This topic describes how to configure an Active Directory (AD) domain controller on an Elastic Compute Service (ECS) instance and connect an ApsaraDB RDS for PostgreSQL instance to a self-managed AD domain.
Background information
AD is a directory service that is provided by Microsoft. A directory is a hierarchical structure that stores information about the objects on the same LAN. An enterprise can store data, such as computer accounts, user accounts, and groups, in a directory. This way, the enterprise can improve the security of the data and manage the data in a more convenient manner.
You can connect your RDS instance to a self-managed AD domain. This way, you can manage your enterprise in a centralized manner and can configure IP address whitelists at the database level and the user level to improve the security of your data.
You can modify the information of the AD domain controller in the pg_hba.conf file of your RDS instance or add the information of the AD domain controller to the pg_hba.conf file of your RDS instance. You can configure the AD domain controller and the pg_hba.conf file in the ApsaraDB RDS console. For more information, see Introduction of pg_hba.conf file.
Prerequisites
Your RDS instance meets the following requirements:
The RDS instance runs PostgreSQL 10 or later.
The RDS instance runs a minor engine version of 20210228 or later. For more information about how to update the minor engine version of your RDS instance, see Update the minor engine version of an ApsaraDB RDS for PostgreSQL instance.
The RDS instance uses cloud disks.
An ECS instance is created. For more information, see Create an ECS instance. Your RDS instance must access the self-managed AD domain by using a private IP address. Therefore, the ECS instance must meet the following conditions:
The ECS instance and your RDS instance reside in the same virtual private cloud (VPC).
The security group to which the ECS instance belongs is configured to allow access from the private IP address of your RDS instance. For more information, see Add a security group rule.
The firewall of the ECS instance is disabled by default. If the firewall is enabled for the ECS instance, you must configure the firewall to allow access from the private IP address of your RDS instance.
The image of the ECS instance runs Windows Server 2016 or later.
The domain account belongs to the Domain Admins group.
Your Alibaba Cloud account is used to log on to the ApsaraDB RDS console.
Procedure
Configure an AD domain controller for the ECS instance.
Log on to the ECS instance.
NoteThe AD domain controller must run a Windows Server system. We recommend that you use Windows Server 2016 or later. In this example, the AD domain controller runs Windows Server 2016.
Search for and open Server Manager.
In the left-side navigation pane, click Dashboard. On the page that appears, click Add roles and features.
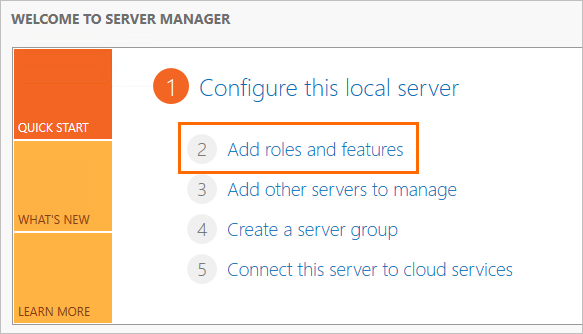
In the Add Roles and Features Wizard, configure the following parameters.
Tab
Description
Before You Begin
Use the default settings.
Installation Type
Use the default settings.
Server Selection
Use the default settings.
Server Roles
Select Active Directory Domain Services. In the dialog box that appears, click Add Features.
Select DNS Server. In the dialog box that appears, click Add Features.
NoteMake sure that your computer uses a fixed IP address. If the IP address dynamically changes, the DNS server becomes unavailable.
Features
Use the default settings.
AD DS
Use the default settings.
DNS Server
Use the default settings.
Install
Click Install to add the role that you configured.
After the role is added, click Close to close the wizard.
In the left-side navigation pane of Server Manager, click AD DS. In the upper-right corner of the page that appears, click More.
