If you want to monitor applications and implement tracing capabilities across Alibaba Cloud accounts. You can aggregate application data into an Alibaba Cloud account, and use RAM users or RAM roles to authorize other Alibaba Cloud accounts to view or manage the data.
Limits
If you aggregate application data from multiple Alibaba Cloud accounts into an Alibaba Cloud account, you need to manually separate the data reporting, authorization, bills, and fine-grained permissions of different accounts. This greatly increases the complexity in user experience. Generally, for enterprises that have multiple Alibaba Cloud accounts, we recommend that each account manages applications on its own. Therefore, please comprehensively consider the aggregation.
Solution
Assume that an enterprise has both Alibaba Cloud accounts A and B. Account A was used to activate Application Real-Time Monitoring Service (ARMS), and Account B was used to activate Elastic Compute Service (ECS) and Container Service for Kubernetes (ACK). If the enterprise wants to integrate the applications of Account B into the ARMS service that belongs to Account A, and use Account A to manage all applications, the enterprise can perform the following operations:
ACK applications
Create a RAM user for Account A, and attach the AliyunARMSFullAccess and AliyunSTSAssumeRoleAccess policies to the RAM user. For more information, see Create a RAM user.
Create an AccessKey pair for the RAM user. For more information, see Create an AccessKey pair.
Install the ARMS agent (ack-onepilot component) for the applications of Account B. For more information, see Automatically install an ARMS agent in ACK.
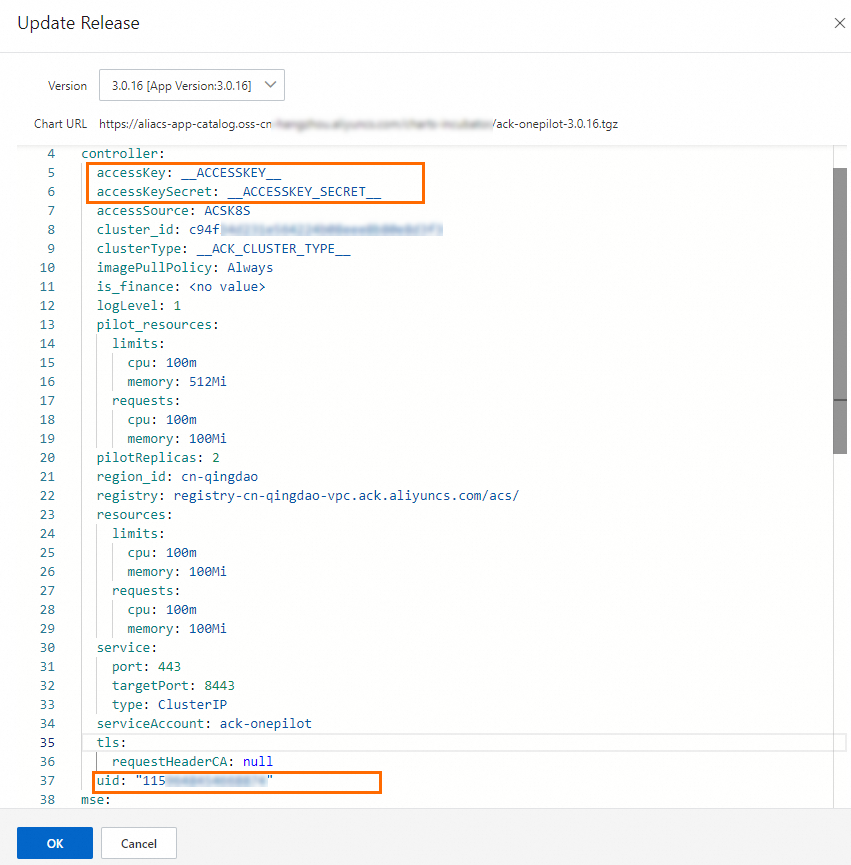
Log on to the ACK console. In the left-side navigation pane of the cluster details page, choose . On the Helm page, find ack-onepilot and click Update in the Actions column.
Replace the
accessKeyandaccessKeySecretparameters with the AccessKey ID and AccessKey secret obtained in Step 2, replace theuidparameter with the ID of Account A, and then click OK.Then, the ACK application data of Account B will be reported to the ARMS service of Account A.
ImportantMake sure that the version of the ack-onepilot component is 3.0.14 or later. The ack-onepilot component v3.0.14 and later requires configuring the AccessKey pair for reporting data across Alibaba Cloud accounts. For information about the release notes of the ack-onepilot component, see ack-onepilot.
Use a RAM user of Account A to manage applications.
Method 1: Use the RAM user created in Step 1.
Method 2: Create another RAM user for Account A.
Create another RAM user for Account A. Then, you can attach the AliyunARMSFullAccess policy to the RAM user so that the RAM user has full permissions on ARMS. You can also attach a custom policy to the RAM user to grant fine-grained permissions on the applications. For more information, see Application Monitoring: Attach a custom policy to a RAM user.
NoteIn addition to the preceding methods, you can manage applications by using a RAM user of Account B to assume a RAM role of Account A. For more information, see the (Optional) Use a RAM role to manage applications section.
ECS applications
On the Integration Center page of the ARMS console, obtain the license key of Account A.
ImportantEach account has a unique license key.
