This topic describes how to grant privileges to an Alibaba Cloud account and an RAM user for data transmission.
Background
The logon system of the data transmission service is the same as that of Alibaba Cloud. You can log on by using an Alibaba Cloud account or an RAM user. For more information, see documentation of Resource Access Management (RAM).
An Alibaba Cloud account owns Alibaba Cloud resources and is billed for resource usage. You can use it to create RAM users for your enterprise and manage and grant privileges to the RAM users.
RAM users are created and managed by Alibaba Cloud accounts in the RAM system. They do not own resources and are not independently billed. All RAM users are controlled and charged by their respective Alibaba Cloud accounts.
Grant privileges to an Alibaba Cloud account for data transmission
The data transmission system must have the privileges to access cloud resources. If you have logged on by using an Alibaba Cloud account with no required privileges, go to the Alibaba Cloud console to grant privileges to the Alibaba Cloud account for data transmission.
Log on to the
by using an Alibaba Cloud account.
In the left-side navigation pane, expand Data Transmission and go to a navigation page.
Click Grant Privileges to RAM Role as prompted.
Confirm the information on the page and click Agree.
Return to and refresh the data transmission page.
Grant privileges to an RAM user for data transmission
The data transmission system must have the privileges to access cloud resources. If you have logged on by using an RAM user with no required privileges, go to the Alibaba Cloud console to grant privileges to the RAM user for data transmission.
Log on to the
by using an RAM user.
In the left-side navigation pane, expand Data Transmission and go to a navigation page.
Click Grant Privileges to RAM Role as prompted.
You can also click Switch to Alibaba Cloud Account to use the data transmission service.
Confirm the information on the page and click Agree.
Return to and refresh the data transmission page.
If the grant fails, you can perform any one of the following operations:
Switch to the Alibaba Cloud account to log on to the console.
Authorize the RAM user to grant privileges to other RAM users.
Log on to the RAM console by using the Alibaba Cloud account.
In the left-side navigation pane, choose Identities > Users.
On the Users page, click Add Permissions in the Actions column for the RAM user.
In the Add Permissions dialog box, click the System Policy tab. On this tab, search for and select AliyunRAMFullAccess to add it to the Selected list on the right.
Grant privileges to the RAM user for data transmission.
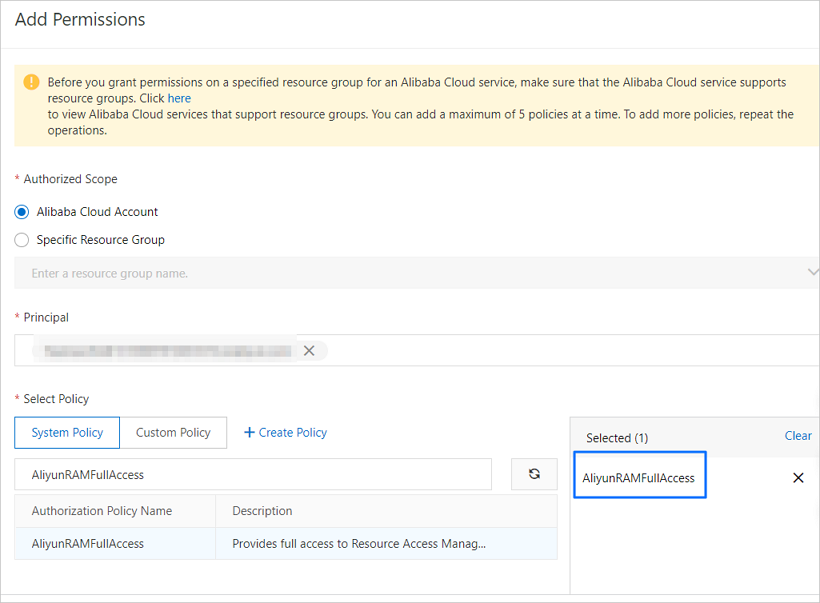
Click OK.
Click Complete.
Switch to an RAM user authorized to grant privileges to roles for data transmission and log on to the console again.
(Optional) Switch to the Alibaba Cloud account to log on to the console
If you have logged on to the console by using an RAM user, perform the following operations to switch to the Alibaba Cloud account. You can also skip the following operations and directly log on to the console by using the Alibaba Cloud account.
Log on to the
by using an RAM user.
Click User Center icon in the upper-right corner and then click Log Out.
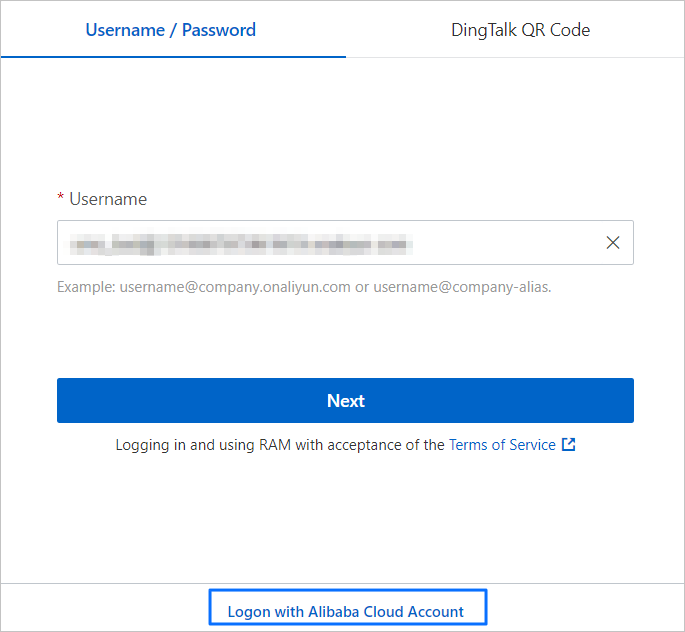
On the logon page, log on by using your Alibaba Cloud account.