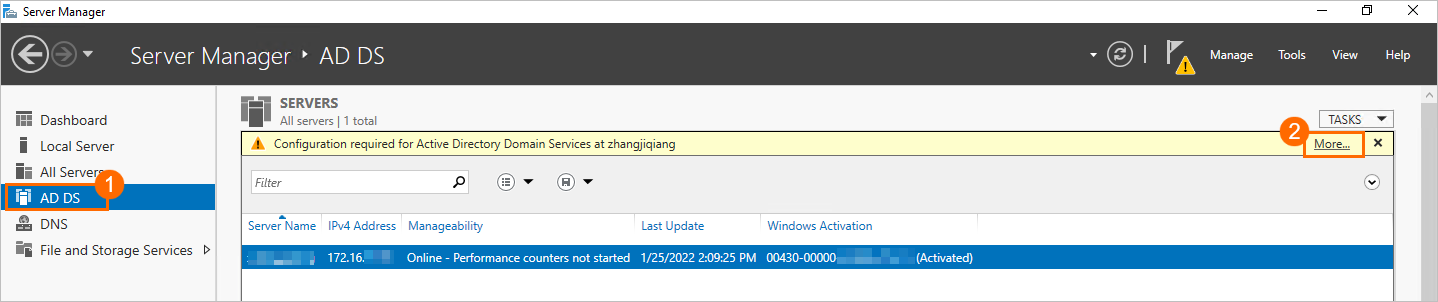
In the All Servers Task Details and Notifications wizard, click Promote this server to a domain controller.
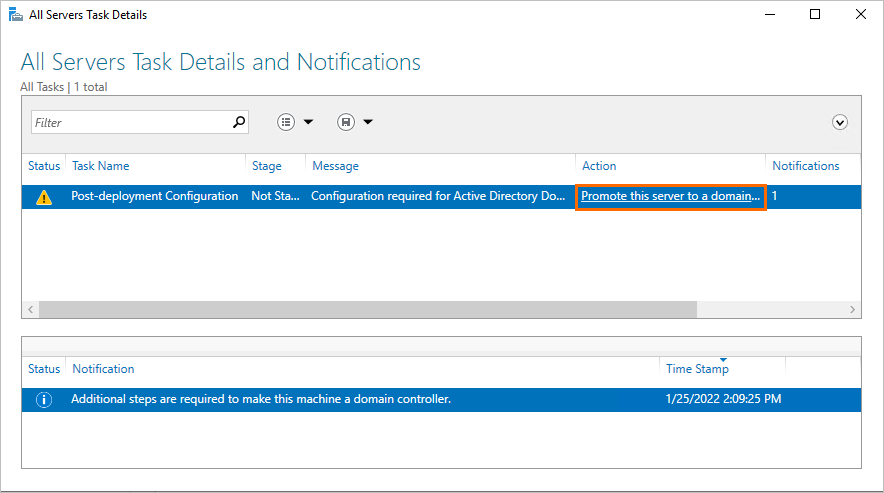
In the Active Directory Domain Services Configuration Wizard, configure the following parameters.
Tab
Description
Deployment Configuration
Select Add a new forest and configure the Root domain name parameter.
NoteIn this example, the Root domain name parameter is set to
pgsqldomain.net, wherepgsqldomainis the prefix andnetis the suffix of the domain name. You can specify a value based on your business requirement and use the same value during the whole process.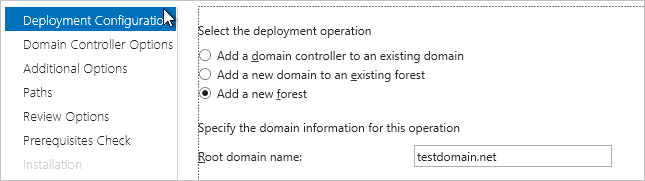
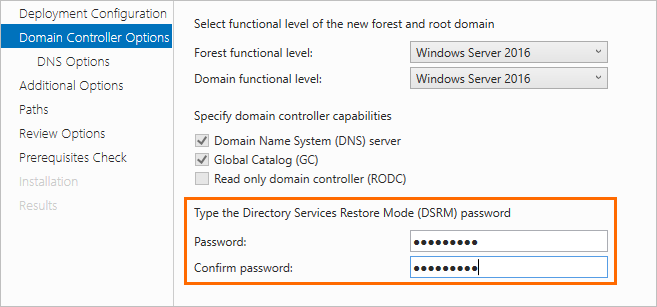
Domain Controller Options
Specify a Directory Service Restore Mode (DSRM) password.
Server Selection
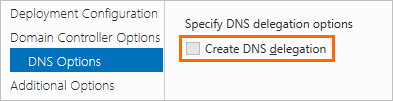
Clear Create DNS delegation.
Additional Options
Use the default settings.
Paths
Use the default settings.
Review Options
Use the default settings.
Prerequisites Check
Click Install.
NoteAfter the ECS instance is promoted to an AD domain controller, you must restart the ECS instance. Then, you can perform the subsequent steps.
Add an administrator user to the AD domain controller.
Log on to the ECS instance. Then, search for and open Server Manager.