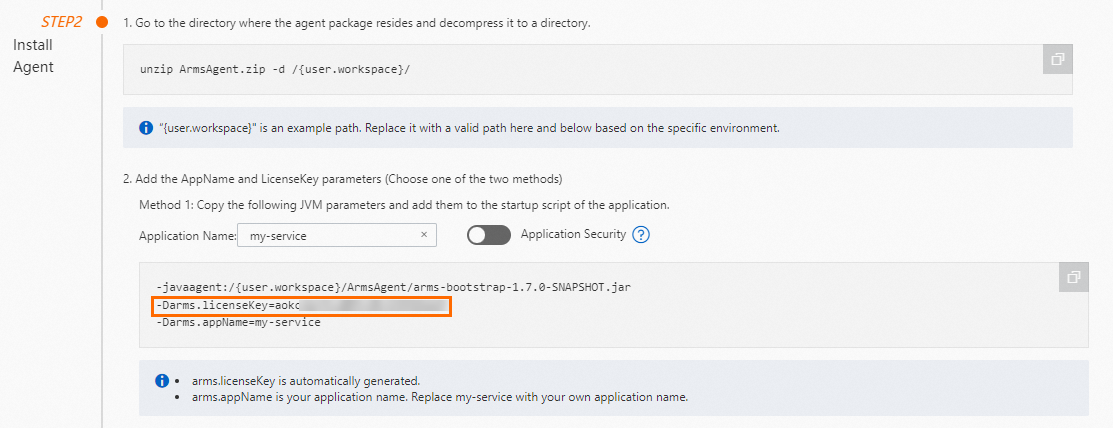
Download the installation package of the ARMS agent. Then, use the preceding license key to install an ARMS agent for each application deployed in ECS instances. For more information, see Manually install an ARMS agent.
Use a RAM user of Account A to manage applications.
Create another RAM user for Account A. Then, you can attach the AliyunARMSFullAccess policy to the RAM user so that the RAM user has full permissions on ARMS. You can also attach a custom policy to the RAM user to grant fine-grained permissions on the applications. For more information, see Application Monitoring: Attach a custom policy to a RAM user.
NoteIn addition to the preceding methods, you can manage applications by using a RAM user of Account B to assume a RAM role of Account A. For more information, see the (Optional) Use a RAM role to manage applications section.
(Optional) Use a RAM role to manage applications
If you do not want the RAM user of Account A to use ARMS, you can authorize the RAM user of Account B to use ARMS.
Step 1: Grant permissions to Account B
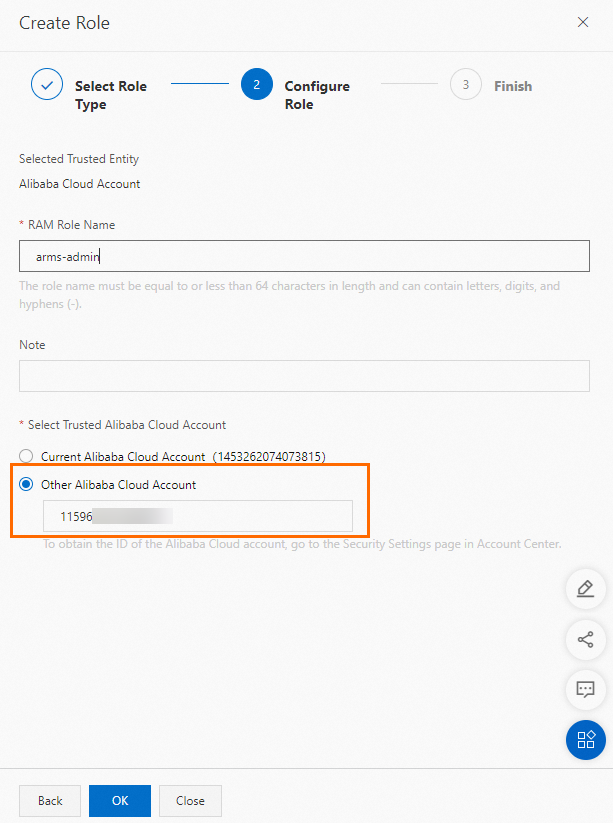
Use Account A to create a RAM role whose trusted entity is an Alibaba Cloud account. In this example, the RAM role
arms-adminis created. Configure Account B as the trusted entity.For more information, see Create a RAM role for a trusted Alibaba Cloud account.
Attach the AliyunARMSFullAccess policy to
arms-adminso that the RAM user has full permissions on ARMS. You can also attach a custom policy to the RAM role to grant fine-grained permissions on the applications.For information about how to create a custom policy, see Application Monitoring: Attach a custom policy to a RAM user.
For information about how to attach a policy to a RAM role, see Grant permissions to a RAM role.
Create a RAM user for Account B.
For more information, see Create a RAM user.
ImportantSave the username and password of the RAM user.
Use Account B to attach the AliyunSTSAssumeRoleAccess policy to the RAM user. Then, the RAM user can assume the RAM role.
For more information, see Grant permissions to a RAM user.
Step 2: Use the RAM user of Account B to manage applications
Use the RAM user that belongs to Account B to log on to the RAM console.
For more information, see Log on to the Alibaba Cloud Management Console as a RAM user.
Move the pointer over the avatar and click Switch Identity.
Enter the ID of Account A and the name of the RAM role created for Account A in Step 1.
For more information, see Assume a RAM role.
Log on to the ARMS console. In the left-side navigation pane, choose . On the Applications page, view the applications.