Domain Name System (DNS) resolution is one way to implement service discovery in an ACK Serverless cluster. This topic describes the principles of DNS resolution and the DNS service discovery solutions available for ACK Serverless clusters.
Index
Notes
If you do not enable a DNS service discovery component when you create an ACK Serverless cluster, pods use the DNS servers provided by the Virtual Private Cloud (VPC) for domain name resolution by default. In this mode, the domain names of Kubernetes services cannot be resolved.
For existing ACK Serverless clusters, enabling a DNS service discovery solution takes effect only on new pods. Pods created before you enable the solution do not switch their DNS configuration files. You must recreate these pods to use the new DNS service discovery solution.
The managed CoreDNS component will gradually replace the self-managed CoreDNS component until the self-managed CoreDNS component is discontinued. The self-managed CoreDNS component may not be available in the console in the future. To use the self-managed CoreDNS component, submit a ticket for assistance.
How DNS resolution works in ACK Serverless clusters
When a pod is created in an ACK Serverless cluster, the /etc/resolv.conf file contains the following content by default. This file specifies the DNS server, search domains, and other parameters.
# The nameserver indicates the IP address of the DNS server used by this pod.
nameserver 172.xx.x.xx
# The search indicates the domain name suffixes to append when a service is requested. The following example shows the suffixes when the pod is in the kube-system namespace.
search kube-system.svc.cluster.local svc.cluster.local cluster.local
# Other parameters
options ndots:5For more information about the fields in the DNS resolution configuration file and the Pod DNSPolicy, see DNS principles and configurations.
DNS service discovery solutions for ACK Serverless clusters
DNS service discovery solution | Description |
Managed CoreDNS | Recommended. Pods use the managed CoreDNS component for domain name resolution. ACK Serverless creates and manages CoreDNS to ensure it runs properly. You do not need to manually perform O&M tasks or monitor the status of CoreDNS. This solution does not consume Elastic Container Instance (ECI) resources in your cluster. |
Self-managed CoreDNS | Pods use the self-managed CoreDNS component for domain name resolution. You must correctly configure CoreDNS and monitor the status of its replicas. |
PrivateZone | Pods use the PrivateZone component for domain name resolution. ACK Serverless automatically creates and updates the DNS records in PrivateZone. |