(Optional) Authorize an RAM user to grant privileges to roles for data transmission
An RAM user must be granted the AliyunOceanbaseMigrationServiceRolePolicy role before it can access the data transmission system. If the RAM user is not granted the role, log on to the RAM console with your Alibaba Cloud account and manually add privileges to this role.
Log on to the RAM console by using the Alibaba Cloud account.
Create a role for data transmission.
In the left-side navigation pane, choose Identities > Roles.
On the Roles page, click Create Role.
In the Create Role dialog box, set the trusted entity to Alibaba Cloud Account and click Next.
On the Configure Role page, configure the parameters.
Parameter
Description
Role Name
Enter AliyunOceanbaseMigrationServiceRole.
Remarks (Optional)
The description of the role to be created.
Select Trusted Alibaba Cloud Account
Current Alibaba Cloud Account: If you allow an RAM user under the current Alibaba Cloud account to assume the RAM role, select Current Alibaba Cloud Account.
Other Alibaba Cloud Account: If you allow an RAM user under another Alibaba Cloud account to assume the RAM role, select Other Alibaba Cloud Account and enter the ID of the Alibaba Cloud account. This option is intended for resource access across Alibaba Cloud accounts.
Click Complete.
Create a permission strategy for the data transmission service to obtain RDS information.
Return to the Roles page and click Add Permissions for the new role.
In the Add Permissions dialog box, click Create Policy in Select Policy.
On the Create Policy page, click JSON and enter the following policy statement:
{ "Statement": [ { "Action": [ "rds:DescribeDBInstances", "rds:DescribeDBInstanceNetInfo", "rds:DescribeDBInstanceIPArrayList", "rds:ModifySecurityIps" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "vpc:DescribeVpcs", "vpc:DescribeVSwitches" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "polardb:DescribeDBClusterIPArrayList", "polardb:DescribeDBClusterNetInfo", "polardb:DescribeDBClusters", "polardb:DescribeRegions", "polardb:DescribeDBClusterEndpoints", "polardb:DescribeDBClusterAccessWhitelist", "polardb:ModifyDBClusterAccessWhitelist" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "dg:GetUserGatewayInstances", "dg:GetUserGateways", "dg:GetUserDatabases", "dg:ListDatabaseAccessPoint", "dg:DescribeRegions", "dg:FindUserGatewayById" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "adb:DescribeDBClusters", "adb:DescribeDBClusterAttribute", "adb:DescribeAutoRenewAttribute", "adb:DescribeAvailableResource", "adb:DescribeDBResourcePool", "adb:DescribeElasticDailyPlan", "adb:DescribeElasticPlan", "adb:DescribeTables", "adb:DescribeAllDataSource", "adb:DescribeSchemas", "adb:DescribeColumns", "adb:DescribeTablePartitionDiagnose", "adb:DescribeRegions", "adb:DescribeDBClusterNetInfo", "adb:DescribeDBClusterAccessWhiteList", "adb:ModifyDBClusterAccessWhiteList" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "dms:ListUsers", "dms:ListUserTenants", "dms:ListColumns", "dms:ListIndexes", "dms:ListDatabases", "dms:ListLogicDatabases", "dms:ListTables", "dms:ListLogicTables", "dms:ListInstances", "dms:GetUserActiveTenant", "dms:GetTableDBTopology", "dms:SearchDatabase", "dms:SearchTable" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "cms:DescribeContactList", "cms:DescribeMonitorGroups", "cms:DescribeMonitorGroupInstances", "cms:DescribeCustomMetricList", "cms:DescribeSystemEventMetaList", "cms:DescribeSystemEventCount", "cms:DescribeSystemEventAttribute", "cms:DescribeSystemEventHistogram", "cms:DescribeCustomEventCount", "cms:DescribeCustomEventAttribute", "cms:DescribeCustomEventHistogram", "cms:CreateMonitorGroup", "cms:PutCustomEvent", "cms:PutCustomMetric", "cms:PutContactGroup", "cms:PutCustomMetricRule" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "alikafka:ListInstance", "alikafka:UpdateInstance", "alikafka:ReadOnly" ], "Resource": "*", "Effect": "Allow" }, { "Effect": "Allow", "Action": [ "ecs:DescribeVSwitches", "ecs:DescribeSecurityGroups", "ecs:CreateSecurityGroup", "ecs:DeleteSecurityGroup", "ecs:CreateNetworkInterface", "ecs:DescribeNetworkInterfaces", "ecs:CreateNetworkInterfacePermission", "ecs:DescribeNetworkInterfacePermissions", "ecs:DeleteNetworkInterface" ], "Resource": "*" } ], "Version": "1" }Click Next: Edit Basic Information.
Set Name and click OK.
Add privileges to the RAM role.
Return to the Roles page and click Add Permissions for the new role.
In the Add Permissions dialog box, click Custom Policy in Select Policy.
Search for and select the new policy to add it to the Selected list on the right.
Click OK.