In the left-side navigation pane of Server Manager, click AD DS, right-click the AD domain controller that you want to configure, and then select Active Directory Users and Computers.
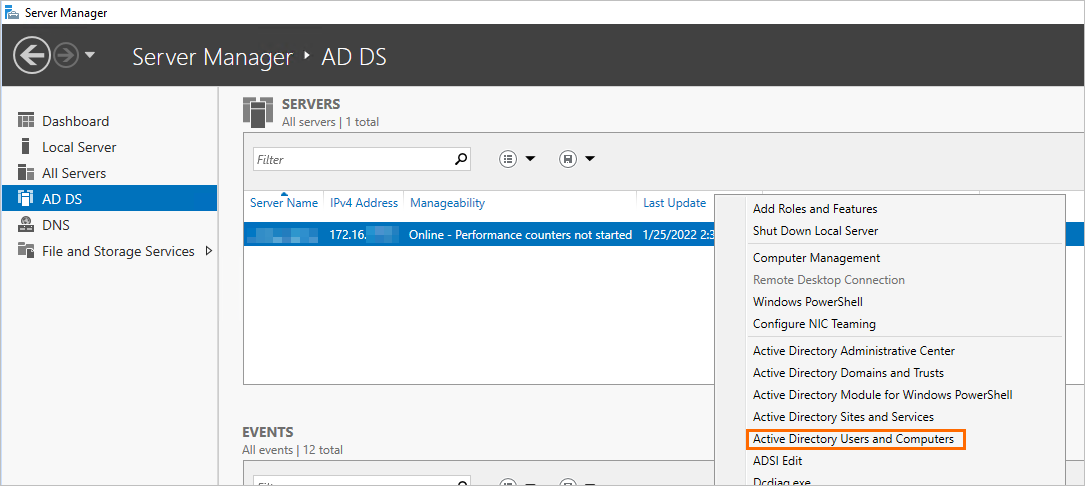
Click , right-click Users, and then choose .
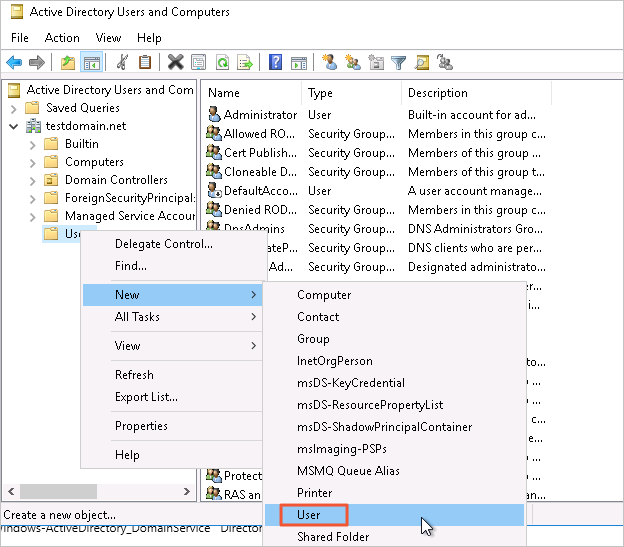 Note
Notepgsqldomain.net is the root domain name that is specified in the Active Directory Domain Services Configuration Wizard.
Specify a username and click Next.
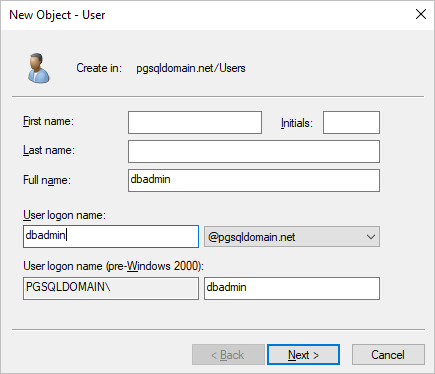
Specify a password, select Password never expires, and then click Next. Then, click Finish.
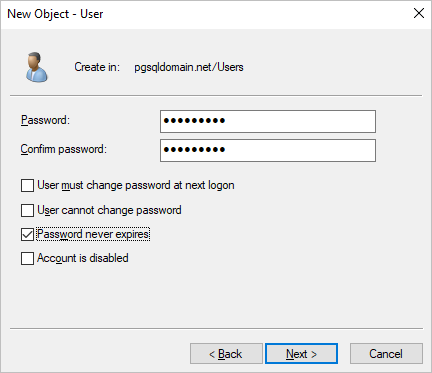
Double-click the created user and add the user to the Domain Admins administrator group.