Managed CoreDNS
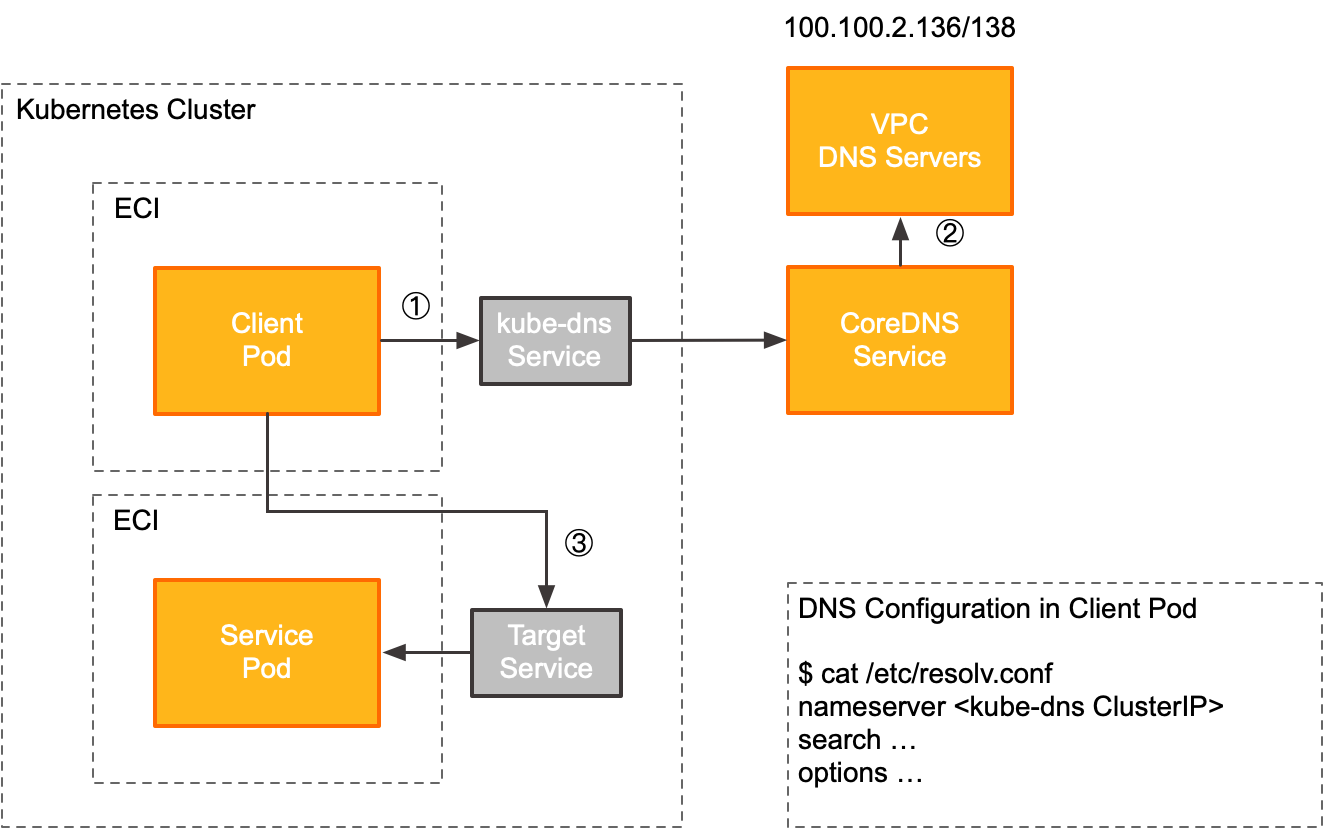
The managed CoreDNS component exposes the DNS service through the cluster IP of the kube-dns service in the kube-system namespace. The following flow shows how an application pod uses the managed CoreDNS.
Link | Description |
1 | When a client pod accesses an upstream service (TargetService), it first gets the DNS server address from the local DNS resolution configuration file ( In this solution, the DNS server address is the IP address of the kube-dns service in the kube-system namespace of the ACK Serverless cluster. The backends of the kube-dns cluster IP are dynamically maintained and updated by the ACK Serverless cluster. You do not need to manage them.
|
2 | When a client pod requests a domain name outside the cluster, the managed CoreDNS forwards the request to the DNS servers provided by the VPC (100.100.2.136 and 100.100.2.138) for resolution. |
3 | After the client pod gets the IP address of the upstream service (TargetService) from the DNS server, it sends a request to that IP address. |
Enable the managed CoreDNS component
After you enable the managed CoreDNS component, the ACK Serverless cluster automatically creates a service named kube-dns in the kube-system namespace. Do not modify this service.
The managed CoreDNS component is being rolled out. If you cannot find the managed CoreDNS component in the console, the component is not yet available in the current region. The custom configuration feature for the managed CoreDNS component is also being rolled out. To use this feature, submit a ticket for assistance.
Method 1: For a new ACK Serverless cluster, you can specify Managed CoreDNS as the DNS service discovery method when you create the cluster to enable the managed CoreDNS component.
Method 2: For an existing ACK Serverless cluster, go to the cluster management page. Choose Operations Management > Components. Click the Network tab, and then click Install for the Managed CoreDNS component. For more information, see Manage components.
Self-managed CoreDNS
Self-managed CoreDNS is a component in Kubernetes clusters that handles DNS resolution. It can resolve custom service domain names within the cluster and external domain names. Self-managed CoreDNS has a rich set of plug-ins and supports custom DNS, custom hosts, canonical names (CNAMEs), and rewrites at the cluster level. Like Kubernetes, the CoreDNS project is hosted by the Cloud Native Computing Foundation (CNCF). For more information about the CNCF, see CNCF. For more information about CoreDNS, see CoreDNS: DNS and Service Discovery.
