ASM gateways. This topic describes how to use SSL certificates from Certificate Management Service in an ASM gateway.
Prerequisites
You have purchased or uploaded an available SSL certificate in the Certificate Management Service console.
You have deployed the httpbin application.
Step 1: Grant permissions to Certificate Management Service
Certificate Management Service uses the AliyunCASDefaultRole role to access and manage ACK clusters. You must grant permissions to this role.
Log on to the ACK console. In the left navigation pane, click Authorizations.
Click the RAM Roles tab, enter
AliyunCASDefaultRolein the search box, and then click Manage Permissions.If the message AliyunCASDefaultRole Does Not Exist appears, you must first create a RAM role for Certificate Management Service and grant permissions to the role.
In the Permission Management dialog box, click + Add Permissions. In the Cluster column, select the name of the cluster that you want to manage from the drop-down list. In the Namespace column, select
istio-systemfrom the drop-down list. In the Permission Management column, select Restricted User.Click Submit Authorization.
Step 2: Deploy the certificate to an ACK cluster
The domain name of the certificate used in this topic is test.com. You can modify the domain name as needed.
Deploy the certificate.
If this is the first time you use the deployment service, follow the on-screen prompts to grant the required permissions. After you grant the permissions, you can create deployment tasks. For more information about authorization, see Grant permissions to access cloud resources.
Log on to the Certificate Service console.
In the navigation pane on the left, choose .
On the SSL Certificate Management page, click the tab for your certificate type. In the certificate list, find the certificate and click Deploy in the Actions column.
Certificates issued by Private CA are synchronized to the Manage Uploaded Certificates tab. You can manage them on that tab.
On the Select Resource step of the Create Task page, select one or more cloud services and their resources. You can also adjust the selected resources. Then, click Preview and Submit.
The system automatically matches the selected SSL certificate with cloud service resources that already have an SSL certificate configured. In the dialog box that appears, click Submit. The system adds the matched resources to the Selected Resources section. You can then adjust the selection.
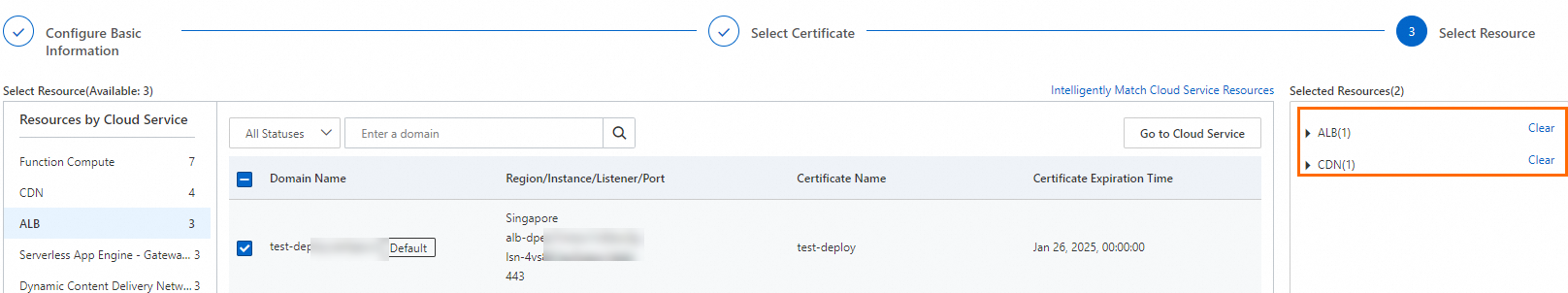
The system automatically detects and retrieves all resources of your cloud services. If you cannot find the destination resource in the corresponding cloud service, check the following items:
In the Total Resources section, check whether the resources are synchronized. If the resources are being synchronized (the status is grayed out as shown in the figure), wait for the synchronization to complete. The synchronization time varies based on the number of resources in your cloud service.