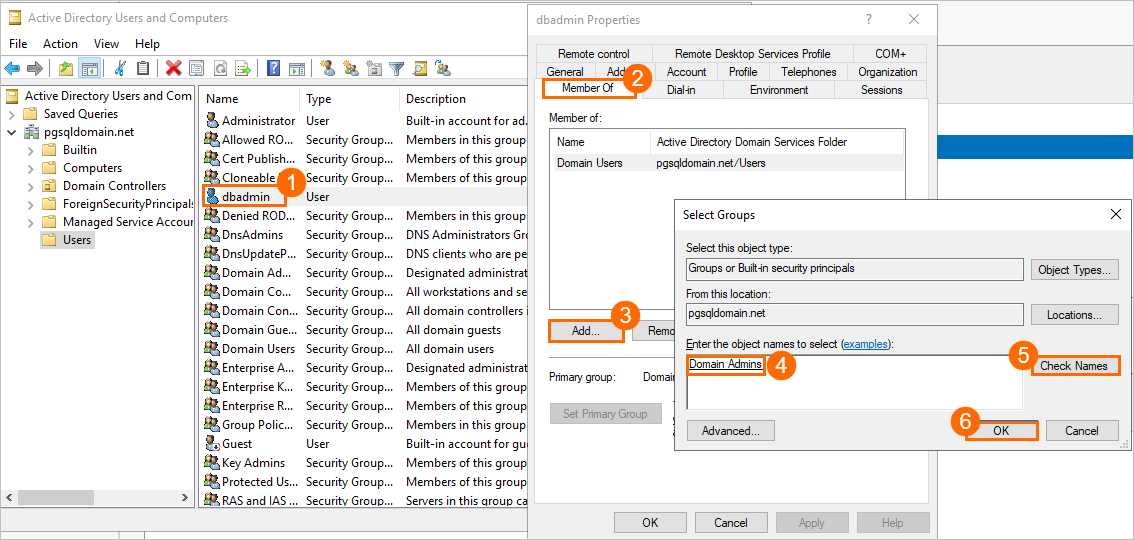
After the user is added to the Domain Admins administrator group, the following page appears.
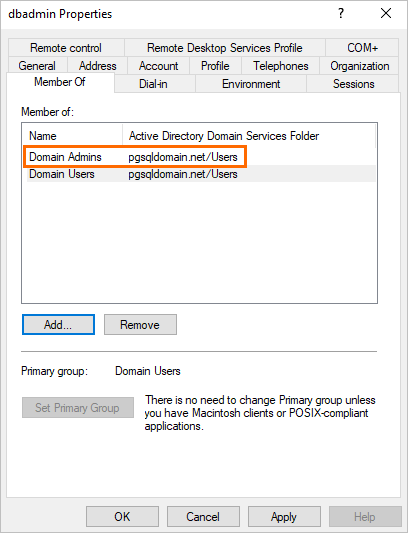
Add a standard user to the AD domain controller for logon.
NoteYou must perform the same operations that are described in Add an administrator user to the AD domain controller. A standard user does not need to be added to the Domain Admins administrator group.
In this example, a standard user named
ldapuseris added to the AD domain controller. This user is used to log on to your RDS instance.Configure security group rules for the ECS instance.
Log on to the ECS console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region in which the ECS instance resides.
On the Instances page, find the required ECS instance and click the ID of the ECS instance.
In the left-side navigation pane, click Security Groups. On the page that appears, click Add Rules in the Actions column.
NoteA number of ports need to be enabled for the AD domain controller. We recommend that you configure a separate security group for the AD domain controller rather than configuring the AD domain controller in the same security group as other ECS instances.
On the Inbound tab, click Add Rule to create a rule to allow your RDS instance to access the ECS instance over the following ports.
Protocol type
Port range
Description
TCP
88
The port for the Kerberos authentication protocol.
TCP
135
The port for the Remote Procedure Call (RPC) protocol.
TCP/UDP
389
The port for the Lightweight Directory Access Protocol (LDAP).
TCP
445
The port for the Common Internet File System (CIFS) protocol.
TCP
3268
The port for Global Catalog.
TCP/UDP
53
The port for the DNS service.
TCP
49152 to 65535
The default dynamic port range for connections. Enter a value in the following format: 49152/65535.