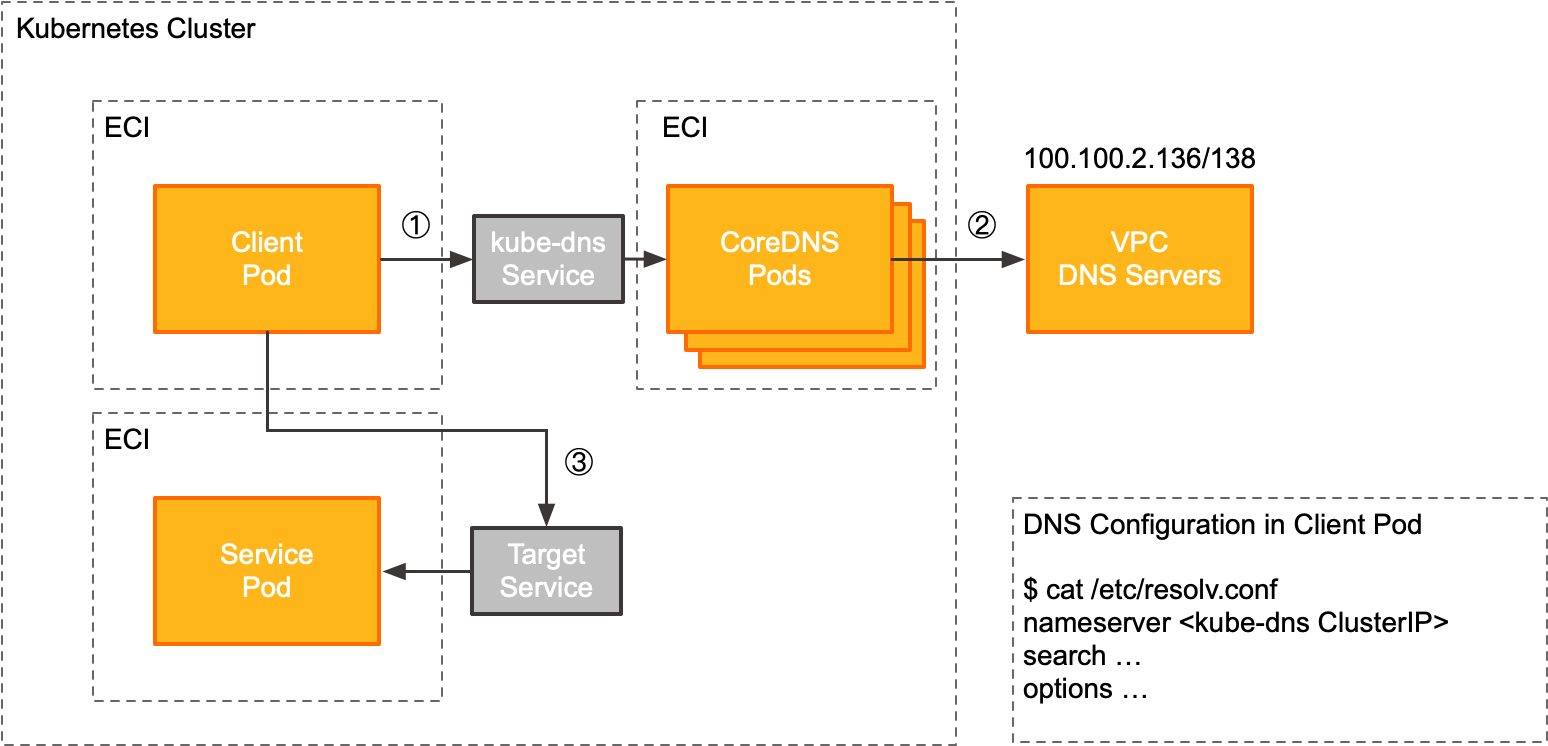
The self-managed CoreDNS component exposes the DNS service through the cluster IP of the kube-dns service in the kube-system namespace. The following flow shows how an application pod uses the self-managed CoreDNS.
