You can separately configure the features of generating and collecting the access logs of a Service Mesh (ASM) gateway based on your business requirements. If you enable the feature of generating the access logs of an ASM gateway, the gateway prints the access logs to the standard output. You can customize the fields that are printed in the access logs. If you enable the feature of collecting the access logs of an ASM gateway, the logs printed by the gateway are collected to Simple Log Service of Alibaba Cloud, which allows you to store and analyze logs and visualize the query and analysis results on charts. This topic describes how to configure the features of generating and collecting the access logs of an ASM gateway and view the access logs.
Prerequisites
Simple Log Service is activated for your Alibaba Cloud account. For more information, see Step 1: Activate Log Service in the Getting Started topic.
ImportantYou are not charged for collecting logs to Simple Log Service in ASM. However, Simple Log Service charges you in the pay-by-feature or pay-by-ingested-data billing mode. For more information about the billing of Simple Log Service, see Billing overview.
The logtail-ds component is installed in the data-plane cluster. For more information, see Step 1: Install Logtail in the Collect log data from containers by using Log Service topic.
Step 1: Enable the feature of generating access logs
For more information, see Customize access logs of clusters on the data plane.
Step 2: Enable the feature of collecting access logs and view the access logs
Enable the feature of collecting access logs. For more information, see Use Log Service to collect access logs on the data plane.
View access logs.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose or .
In the Observability section of the desired gateway, click Log Center or Log Dashboard.
Gateway Logs: displays only the logs of the current gateway.
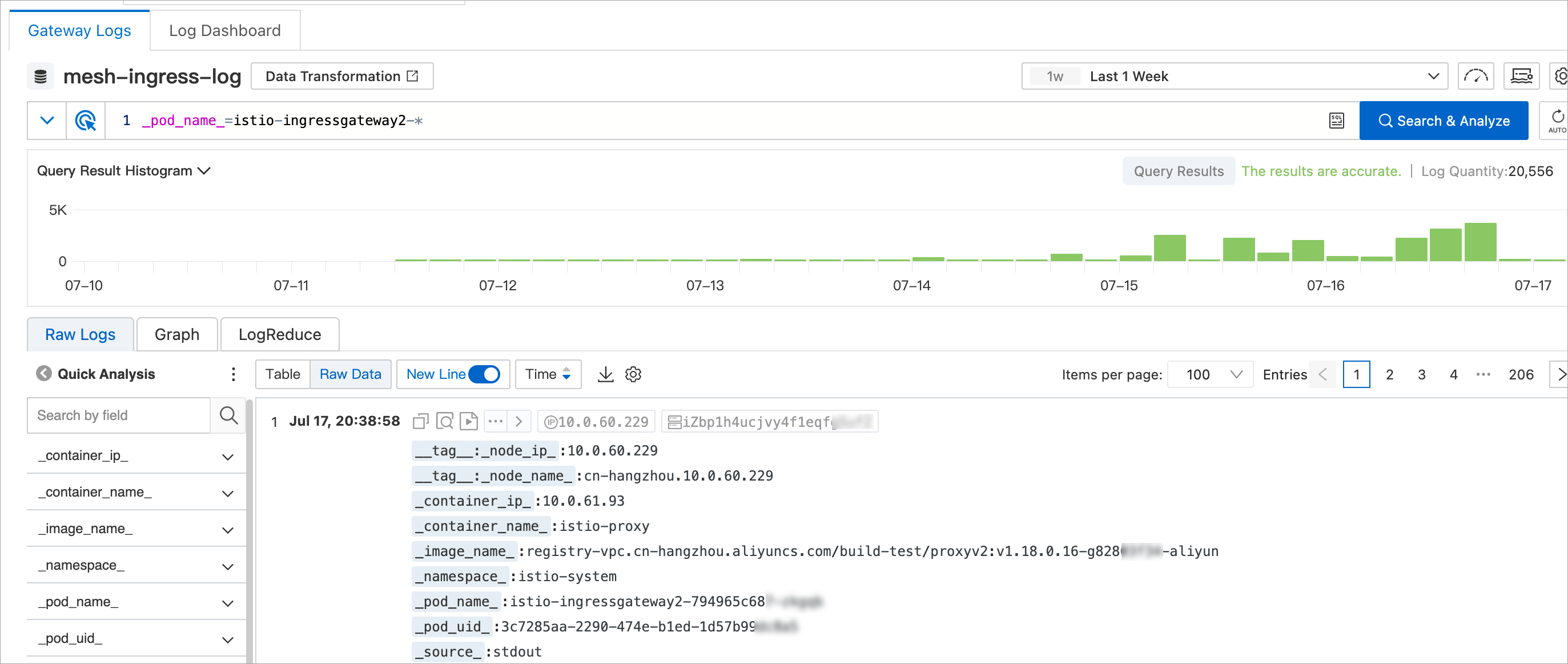
Log Dashboards: displays only the log analysis results of the current gateway.