Configure the RDS instance
Log on to the ApsaraDB RDS console and go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
Create an account named
ldapuser. For more information, see Create an account.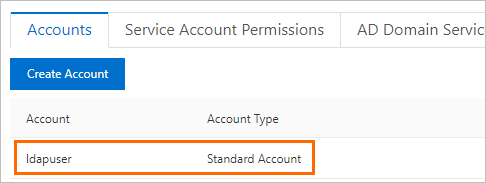 Note
NoteThe username of the account of your RDS instance must be the same as the name of the standard user that is created for the AD domain controller. The passwords of the two accounts can be different. When the AD domain controller is enabled for access control, the AD domain controller verifies the password of the standard user. When the AD domain controller is disabled for access control, ApsaraDB RDS verifies the password of the account of your RDS instance. You can set the password of the account on the Accounts page in the ApsaraDB RDS console.
In the left-side navigation pane, click Accounts. On the page that appears, click the AD Domain Services tab.
If the AD Domain Service tab is opened for the first time, the system creates the following two records by default:
host all all 0.0.0.0/0 md5 host replication all 0.0.0.0/0 md5You can delete or modify the records.
Click Edit of the first record and modify the following parameters.
NoteThe following table describes only the parameters that are used in the provided example. For more information, see Official documentation of PostgreSQL.
Parameter
Example
Description
Priority
0
The priority of the record. If you set this parameter to 0, the record has the highest priority and is automatically generated. Modify the first record and set this parameter to 0. The value 0 specifies the highest priority for the AD domain service.
TYPE
host
Valid values:
host: The record matches TCP/IP connections, including SSL connections and non-SSL connections.
hostssl: The record matches only TCP/IP connections that are established over SSL.
NoteThis parameter takes effect only when SSL encryption is enabled for your RDS instance. For more information, see Configure SSL encryption for an ApsaraDB RDS for PostgreSQL instance.
hostnossl: The AD domain verifies only TCP/IP connections that are established over non-SSL connections.
DATABASE
all
The database that the specified users are allowed to access. If the value of this parameter is all, the specified users are allowed to access all databases of your RDS instance. If you specify multiple entries, separate the entries with commas (,).
USER
ldapuser
The user that is allowed to access your RDS instance. Valid values: the created usernames of the AD domain controller. If you specify multiple entries, separate the entries with commas (,).
NoteThis parameter can be set only to the usernames of standard users that are created in the AD domain.
ADDRESS
0.0.0.0/0
The IP addresses from which the specified users can access the specified databases. If you set this parameter to 0.0.0.0/0, the specified users are allowed to access the specified databases from all IP addresses.
MASK
None
The mask for the IP address in the record. If the value of the ADDRESS parameter is an IP address, you can use this parameter to specify the mask of the IP address.
METHOD
ldap
NoteLDAP is a protocol that is used to access the directories of databases. In this topic, LDAP is used as an example.
This parameter specifies the authentication method of LDAP. Valid values:
trust
reject
scram-sha-256
md5
password
gss
sspi
ldap
radius
cert
pam
NoteThe valid values of this parameter must be in lowercase letters.
OPTION
ldapserver=<Private IP address of the ECS instance> ldapbasedn="CN=Users,DC=Prefix of the root domain name, pgsqldomain in this example,DC=Suffix of the root domain name, net in this example" ldapbinddn="CN=<Username of the administrator user of the AD domain>,CN=Users,DC=Prefix of the root domain name, pgsqldomain in this example,DC=Suffix of the root domain name, net in this example" ldapbindpasswd="<Password of the administrator user of the AD domain>" ldapsearchattribute="sAMAccountName"
The options of the authentication method. In this topic, LDAP is used as an example. You must specify this parameter. For more information, see Authentication Methods.
Click add to the right of the AD domain service record to add a record. The following information provides the valid values of the new record.
host all all 0.0.0.0/0 md5Click OK. Then, click Submit.
NoteAfter you click Submit, the status of your RDS instance changes to Maintaining Instance for about 1 minute. The new configurations take effect only for new connections. You must close the existing connections and re-establish these connections for the new configurations to take effect.
Optional. Import the service information about multiple AD domains at a time. You can also manually add the service information about the AD domain.