Link | Description |
1 | When a client pod accesses an upstream service (TargetService), it first gets the DNS server address from the local DNS resolution configuration file ( In this solution, the DNS server address is the IP address of the kube-dns service in the kube-system namespace of the ACK Serverless cluster.
|
2 | When a client pod requests a domain name outside the cluster, CoreDNS forwards the request to the DNS servers provided by the VPC (100.100.2.136 and 100.100.2.138) for resolution. |
3 | After the client pod gets the IP address of the upstream service (TargetService) from the DNS server, it sends a request to that IP address. |
Enable the self-managed CoreDNS component
Method 1: For a new ACK Serverless cluster, you can specify CoreDNS as the DNS service discovery method when you create the cluster to enable the self-managed CoreDNS component.
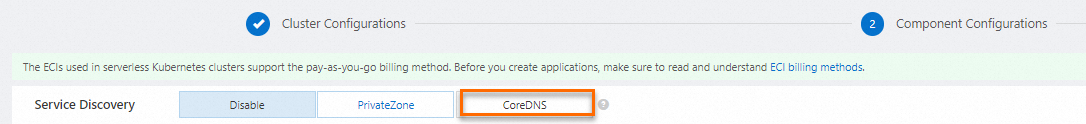
Method 2: For an existing ACK Serverless cluster, go to the cluster management page. Choose Operations Management > Components. Click the Network tab, and then click Install for the CoreDNS component. For more information, see Manage components.
PrivateZone
PrivateZone is a private domain name resolution service based on the Alibaba Cloud VPC environment. You can use the PrivateZone controller to monitor the services and endpoints in each namespace of an ACK Serverless cluster in real time. The controller interacts with the API server to automatically sync the domain names of resources to PrivateZone. Pods in the ACK Serverless cluster can then use the PrivateZone DNS service to implement Kubernetes service discovery. For more information about how to use the PrivateZone solution, see Service discovery based on Alibaba Cloud DNS PrivateZone in ACK Serverless clusters.