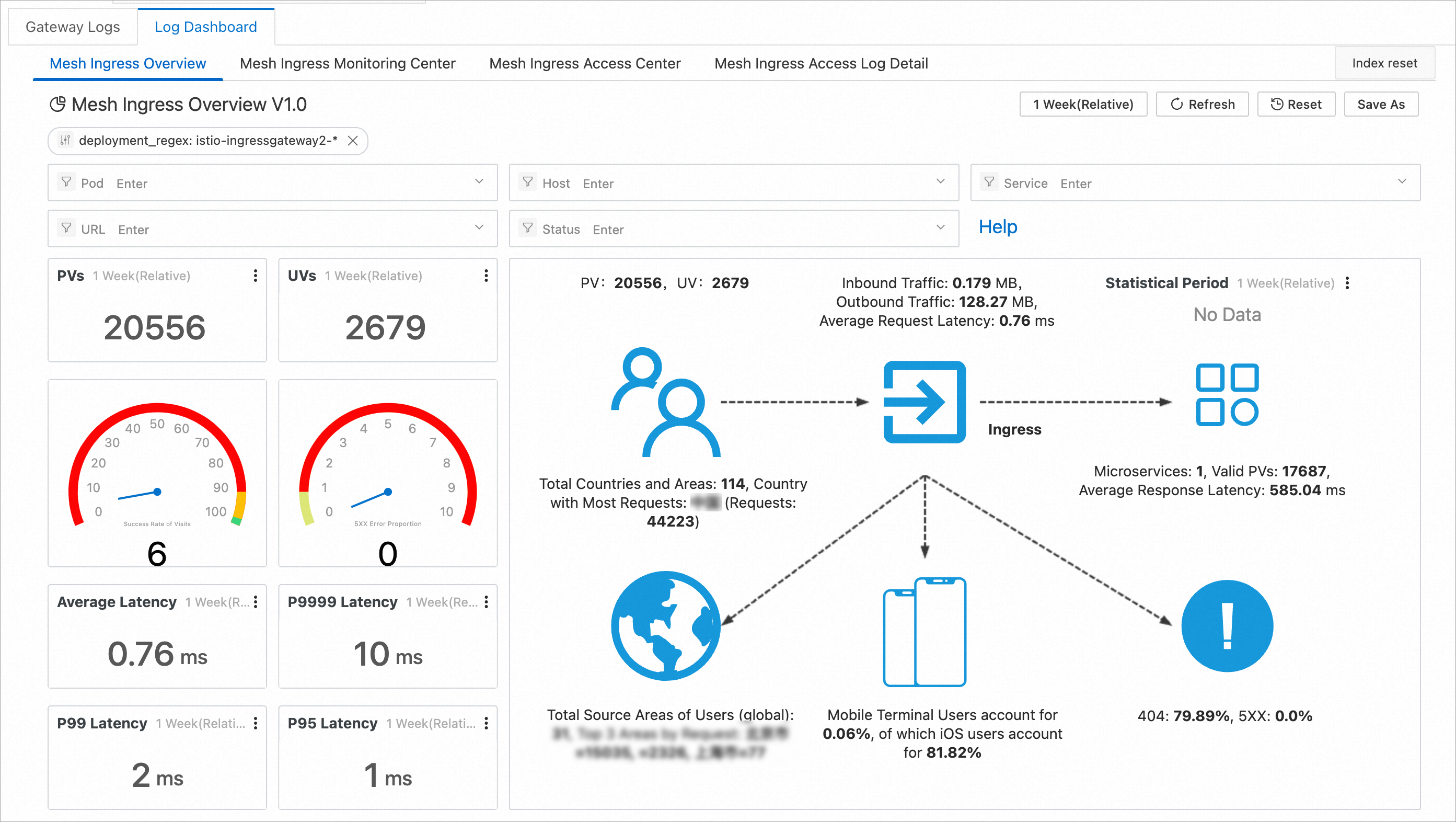
ASM instances of versions earlier than 1.17.2.35
For more information, see Use Log Service to collect access logs on the data plane.