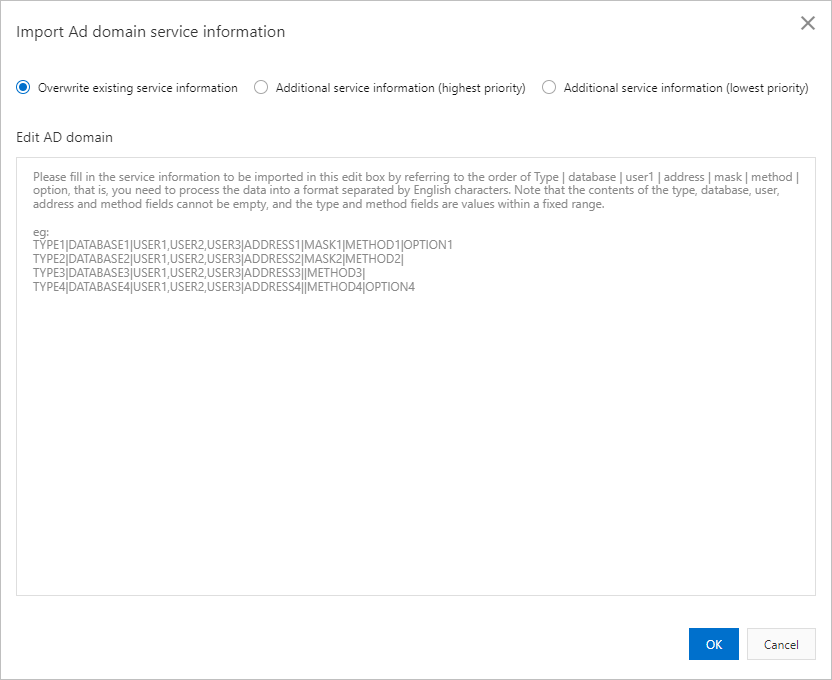
The following import methods are supported:
Overwrite existing service information.
Additional service information (highest priority): If you select this option, the service information of the AD domain is appended to the beginning of the existing service information. The priority of the appended information is higher than the priority of the existing service information.
Additional service information (lowest priority): If you select this option, the service information of the AD domain is appended to the end of the existing service information. The priority of the appended information is lower than the priority of the existing service information.
Valid format:
TYPE|DATABASE|USER1|ADDRESS|MASK|METHOD|OPTIONEnter the service information that you want to import in the Edit AD domain text box. For more information about the parameters, see Parameters.
Sample configuration:
host|all|<Username of the standard account of the AD domain>|0.0.0.0/0||ldap|ldapserver=<Private IP address of the ECS instance> ldapbasedn="CN=Users,DC=<Prefix of the root domain name, pgsqldomain in this example>,DC=<Suffix of the root domain name, net in this example>" ldapbinddn="CN=<Username of the administrator user of the AD domain>,CN=Users,DC=<Prefix of the root domain name, pgsqldomain in this example>,DC=<Suffix of the root domain name, net in this example>" ldapbindpasswd="<Password of the administrator user of the AD domain>" ldapsearchattribute="sAMAccountName"Test the connectivity.
Use a PostgreSQL command-line tool to connect to your RDS instance.
NoteYou can connect to your RDS instance by using multiple methods. In this topic, a PostgreSQL command-line tool is used. You must install the PostgreSQL client before you use the PostgreSQL command-line tool. For more information, see Connect to an ApsaraDB RDS for PostgreSQL instance.
Run the following command and use the username and password of the standard account of the AD domain controller to connect to your RDS instance:
psql -h <Endpoint of your RDS instance> -U <Username of the standard account of the AD domain> -p 5432 -d postgres
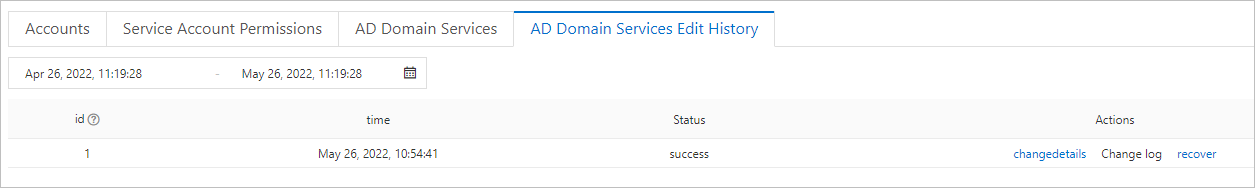
View the modification history of AD domain service information
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
In the left-side navigation pane, click Accounts. On the page that appears, click the AD Domain Services Edit History tab.
Click changedetails in the Actions column to view the change details. If the modification fails, the status is Not Taking Effect. You can click Change log to view the error message.