PrivateZone exposes the DNS service through the DNS servers provided by the VPC (100.100.2.136 and 100.100.2.138). The following flow shows how an application pod uses PrivateZone.
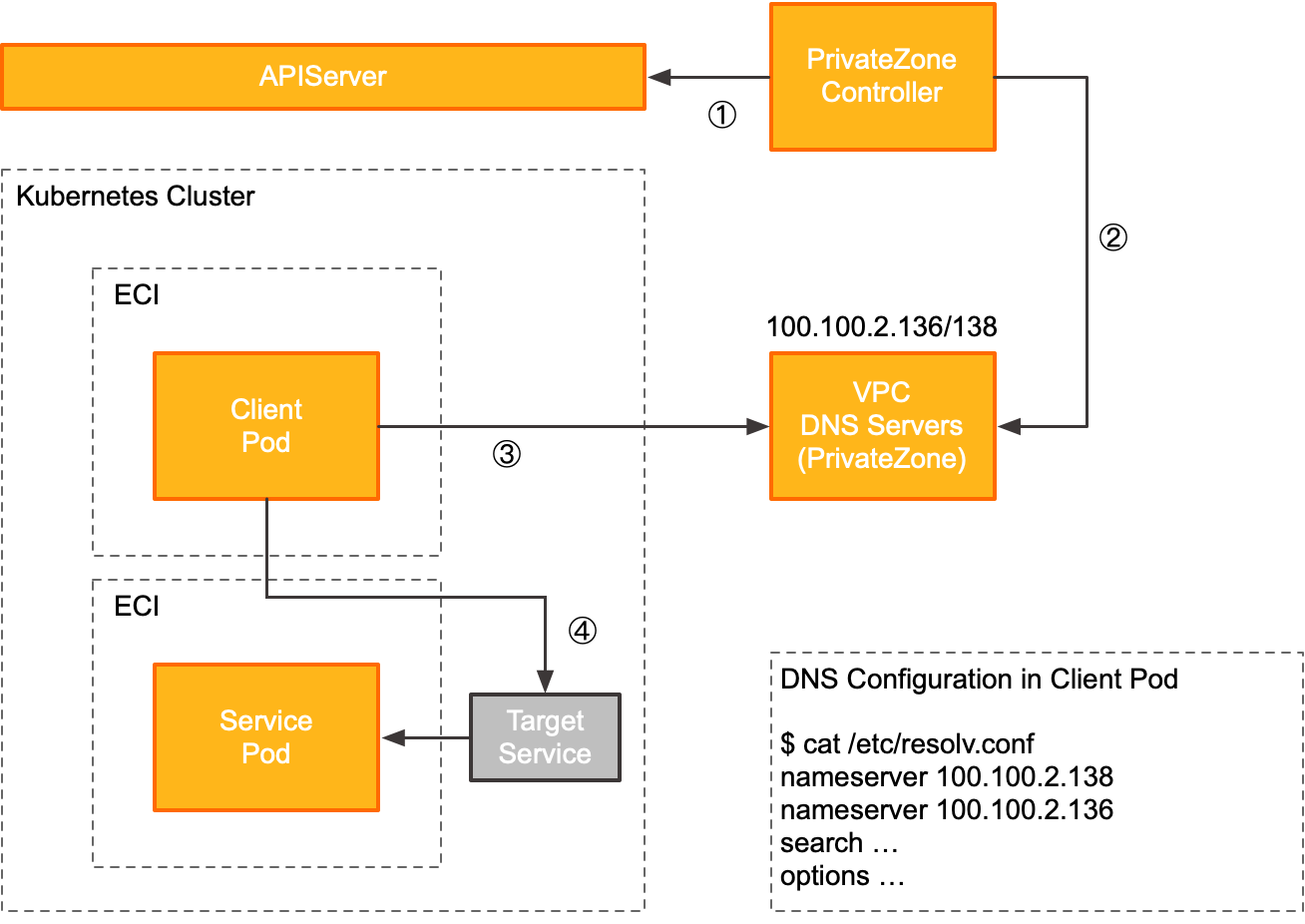
Link | Description |
1 | The PrivateZone controller connects to the API server and listens for service creation and update events in the cluster. |
2 | When the PrivateZone controller detects a service creation or update event, it syncs the information to the authoritative zone records in PrivateZone. |
3 | When a client pod accesses an upstream service (TargetService), it first gets the DNS server address from the local DNS resolution configuration file ( In this solution, the DNS server addresses are the IP addresses of the DNS servers provided by the VPC (100.100.2.136 and 100.100.2.138) that are configured in the DNS resolution configuration file. The DNS server gets the correct DNS record from PrivateZone and returns it to the client. |
4 | After the client pod gets the IP address of the upstream service (TargetService) from the DNS server, it sends a request to that IP address. |
Enable the PrivateZone component
Method 1: For a new ACK Serverless cluster, you can specify PrivateZone as the DNS service discovery method when you create the cluster to enable the PrivateZone component.
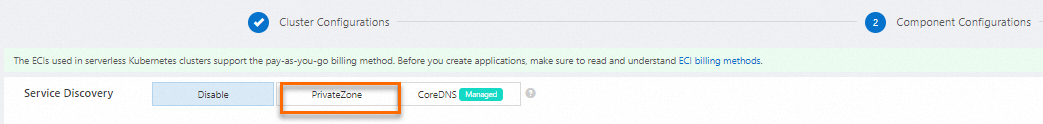
Method 2: For an existing ACK Serverless cluster, you can set the
enablePrivateZoneparameter totruein theeci-profileconfiguration item to enable the PrivateZone component.
FAQ
How can I check whether the managed CoreDNS, self-managed CoreDNS, or PrivateZone component is enabled for my cluster?
