If the default containerd configuration does not meet your business requirements, you can customize the containerd configuration for nodes in a node pool. For example, you can configure multiple mirror repositories for a specific image repository, or configure the container runtime to skip certificate authentication when it pulls container images.
Limits
The node pool must use containerd 1.6.20 or later as its container runtime. If the containerd version is earlier than 1.6.20, you must upgrade the node pool.
Notes
Custom containerd configurations are applied to nodes in batches. The changes take effect immediately on existing nodes in the node pool. New nodes added to the node pool also use the new configuration.
Do not use the command line to modify the customizable containerd parameters. ACK intercepts these operations and prevents them from taking effect. If you have modified these parameters from the command line, you must restore them to their original values.
When the custom containerd configuration takes effect, the system automatically formats the configuration and corrects any improper syntax.
Customizable containerd parameters
Custom container runtime configuration
Parameter | Description | Type | Value description |
| The maximum number of concurrent image layer downloads. Increasing this value can speed up pulling multilayer images, but it also increases network and I/O load. | Int |
|
| Specifies whether to ignore anonymous volumes defined by | Bool | Default value: true |
| The maximum size in bytes of a core file that is generated when a process inside a container creates a core dump. Key values:
| Int |
|
| The maximum number of file descriptors that a container can open. | Int |
|
| The maximum amount of memory in bytes that a process inside a container can lock. | Int |
|
Registry Mirrors
Description | Configuration suggestion |
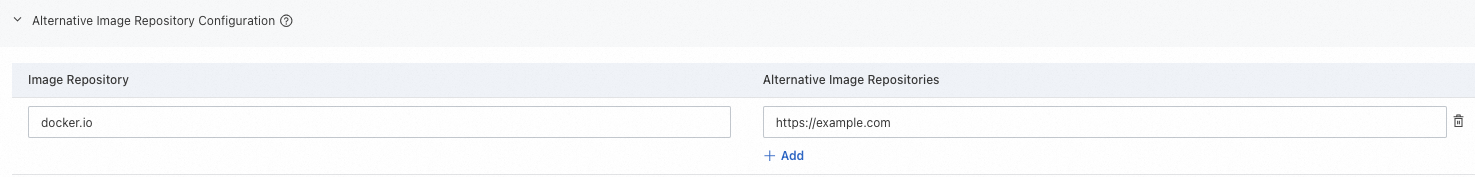
Configure mirror repositories for an image repository to accelerate image pulls. This allows the container runtime to pull images from the specified mirror repositories. This configuration does not require a container restart. |
|
Insecure Registries
Description | Configuration suggestion |
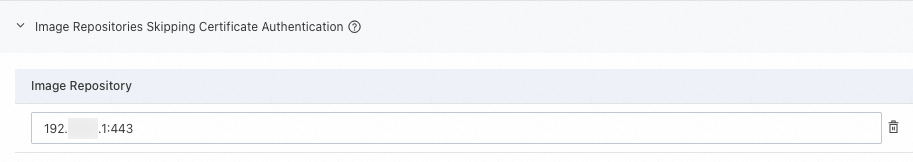
Allows the container runtime to skip certificate authentication when it pulls container images from a specified image repository. This is typically used in a staging environment to pull images from repositories that use self-signed certificates. This configuration does not require a container restart. |
|
Customize the containerd configuration of a node pool in the console
Modifying the containerd configuration does not affect existing containers. To ensure cluster stability, we recommend that you perform this operation during off-peak hours.
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Cluster List page, click the name of the target cluster. In the navigation pane on the left, choose .
On the Node Pools page, click
 > Containerd Configuration in the Actions column of the target node pool.
> Containerd Configuration in the Actions column of the target node pool.Read the notes on the page. Follow the instructions to add the required parameters, specify the target nodes, and set the batch configuration policy. Then, click Submit.
For more information, see Configuration examples.
If you remove a Custom container runtime configuration, the parameters are automatically restored to their default values.
After you submit the configuration, the changes are applied to nodes in batches. The process takes some time. You can view the progress and manage the process in the event list. For example, you can pause, resume, or cancel the task. If a task fails on a node, you can troubleshoot the node and click Continue to retry the operation.
You can use the pause feature to validate the upgraded nodes. When you pause the task, nodes that are being updated will complete the configuration process. Nodes that are not yet updated will not be configured until you resume the task. Complete the custom configuration task as soon as possible. A paused task is automatically canceled after 7 days, and the related events and logs are cleared.
Configuration examples
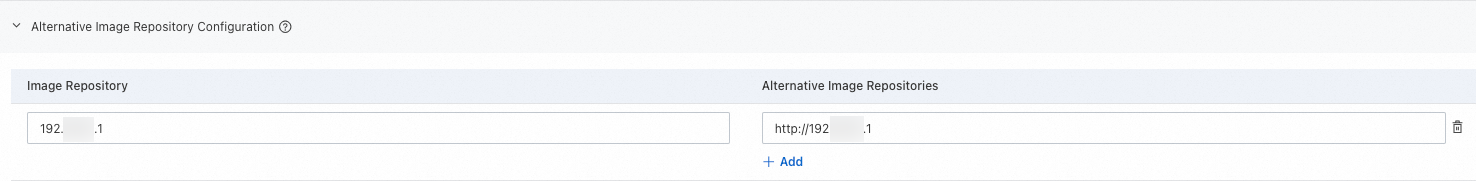
Configure a mirror repository for docker.io | Specify a private repository to skip certificate authentication | Configure an HTTP private image repository |
|
|
|
FAQ
Will customizing containerd parameters affect my services?
The changes do not affect running pods. The new configuration takes effect only on pods that are created after the changes are applied. We recommend that you perform this operation during off-peak hours.
To apply the new configuration to existing pods, you must manually recreate them.
What do I do if I receive a not match XXX or must be between XXX error when I customize containerd parameters?
The following are common reasons:
must be between XXX: The parameter value or format is invalid. For example, the format may be incorrect or the value is outside the valid range.not match XXX: This error indicates that you have modified the configuration file from the command line. ACK intercepts such changes. You must restore the parameter to its original value.
References
For more information about the automated O&M capabilities of node pools, see Automated O&M capabilities.
If an error occurs or an exception is reported for a node, pod, containerd, or kubelet, see Troubleshoot node exceptions, Troubleshoot pod exceptions, and FAQ about nodes and node pools.