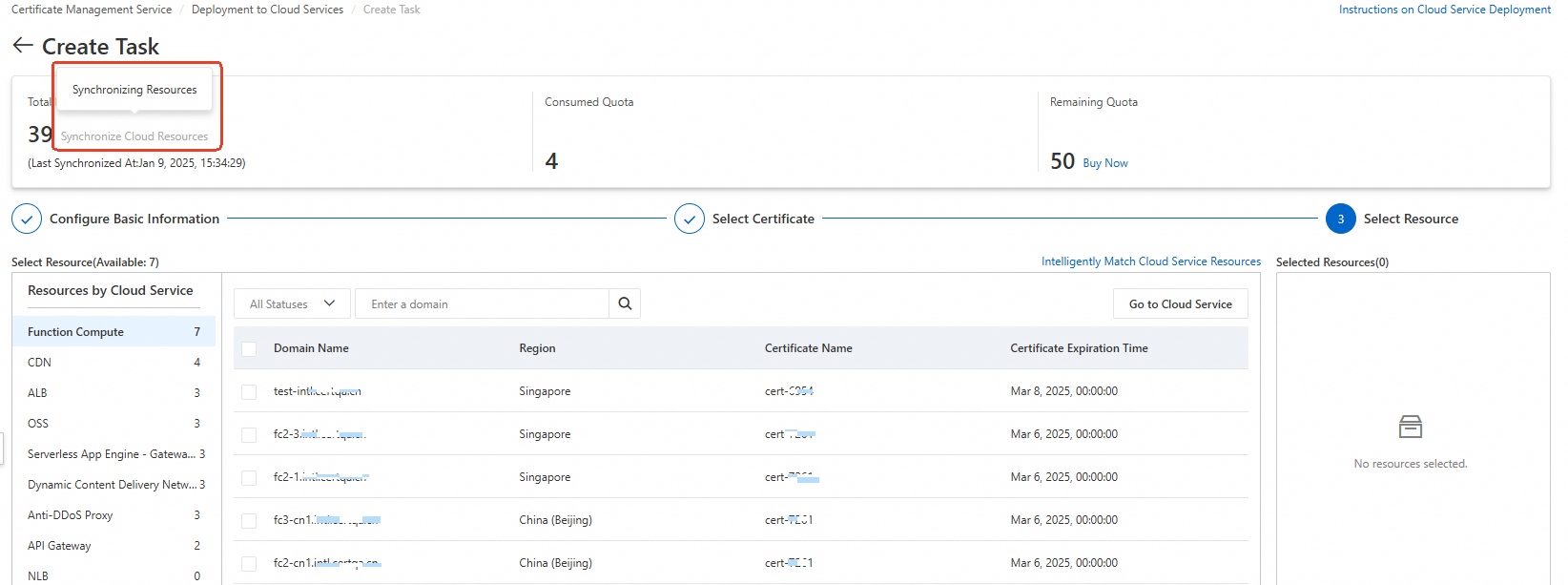
If you still cannot find the resource after synchronization is complete, check whether the prerequisites for certificate deployment are met.
In the Task Preview panel, confirm the information about the certificate instance and cloud service resources. If everything is correct, click Submit.
The preview page shows the number of matched certificates for the cloud service and the number of deployment quotas that will be consumed. If the number of matched certificates is 0, it means the selected certificate does not match the cloud service resource and the deployment will fail. In this case, review the selected certificate.
Obtain the Secret information.
kubectl -n istio-system get secret -l alibabacloud.com/ssl-certificate-identifier=${CertIdentifier of the SSL certificate}Expected output:
NAME TYPE DATA AGE cas-cert-305xxx76 kubernetes.io/tls 2 10m
Step 3: Update the gateway rule
Update the gateway rule that was created when you deployed the httpbin application. Add the host and the Secret created in the previous step.
kubectl apply -f - <<EOF
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: httpbin
namespace: default
spec:
selector:
istio: ingressgateway
servers:
- hosts:
- '*'
port:
name: test
number: 80
protocol: HTTP
- hosts:
- 'test.com'
port:
name: https
number: 443
protocol: HTTPS
tls:
mode: SIMPLE
credentialName: ${Name of the Secret obtained in the previous step}
EOFStep 4: Test the access
Obtain the gateway IP address.
export GATEWAY_IP=$(kubectl get service istio-ingressgateway -n istio-system -o jsonpath='{.status.loadBalancer.ingress[0].ip}' )Send a test request.
curl -vk --resolve test.com:443:${GATEWAY_IP} https://test.com/status/418Expected output:
* Added test.com:443:47.xx.xxx.146 to DNS cache * Hostname test.com was found in DNS cache * Trying 47.xx.xxx.146... * TCP_NODELAY set * Connected to test.com (47.xx.xxx.146) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: /etc/pki/tls/certs/ca-bundle.crt CApath: none ... * SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384 * ALPN, server accepted to use h2 * Server certificate: * subject: CN=test.com; O=myexample organization * start date: Jul 28 09:19:32 2025 GMT * expire date: Jul 28 09:19:32 2026 GMT * issuer: O=myexample Inc.; CN=test.com * SSL certificate verify result: unable to get local issuer certificate (20), continuing anyway. * Using HTTP2, server supports multi-use * Connection state changed (HTTP/2 confirmed) * Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0 ... > GET /status/418 HTTP/2 > Host: test.com > User-Agent: curl/7.61.1 > Accept: */* > ... < HTTP/2 418 < server: istio-envoy < date: Tue, 29 Jul 2025 08:45:10 GMT < x-more-info: http://tools.ietf.org/html/rfc2324 < access-control-allow-origin: * < access-control-allow-credentials: true < content-length: 135 < x-envoy-upstream-service-time: 5 < -=[ teapot ]=- _...._ .' _ _ `. | ."` ^ `". _, \_;`"---"`|// | ;/ \_ _/ `"""` * Connection #0 to host test.com left intactThe response includes TLS-related information and a 418 response.