Managed CoreDNS and self-managed CoreDNS components
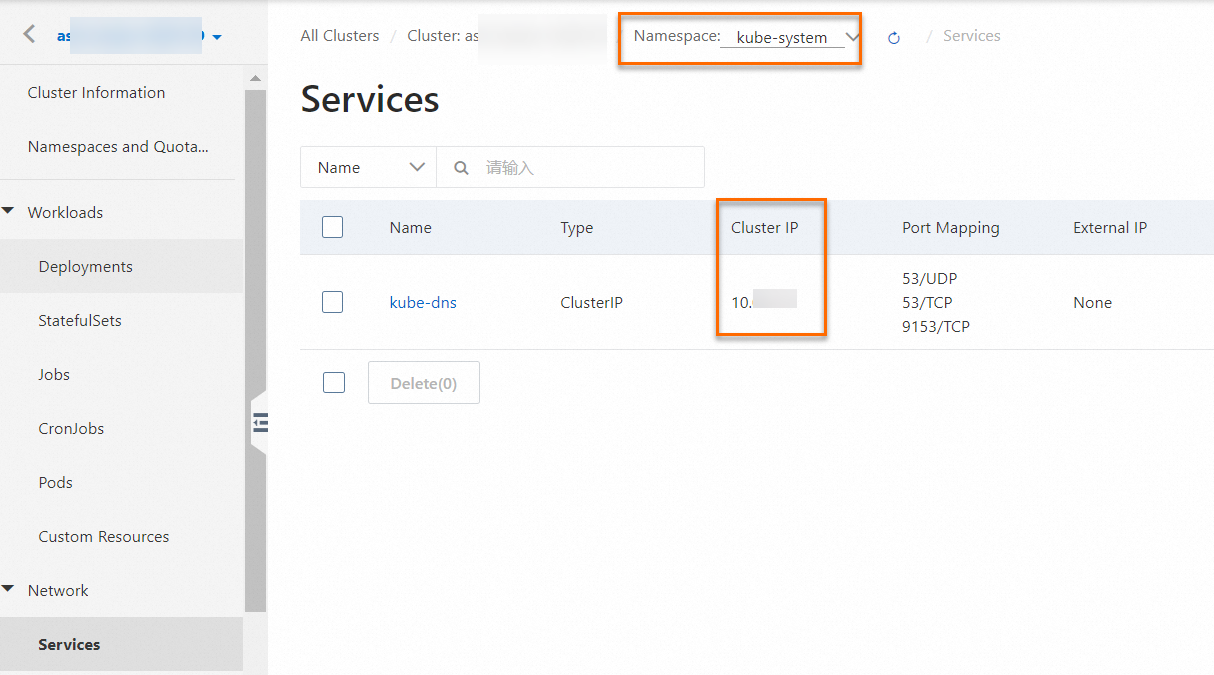
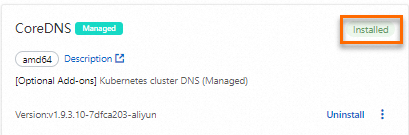
Log on to the Container Service Management Console. On the cluster management page, select Operations Management > Component Management and click the Network tab. If the Installed label is displayed in the upper-right corner of a component, this indicates that the managed CoreDNS or self-managed CoreDNS component is enabled for the cluster.
The following figure shows an example of the managed CoreDNS component.
PrivateZone component
Log on to the PrivateZone console. On the Authoritative Zones On VPC tab, search for a Domain Zone by cluster ID. If you find a zone whose name ends with the cluster ID, this indicates that the PrivateZone component is enabled.
How can I check whether an application pod is using the managed CoreDNS, self-managed CoreDNS, or PrivateZone component?
Managed CoreDNS and self-managed CoreDNS components
Run the
kubectl execcommand to enter the pod. Run thecat /etc/resolv.confcommand. If thenameserverfield is set to the cluster IP address of the kube-dns service in the kube-system namespace, the pod is using the managed CoreDNS or self-managed CoreDNS component.PrivateZone component
Run the
kubectl execcommand to enter the pod. Run thecat /etc/resolv.confcommand. If thenameserverfield is set to100.100.2.136and100.100.2.138, the pod is using the PrivateZone component. The IP addresses in this example are for reference only. Use the actual IP addresses.